EKS Cluster Components
An EKS cluster has two primary parts:| Component | Ownership | Role |
|---|---|---|
| Control Plane | AWS-managed | API server and etcd—with an AWS-managed load balancer endpoint. |
| Nodes & Pods | Your AWS account | Worker nodes (EC2) and pods, communicating via an ENI in your VPC. |
kubectl get nodes) against the public control plane endpoint. Nodes assume IAM roles to authenticate to the API server.
Authentication Flow
When you runkubectl get nodes, EKS performs:
- Invocation of the AWS IAM Authenticator plugin to fetch a token.
kubectlsends that token to the public API server endpoint.- The AWS-managed load balancer forwards the request to the API server.
- The API server verifies the token with AWS IAM and executes the request.
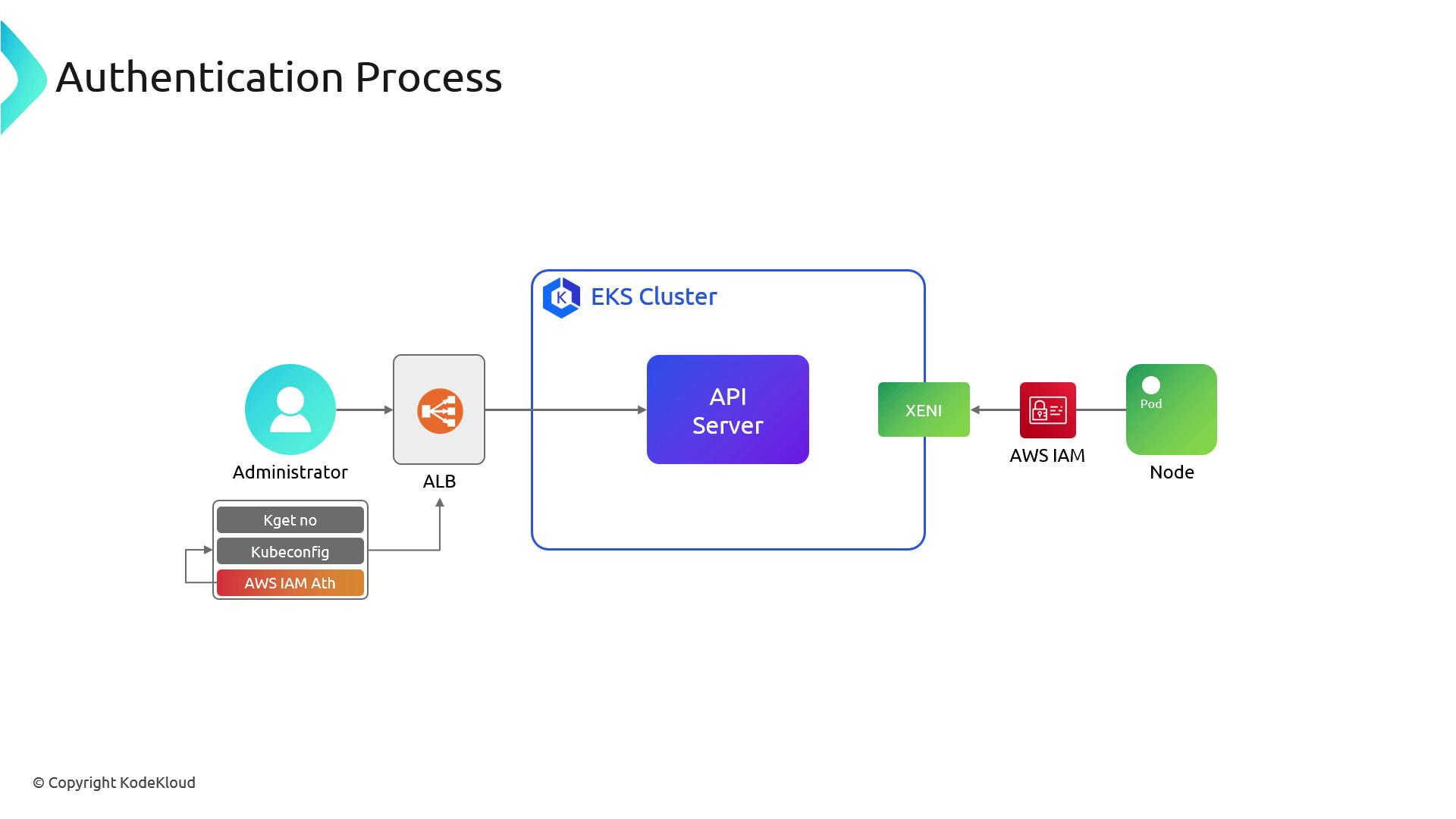
Although the endpoint is publicly reachable, AWS IAM verification ensures only valid IAM principals and node roles can access the API.
