Service Endpoint
Service Endpoints enable resources within your virtual network to securely access Azure PaaS services without routing traffic over the public internet. Once configured—for instance, to access an Azure Storage account—outbound traffic from your virtual machines uses the VM’s private IP address. Although the service name still resolves to a public IP, the traffic flows solely over Microsoft’s backbone network, enhancing security by eliminating the need for public IP assignments. To set up a Service Endpoint, configure the storage account firewall to allow traffic originating from the Service Endpoint of your virtual network. Once enabled, outbound requests carry the private IP address, ensuring secure and efficient communication.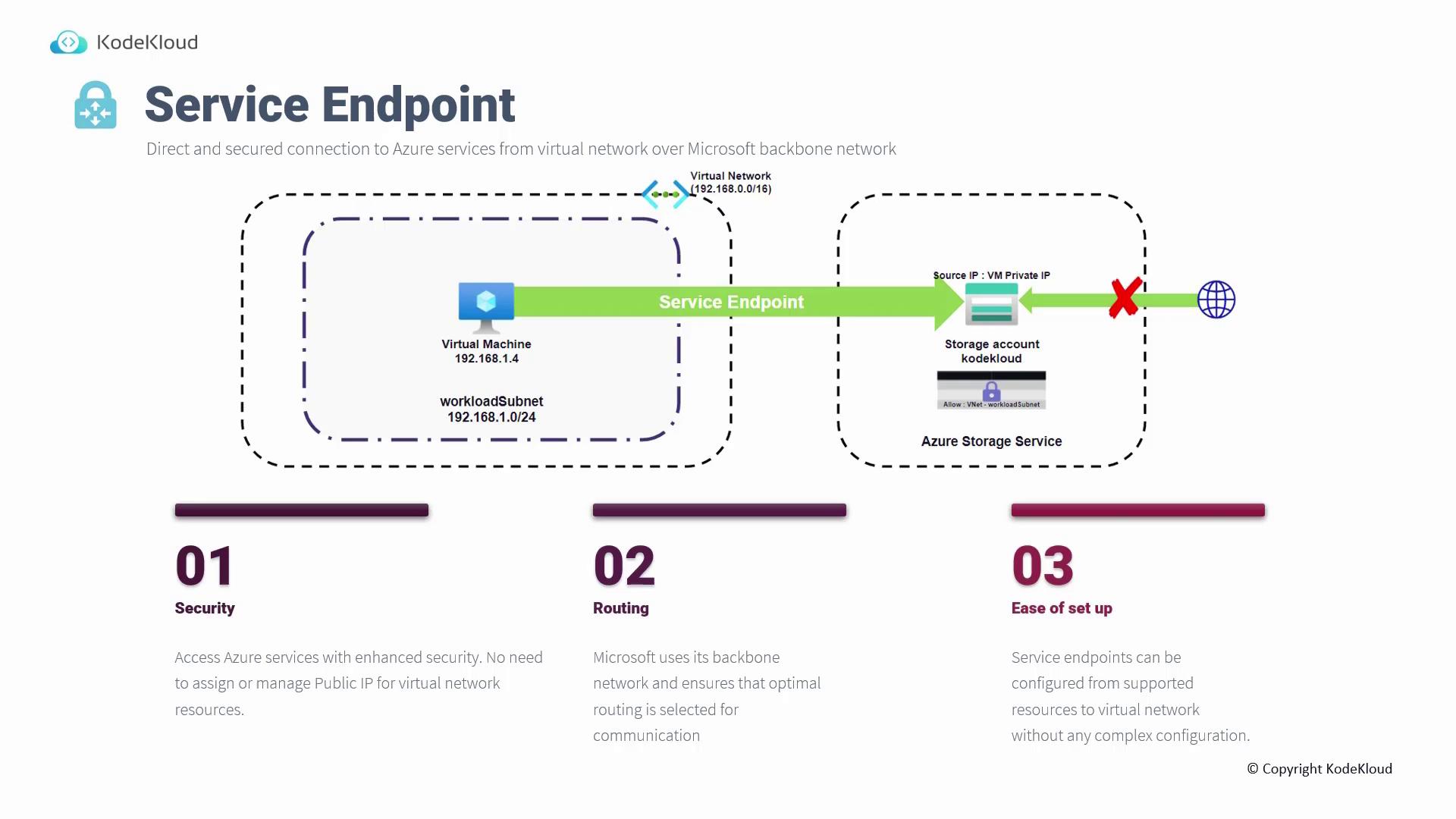
