AZ-305: Microsoft Azure Solutions Architect Expert
Design for authentication and authorization
Design for identity and access management
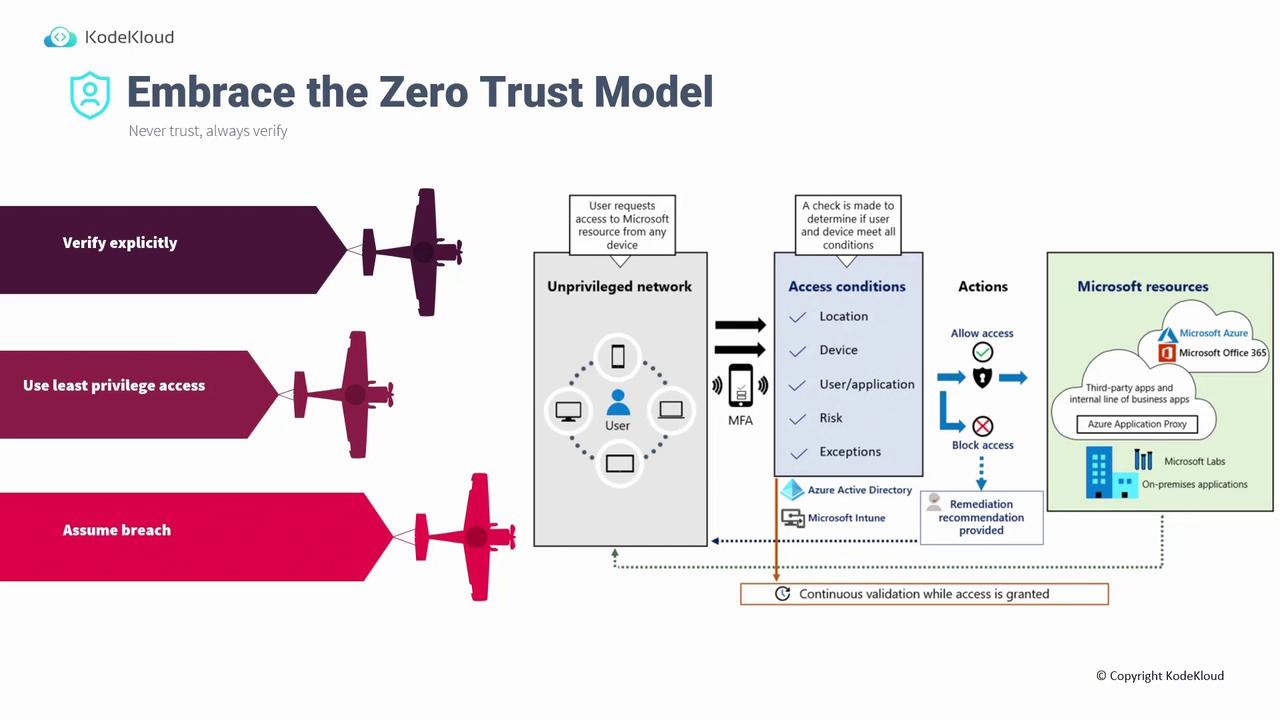
This article delves into creating robust Identity and Access Management (IAM) systems based on the Zero Trust model—an approach where every access request is rigorously verified, ensuring a secure and reliable environment.
The Zero Trust model adheres to the principle: never trust, always verify. This means that every time a user requests access to resources, regardless of device or location, the request undergoes a thorough verification process. Verification involves checking device details, user credentials, location, application context, and risk factors. The conditional access module then decides whether to grant or deny access based on these assessments.
The Zero Trust model is built on three core principles:
- Verify explicitly – Always confirm every request, no matter where it originates.
- Use the principle of least privilege – Assign only the permissions necessary for routine tasks. Overprivileging can lead to security vulnerabilities, while underprivileging may hinder productivity.