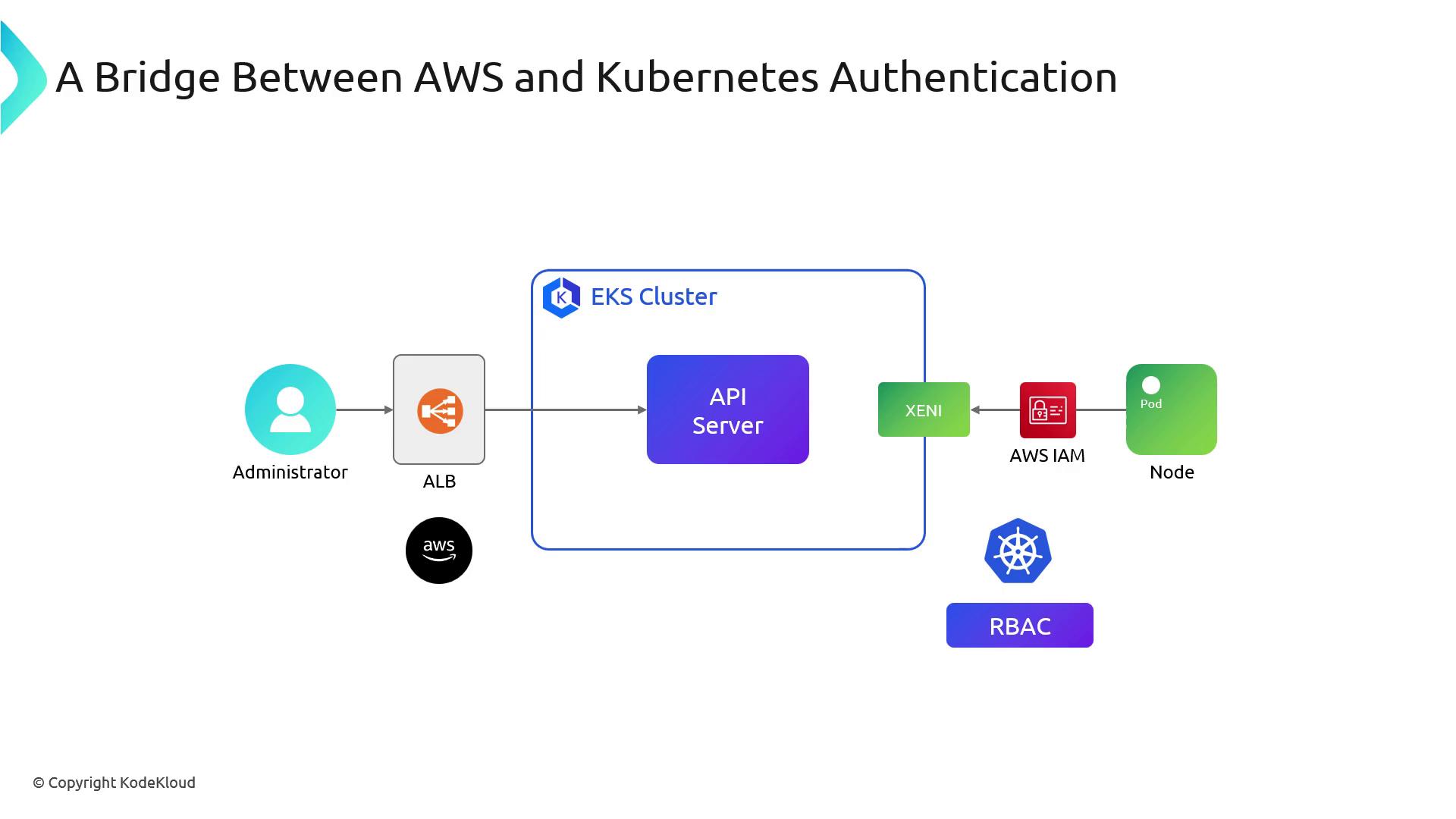
Bridging AWS IAM and Kubernetes RBAC
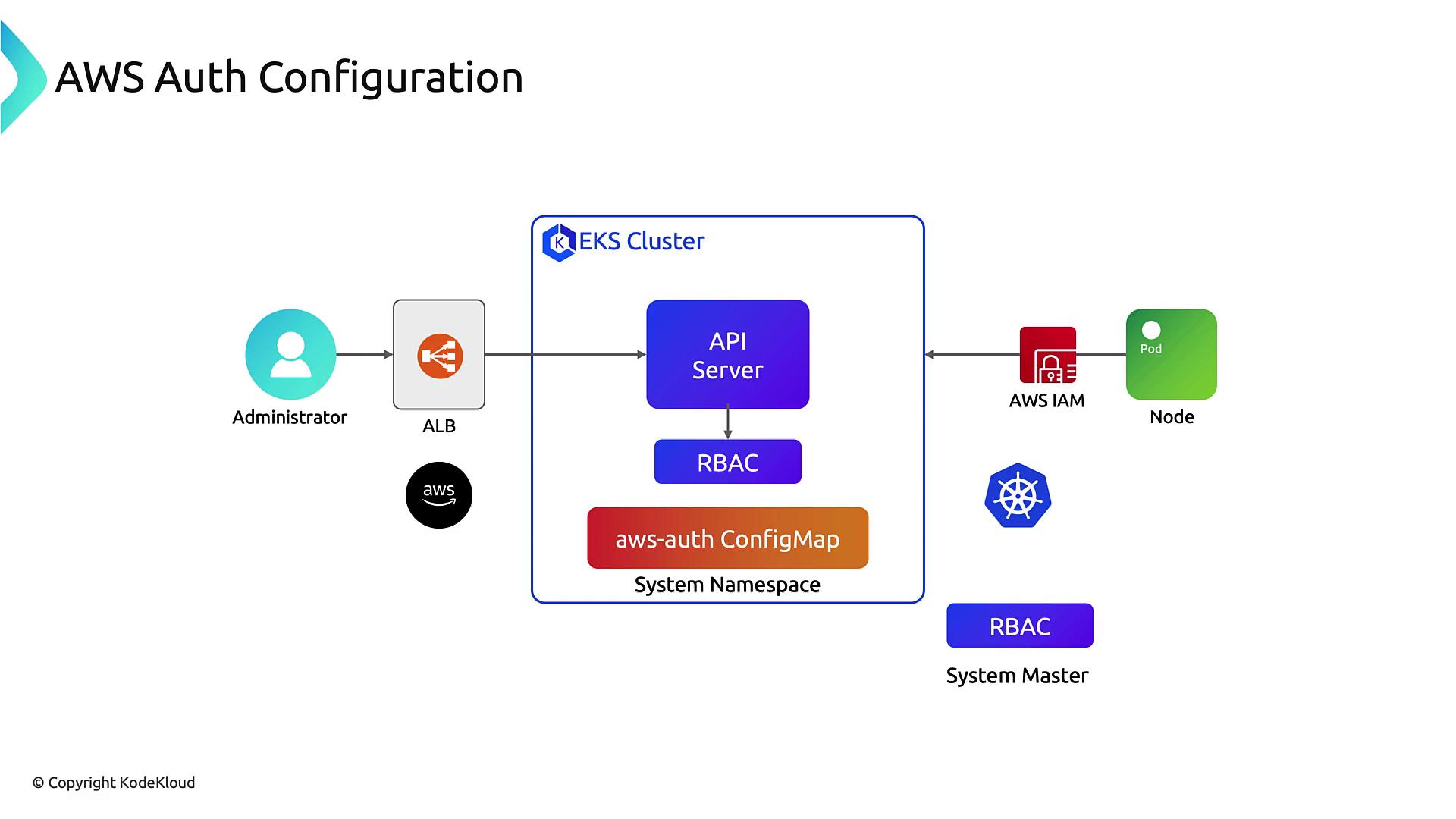
Inside Kubernetes, Role-Based Access Control (RBAC) controls permissions. EKS originally bridged IAM identities to RBAC roles via theaws-auth ConfigMap:
aws-auth ConfigMap
