AZ900: Microsoft Azure Fundamentals
Governance and Compliance
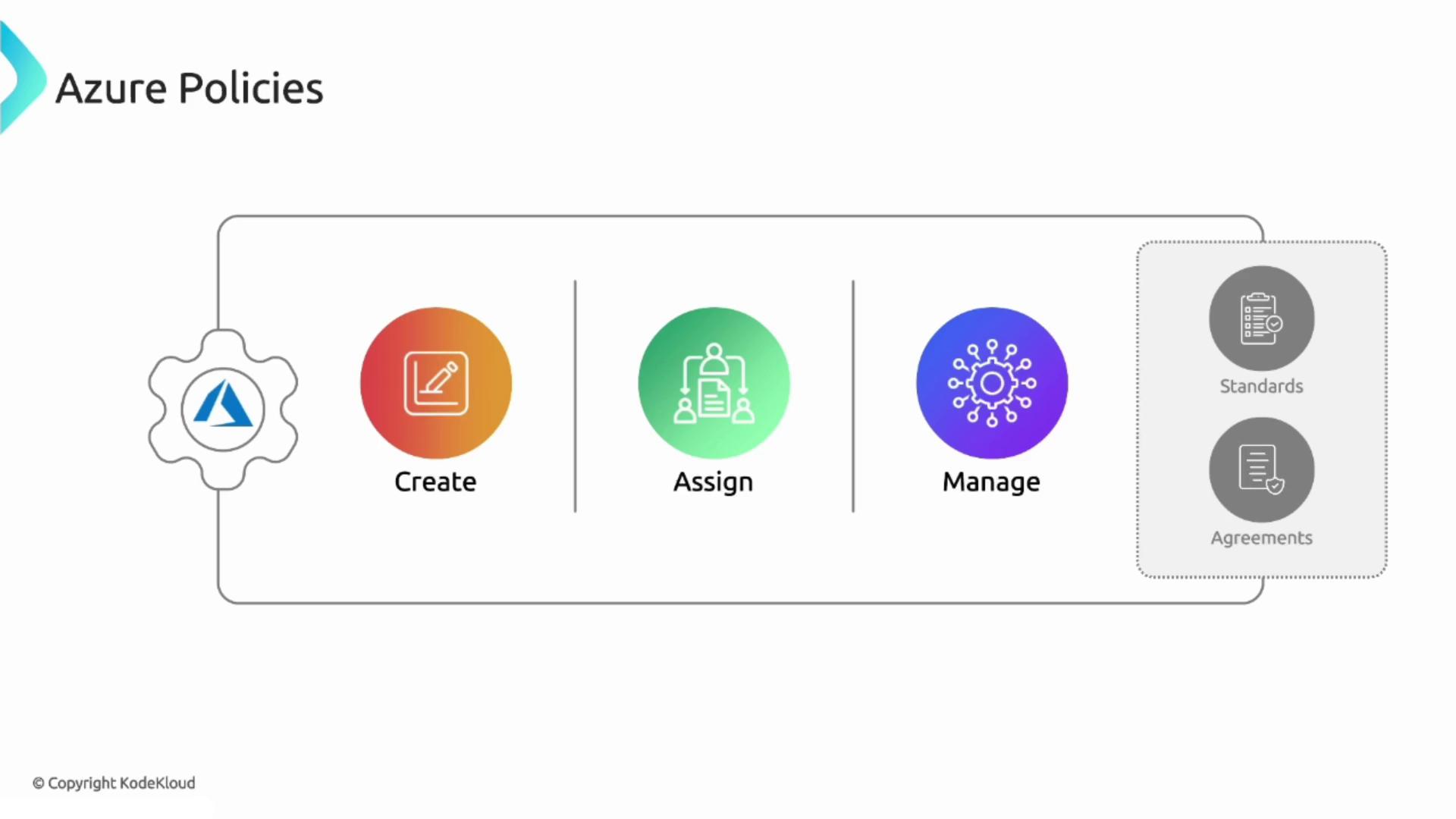
Azure Policies
Azure Policies empower organizations, such as Bella Innovations, to enforce organizational standards and ensure compliance with industry benchmarks like ISO 27001 and PCI DSS. This comprehensive guide explains how to use Azure Policies to assess compliance and enforce regulatory standards.

Azure Policy is a service designed to help you create, assign, and manage policies that govern your resources effectively. By ensuring all resources adhere to your organizational standards and service level agreements (SLAs), Azure Policy plays a crucial role in maintaining compliance. Below, we showcase a practical example of its usage.
