Azure Policy
Azure Policy enforces organizational standards and verifies compliance across your environment. It ensures that resources adhere to defined guidelines and offers a comprehensive dashboard to monitor compliance levels—including the compliant, non-compliant, and unchecked resources.Best Practices for Policy Design
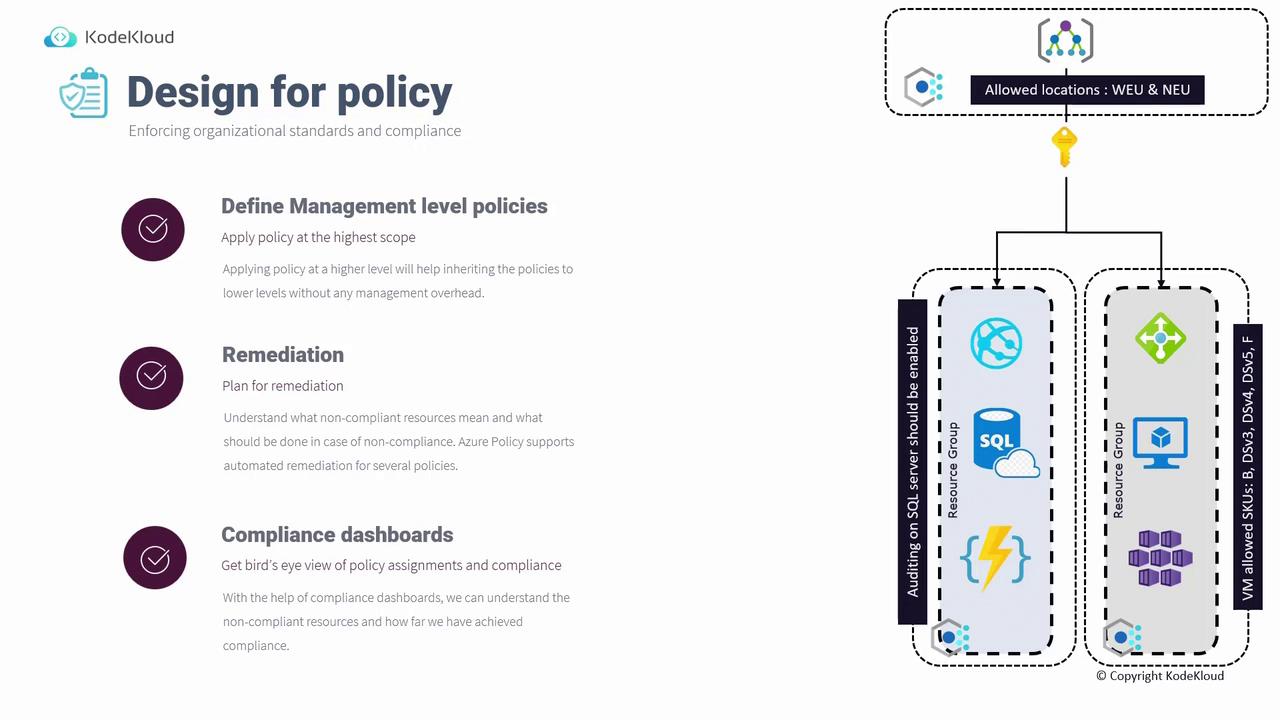
- Management-Level Policies:
Define policies at the management group level to automatically inherit them across all underlying management groups, subscriptions, resource groups, and resources. Consider the following examples:- An auditing policy for SQL Servers assigned to a specific resource group.
- A policy restricting allowed Virtual Machine SKUs (e.g., B-Series, DSV3, DSV4, DSV5, and FCDs) applied at the resource group level.
- An organizational-level policy (e.g., restricting deployments to West Europe and North Europe) applied at the root management group to ensure consistency across all subscriptions and resources.
Defining policies at a higher scope (such as the management group level) reduces administrative overhead and ensures uniform policy enforcement across all resources.
Remediation
Azure Policy not only enforces compliance but also includes remediation plans that help correct non-compliant resources. However, it’s important to note:- For policies like allowed locations, if resources were deployed in regions such as East US or West US prior to the policy’s assignment, remediation won’t automatically move these resources—manual intervention is required.
- Conversely, tasks like installing a missing Log Analytics Agent can be remediated automatically.
Even with effective policies, some remediation actions require manual redeployment. Always review the remediation plan details to avoid unsupported operations.
