AWS Certified Developer - Associate
Security
ACM Demo
In this lesson, we demonstrate how to work with AWS Certificate Manager (ACM) to generate an SSL certificate. This certificate enables HTTPS on your load balancer, ensuring secure traffic delivery to your EC2 instance running a basic nginx server. When accessing the application via HTTP (using a URL like http://), you see the default nginx HTML page with insecure traffic—even though the load balancer successfully forwards requests. By enabling HTTPS for your purchased domain, you improve security and performance.
We assume you have set up a hosted zone in Route 53 for the domain "KodeKloudDemo123". Once HTTPS traffic is sent to "KodeKloudDemo123", the SSL certificate secures the connection and forwards the traffic to your load balancer.
Region-Specific ACM Certificate
AWS Certificate Manager is region-specific. For example, if your load balancer is deployed in the Northern Virginia region, you must generate the certificate in that same region.
Requesting a Public Certificate
Follow these steps to request a public SSL certificate using ACM:
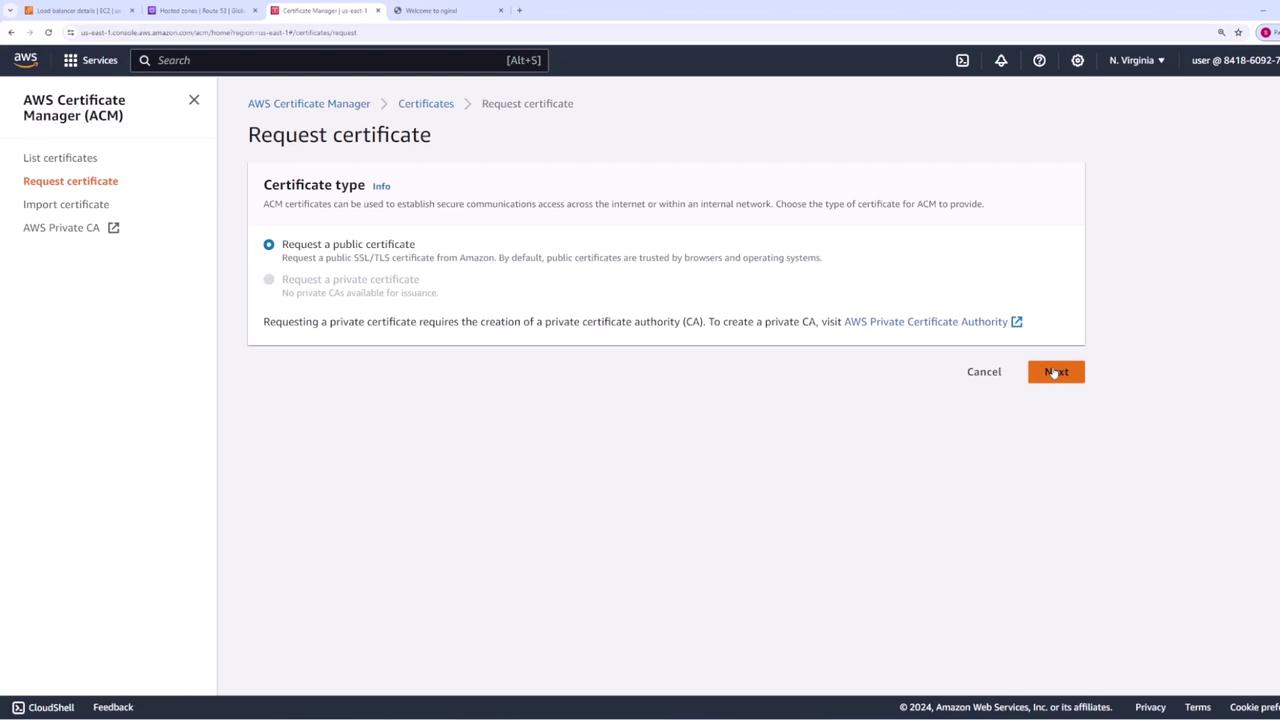
Open ACM in the AWS Management Console and select Request a certificate.
Choose Request a public certificate to obtain a certificate accessible on the internet.
