Amazon Simple Storage Service (Amazon S3)
AWS S3 Management
Demo Access Points
In this tutorial, you’ll learn how to use Amazon S3 Access Points to delegate and isolate access control for different teams. By the end, you will have configured two access points—one for developers and one for finance—each with its own fine-grained policy.
Table of Contents
- Create a Demo Bucket
- Verify Default Access for Other Users
- Create Access Points
- Delegate Bucket Permissions to Access Points
- Define Access Point Policies
- Test Access via Access Points
- Final Permissions Overview
- Conclusion
- Links and References
1. Create a Demo Bucket
First, set up a new S3 bucket named kk-accesspoint with the default settings. Then upload a sample file (beach.jpg) for testing.
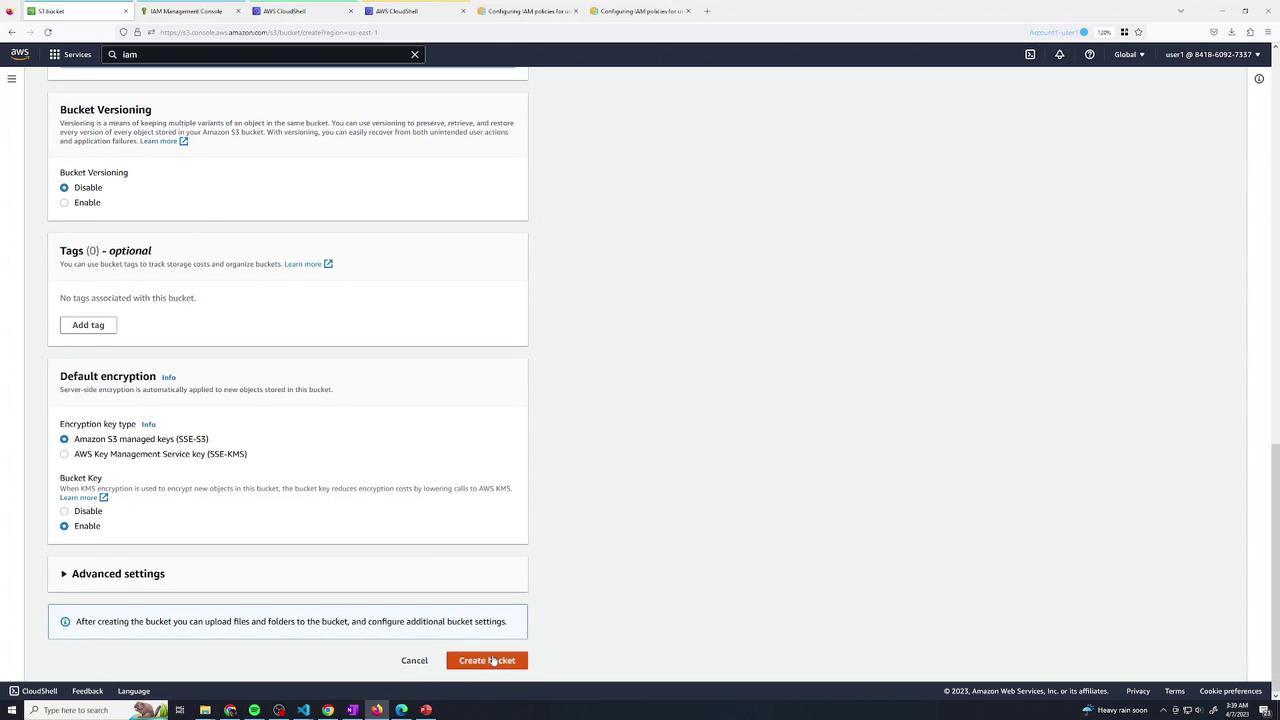
Upload your test asset:
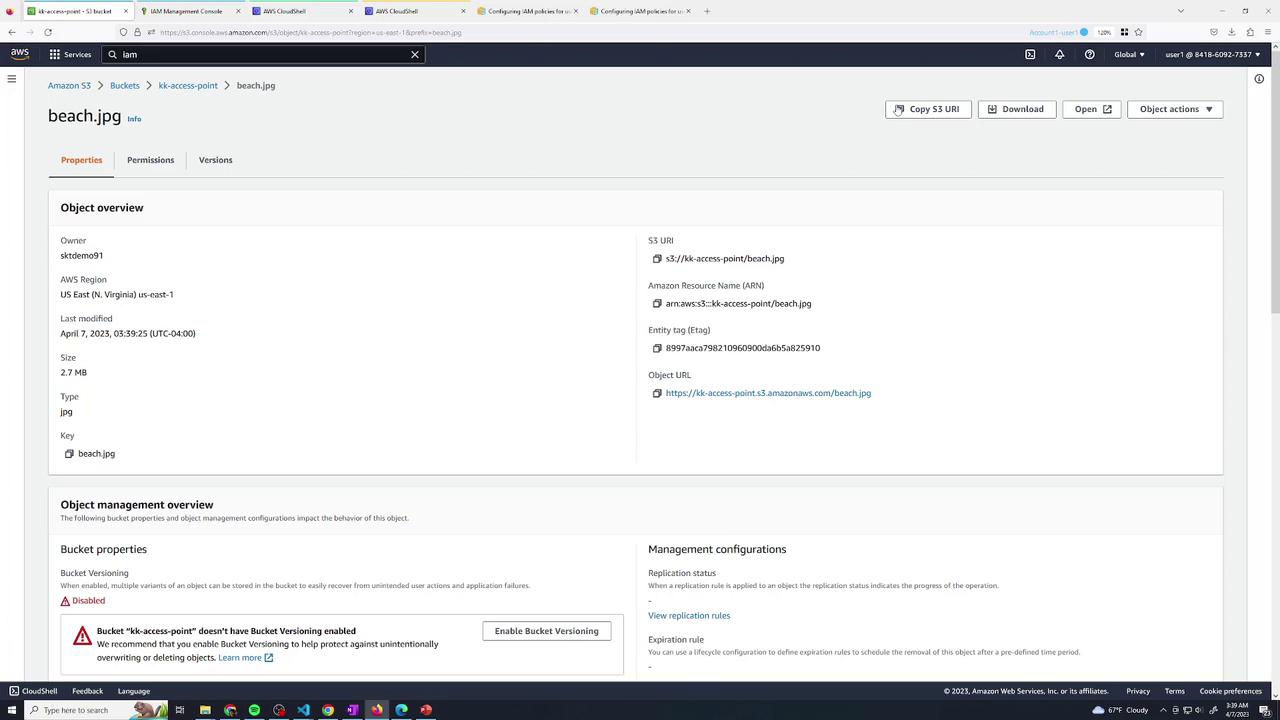
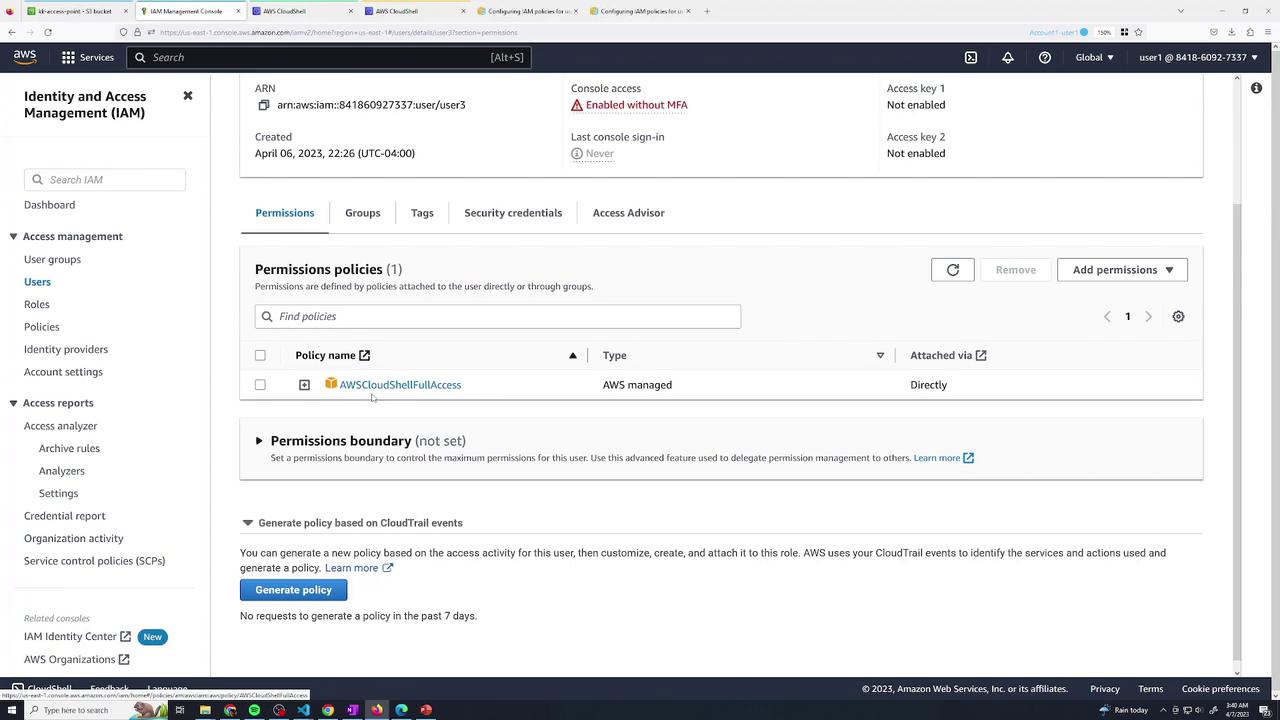
Once uploaded, as the bucket owner (user1), you can view the object details:
Best Practice
Consider enabling versioning and default encryption on production buckets to protect against accidental data loss or unauthorized access.