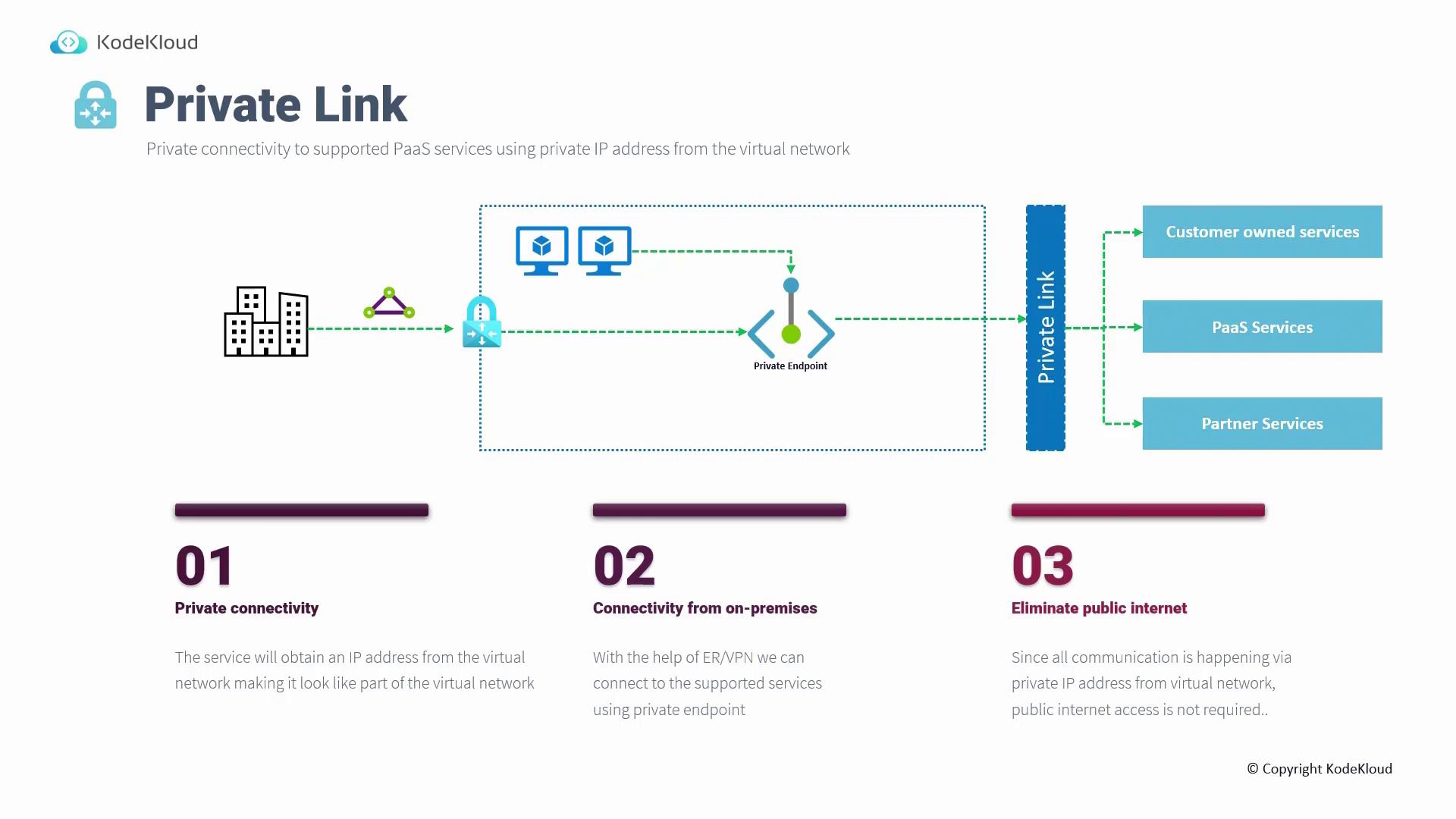
Private Link
Private Link extends the concept of secure connectivity by assigning a private IP address from your virtual network directly to the PaaS service. Unlike Service Endpoints—where the service name still resolves to a public IP—Private Link incorporates the service into your network as if it were a native network interface. Key advantages of using Private Link include:- Communication exclusively over private IP addresses.
- Simplified integration with on-premises networks via ExpressRoute or VPN without additional NAT requirements.
- Enhanced security by removing exposure to the public internet.
