Simplifying Access Management
Managing an S3 bucket that supports multiple groups, users, and roles can quickly become complex when different levels of access are required. For instance, developers may need permissions for certain folders, the infrastructure team might require comprehensive access, and the legal team could be limited to read-only access. Instead of managing a convoluted bucket policy for every principal and object, you can create individual access points with unique ARNs. Each access point behaves like an independent S3 bucket, enabling you to delegate policies more efficiently. When developers need to access objects, they use their specific access point ARN instead of the generic bucket ARN. This method shifts policy management closer to the relevant teams and simplifies security for your S3 buckets.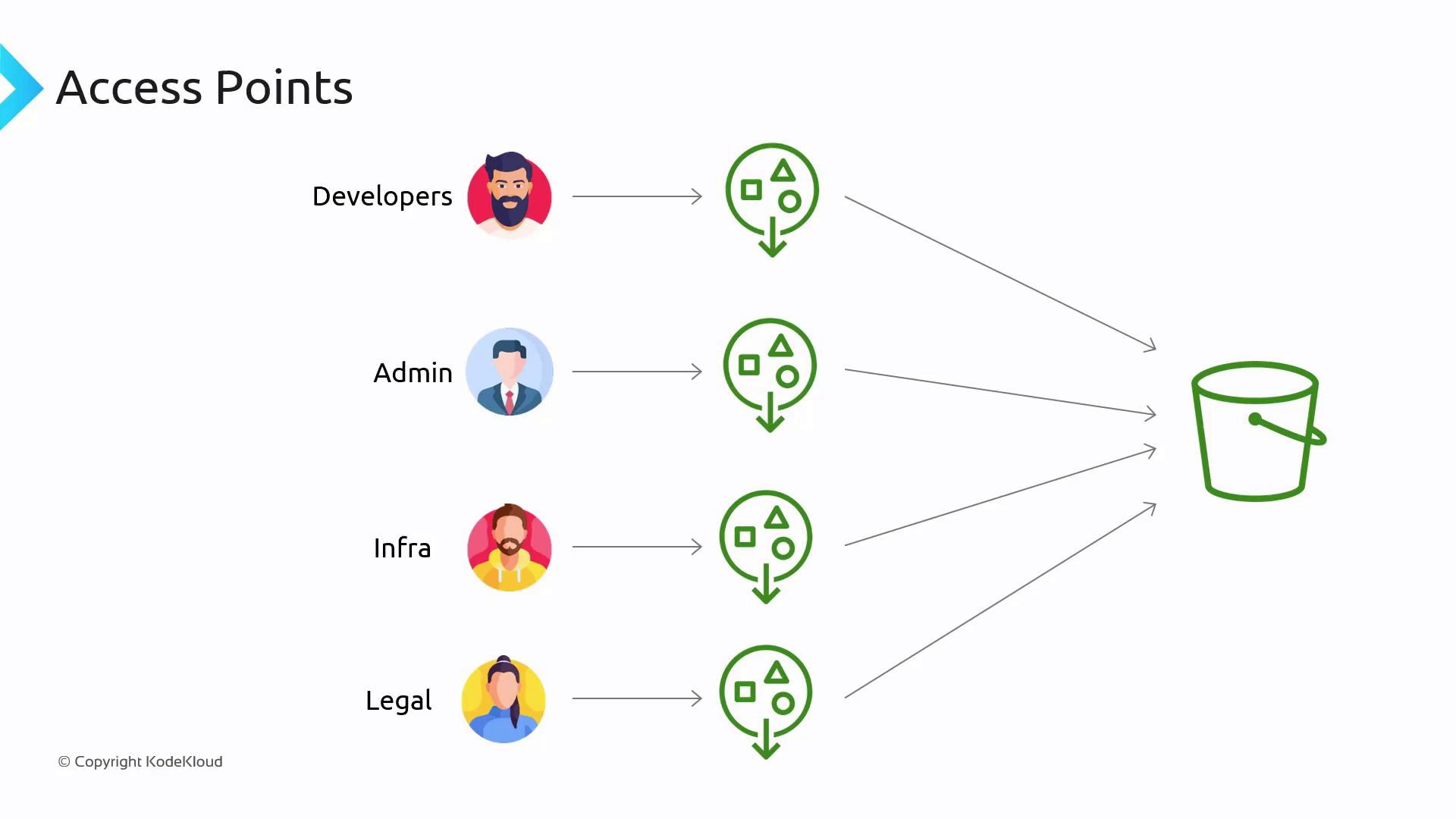
Restricting Access with VPC Endpoints
Another key benefit of using access points is the ability to restrict bucket access based on Virtual Private Cloud (VPC) endpoints. By associating VPC endpoints with an access point, you ensure that only devices within a specified VPC, such as EC2 instances, can interact with the S3 bucket. This adds an additional layer of security, preventing unauthorized access from outside the designated network.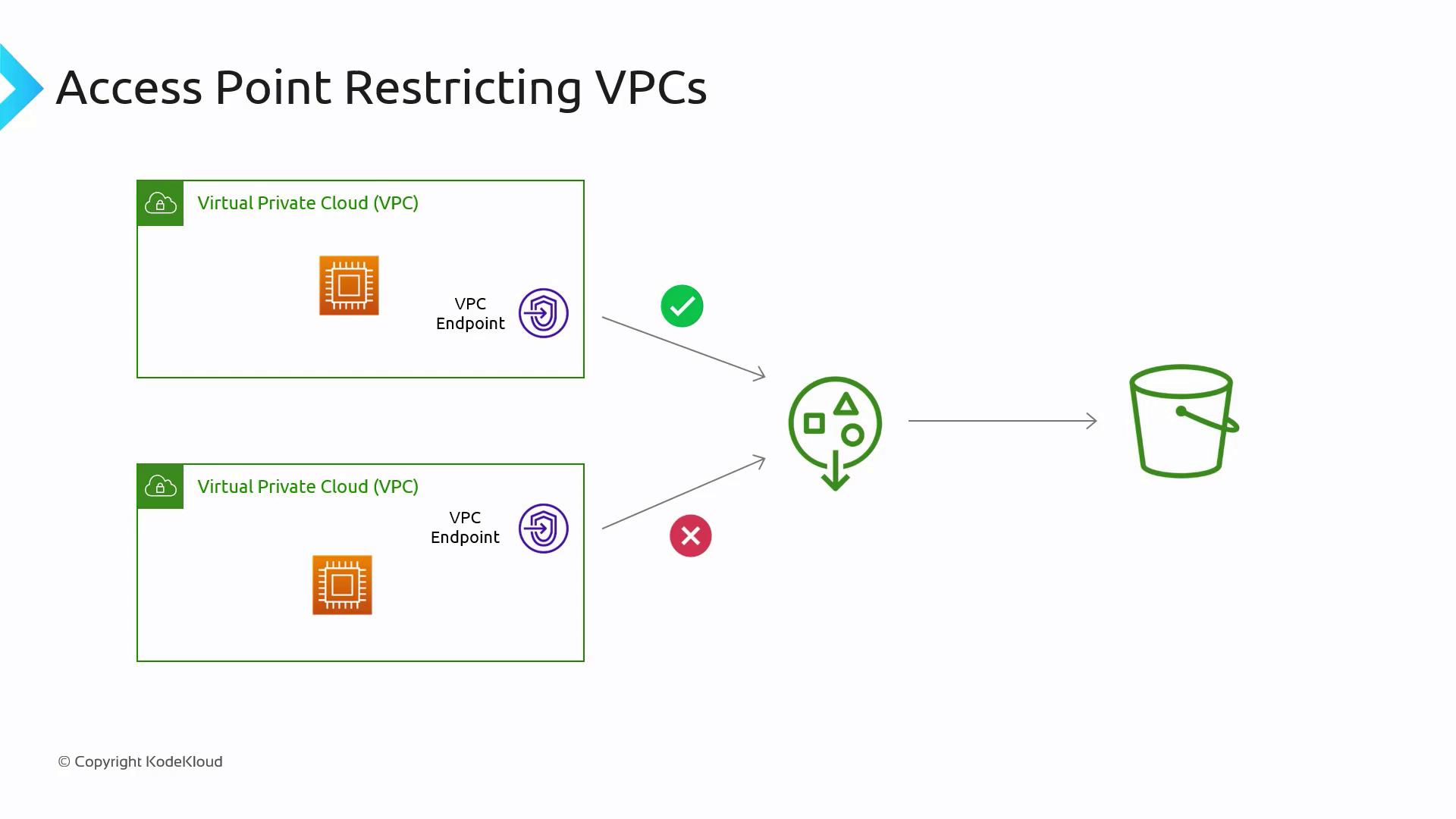
For added security, regularly review and update the VPC endpoint associations to ensure only approved networks can access your S3 buckets.