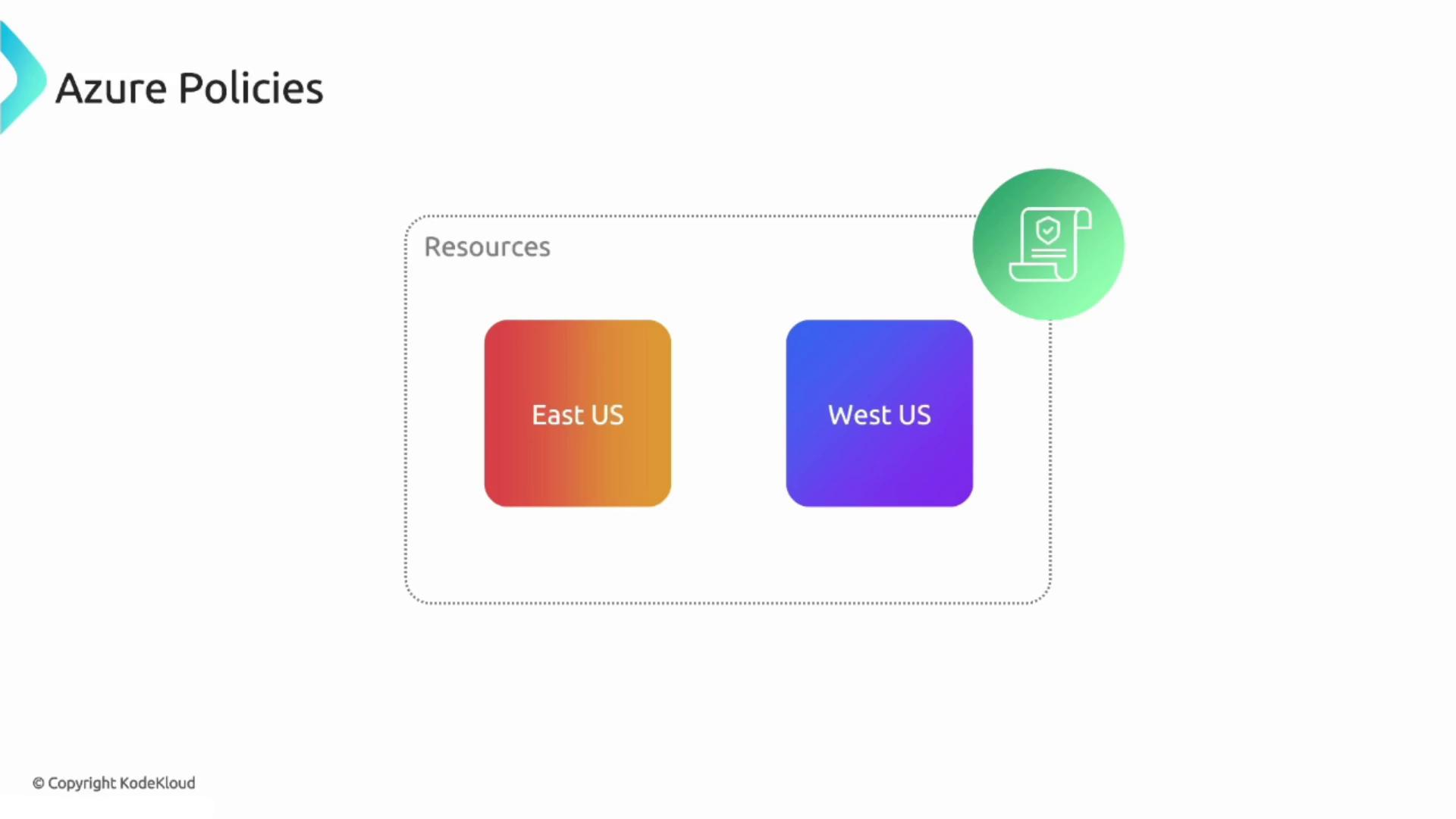
Imagine your organization restricts resource deployments to only the East US and West US regions. Even if users have permission to deploy resources in any region, a policy can enforce this constraint. During deployment, a validation process checks the selected region against the policy. If the region is not among the allowed locations, the deployment is blocked.