- Assume breach – Operate with the assumption that a breach could occur, ensuring every request is carefully scrutinized.
Designing an IAM Solution
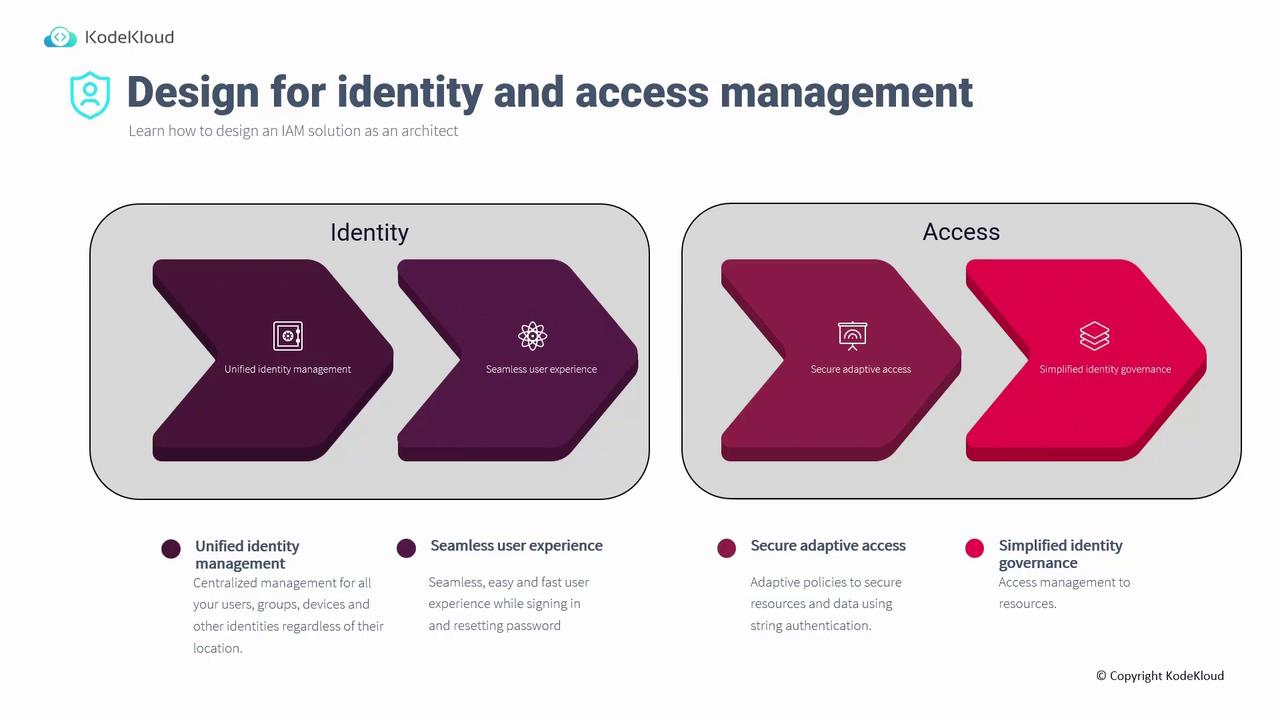
Building an effective IAM solution starts with the Zero Trust model. There are two key components to consider: Identity and Access.
Unified Identity Management
Implement centralized management for all users, groups, devices, and identities—whether they reside on-premises, in remote Active Directories, or in the cloud.
Identity
- Unified Identity Management: Utilize a centralized system for managing users, groups, devices, and identities regardless of their location.
- Seamless User Experience: Ensure a smooth sign-in process and provide efficient password reset options, including self-service capabilities, to decrease reliance on IT support.
Access
- Secure Adaptive Access: Establish dynamic policies that grant or restrict access based on pre-defined conditions and real-time context.
- Simplified Identity Governance: Streamline access procedures to maintain high security standards while ensuring that legitimate users can quickly access the resources they need.