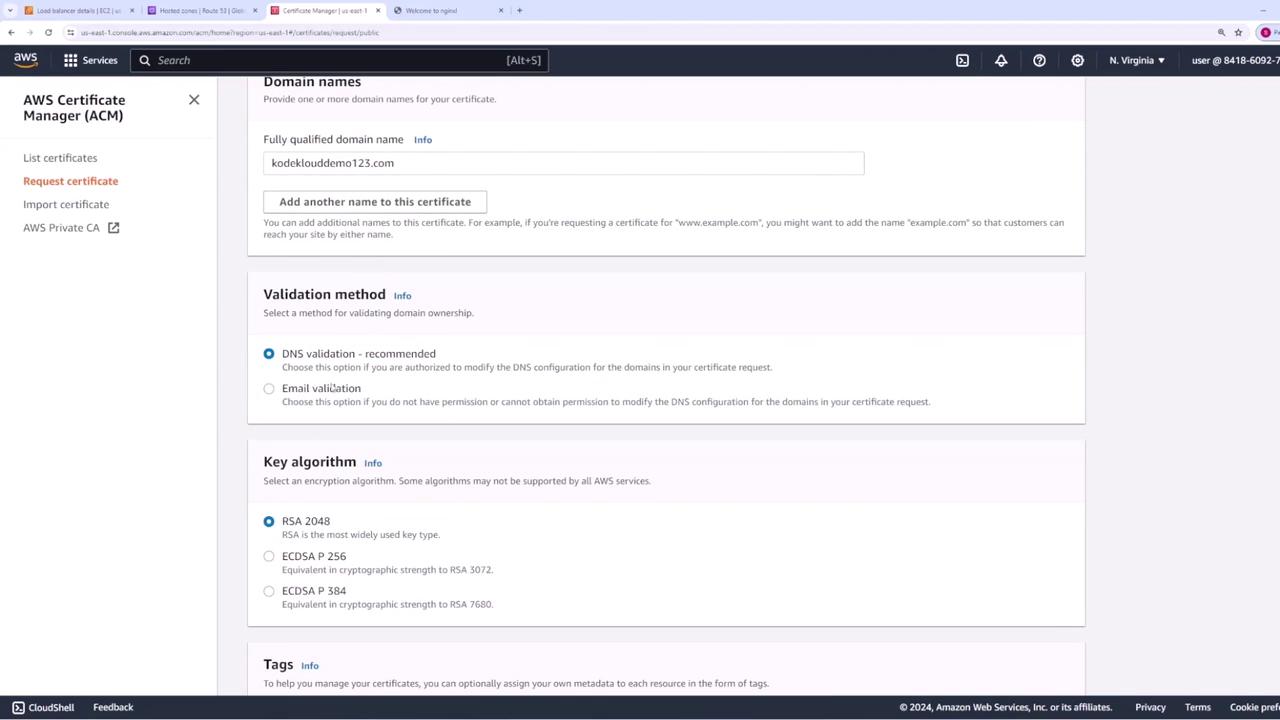
Click Next and add the domain names to be covered (for example, "kodeklouddemo123.com"). You may also add additional names such as "www.kodeklouddemo123.com" if required.
Select the validation method. You have two options:
- Email validation: An email is sent to the domain owner.
- DNS validation: You create a DNS record in Route 53.
For simplicity with AWS integration, we use DNS validation. Choose the key algorithm of your preference and then click Request.
ACM will now display your certificate along with its ID, type (Amazon issued), and a pending validation status.
Validating Domain Ownership
To validate your domain ownership:
- Create a CNAME record in Route 53. You can manually add the record with the provided values or use the integration button (available with DNS validation) to automatically create it.
- Refresh the ACM console. Once the certificate status changes from "Pending validation" to "Issued," your certificate is ready for use.