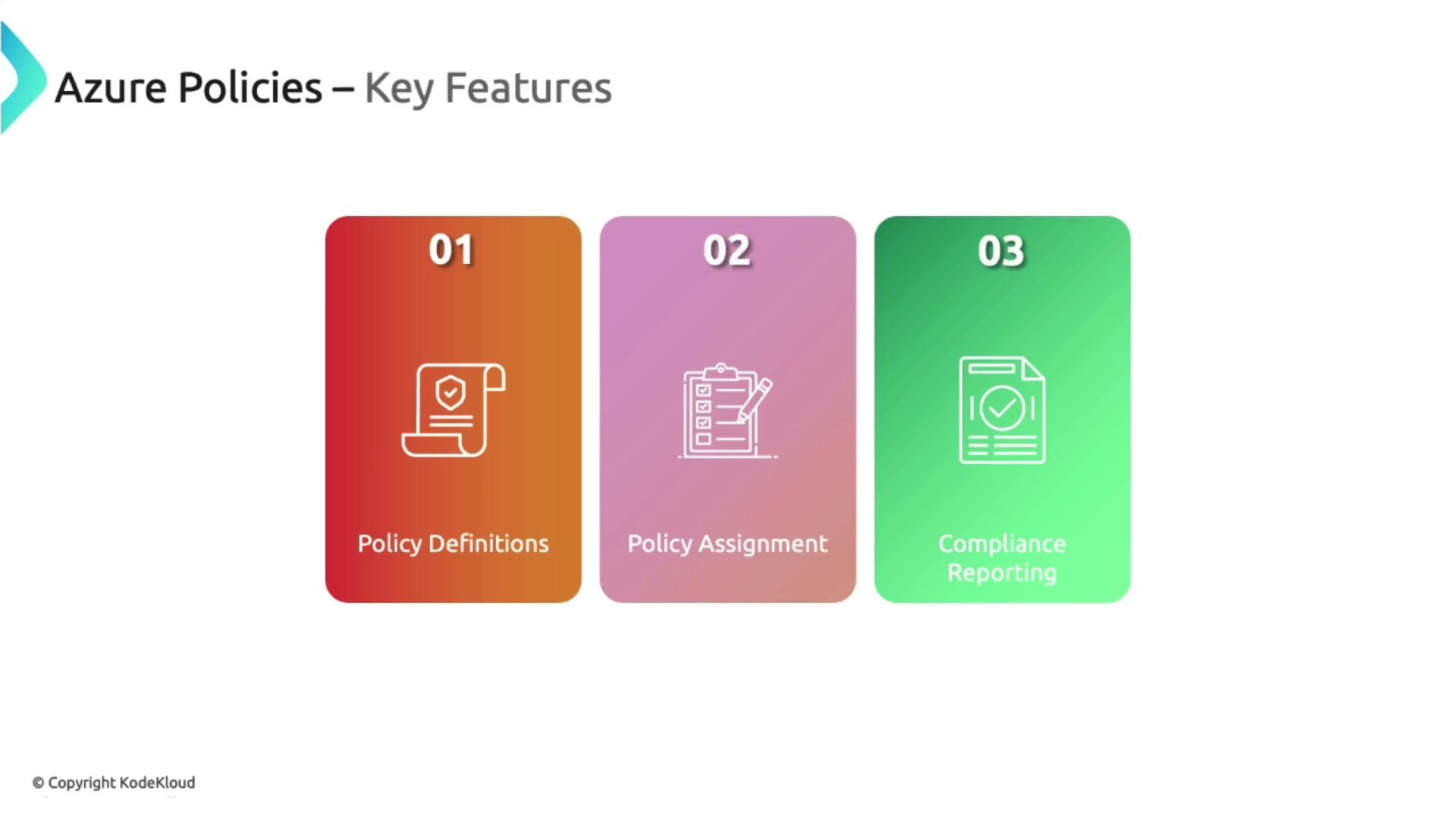
Key Features of Azure Policy
- Policy Definitions: Establish the core rules and effects to enforce when resource configurations do not comply.
- Policy Assignments: Assign policies at various scopes, including resource groups, subscriptions, or management groups.
- Compliance Reporting: Track and report on the compliance status of resources, ensuring alignment with standards like PCI DSS.