Compliance Dashboard
The compliance dashboard provides a visual summary of policy assignments and their current status. Key aspects include:- Overall percentages of compliant and non-compliant resources.
- Identification of resources failing to meet specified standards.
- Available actions for addressing non-compliance issues.
Role-Based Access Control (RBAC)
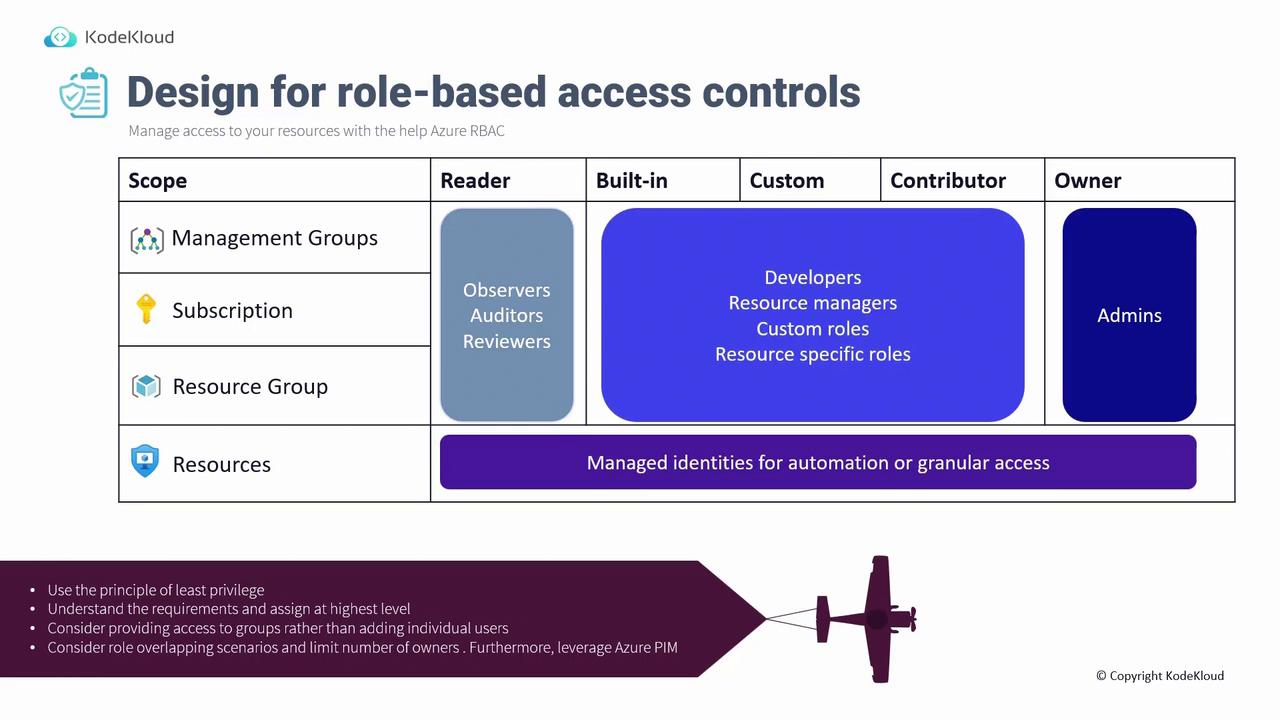
Role-Based Access Control (RBAC) is a key component of managing permissions and controlling resource access in Azure. Different roles help administer access at various scopes effectively.Key RBAC Principles
-
Built-in Roles:
Common roles include:- Reader: Ideal for observers, auditors, and reviewers at the management group or resource group level.
- Contributor: Suitable for developers and resource managers performing resource-specific tasks. Custom roles can further refine permissions.
- Owner: Contains privileges to delegate access; use sparingly and reserve for administrators only.
-
Resource-Specific Roles:
Azure also provides roles tailored for specific resources:- Virtual Machine Contributor for managing VMs.
- Monitoring Contributor or Monitoring Reader for Azure Monitor.
- Storage Blob Contributor for handling storage operations.
Role Assignment Best Practices
- Principle of Least Privilege:
Grant users only the minimum necessary permissions. - Scope of Assignment:
Assign roles at the highest viable level (e.g., Subscription level) to simplify management. - Group Assignment:
Prefer grouping users and assigning roles to groups rather than individual users to ease administration during team transitions. - Owner Role Limitation:
Minimize the number of users with Owner roles to reduce the risk of permission overlap or conflicts.