Below is a sampleaws-auth ConfigMap used to map IAM roles and users to Kubernetes groups:
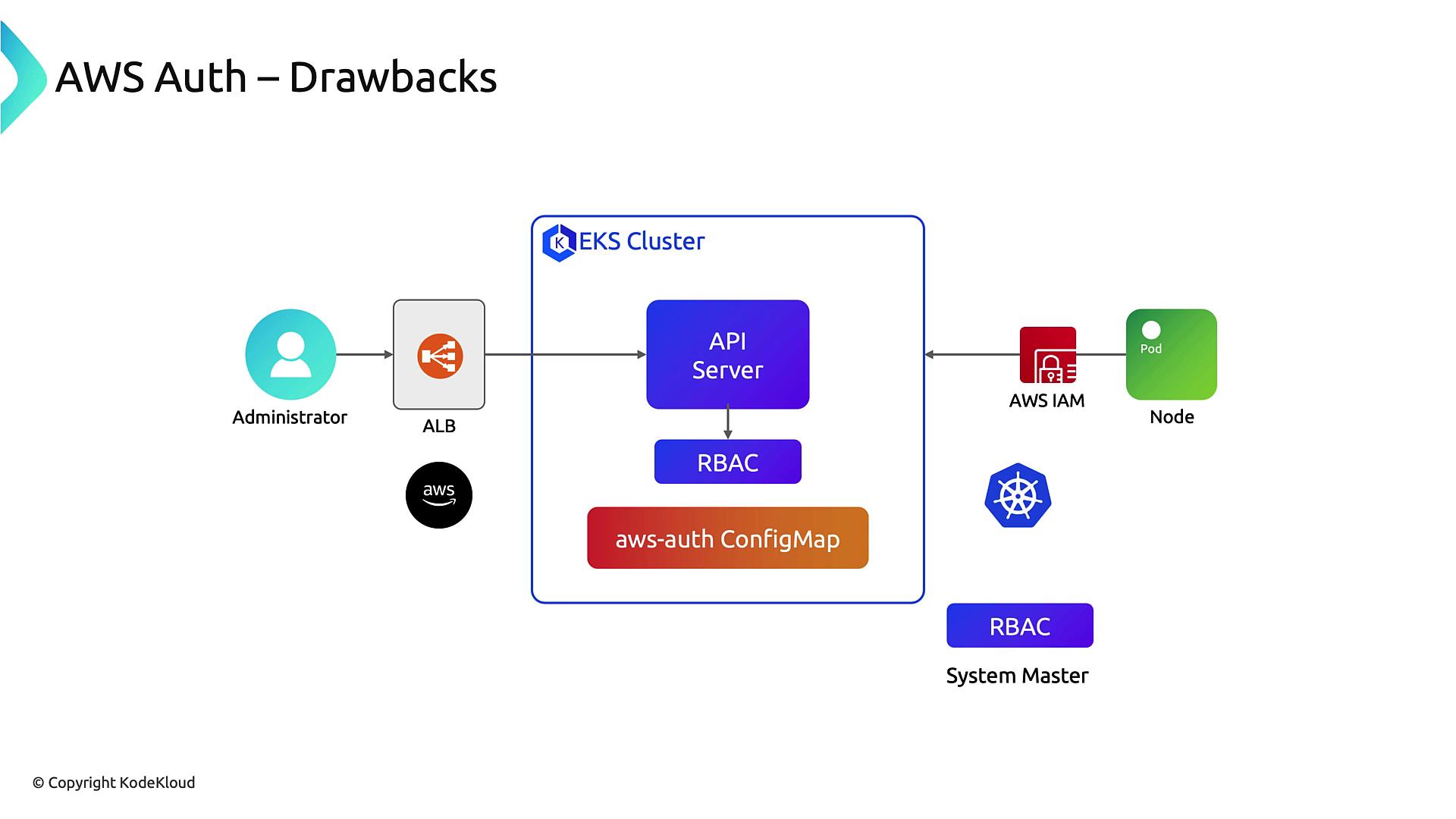
Drawbacks of the aws-auth ConfigMap
| Drawback | Impact |
|---|---|
| Permanent Creator Admin | The cluster creator gains unrevokable system:masters privileges. |
| Deleted IAM Identity | Removing the IAM user/role locks out admin access unless AWS Support intervenes. |
| ConfigMap Syntax Errors | A malformed YAML can prevent any admin from modifying access. |
| Manual Automation | Scripts or CI/CD pipelines must validate changes to avoid downtime. |
Relying on a free-form ConfigMap for critical access control can lead to accidental lockouts and complex recovery procedures.