Delegating Policy Management
Access point policies are defined at the access point level. However, note that current limitations require the corresponding policies to be duplicated in the bucket policy. This duplication can make management cumbersome, especially as policies evolve. A more scalable approach is to delegate policy management by configuring a central bucket policy that defers further access control decisions to the respective access points. This approach eliminates the need for constant updates to the bucket policy and centralizes control within each access point.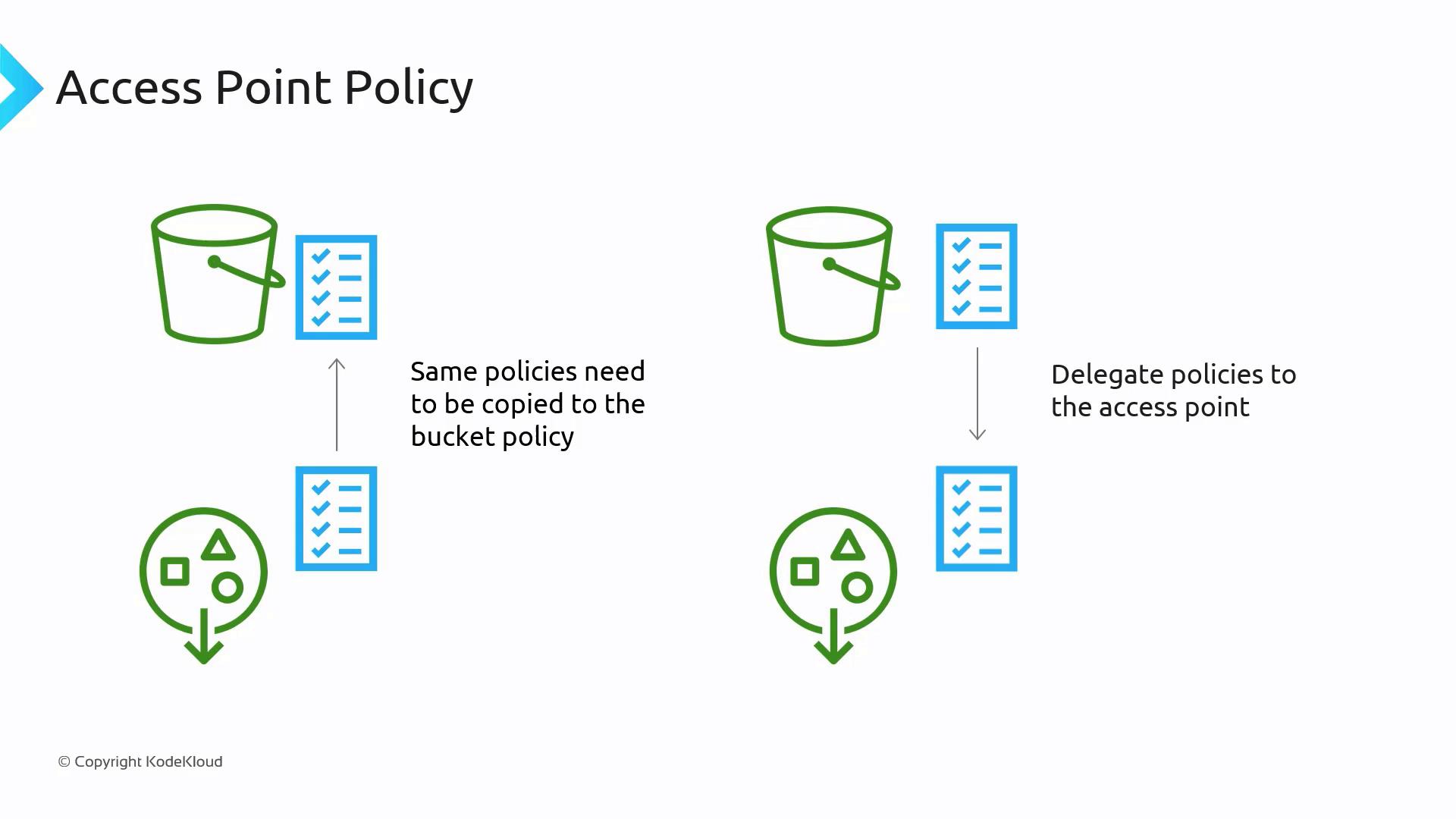
Remember that your access points will not work as intended unless the corresponding bucket policy includes the necessary permissions. Always verify that the bucket policy reflects any changes made at the access point level.
Key Benefits of Using S3 Access Points
Using S3 access points offers several advantages:- Simplifies the management of complex access policies.
- Provides each group or user with a dedicated access point, functioning as a personalized view into the S3 bucket.
- Utilizes unique ARNs for each access point, allowing users to interact with buckets through specific access point URLs.
- Enables applying targeted policies directly to individual access points, reducing the complexity of bucket-level policy management.
- Restricts access to devices within specific VPCs by associating VPC endpoints with access points.