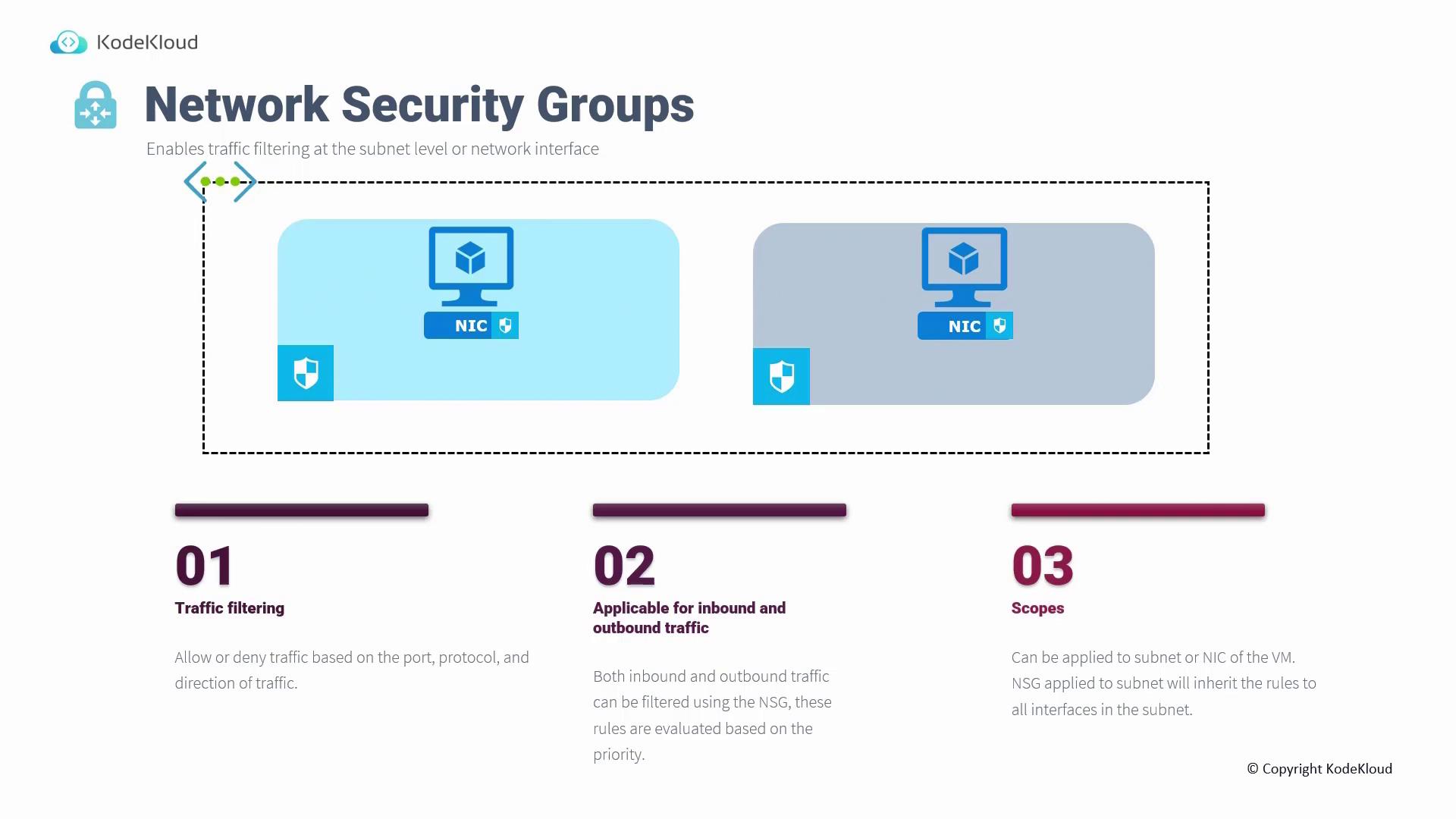
Network Security Groups (NSGs)
Network Security Groups (NSGs) serve as virtual firewalls that filter traffic at the subnet and network interface levels within your virtual network. NSGs use customizable rules based on factors such as port, protocol, direction, and Azure service tags to allow or deny traffic. Key features include:- Traffic Filtering: Define granular rules to permit or block traffic based on your security requirements.
- Rule Inheritance: NSGs applied at the subnet level automatically protect all associated virtual machine interfaces, though you can attach NSGs directly to a NIC to override inherited rules.
- Default Behavior: Inbound traffic is blocked by default (with the exception of VNet and Azure load balancer health probes), while outbound traffic is allowed unless specifically restricted.
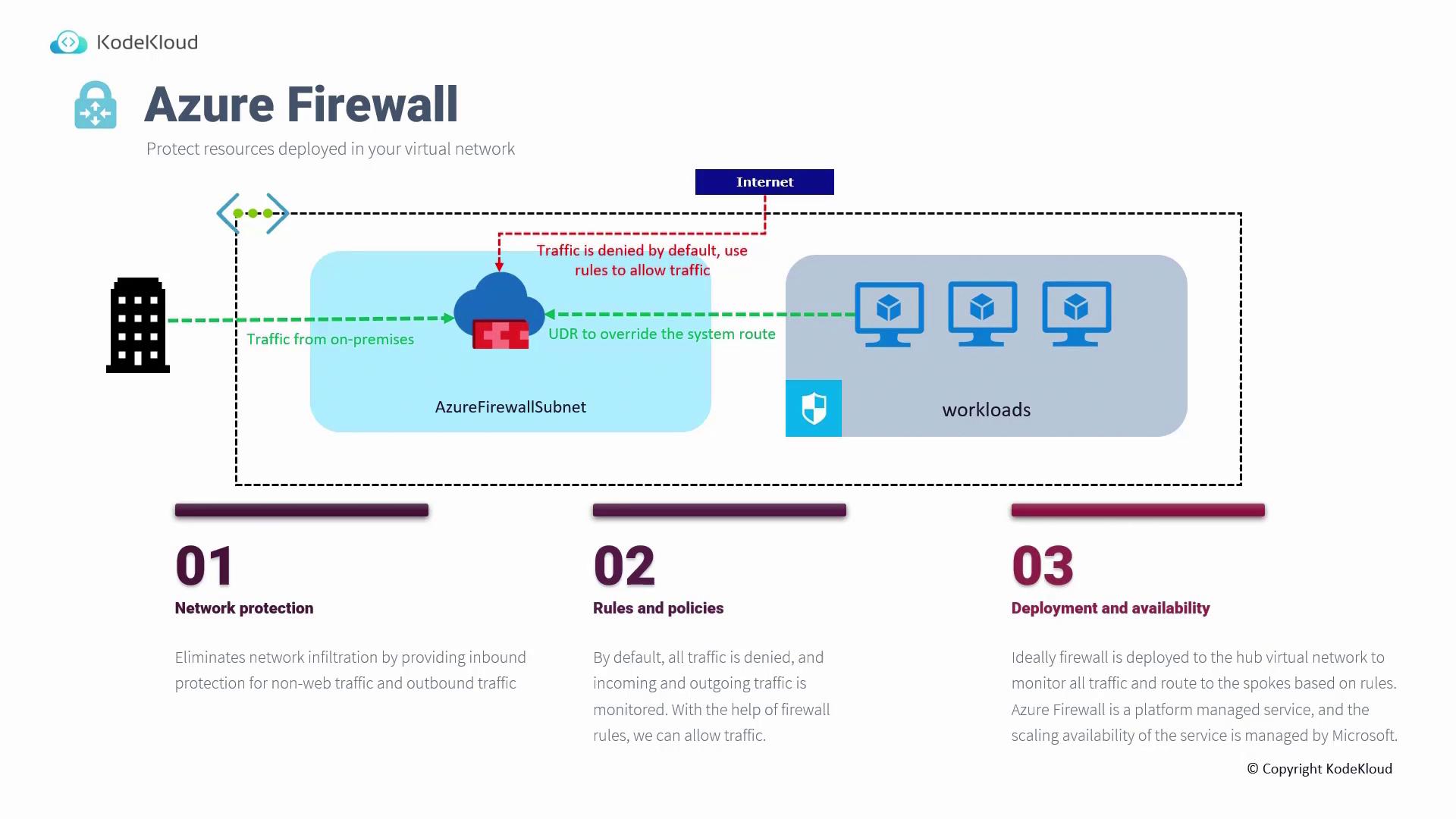
Azure Firewall