Configuring the Load Balancer for HTTPS
Next, assign the new SSL certificate to your load balancer by following these steps:
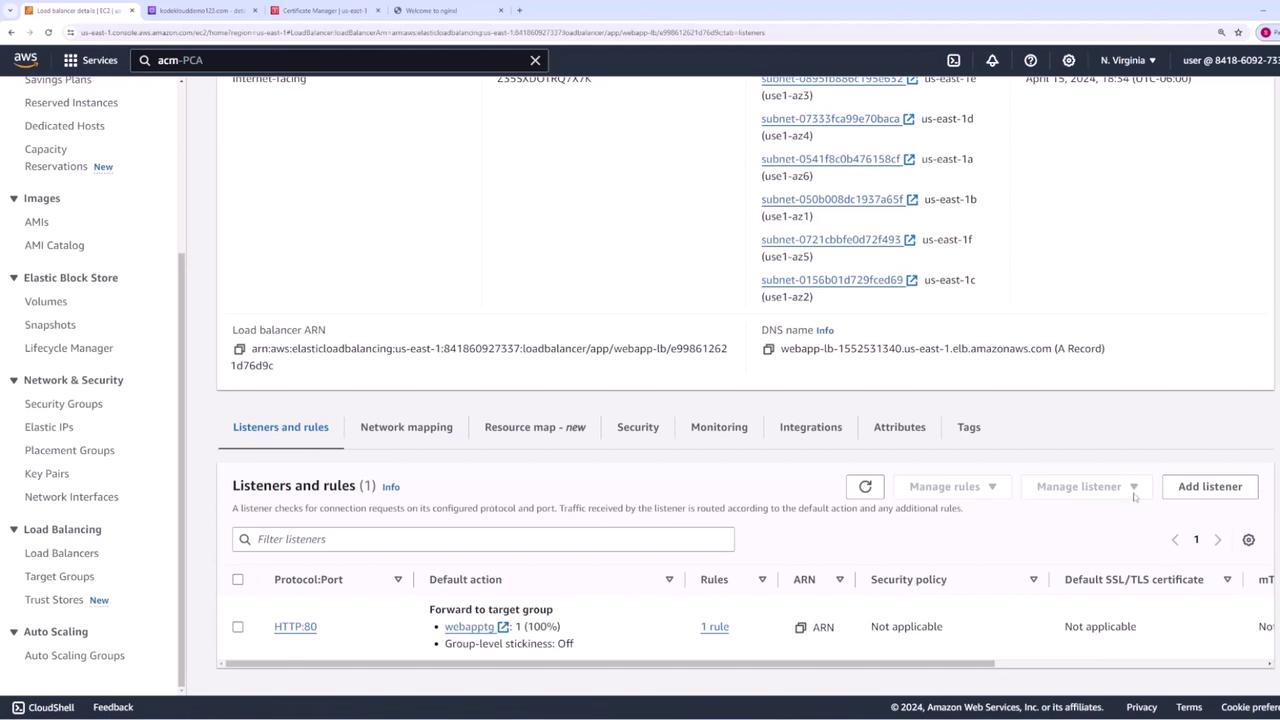
- Open the Load Balancer details in the AWS Management Console.
- Your load balancer currently has an HTTP listener on port 80. Add a new listener for HTTPS on port 443.
- In the HTTPS listener configuration, forward the traffic to the same target group as the HTTP listener.
- Under secure listener settings, choose ACM as the source for the SSL certificate, then select the certificate you created.
- Save the configuration.
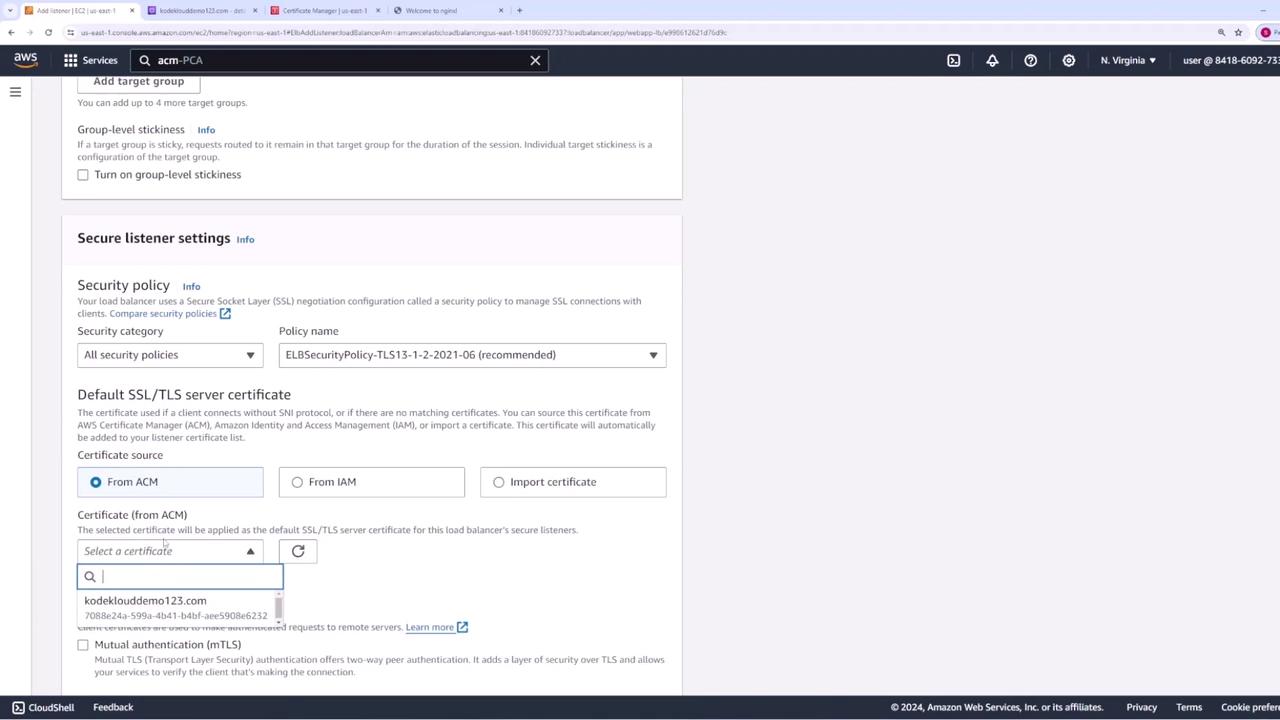
With the HTTPS listener correctly configured, your load balancer now supports secure traffic.
