AWS Certified Developer - Associate
Identity and Access Management IAM
IAM PassRole for AWS Services Demo
In a previous lesson, we discussed the importance of assigning IAM roles to specific AWS services so that they have the necessary permissions to perform various operations in your AWS accounts. When logged in as a user, you must possess the IAM PassRole permission to assign a role to an AWS service. In this demo, we will explain how to grant a user the IAM PassRole permission, enabling them to assign a specific role to an EC2 instance.
Overview
For this demonstration, Firefox is set up to log into three AWS accounts simultaneously:
- Administrator Account (Blue): Full permissions.
- User One Account (Green)
- User Two Account (Purple)
The demo involves creating a role named "EC2 S3 Access" with a trust policy configured to allow only EC2 to assume the role.
Configuring the Trust Policy
The trust policy for the "EC2 S3 Access" role is defined as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"sts:AssumeRole"
],
"Principal": {
"Service": [
"ec2.amazonaws.com"
]
}
}
]
}
This configuration ensures that only the EC2 service can assume the role. After creating the role, verify its existence by searching for "EC2 S3 Access" in the AWS console.
Assigning the Role to an EC2 Instance
Next, using either User One or User Two, navigate to the EC2 dashboard and select an instance (for example, a web app instance). Follow these steps to assign the role:
- Choose the instance.
- Click on Actions.
- Select Security.
- Click Modify IAM Role.
- Search for "EC2 S3 Access" and assign it to the instance.
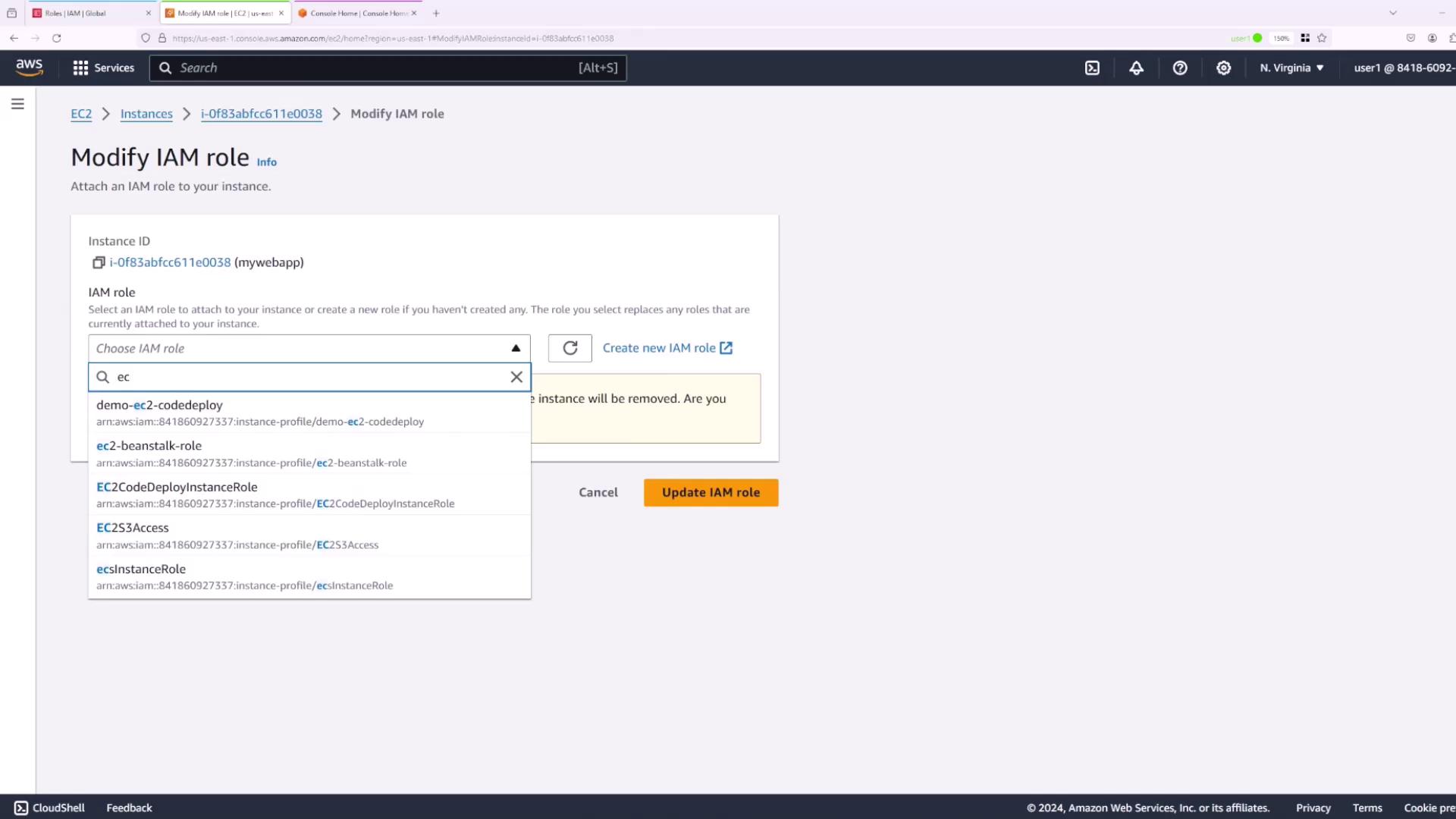
Important
When attempting this operation with User One, an error message appears stating that they are not authorized to perform the operation. This clearly demonstrates the necessity of having the proper IAM PassRole permission during role assignment.