Azure Firewall is a robust, cloud-native security service designed to protect your virtual networks. Deployed within its dedicated subnet, the Azure Firewall acts as a central point for inspecting and filtering traffic between on-premises networks and Azure, or among various virtual networks. Key capabilities include:- Comprehensive Protection: Utilize network and application rules to block unauthorized traffic.
- Centralized Rule Management: By default, all traffic is denied until you explicitly define permissions.
- Hub-and-Spoke Deployment: Commonly used in a centralized hub-and-spoke architecture for efficient traffic inspection and routing.
- Managed Service: Enjoy automated scalability, availability, maintenance, and patching managed by Microsoft.
For more detailed configuration instructions, see the Azure Firewall Documentation.
Web Application Firewall (WAF)
The Web Application Firewall (WAF) safeguards your web applications from common attack vectors such as cross-site scripting (XSS) and SQL injection. WAF can operate in two modes:- Prevention Mode: Actively blocks malicious traffic.
- Detection Mode: Monitors and logs suspicious activity without blocking, allowing you to fine-tune security policies before full enforcement.
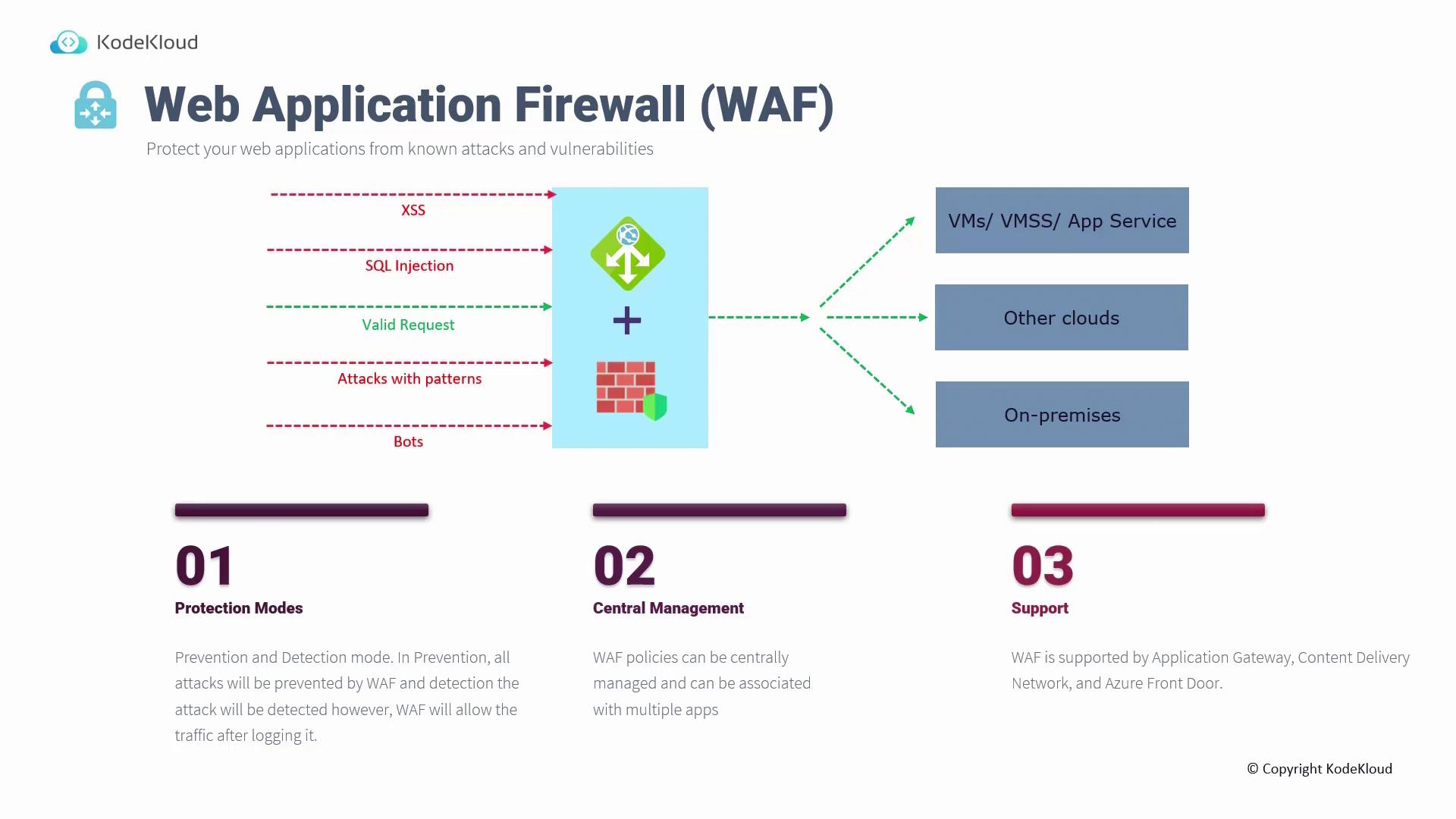
- Azure Firewall Alone: Best for non-HTTP workloads.
- WAF Alone: Ideal for web application protection, combined with NSGs for broader traffic control.
- Parallel Deployment: Use WAF for HTTP traffic and Azure Firewall for other network traffic.
- WAF in Front: Filter HTTP traffic with WAF first, then use the firewall for deeper inspection.
- Azure Firewall in Front: Inspect all traffic using Azure Firewall, then forward web-specific traffic to WAF for final processing.

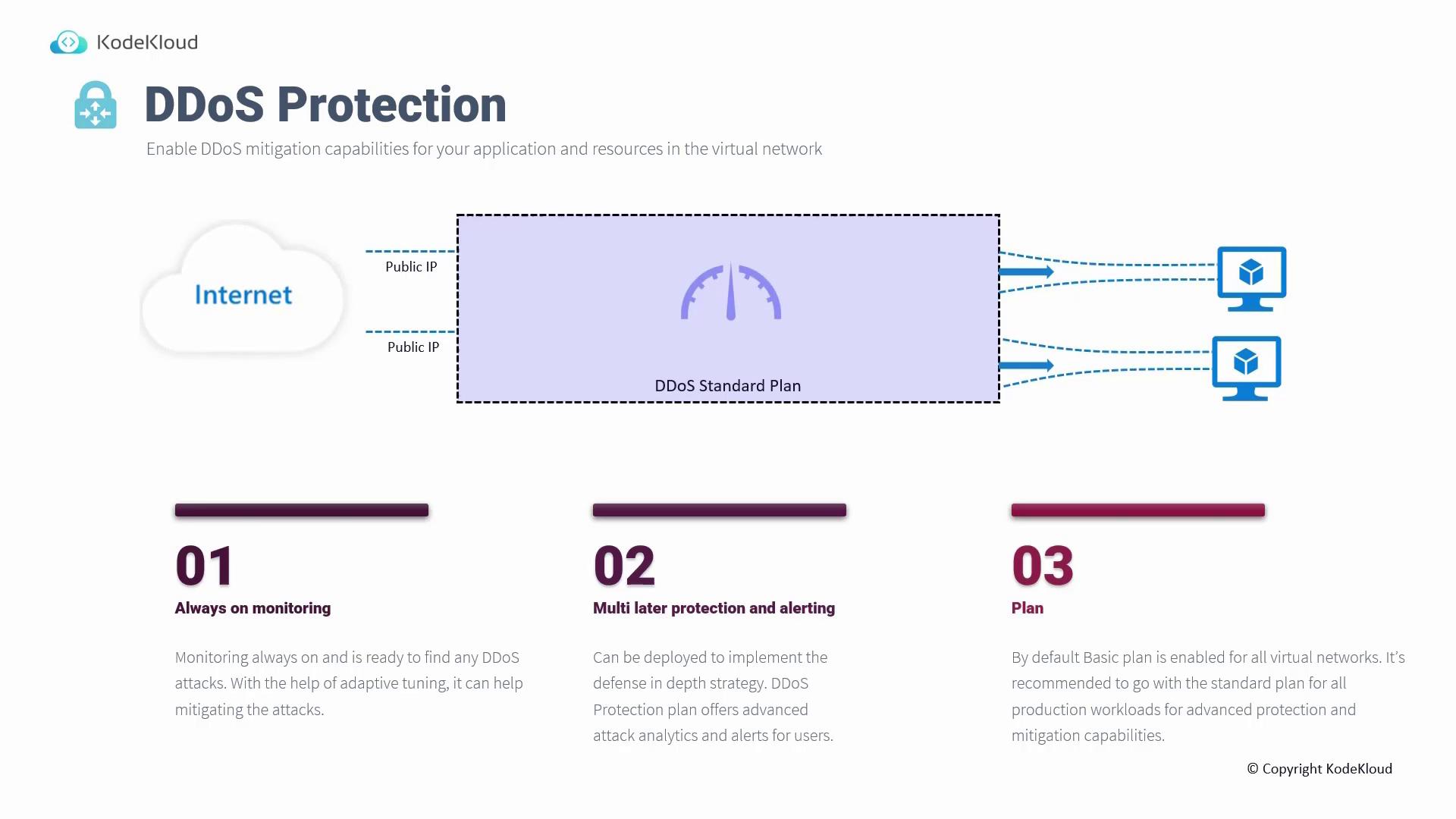
DDoS Protection
