Elastic Block Store (EBS)
EBS (Elastic Block Store) provides block storage by dividing data into blocks, each with a unique identifier. The operating system views these blocks as a single volume. Importantly, you can both boot and mount from block storage. This capability makes EBS unique as the only storage option that can be used to boot an operating system. EBS volumes are created within a single Availability Zone (AZ). To transfer data to another AZ, you must generate an EBS snapshot and then create a new volume from that snapshot in the target AZ. Familiarize yourself with the various EBS volume types—general purpose, provisioned IOPS, and magnetic (HDD)—to choose the optimal option based on your performance and cost requirements. Billing is based on the number of gigabytes provisioned each month.
Elastic File System (EFS)
Amazon EFS is a fully managed file system service that supports the NFSv4 protocol. This means applications using NFSv4 can integrate seamlessly without modifications. Note that EFS is supported only on Linux-based EC2 instances. One of its key advantages is the ability to mount the same file system across multiple EC2 instances, providing shared access to data. When setting up an EFS file system, you must provision mount targets. Each mount target is assigned an IP address from the subnet in which it is deployed, enabling EC2 instances to connect to the file system. EFS offers two main storage classes—Standard and One Zone—and supports two performance modes: general purpose and elastic throughput. Unlike EBS, EFS volumes are designed solely for mounting and cannot be used to boot an operating system.
Simple Storage Service (S3)
Amazon S3 is a scalable object storage service recognized for its high availability, robust security, and excellent performance. It is ideal for use cases such as hosting static websites, storing media files, or maintaining logs. S3 organizes data as a flat structure instead of a directory hierarchy. Keep in mind that S3 objects cannot be booted or mounted like traditional operating system volumes. An S3 object comprises two parts:- The key: a unique identifier for the file.
- The value: the content of the file.