Updating DNS Records in Route 53
To route traffic for "KodeKloudDemo123.com" to your load balancer:
- Create a new A record using simple routing in Route 53.
- Set the record name to your root domain and select Application Load Balancer as the endpoint.
- Choose the appropriate AWS region and select your load balancer.
- Save the record.
This configuration ensures that both HTTP and HTTPS traffic are directed to your load balancer.
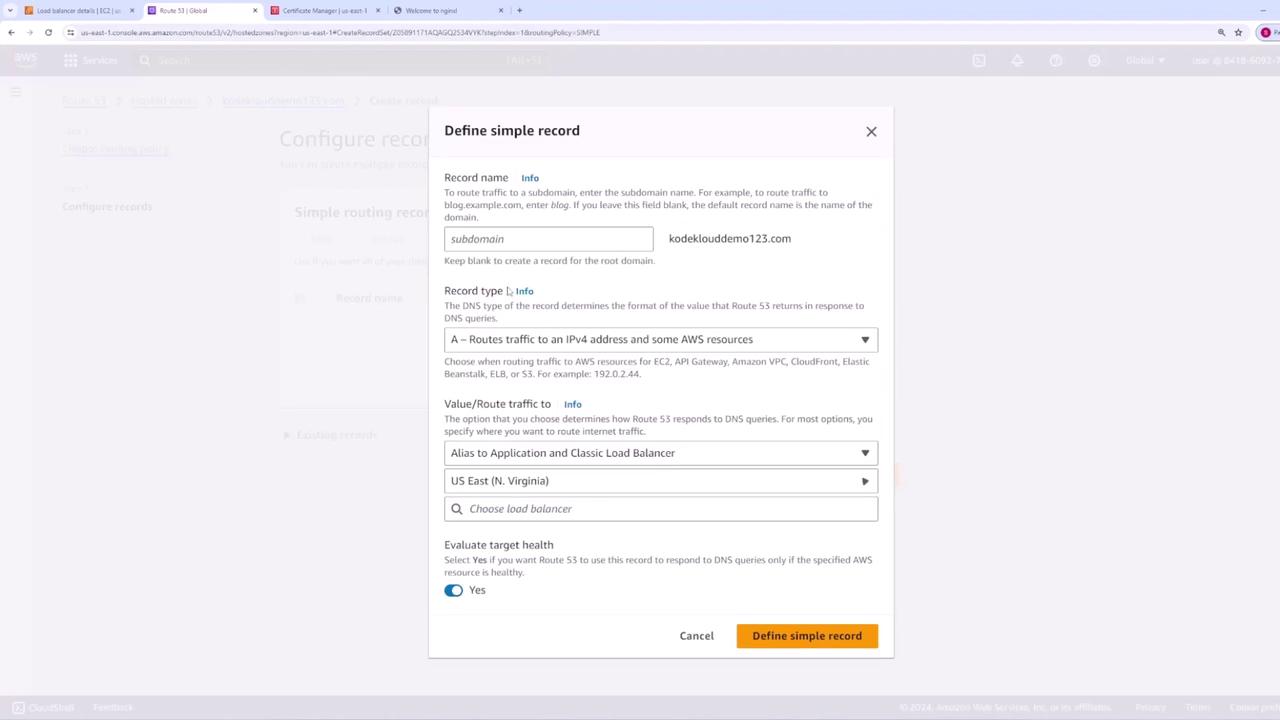
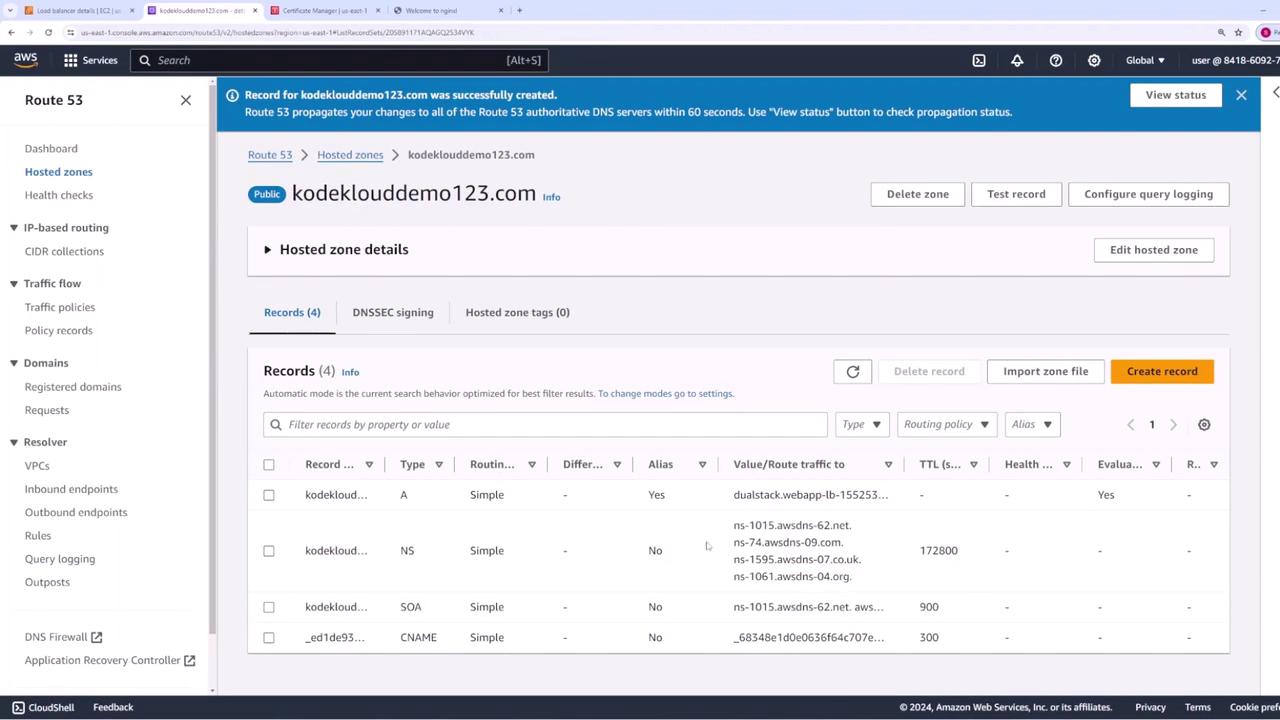
Now, when you access your domain via HTTPS, the load balancer will use the assigned SSL certificate to secure the connection.
Testing and Verifying the Certificate
To confirm your SSL certificate is active:
- Open your browser and navigate to https://kodeklouddemo123.com.
- Verify that the web application loads securely over HTTPS.
- Click the padlock icon in the browser address bar to inspect the certificate details, ensuring the common name matches your domain and checking the validity dates and encryption settings.