Azure’s built-in Distributed Denial of Service (DDoS) protection safeguards your virtual networks from large-scale attacks. While all virtual networks come with basic DDoS protection enabled, the Standard SKU offers enhanced features:- Always-On Monitoring: Constantly analyzes traffic with adaptive tuning to detect anomalies.
- Layered Defense and Alerting: Provides advanced attack analytics along with comprehensive alerting features.
- Targeted Security: The Standard plan is particularly recommended for public-facing resources to maximize security.
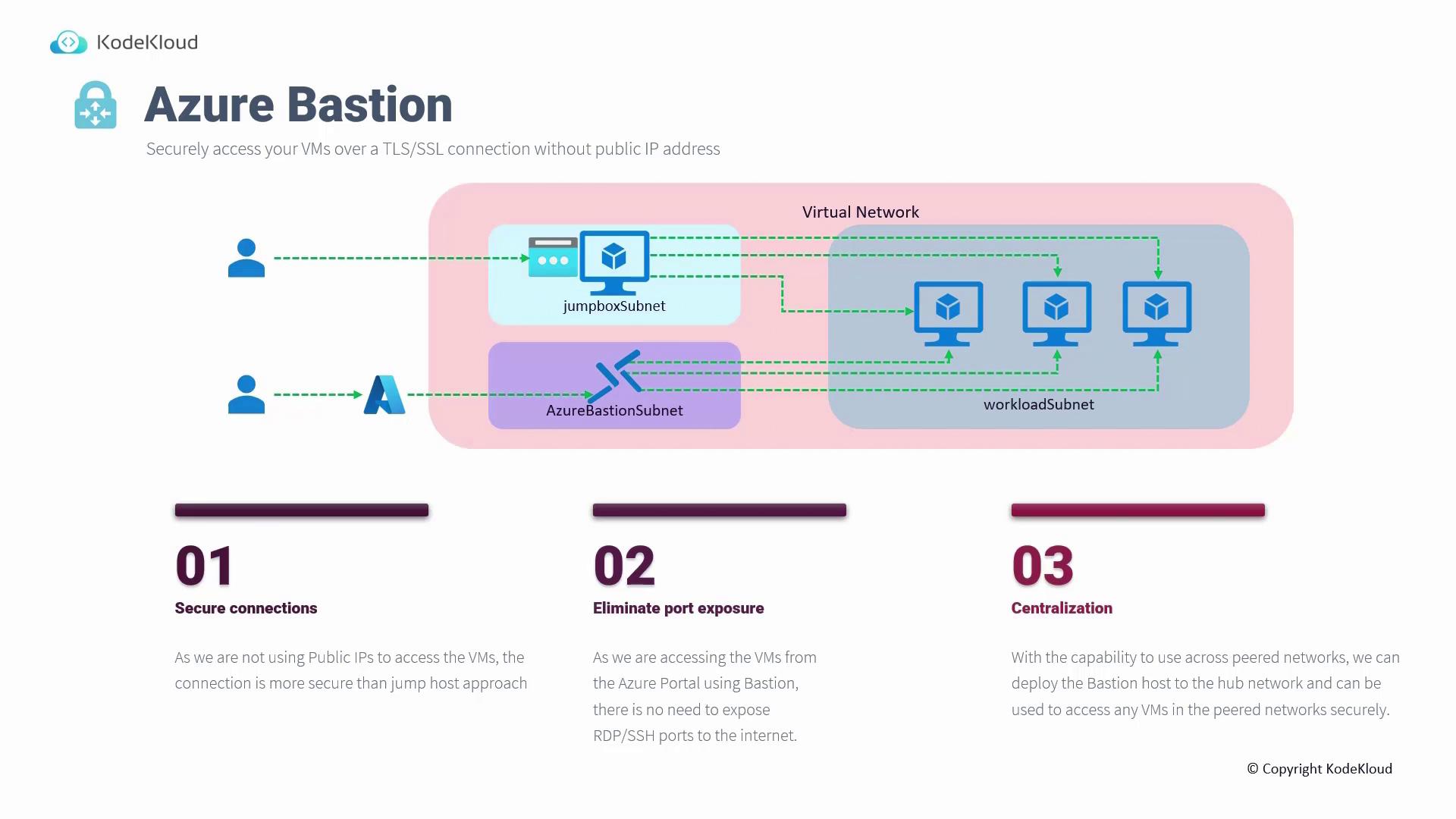
Azure Bastion
Azure Bastion enables secure, seamless RDP and SSH connectivity to your Azure Virtual Machines without the need for public IP addresses. Traditionally, accessing VMs without public IPs required a jump host, but Azure Bastion allows you to initiate secure sessions directly from the Azure Portal over SSL/TLS. Benefits of using Azure Bastion include:- Enhanced Security: Eliminates reliance on public IPs and exposure of RDP/SSH ports.
