What Are EKS Add-ons?
EKS add-ons are extensions that AWS maintains for compatibility with your cluster’s Kubernetes version. They include:- Amazon VPC CNI: Integrates Kubernetes pod networking directly with your VPC.
- CoreDNS: Provides DNS resolution for in-cluster services.
- kube-proxy: Manages cluster networking rules.
Inspecting Default Add-ons in the Console
Let’s explore an EKS cluster via the AWS Management Console. Here’s my cluster named kodekloud, running Kubernetes v1.29. The Amazon VPC CNI appears automatically under the Add-ons section.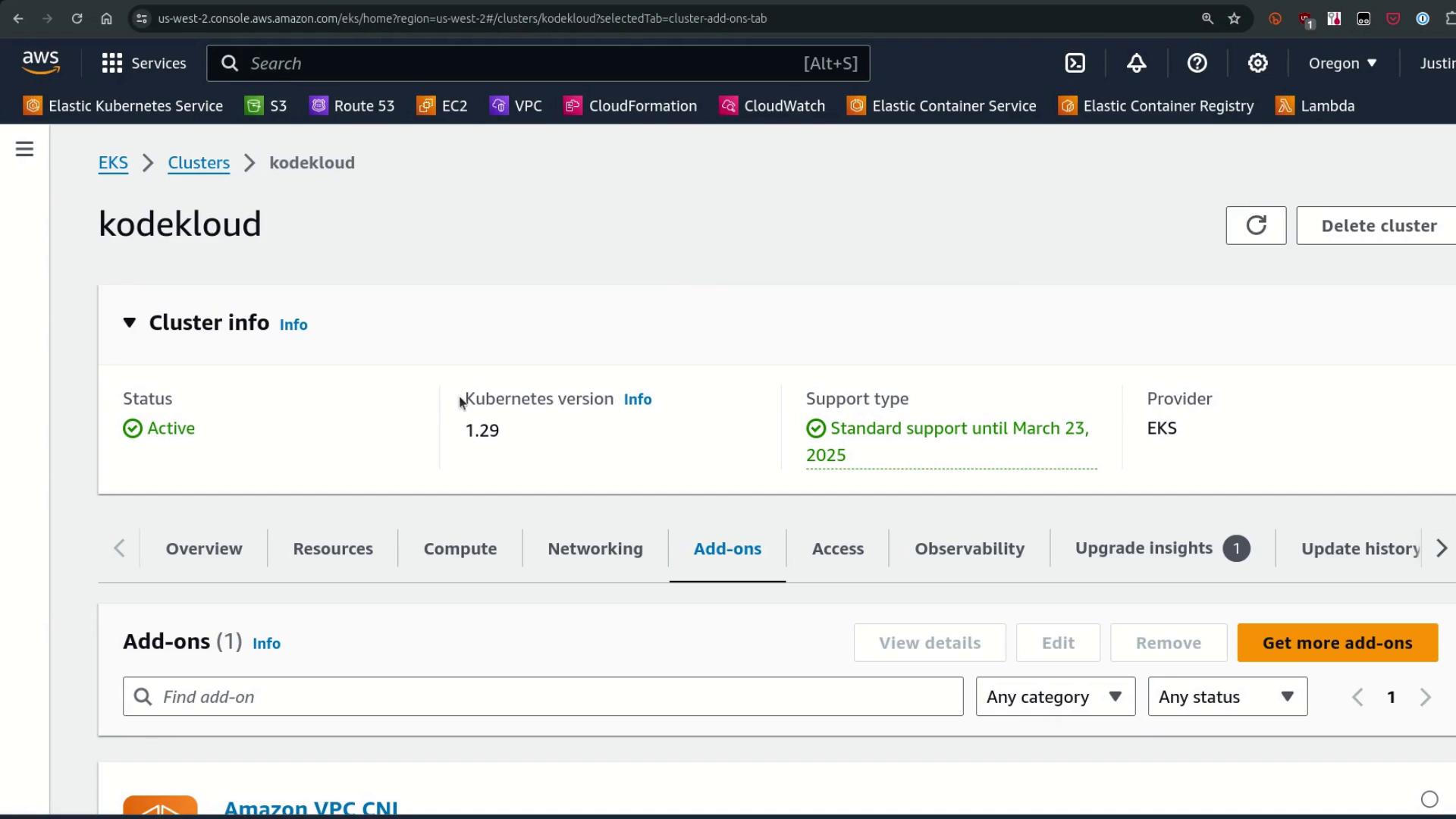
Converting CoreDNS and kube-proxy to Managed Add-ons
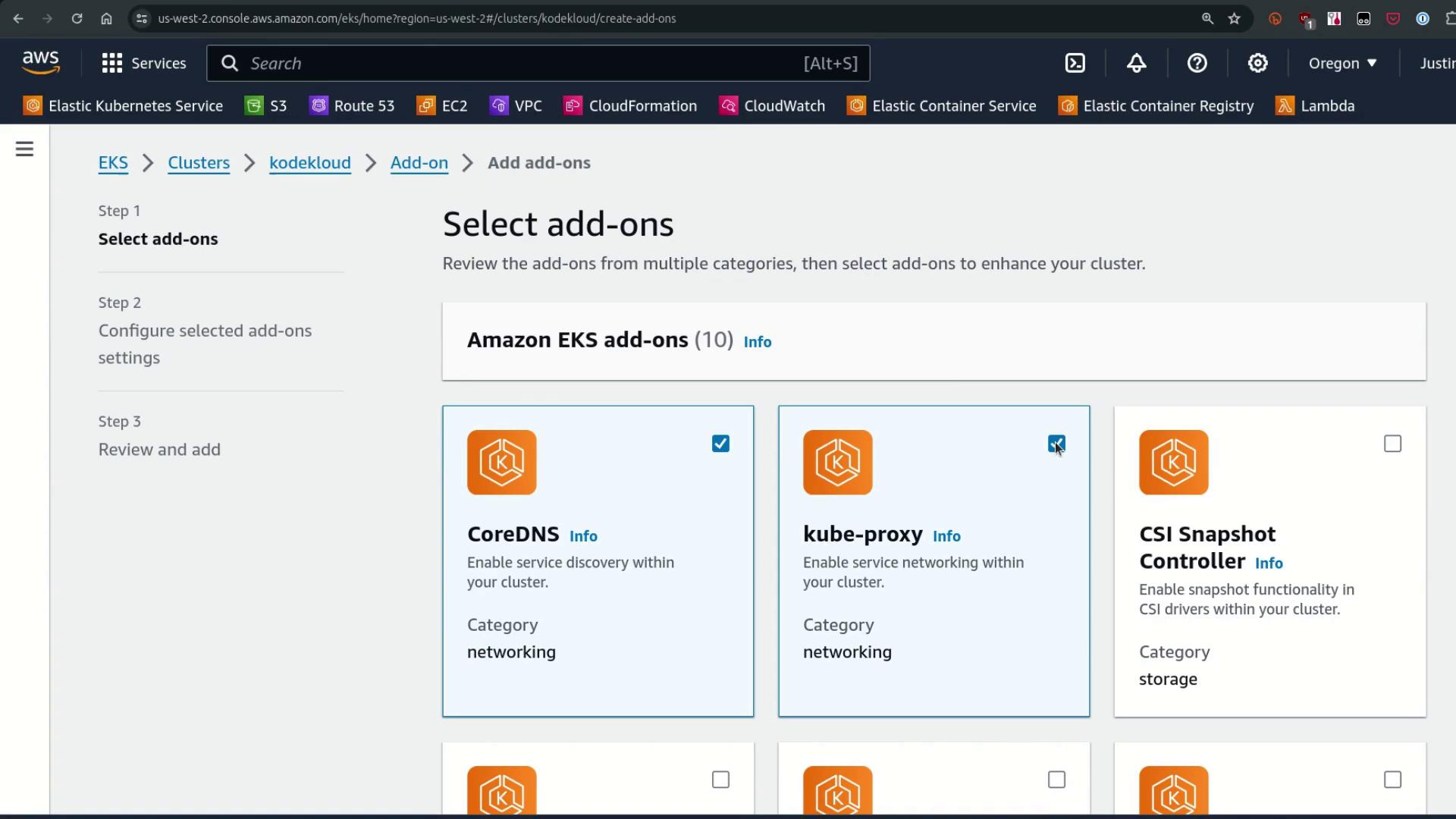
To bring CoreDNS and kube-proxy under managed add-on control:- In the AWS Console, go to Add-ons for your cluster.