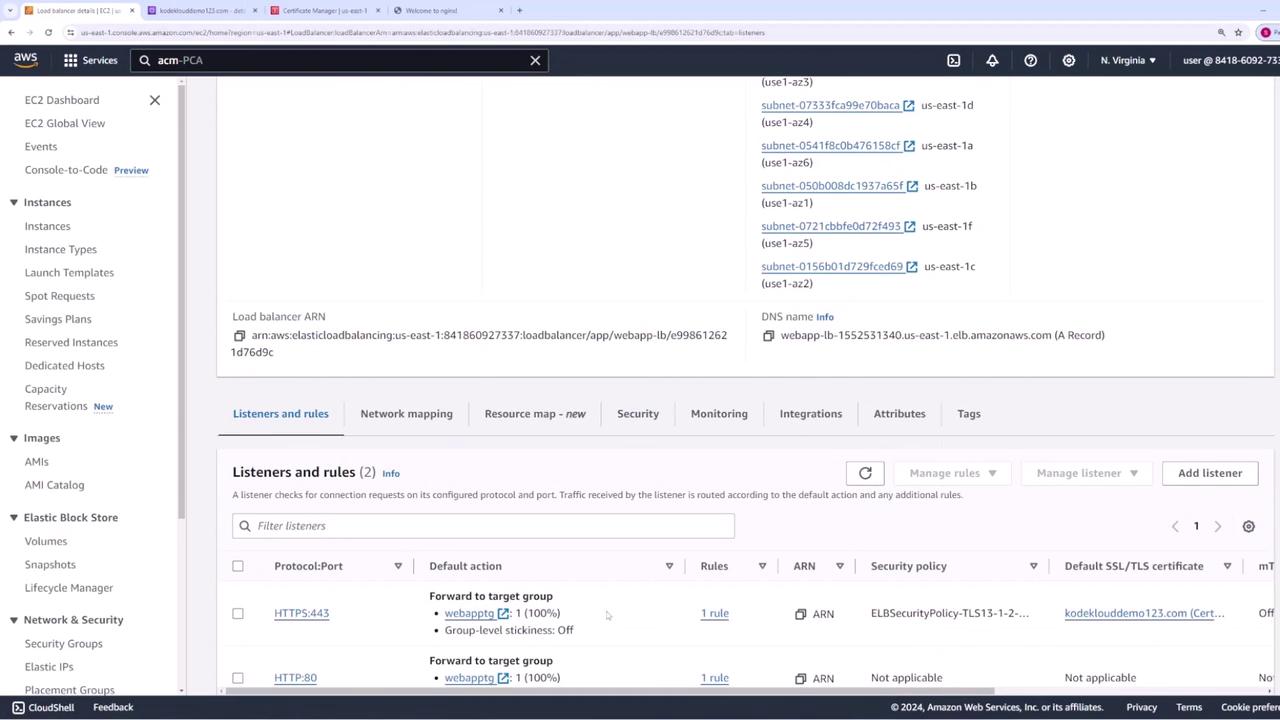
Using ACM with CloudFront
You can also assign your ACM SSL certificate to a CloudFront distribution. In this scenario, you initially access your web application using the CloudFront-provided domain name. To enhance your setup with your custom domain "KodeKloudDemo123.com" secured by an ACM certificate, follow these steps.
CloudFront Certificate Region Requirement
Remember that CloudFront requires the SSL certificate to be created in the US East (N. Virginia) region. If your certificate was created in another region, you must issue a new one in US East 1.