A similar error will occur for User Two if the required permission hasn’t been granted.
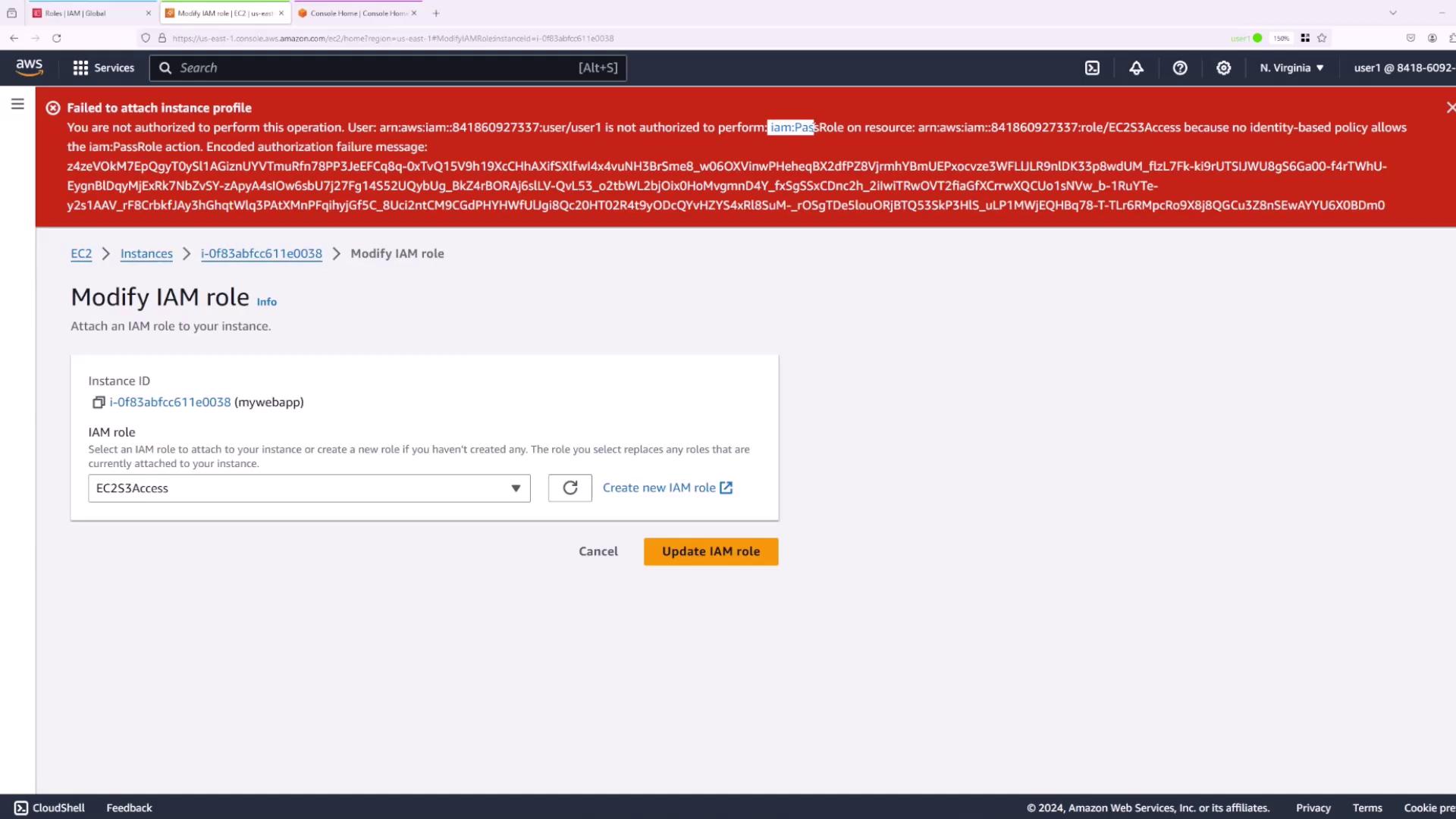
Granting IAM PassRole Permission to a User
To resolve permission issues for User Two, the IAM PassRole permission must be explicitly assigned. The inline policy below grants User Two permission to pass the EC2 S3 Access role (in addition to the iam:GetRole action, although only iam:PassRole is required):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:PassRole"
],
"Resource": "arn:aws:iam::841860927337:role/EC2S3Access"
}
]
}
To apply this policy:
- Log in as the Administrator.