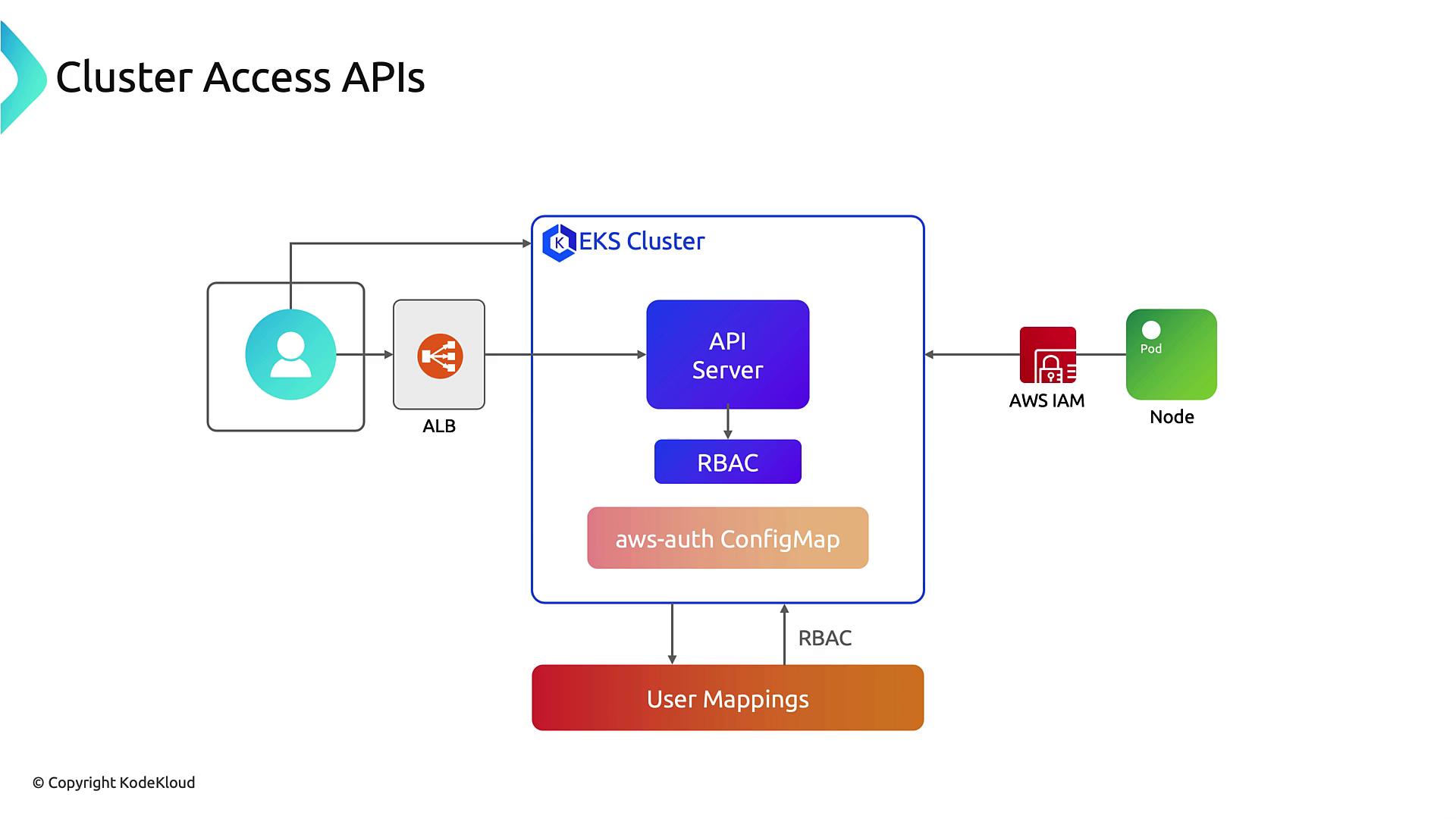
EKS Cluster Access APIs
AWS now offers native Cluster Access APIs, which deprecate the in-clusteraws-auth ConfigMap in favor of declarative IAM-to-RBAC mappings via the EKS control plane API:
- Manage IAM identity mappings directly through the EKS API.
- Offload access control logic from your cluster into the EKS service.
- Assign multiple IAM roles/users as cluster administrators without recreating the cluster.
