AWS Certified Developer - Associate
API Gateway
Authentication Authorization Demo
In this lesson, you will learn how to configure authentication and authorization for your API Gateway using various methods. We'll walk through setting up method-level authorization with AWS IAM and resource policies, as well as implementing a custom Lambda authorizer.
Configuring Method-Level Authorization
To enable authorization for a specific method on your API Gateway, follow these steps:
- Select the API from the AWS API Gateway console.
- Choose the method you wish to modify.
- Click Edit under the method request.
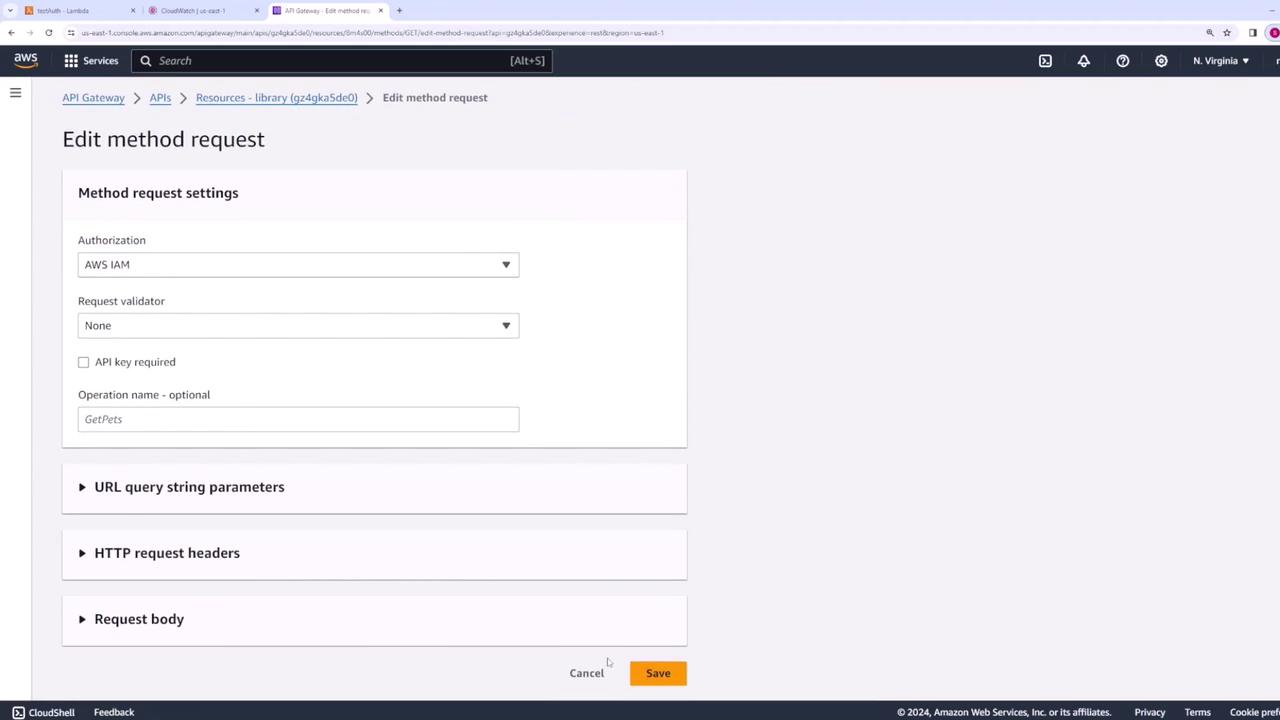
In the authorization section, you can select one of the available options. By default, AWS IAM is chosen, which means IAM handles all authorization and integrates seamlessly with other AWS services.