- Centralized Management: Deploy Bastion in a hub network to manage access across multiple virtual networks.
- Fully Managed Service: Microsoft handles all maintenance, patching, and scalability requirements.
Just-In-Time (JIT) VM Access
Just-In-Time (JIT) access, part of the Microsoft Defender for Cloud Standard plan, reduces the exposure of management ports (like RDP and SSH) by blocking inbound traffic until explicit permission is granted. This temporary access model minimizes the risk of attacks on commonly targeted ports. When you request access:- Pre-existing deny rules for the management ports are temporarily lifted.
- Access is granted for a predefined duration, after which the firewall rules are automatically reinstated.
- This method significantly lowers the attack surface while still providing necessary administrative access.
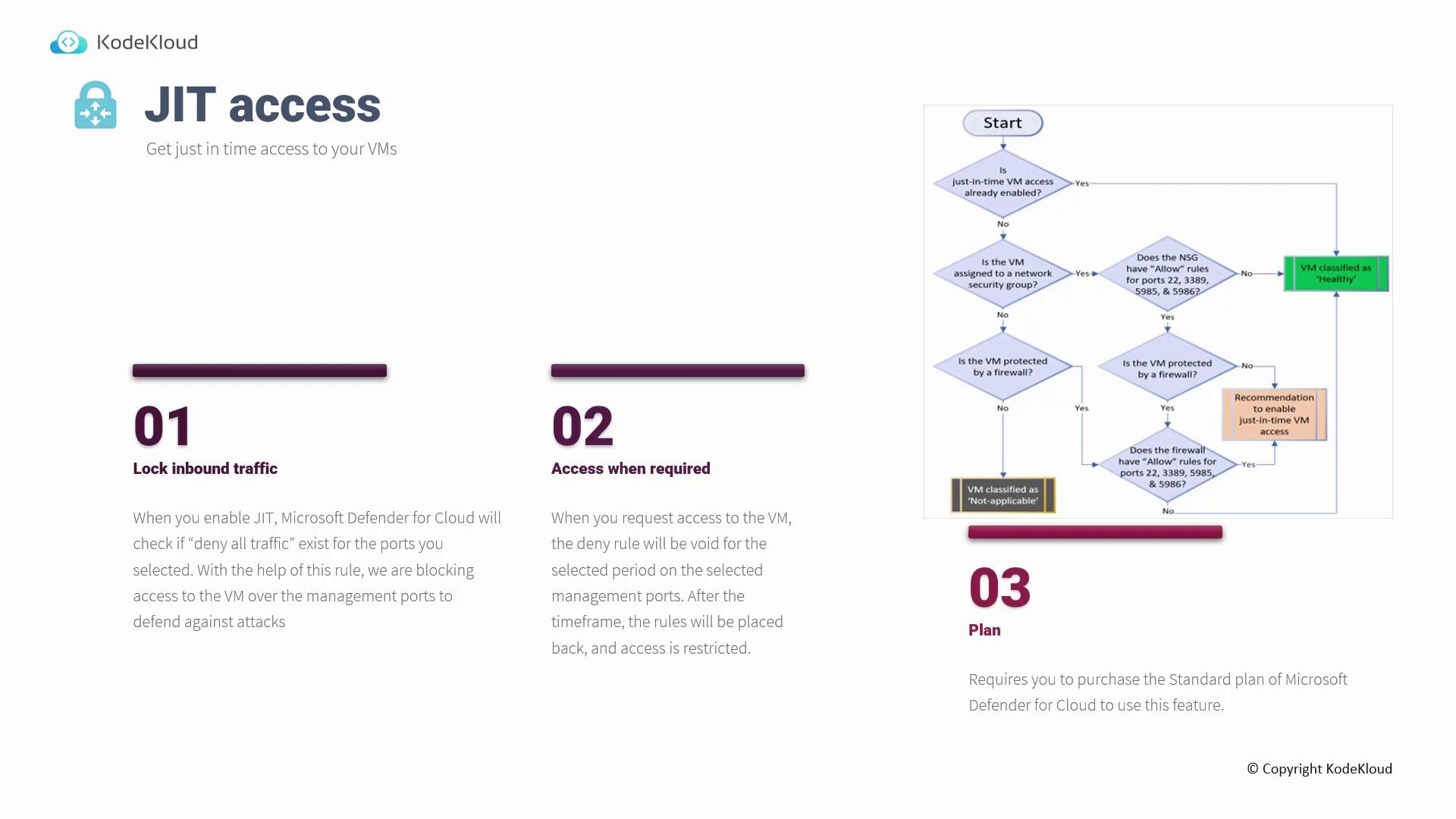
Ensure that your VMs are also protected by Network Security Groups or a firewall when enabling JIT access.