- Select CoreDNS and kube-proxy.
- Click Install; the console auto-selects a compatible version via the EKS API.
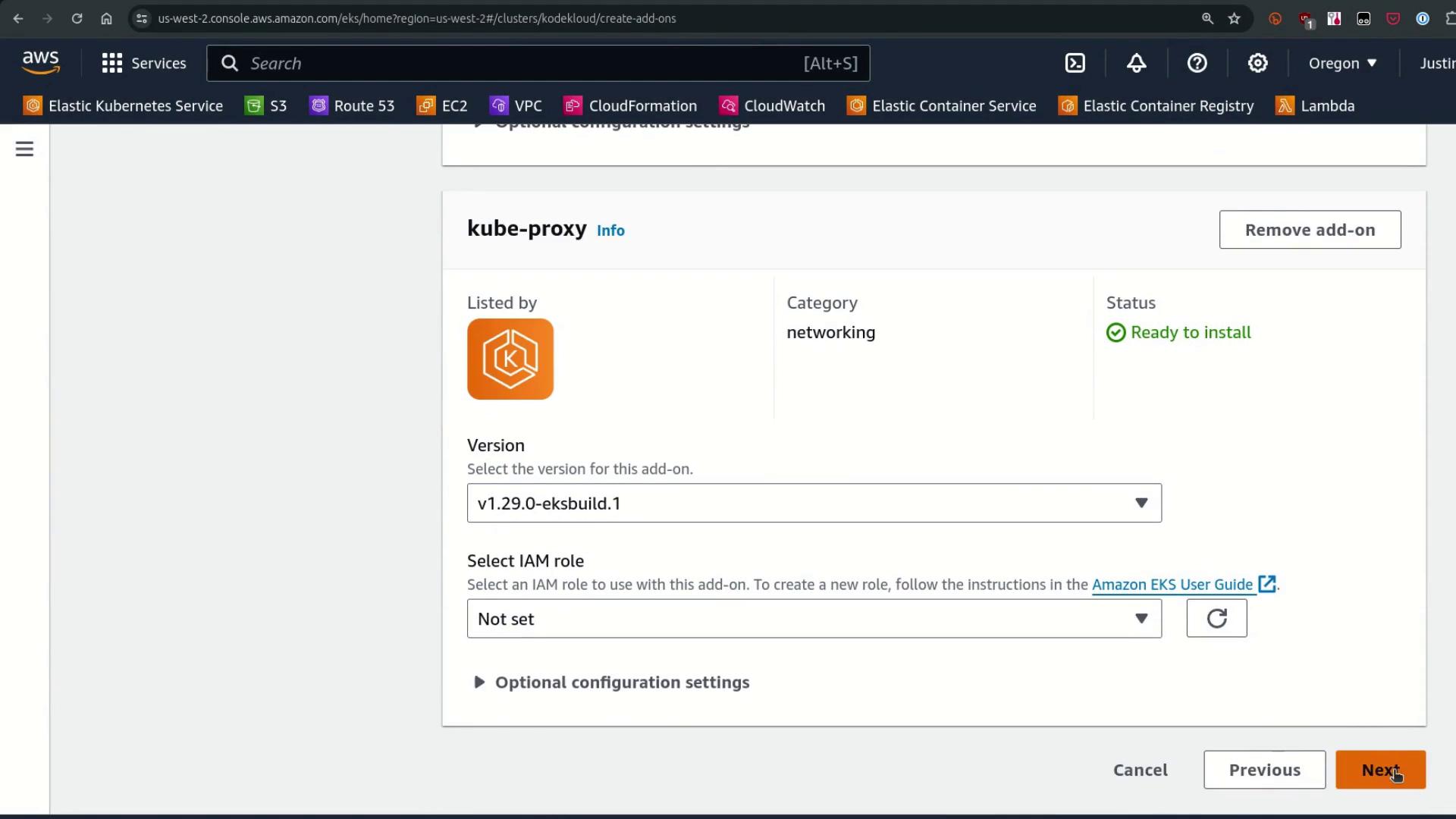
During installation, you may observe both unmanaged and managed instances of these components running in parallel. This is normal until you remove the original unmanaged deployments.