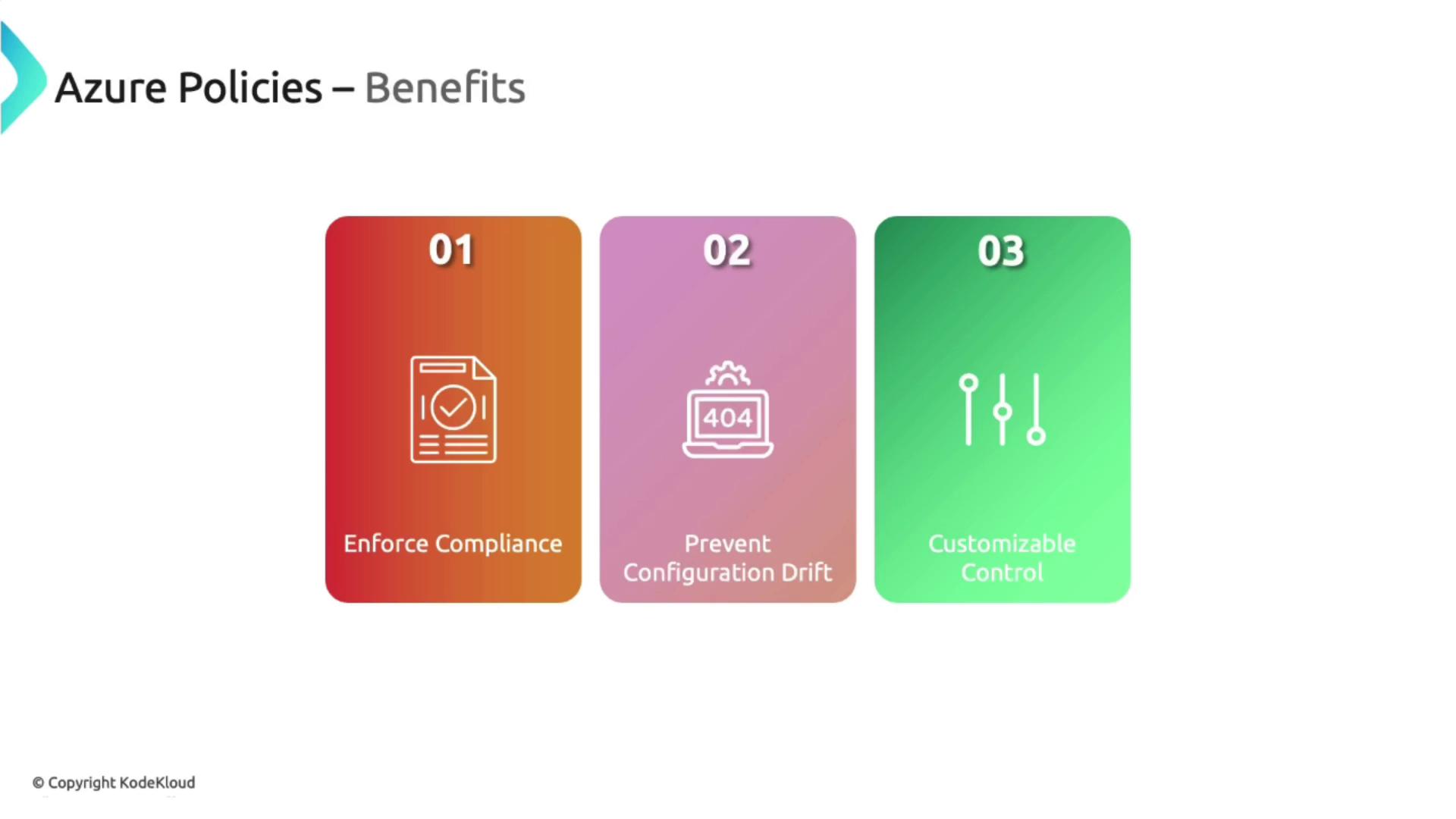
Benefits and Use Cases
Azure Policy provides numerous benefits:
- Enforcing Compliance: Guarantees that all resources meet corporate and regulatory standards.
- Preventing Configuration Drift: Automatically maintains consistency by blocking unauthorized changes.
- Customizable Control: Allows you to tailor policies specific to your organizational needs.
Azure Policy is an ideal solution for maintaining security standards and managing costs in your Azure environment. For example, by restricting the deployment of expensive virtual machine sizes, you can prevent unintended cost overruns.