Another approach to controlling API access involves using resource policies. In the resource policies section, click Create policy to define a policy document similar to those used with other AWS services like S3 or Lambda. For example, to allow access only from specific AWS accounts, you could define a policy like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::{{otherAWSAccountID}}:root",
"arn:aws:iam::{{otherAWSAccountID}}:user/{{otherAWSUserName}}",
"arn:aws:iam::{{otherAWSAccountID}}:role/{{otherAWSRoleName}}"
]
},
"Action": "execute-api:Invoke",
"Resource": [
"execute-api:{{stageNameOrWildcard}}/{{httpVerbOrWildcard}}/{{resourcePathOrWildcard}}"
]
}
]
}
To restrict access based on IP addresses or IP ranges, use a policy similar to this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Principal": "*",
"Action": "execute-api:Invoke",
"Resource": "execute-api:{{stageNameOrWildcard}}{{httpVerbOrWildcard}}{{resourcePathOrWildcard}}",
"Condition": {
"IpAddress": {
"aws:SourceIp": ["{{sourceIpOrCIDRBlock}}", "{{sourceIpOrCIDRBlock}}"]
}
}
},
{
"Effect": "Allow",
"Principal": "*",
"Action": "execute-api:Invoke",
"Resource": "execute-api:{{stageNameOrWildcard}}{{httpVerbOrWildcard}}{{resourcePathOrWildcard}}"
}
]
}
Setting Up a Lambda Authorizer
A Lambda authorizer allows you to implement custom authorization logic in a Lambda function. When configured, API Gateway passes the incoming request's authorization token to your Lambda function, which returns an IAM policy determining whether to allow or deny the request.