Architectural Scenario
Consider a scenario where a client requires a resilient private connection from their on-premises network to Azure, complete with failover mechanisms. The design includes a central hub with two spokes hosting a three-tier application deployed across two regions. Additional requirements include load balancing, a secure private connection to a SQL PaaS database, and strict traffic controls between the front-end subnet and the database subnet.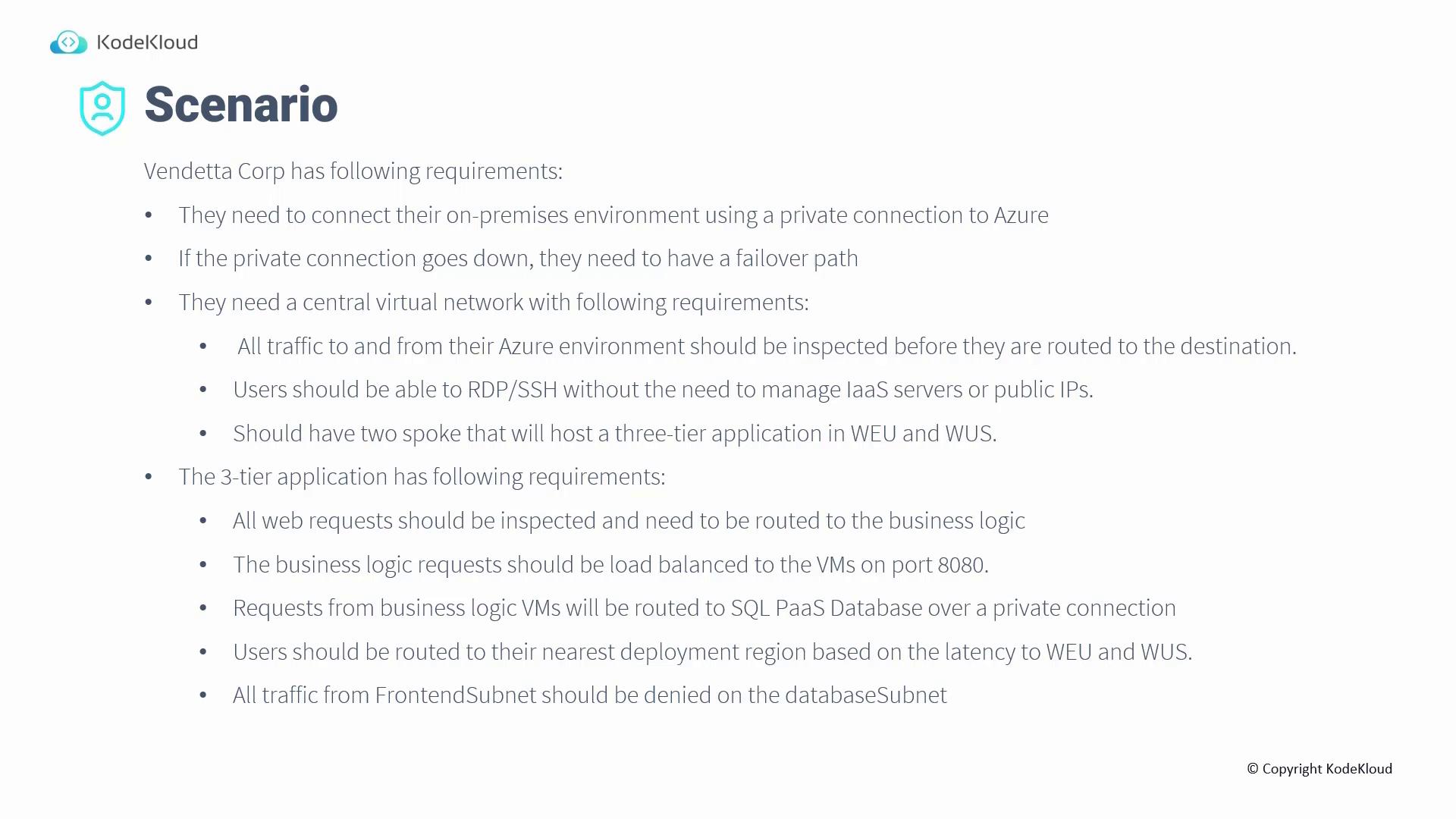
This article has provided a comprehensive look at advanced network security and application protection strategies using Azure services. By understanding and implementing these components, you can build a robust, secure, and scalable infrastructure optimized for modern cloud environments. Happy designing!