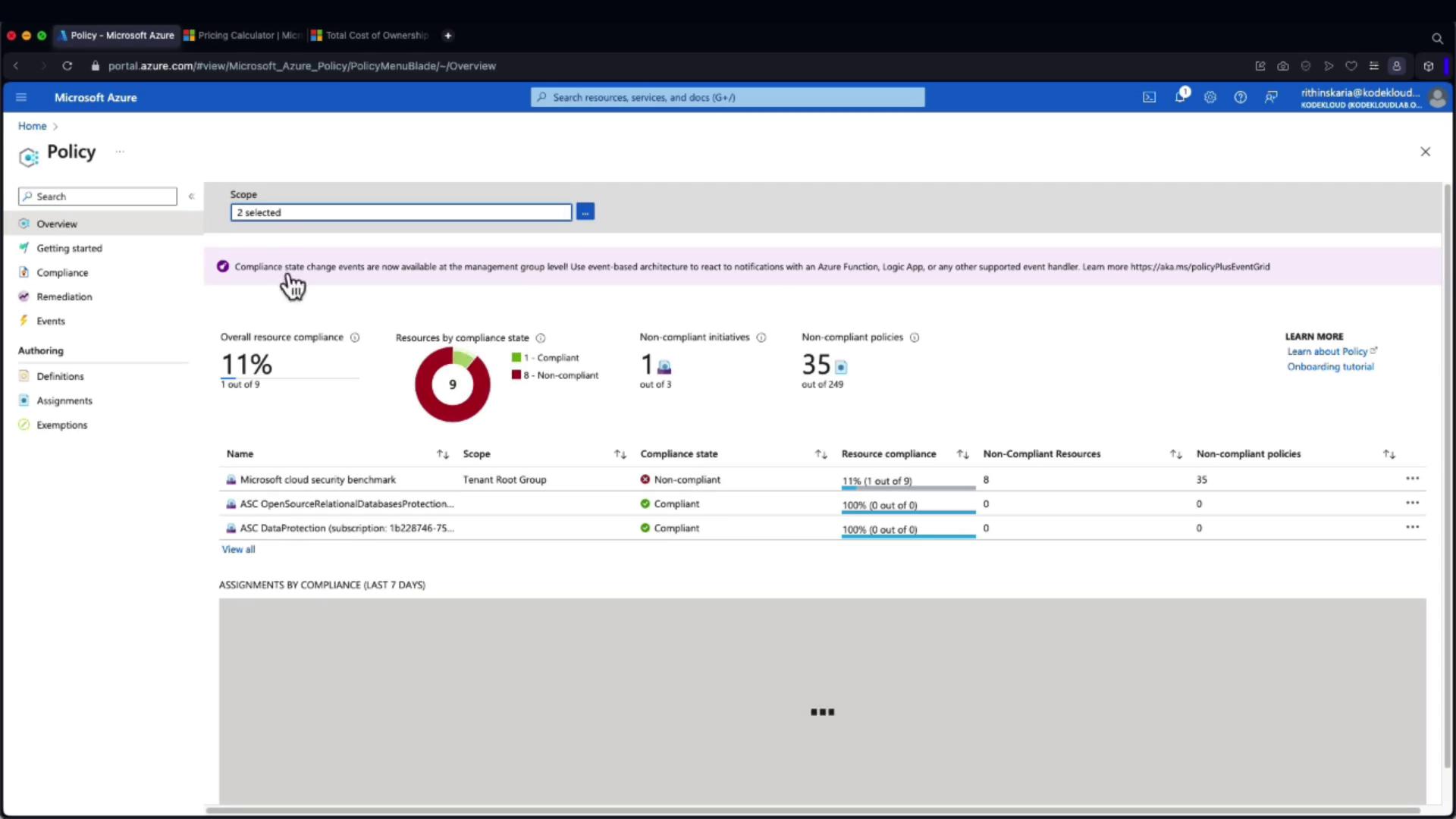
Azure Policy Demonstration in the Azure Portal
Within the Azure Portal, navigate to the Policy section to view compliance data. The dashboard provides an overview of your resource compliance status, highlights non-compliant initiatives, and offers detailed policy insights.