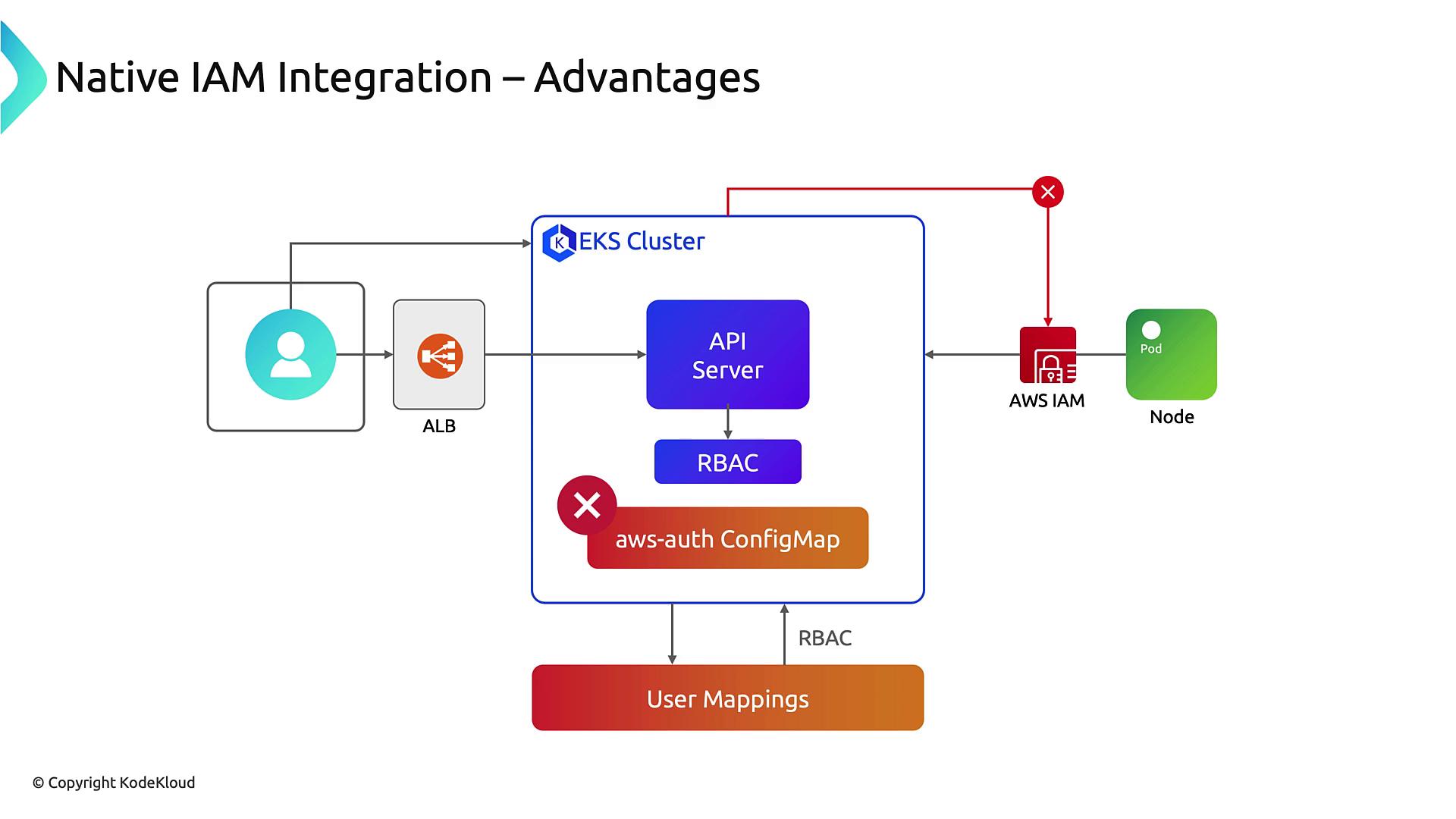
Benefits of Native IAM Integration
- Centralizes IAM and RBAC management within the EKS API.
- Separates cluster provisioning from administration responsibilities.
- Eliminates risk of lockouts caused by invalid ConfigMap edits.
- Enables safer automation and declarative access controls.
Summary
- EKS control plane exposes a public API endpoint, protected by AWS IAM authentication.
- Kubernetes RBAC enforces fine-grained permissions inside the cluster.
- The
aws-authConfigMap is legacy; new clusters should use the Cluster Access APIs. - Upgrade your tooling (Terraform, AWS SDKs, eksctl) to manage access declaratively.