Below is an example of a simple Lambda authorizer written in JavaScript. This function checks if the token is equal to "abc123" and then returns a corresponding IAM policy:
export const handler = async (event) => {
// Implement token validation logic
let effect = "Deny";
if (event.authorizationToken === "abc123") {
effect = "Allow";
}
const policy = {
principalId: "abc123",
policyDocument: {
Version: "2012-10-17",
Statement: [
{
Action: "execute-api:Invoke",
Effect: effect,
Resource: "arn:aws:execute-api:us-east-1:841860927337:gz4gka5de0/dev/*/*"
}
]
}
};
return policy;
};
This Lambda function examines the client-provided header (typically "authorization" or "authorization token"), performs validation, and returns a policy document to either grant or deny access.
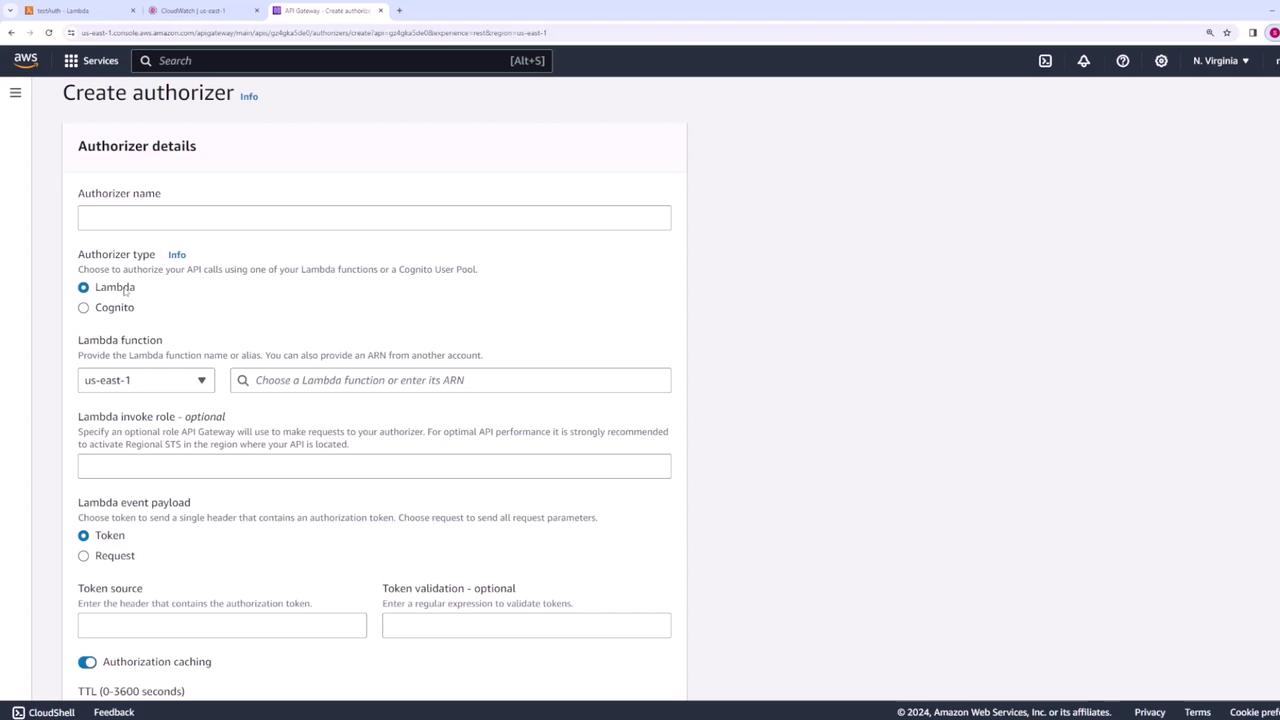
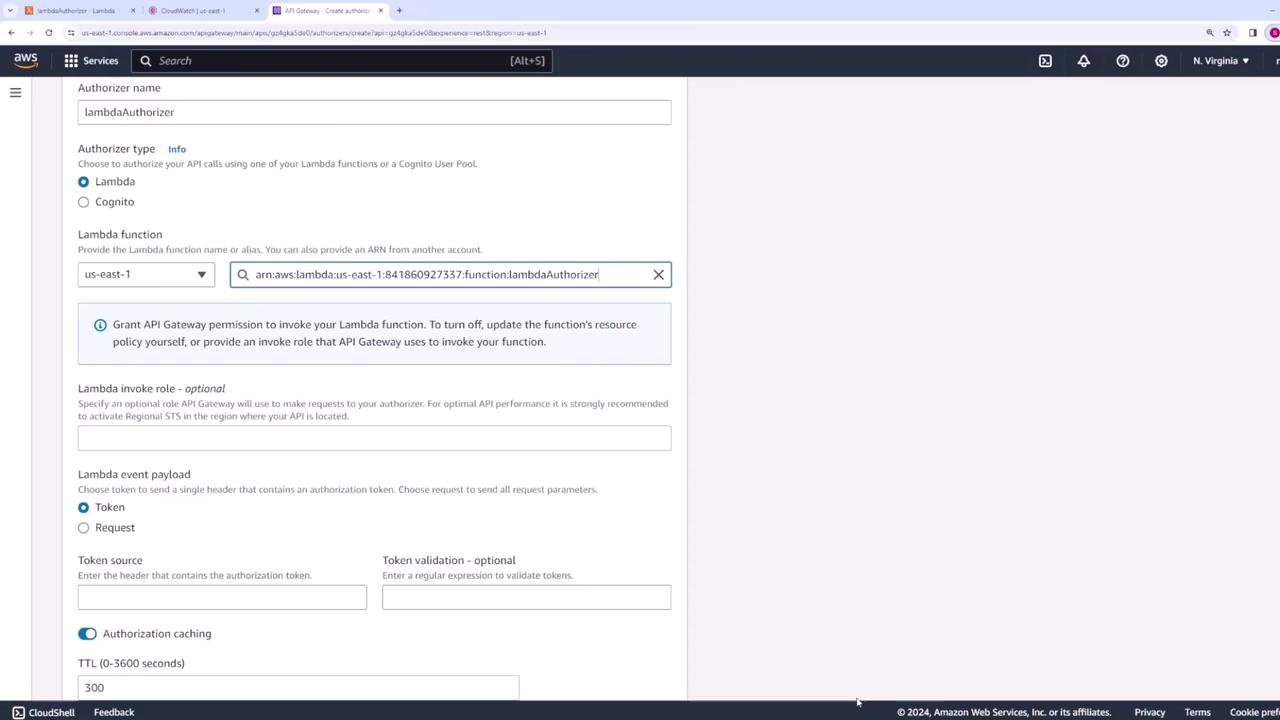
When configuring the Lambda authorizer in API Gateway:
- Select Lambda as the authorizer type.
- Choose the Lambda function you created.
- Specify the header name (for example, "authorization token") that contains the token.
- Optionally, configure caching settings (default is set to 300 seconds) for improved performance.
Once the authorizer is created, you can test it directly from the API Gateway console. Using an incorrect token will return a policy that denies access, while the correct token "abc123" will return a policy that allows access.
To use your new Lambda authorizer on an API method:
- Navigate to the specific method in your API.
