AZ-204: Developing Solutions for Microsoft Azure
Implementing Shared Access Signatures
Stored Access Policies
In this article, you will learn about Stored Access Policies and how they enhance the security and management of shared access signatures (SAS tokens) in Azure Blob Storage. While SAS tokens provide fine-grained control over resources, Stored Access Policies offer an additional layer of server-side control by decoupling permission management from token issuance.
Overview
Stored Access Policies allow you to centrally manage access permissions, simplify expiry management, and swiftly revoke access without the need to recreate SAS tokens.
Key Benefits
Centralized Management
Administrators can streamline the management of access permissions by applying updates to a single stored access policy, which multiple SAS tokens can reference. This centralization simplifies overall access control.Enhanced Expiry Management
With a stored access policy, you can adjust permissions and expiry times without issuing new tokens. Simply update the policy to extend or reduce access according to your requirements.Rapid Revocation
If you need to revoke access immediately, modify or delete the stored access policy. Any SAS token linked to that policy will automatically inherit the updated restrictions, ensuring quick enforcement of security changes.
Example Code
Below are examples demonstrating how to create a stored access policy using both C# and the Azure CLI. In these examples, a policy is set with a one-hour expiry and read/write permissions.
BlobSignedIdentifier identifier = new BlobSignedIdentifier
{
Id = "stored access policy identifier",
AccessPolicy = new BlobAccessPolicy
{
ExpiresOn = DateTimeOffset.UtcNow.AddHours(1),
Permissions = "rw"
}
};
az storage container policy create \
--name <stored access policy identifier> \
--container-name <container name> \
--start <start time UTC datetime> \
--expiry <expiry time UTC datetime> \
--permissions a,c,d,l,r,w \
--account-key <storage account key> \
--account-name <storage account name>
These snippets illustrate how to define an access policy using the BlobSignedIdentifier and BlobAccessPolicy classes in C#, and how to achieve the same with the Azure CLI. In both cases, the policy settings include a one-hour expiry and permissions for read and write (noting that the CLI command syntax specifies permissions for a broader range of actions).
How to Use Stored Access Policies
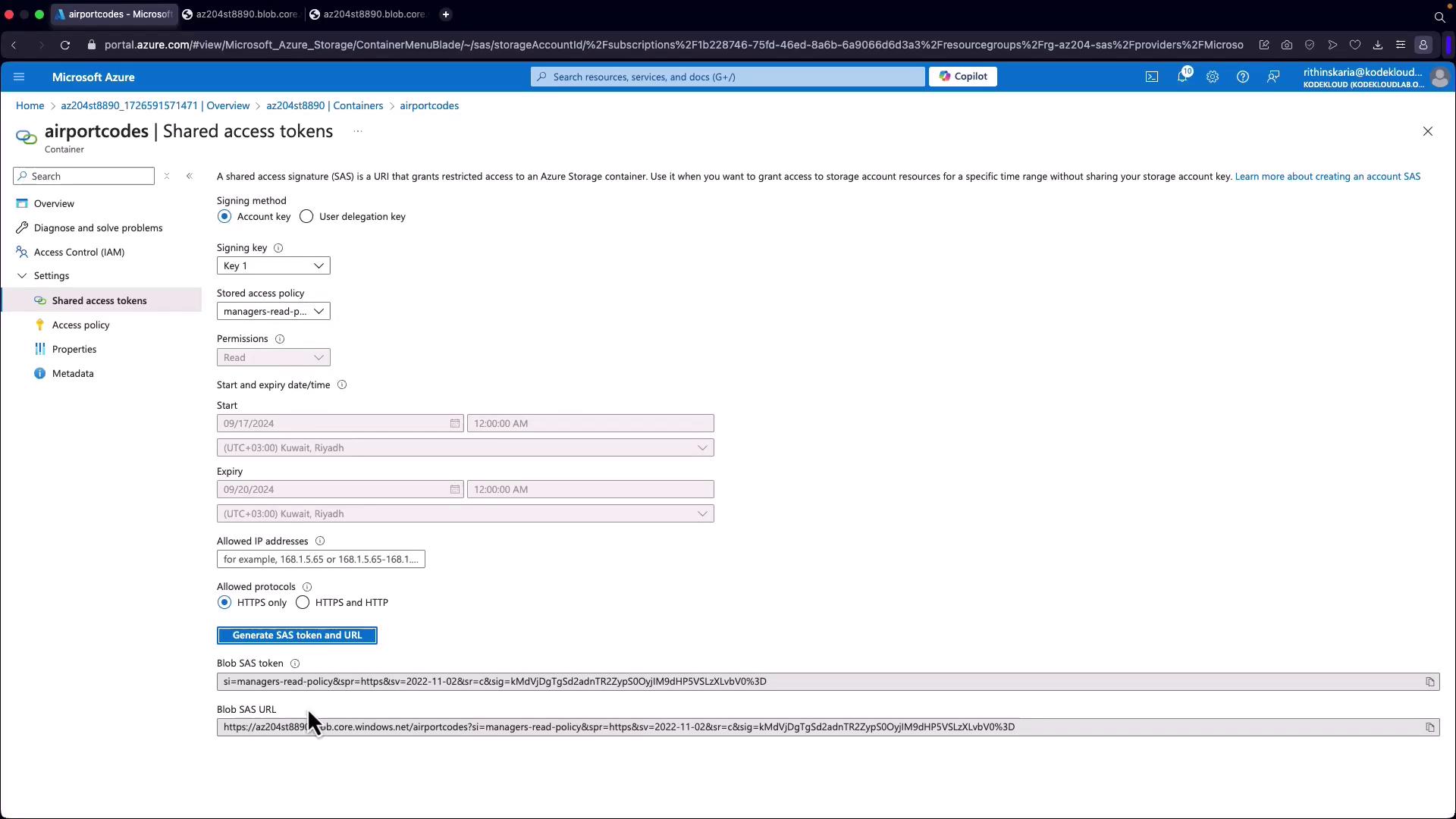
When creating or modifying a SAS token, you can reference a stored access policy rather than embedding permissions and expiry details directly into the token. For example, in the Azure Portal:
- Navigate to your storage account's container.
- Go to the Access Policies section.
- Add a new policy (for instance, a "manager's read policy") with the desired start and expiry times.
- Save the configuration, then proceed to the Shared Access Signatures section.
- Instead of directly specifying permissions, select the stored access policy you created.
This method ensures that the generated SAS token simply references the policy by its identifier. Any future changes to the policy, such as updating permissions, are automatically reflected in the token’s effective access rights.
Tip
Using stored access policies minimizes administrative overhead and reduces the risk of outdated or misconfigured SAS tokens when access requirements change.
Summary
Stored Access Policies provide a robust and efficient mechanism to manage access to Azure Blob Storage by decoupling permission control from SAS tokens. This strategy offers flexibility through centralized management, simplified expiry adjustments, and rapid revocation of access rights. Whether you are managing policies via code or directly through the Azure Portal, leveraging Stored Access Policies can significantly streamline your storage security and operational management.
Stay tuned for further insights, including our upcoming discussion on integrating the Microsoft Graph API for enhanced resource interaction.
For additional reading on Azure Storage features, visit the Azure Documentation.
Watch Video
Watch video content