- Navigate to the IAM console and select User Two.
- Click on Add permissions and choose Create inline policy.
- Switch to the JSON tab and paste the above policy.
- Provide a name for the policy (e.g., pass role EC2 S3 access) and create it.
Testing the Configuration
After assigning the policy, test the configuration with these steps:
- Log in as User One and attempt to modify the IAM role for an EC2 instance. The error should persist since User One does not have the required permissions.
- Log in as User Two and try again. When modifying the IAM role and selecting "EC2 S3 Access", the operation should now succeed.
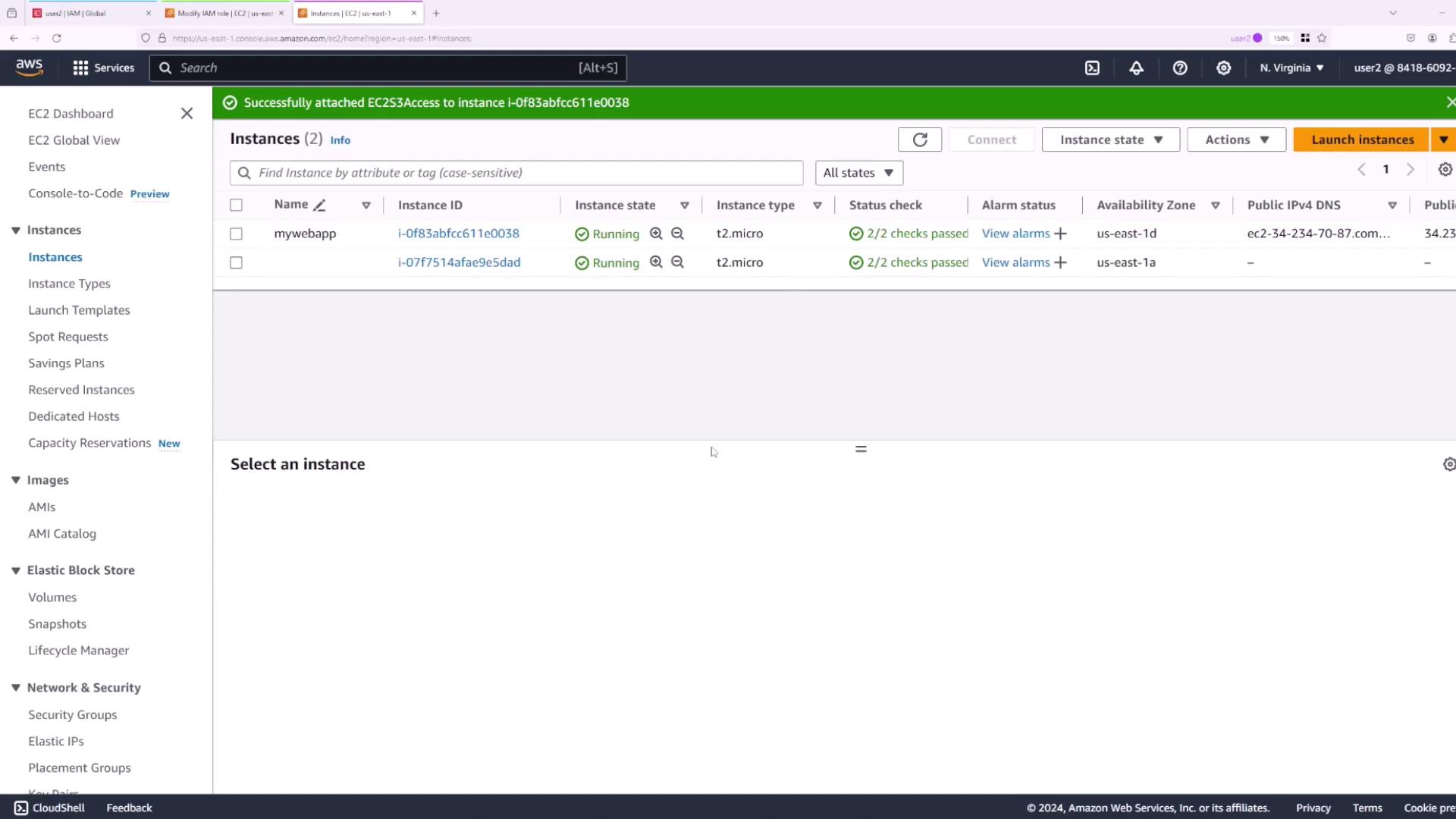
Summary
To enable a user to assign a role to an AWS service, ensure that the specific IAM PassRole permission is granted for that role. For clarity, here is the complete inline policy again:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:PassRole"
],
"Resource": "arn:aws:iam::841860927337:role/EC2S3Access"
}
]
}
Key Takeaway
Configuring the IAM PassRole permission correctly is crucial for enabling AWS services to operate securely and efficiently. Always ensure that only the required permissions are granted to reduce potential security risks.
Watch Video
Watch video content