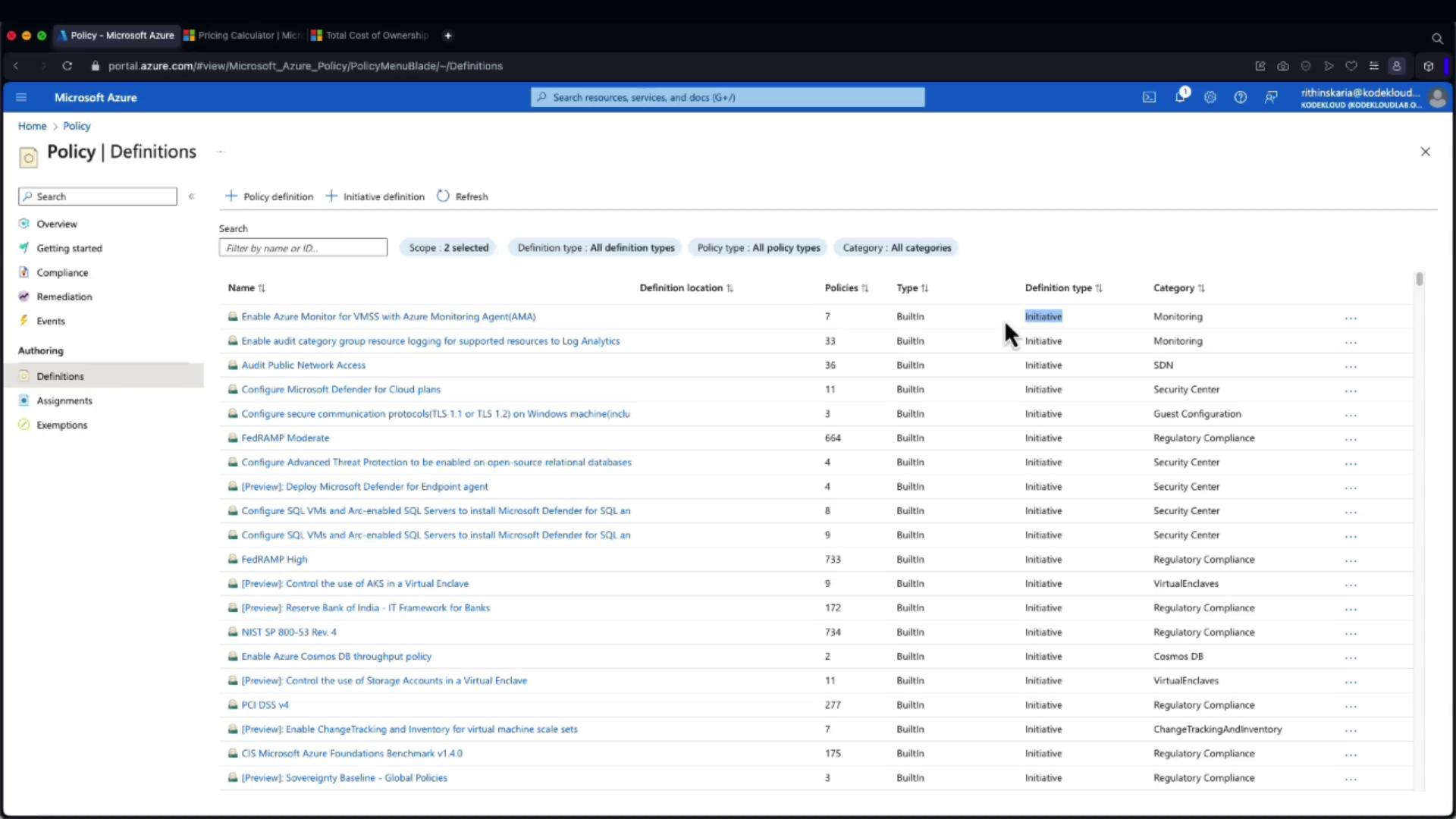
Under the Definitions section, you can explore built-in policies and create customized ones. Initiatives, which are groups of related policies, can also be assigned together for simplified management.
Tip
Review the built-in policies as a starting point, then customize or combine them as needed to suit your organizational requirements.