Always assign roles based on job function and limit high-privilege roles to specialized personnel.
Privileged Identity Management (PIM)
Azure Privileged Identity Management (PIM) boosts security by requiring activation of elevated privileges only when necessary. Similar to usingsudo in Linux, even users with Owner permissions must activate their role, provide justification, and specify a duration for elevated access. Once the duration expires, permissions are automatically revoked until reactivation is required.
Integrating Policy and RBAC
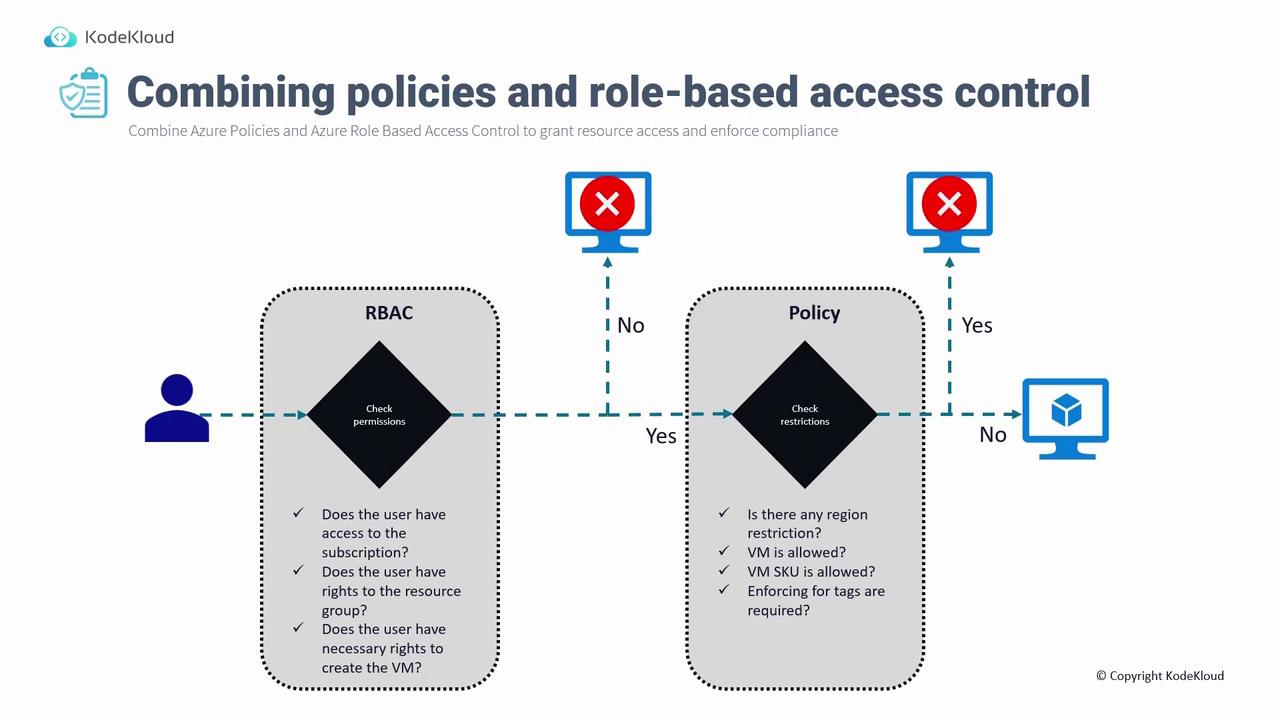
Integrating Azure Policy and RBAC establishes a robust governance framework that both limits user permissions and enforces compliance with organizational standards.Deployment Process Example
When a user attempts to deploy a Virtual Machine, the following checks occur:-
Permission Check (RBAC):
The system first verifies the user’s permissions at the Subscription, Resource Group, or Resource level. -
Policy Evaluation:
After confirming permissions, the system evaluates applicable policies:- Regional restrictions: Only specified regions are allowed.
- SKU restrictions: Only permitted VM SKUs can be deployed.
- Tag requirements: Mandatory resource tagging may be enforced.
This concludes our discussion on designing for Azure Policy and RBAC. For further details, visit the Azure Documentation and explore additional resources on policy management and access control strategies.