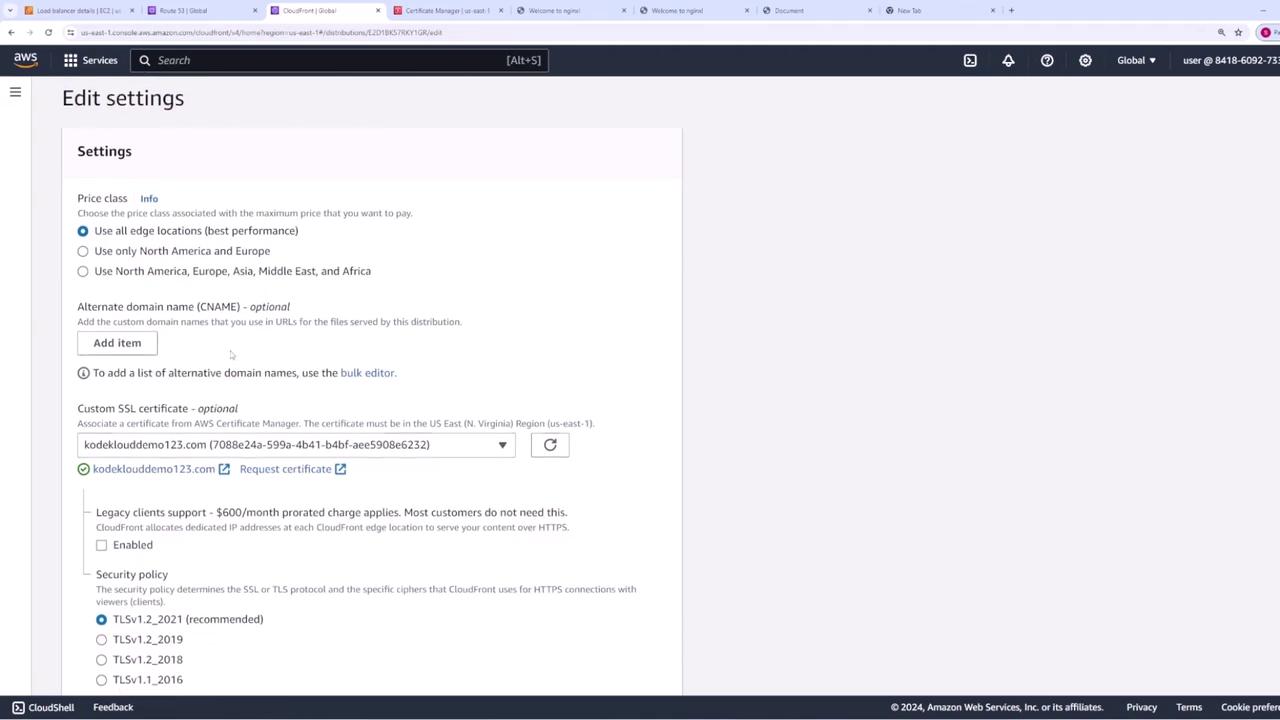
- Open your CloudFront distribution settings and click General then Edit.
- Under Custom SSL Certificate, CloudFront will display certificates available from US East (N. Virginia). Select the desired certificate.
- (Optionally) Choose the appropriate TLS versions—the default settings are typically sufficient—and then save your changes.
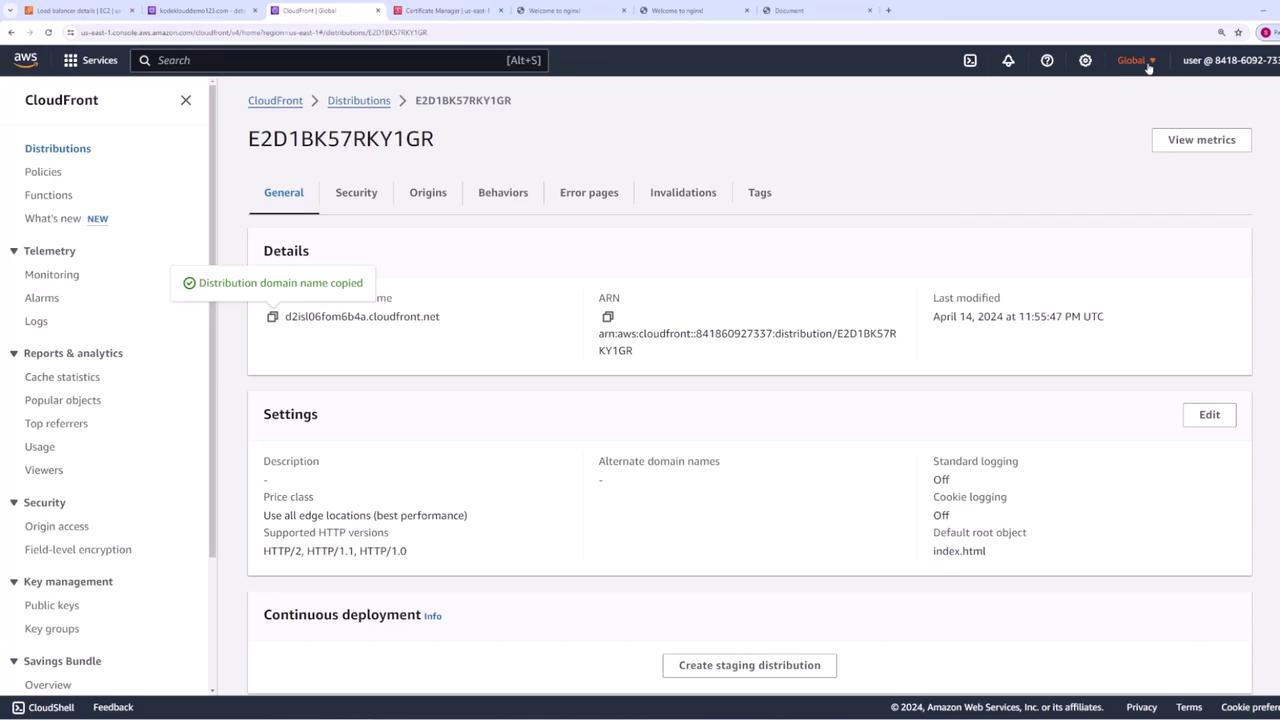
At this point, your CloudFront distribution is associated with the ACM certificate. However, you must update your DNS settings in Route 53 to direct traffic to CloudFront.