Example: Allowed Locations Policy
An example of a built-in policy is the "Allowed locations" policy, which restricts resource deployments to approved regions. Below is the JSON definition for this policy:
{
"properties": {
"displayName": "Allowed locations",
"policyType": "BuiltIn",
"mode": "Indexed",
"description": "This policy enables you to restrict the locations your organization can specify when deploying resources. Use to enforce your geo-compliance requirements. Excludes resource groups, Microsoft.AzureActiveDirectory.",
"metadata": {
"version": "1.0.0",
"category": "General"
},
"version": "1.0.0",
"parameters": {
"listOfAllowedLocations": {
"type": "Array",
"metadata": {
"description": "The list of locations that can be specified when deploying resources.",
"strongType": "Location",
"displayName": "Allowed locations"
}
}
},
"policyRule": {
"if": {
"field": "Location",
"notIn": "[parameters('listOfAllowedLocations')]"
},
"then": {
"field": "Location",
"equals": "global"
}
}
}
}
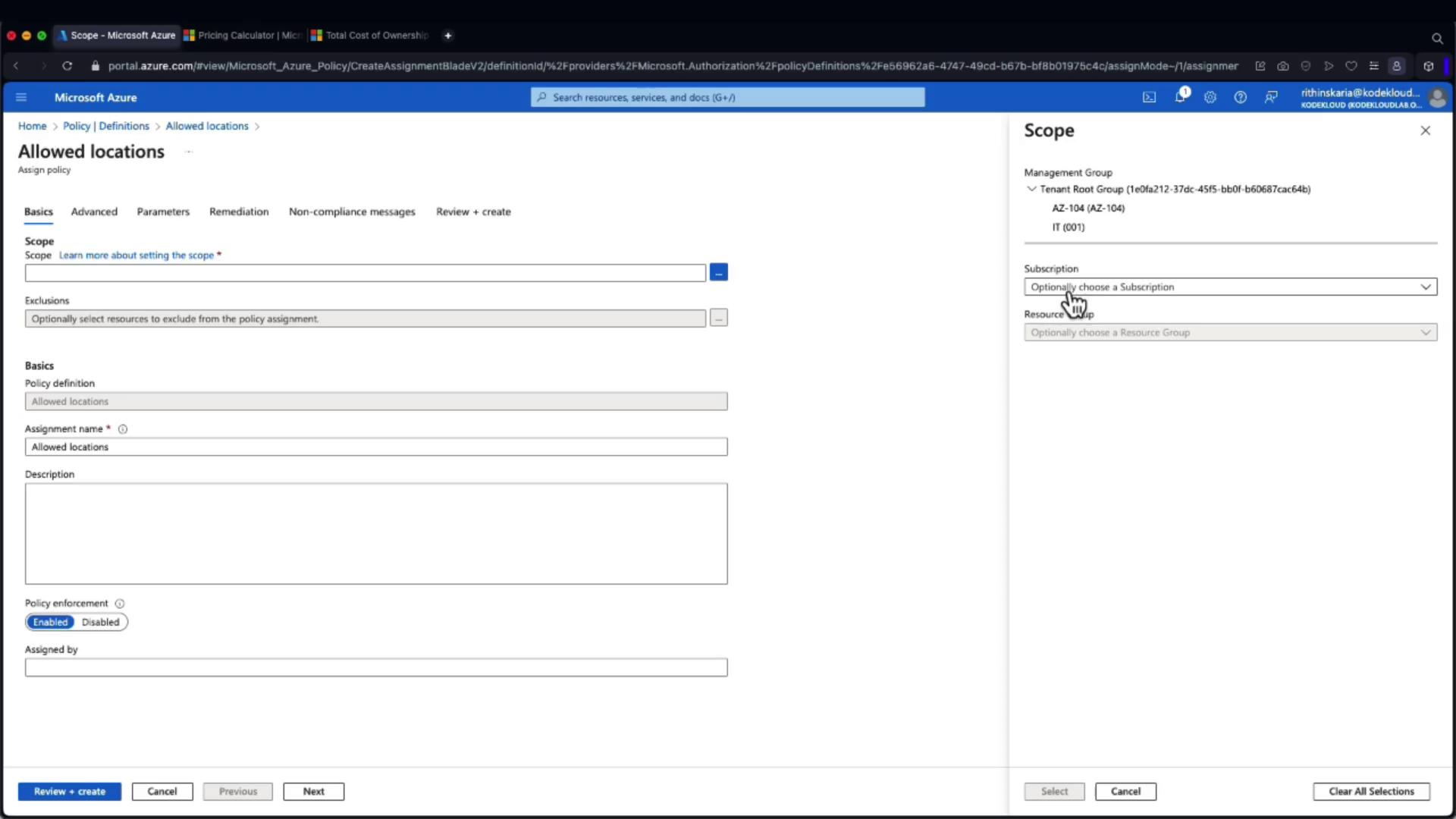
To enforce this policy, follow these steps:
- Click on Assign Policy.
- Choose the appropriate target scope (management group, subscription, or resource group). You can also specify exclusions for certain resource groups.
- Enter a meaningful assignment name and description.
- In the assignment parameters, select the allowed regions such as East US and West US.