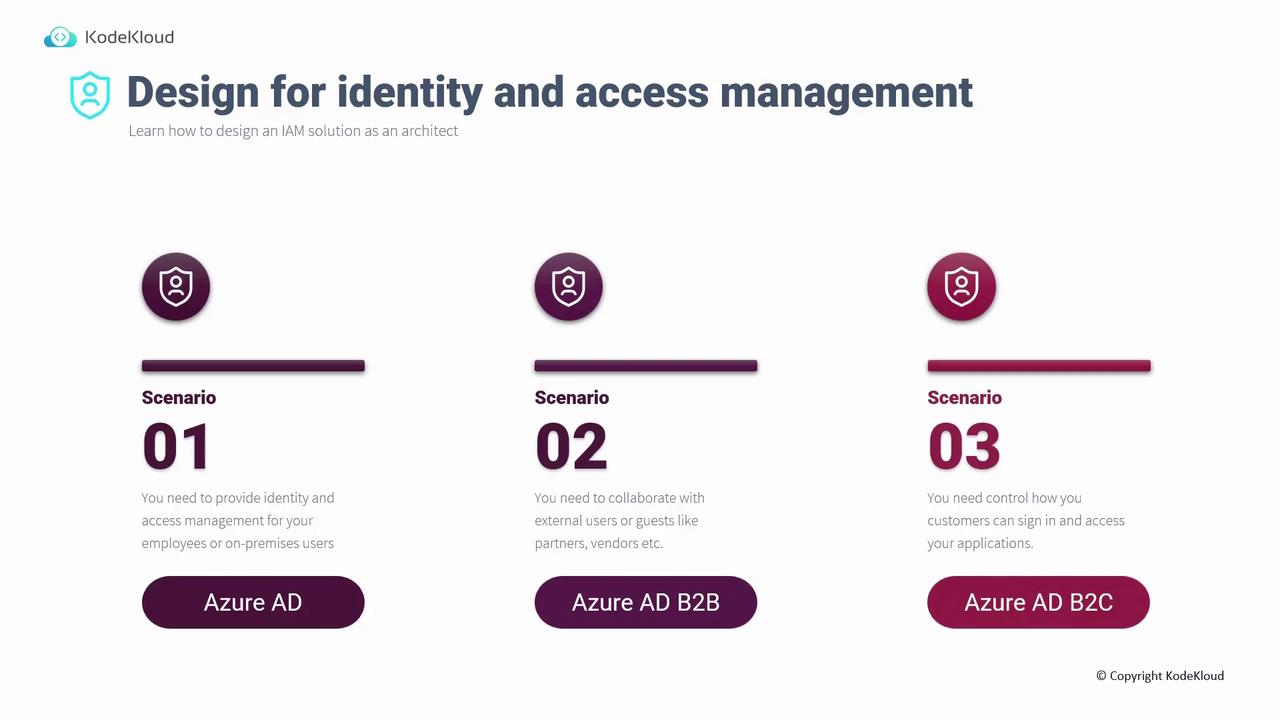
IAM Scenarios and Azure Solutions
IAM plays a critical role in various scenarios. Below are several common use cases along with their corresponding Azure solutions:
Employee and On-Premises User Management:
Manage internal users seamlessly regardless of their location with Azure Active Directory. Azure AD centralizes identity management, while Azure Active Directory Connect synchronizes on-premises users with the cloud.Collaborating with External Users or Guests:
Enhance collaboration by enabling secure access for external partners, vendors, or guests through Azure AD B2B. This solution allows external users to access your systems securely without the need for separate credentials.Customer-Facing Access Control:
For customer-centric applications like e-commerce platforms, manage user access with Azure AD B2C. This solution offers a secure and customizable way for customers to sign in and interact with your applications.
Choosing the Right Azure Solution
Selecting the appropriate Azure solution for your IAM needs ensures that identity management remains secure, streamlined, and tailored to your organization's specific requirements.
Watch Video
Watch video content