- Click Edit under the method request section.
- Under the authorization settings, select your Lambda authorizer.
- Save your changes.
- Deploy the API for the changes to take effect.
Testing the Authorization
After deploying your changes, test your API endpoint to ensure that the authorization settings are functioning as expected.
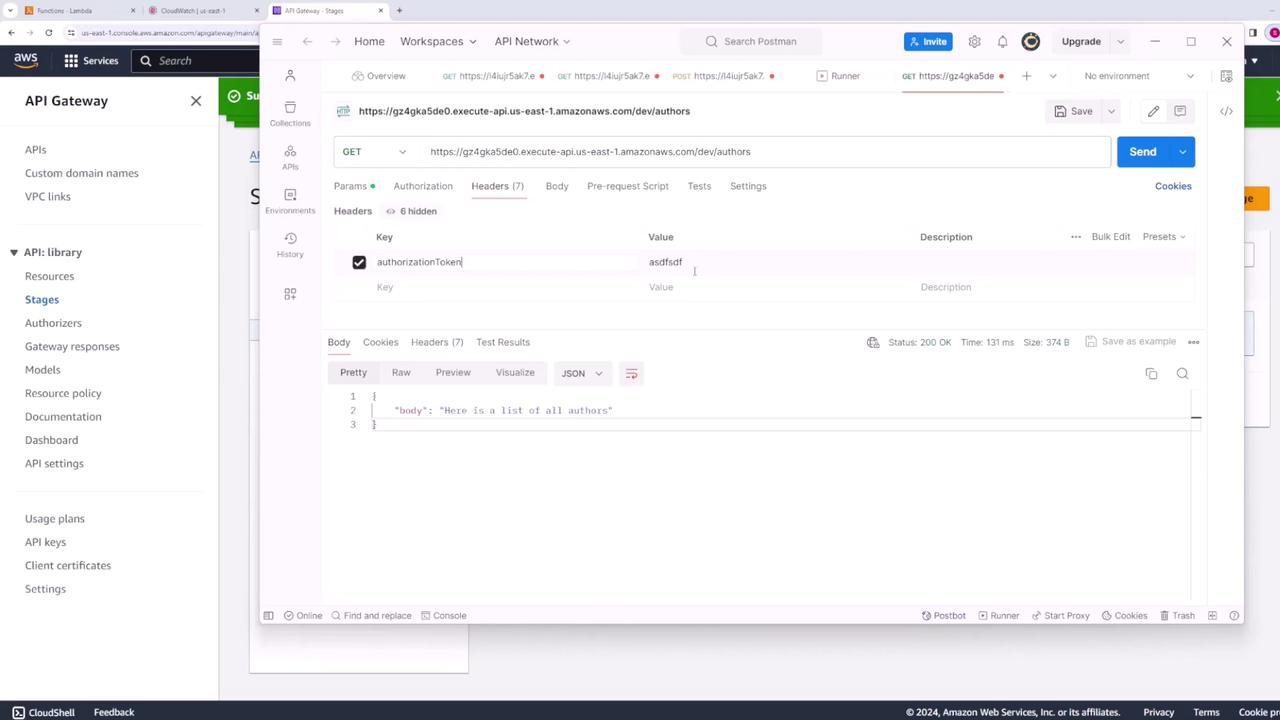
Without sending the token, you should receive an unauthorized response:
{ "message": "Unauthorized" }If you provide an incorrect token, the API will still deny access.
When you send the correct token (authorization token: "abc123"), the API should return the expected response. For instance, if your API returns a list of authors, the response might look like this:
{ "body": "Here is a list of all authors" }
Testing Tip
Ensure you deploy your API after making changes to the authorization configuration. This guarantees that your test results reflect the latest settings.
Summary
In this lesson, we demonstrated multiple approaches for authorizing access to your API Gateway:
- Using AWS IAM for method-level authorization.
- Employing resource policies to restrict access based on AWS account or IP address.
- Implementing a custom Lambda authorizer to handle complex authorization logic.
By selecting and configuring the approach that best fits your security requirements, you can ensure that your API Gateway is robustly secured.
For further details on AWS API Gateway and related configurations, consider exploring the AWS Documentation.
Watch Video
Watch video content