S3 Storage Classes and Versioning
S3 offers a variety of storage classes that cater to different access patterns, resiliency, and cost requirements. When uploading an object, set its storage class by including the x-amz-storage-class header. Moreover, you can later modify an object’s storage class as needed.Versioning in S3
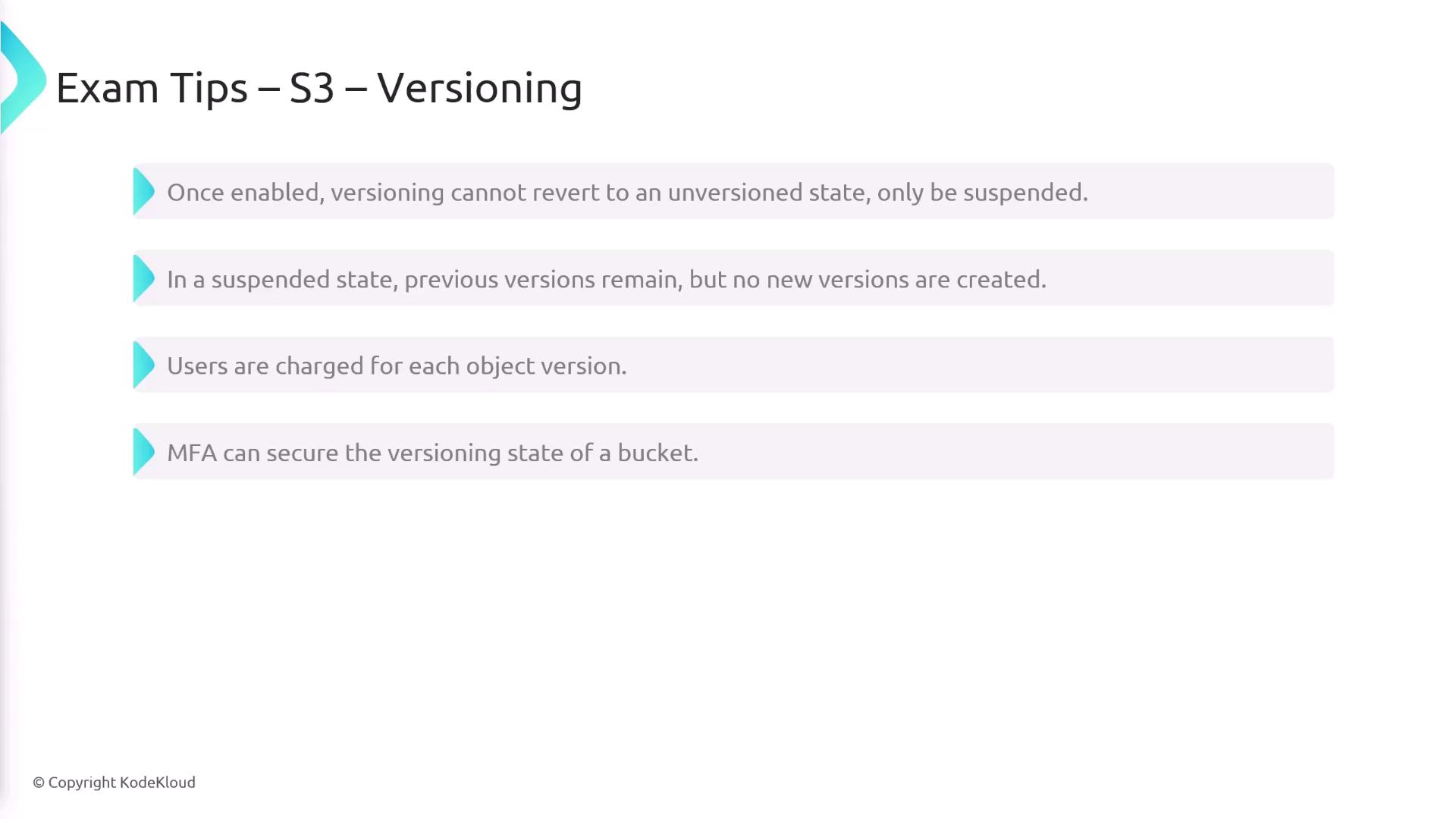
Versioning allows you to preserve, retrieve, and restore every version of an object in an S3 bucket. With versioning enabled, each update to an object creates a new version, helping you recover older versions if needed. Note that versioning is disabled by default and must be activated at the bucket level—not per object. Buckets can have three versioning states:- Unversioned: Versioning is not enabled.
- Versioning enabled: New versions of objects are created upon updates.
- Versioning suspended: Existing versions are maintained, but new updates will not produce additional versions.
Once enabled, versioning cannot be completely turned off; it can only be suspended. Keep in mind that charges apply for every object version, so multiple versions of large files can lead to increased costs.


S3 Bucket Policies and Encryption
Bucket policies in S3 allow you to define who can access specific buckets and what operations are permitted. These policies contain key parameters:- Principal: Specifies who the policy applies to.
- Resource: Defines the bucket and its objects.
- Effect: Indicates whether the action is allowed or denied.
- Action: Lists the permissible or prohibited operations.
S3 Encryption Options
-
Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3):
AWS manages the encryption keys automatically. You do not have access to these keys or the ability to modify any settings. -
Server-Side Encryption with Customer-Provided Keys (SSE-C):
You generate and manage your own encryption keys. These keys must be provided during the upload process for S3 to encrypt your objects. -
Server-Side Encryption with AWS Key Management Service Keys (SSE-KMS):
Manage and create your own keys using AWS KMS. S3 integrates with KMS so you can establish custom access policies for encryption and decryption.