Updating Route 53 for CloudFront
- Delete the previous A record pointing to your load balancer.
- Create a new A record with simple routing for "KodeKloudDemo123.com".
- Under Alias to CloudFront distribution, search for and select your CloudFront distribution.
If your CloudFront distribution does not appear, verify that you have added "KodeKloudDemo123.com" as an Alternate Domain Name in your CloudFront settings. Wait a moment, then refresh the Route 53 console.
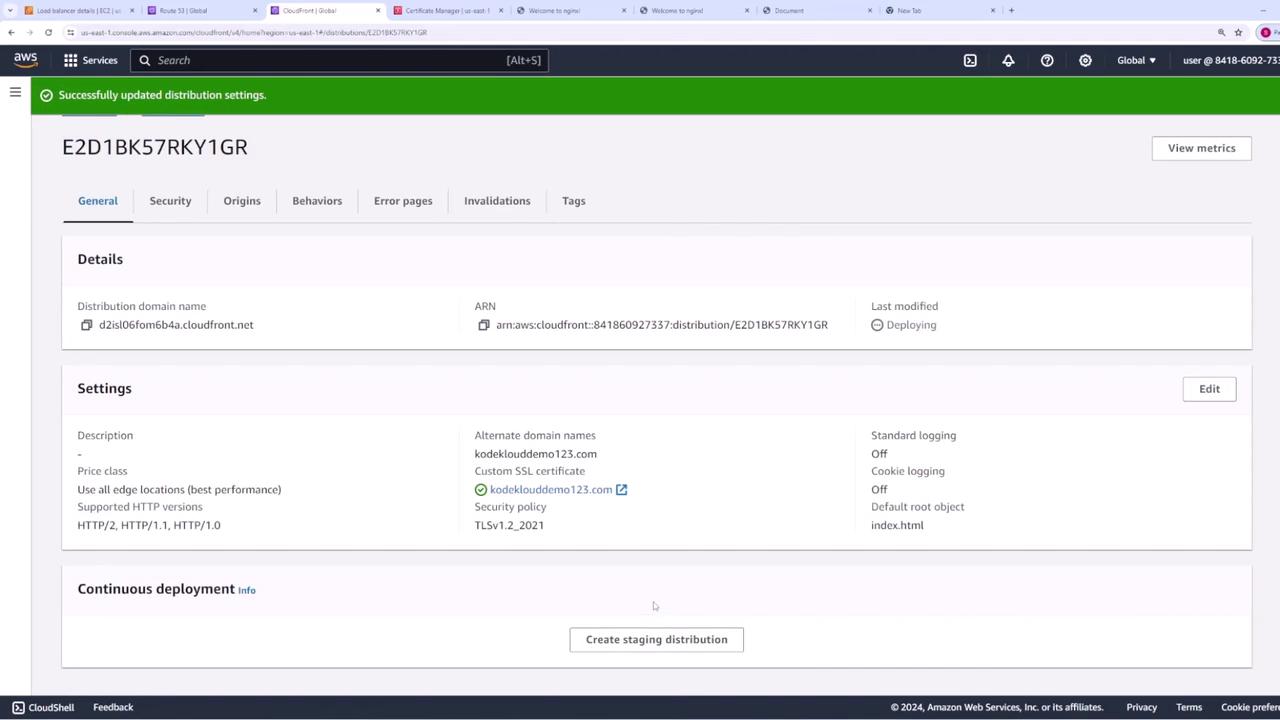
When the new DNS record is active, accessing "KodeKloudDemo123.com" will forward traffic to your CloudFront distribution over HTTPS.
Final Verification
To complete your configuration:
- Open your browser and navigate to https://kodekloudDemo123.com.
- Verify that the CloudFront-hosted web application loads securely using the ACM SSL certificate.
- Inspect the certificate by clicking the padlock icon in your browser to ensure all details are correct.
This concludes our lesson on generating and assigning SSL certificates using AWS Certificate Manager with both a load balancer and a CloudFront distribution. Enjoy the enhanced security and functionality provided by these AWS services, and see you in the next lesson!
Watch Video
Watch video content