Under the parameters, select the desired regions. For example:
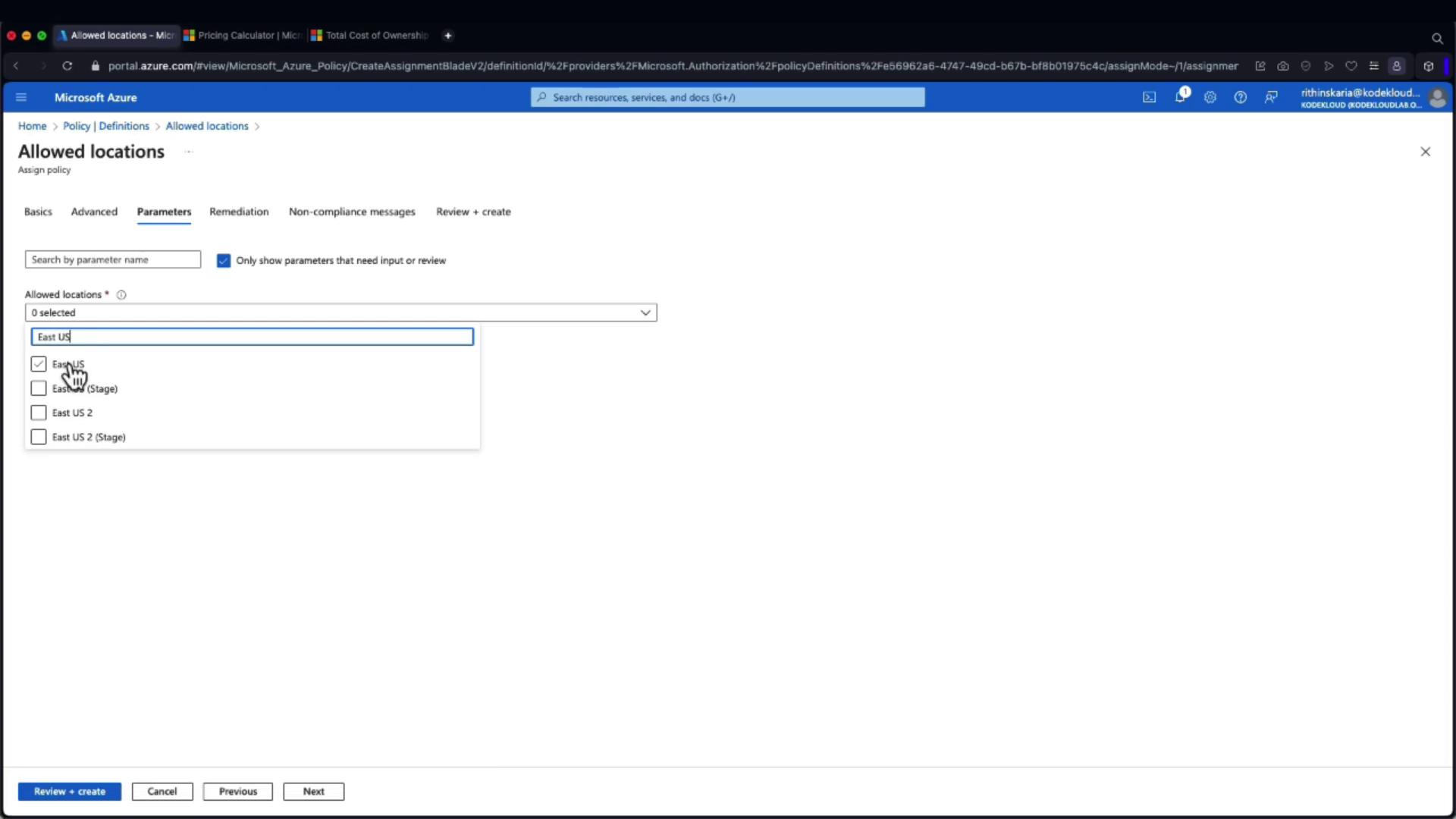
Optionally, you can add a custom non-compliance message that will be shown when a resource deployment is denied. After configuring the assignment, click Create. Note that while policy enforcement begins immediately, it might take 5 to 15 minutes for the changes to propagate.
Verification
To verify the policy, navigate to a resource group where it’s applied and attempt to create a resource (for example, a Storage Account). If you choose a region outside the allowed set (e.g., Canada Central), the deployment will be blocked during the validation phase. Conversely, choosing an allowed region like West US permits the deployment.
This demonstration clarifies how Azure Policy governs resource deployment locations efficiently, adding an extra layer of control alongside resource locks.
For further details, visit the Azure Policy Documentation.
Watch Video
Watch video content