Viewing Add-on Status
Once installed, all add-ons appear as Active in the console—despite already running under the hood.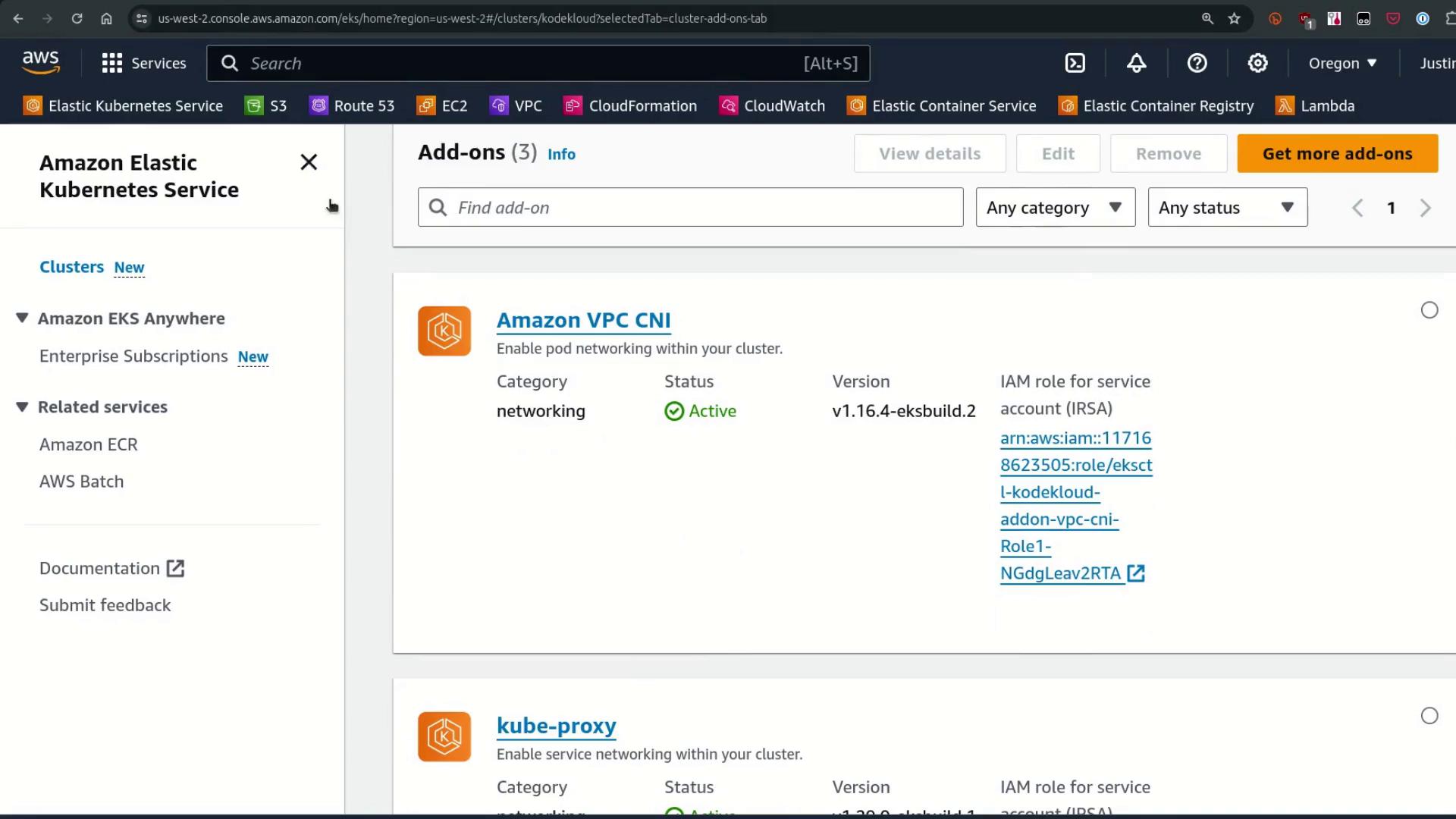
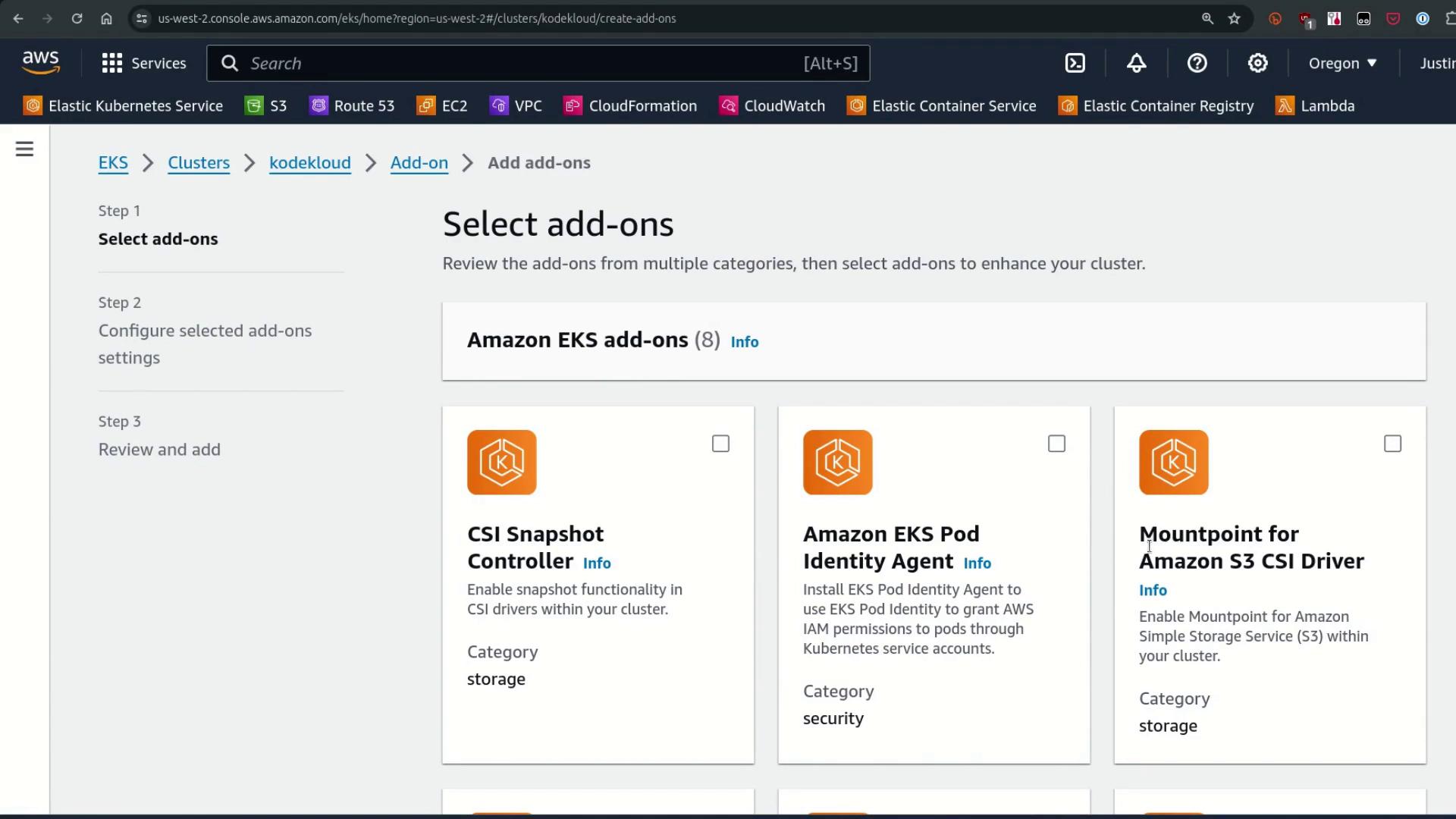
Officially Supported vs. Marketplace Add-ons
AWS maintains a growing roster of officially supported add-ons:| Add-on | Use Case | Example Installation |
|---|---|---|
