AZ-305: Microsoft Azure Solutions Architect Expert
Design a relational data storage solution
Design for data security
In this article, we explore key aspects of SQL database security. Our focus is on developing a robust security strategy that protects both your database infrastructure and the sensitive data it holds. We address several critical topics, including network security, identity and access management, data protection, and overall security management.
Network Security
Securing the network interface of your database is essential. There are three primary deployment methods to enhance your database's network security:
Direct Virtual Network Deployment
For SQL Managed Instances, deploy your database directly into a virtual network for enhanced isolation.SQL Firewall
The SQL firewall feature allows you to grant database access from selective virtual networks and specific IP addresses. This method restricts incoming connections to only those that you have explicitly allowed.Private Link
For scenarios that require private connectivity between your database and virtual machines or on-premises infrastructure (via ExpressRoute or VPN), Private Link is an ideal option. It establishes secure, non-public connections, ensuring that your database is not exposed to the public internet.
Identity and Access Management
Robust identity and access management is vital for maintaining database security. Consider the following best practices:
Authentication Methods
When deploying your SQL database, choose from multiple authentication options like Azure Active Directory (Azure AD), SQL authentication, or a hybrid approach to best meet your security requirements.Azure Role-Based Access Control (RBAC)
Utilize RBAC to precisely control which users have permissions to access the database.Role-Level Security
Implementing role-level security within the database further refines access control, as it allows you to manage permissions for different user roles at a granular level.
Data Protection
Protecting your data involves implementing multiple layers of encryption and data masking. The following measures ensure your data remains secure throughout its lifecycle:
Encryption Measures
Encryption in Use
Encrypt sensitive data (e.g., social security numbers, phone numbers, email addresses) while it is being actively processed. This measure protects data during its lifecycle from potential leaks during processing.Encryption at Rest
Transparent Data Encryption (TDE) safeguards data at rest by encrypting data, backups, and transaction logs at the page level as they are written to disk. TDE is enabled by default on all new SQL databases and SQL Managed Instances, ensuring that data stored on disk is automatically encrypted and decrypted upon loading into memory.Encryption in Transit
Both SQL databases and SQL Managed Instances enforce SSL/TLS encryption for all client-server communications. This guarantees that data remains confidential as it travels between the client and server.
Dynamic Data Masking
Dynamic data masking complements encryption in use by limiting the exposure of sensitive data in query results. This policy-based feature allows you to mask sensitive database fields (e.g., credit card numbers, social security numbers), ensuring that only authorized users can view sensitive information.
Note
Dynamic data masking acts as an extra layer of protection by limiting the information exposed to non-privileged users without altering the underlying data.
Security Management
A comprehensive data security strategy combines technical safeguards with ongoing security management practices:
Azure Threat Protection
Enable Azure Threat Protection through Defender for Cloud to detect and respond to potential security threats, thereby enhancing your database's security posture.SQL Auditing
SQL Auditing tracks all database transactions and changes, generating detailed audit logs that help in monitoring access and detecting suspicious activity.Vulnerability Assessment
Defender for Cloud’s vulnerability assessment scans your database environment for potential weaknesses, allowing you to proactively address identified issues.Data Discovery and Classification
This feature assists in labeling and classifying data based on sensitivity levels (e.g., confidential or general), reducing the risk of exposing highly sensitive information.
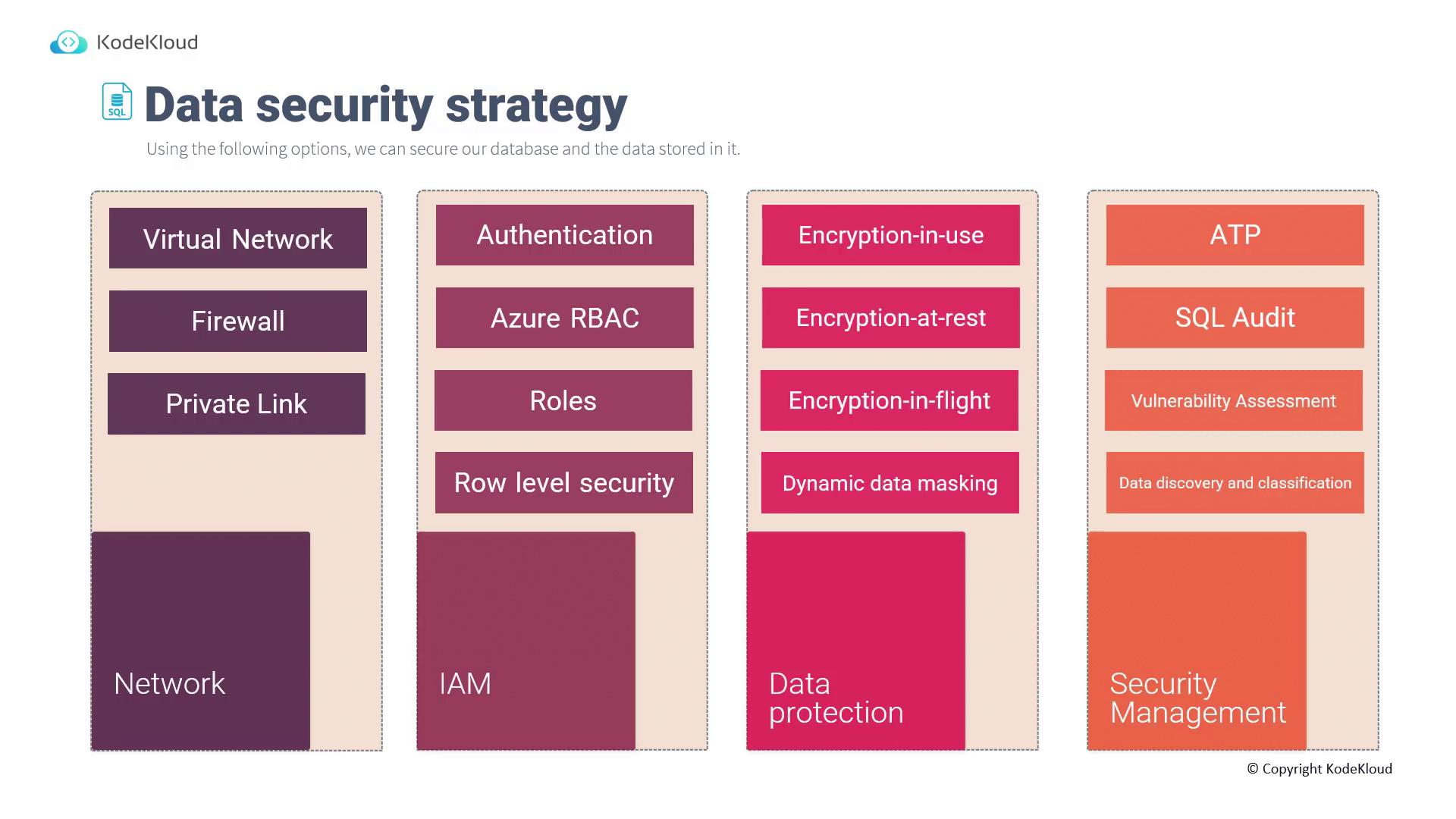
Collectively, these measures form a comprehensive data security strategy tailored for SQL databases.
Next Topic: Design for SQL Edge
This concludes our detailed discussion on securing SQL databases. In the next section, we will dive into design considerations for SQL Edge.
For further reading, consider the following resources:
Watch Video
Watch video content