Pre-signed URLs in S3
Pre-signed URLs offer temporary access to S3 objects without requiring AWS credentials. When you generate a pre-signed URL, it carries the access permissions of its creator. Consequently, anyone using the URL will have the same access rights as the original user. If the creator does not have permissions on the target object, the URL will not function for others.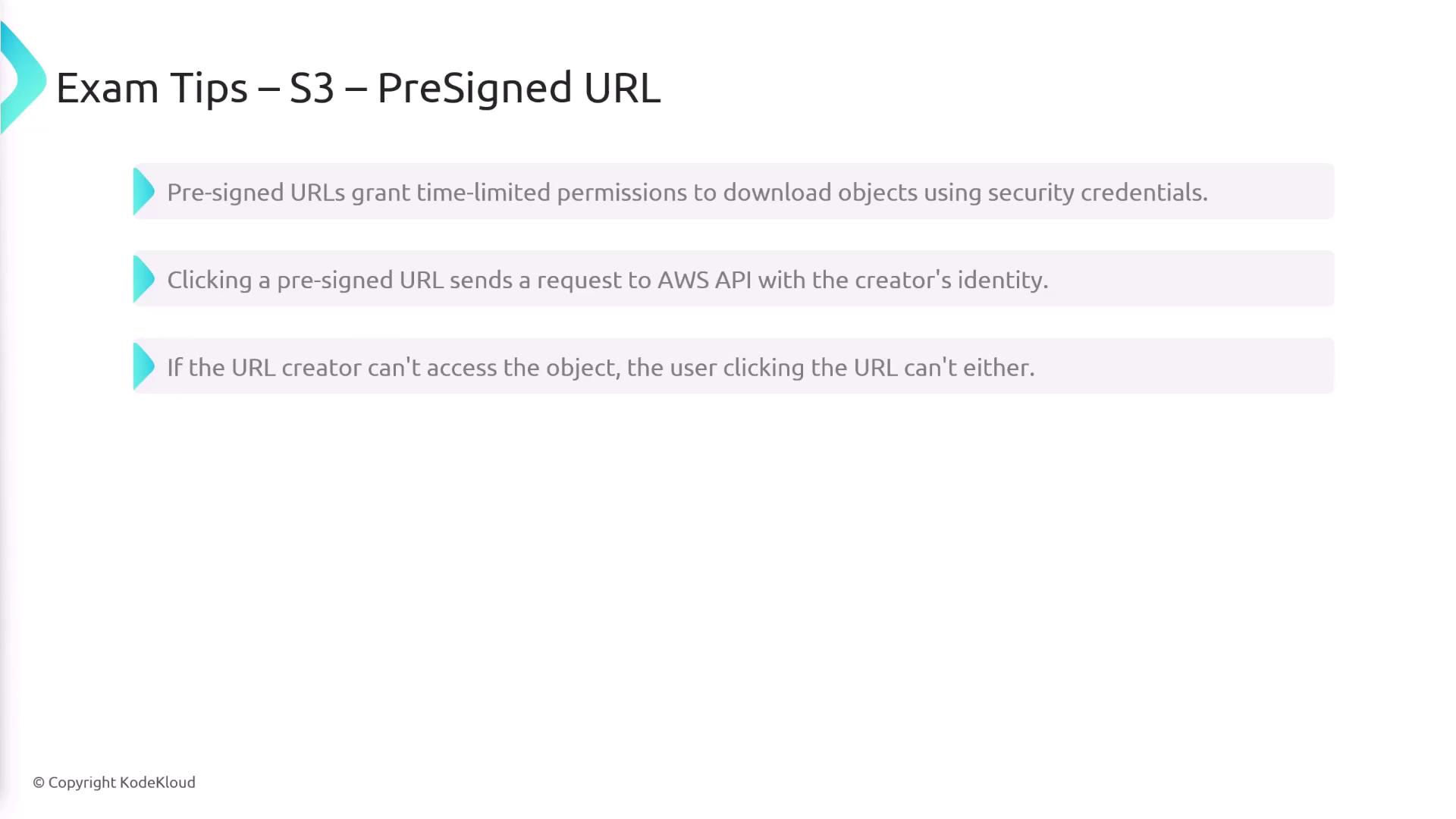
S3 Access Points
Access points simplify S3 bucket permission management by allowing each group or user to have a dedicated endpoint with its own unique ARN. Instead of accessing the bucket through its main URL, users connect via these access point URLs. This enables granular policy management and the possibility to restrict access to specific VPCs.Understanding access points is essential for managing complex S3 environments, especially when different teams or applications require distinct access policies.