| AWS Distro for OpenTelemetry (ADOT) | Collect and export metrics/traces | eksctl create addon --name aws-otel-collector |
| CSI Snapshot Controller | Volume snapshot management | eksctl create addon --name aws-ebs-csi-node |
| EKS Pod Identity Agent | Enable IAM roles for Kubernetes service accounts | eksctl create addon --name aws-iam-authenticator |
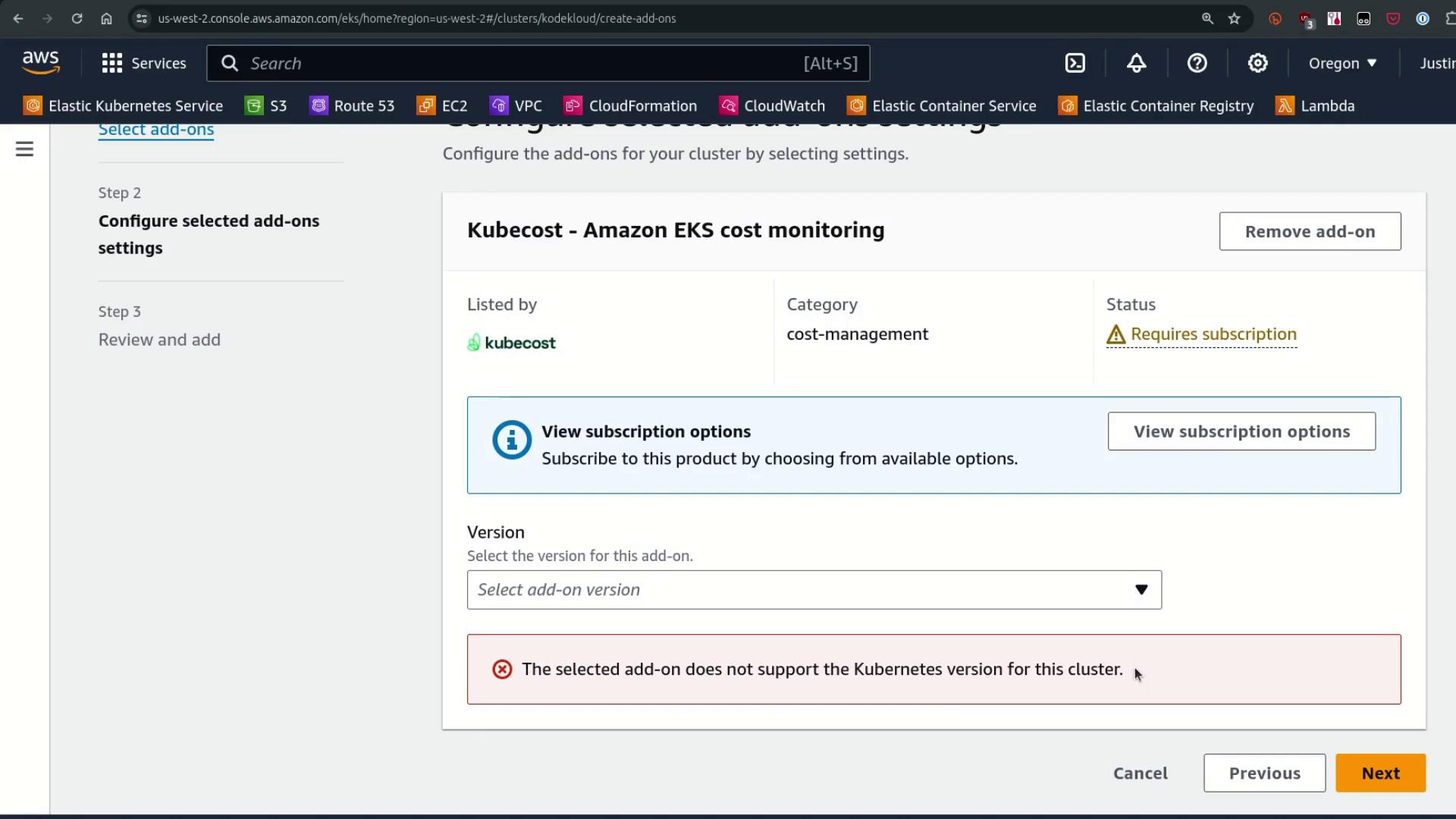
Marketplace add-ons may show “no versions available” if they don’t support your Kubernetes version. This can delay critical upgrades.
Best Practices: Own Your Add-on Manifests
For maximum control over versions, rollout timing, and configuration, consider managing cluster services yourself:- Use Helm charts or plain YAML manifests.
- Incorporate add-on deployments in your GitOps pipeline.
- Align CoreDNS and kube-proxy versions directly with your control plane and node versions.