2. Verify Default Access for Other Users
Assume two IAM users—user2 and user3—each have only CloudShell access. By default, neither can list or retrieve objects from your new bucket.
In AWS CloudShell, both users attempt to list and copy objects:
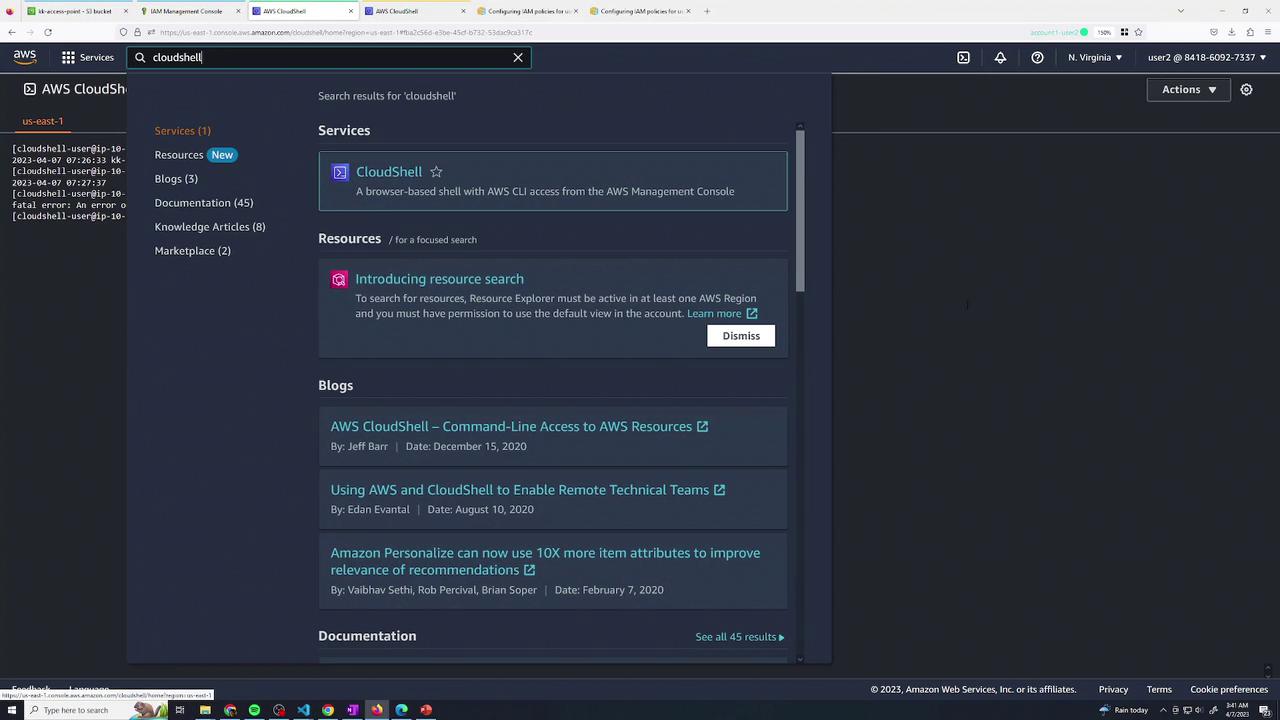
# As user2
[cloudshell-user@ip-... ~]$ aws s3 ls s3://kk-accesspoint/
fatal error: An error occurred (AccessDenied) when calling the ListObjectsV2 operation: Access Denied
[cloudshell-user@ip-... ~]$ aws s3 cp s3://kk-accesspoint/beach.jpg .
fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden
# As user3
[cloudshell-user@ip-... ~]$ aws s3 ls s3://kk-accesspoint/
fatal error: An error occurred (AccessDenied) when calling the ListObjectsV2 operation: Access Denied
[cloudshell-user@ip-... ~]$ aws s3 cp s3://kk-accesspoint/beach.jpg .
fatal error: An error occurred (403) when calling the HeadObject operation: Forbidden
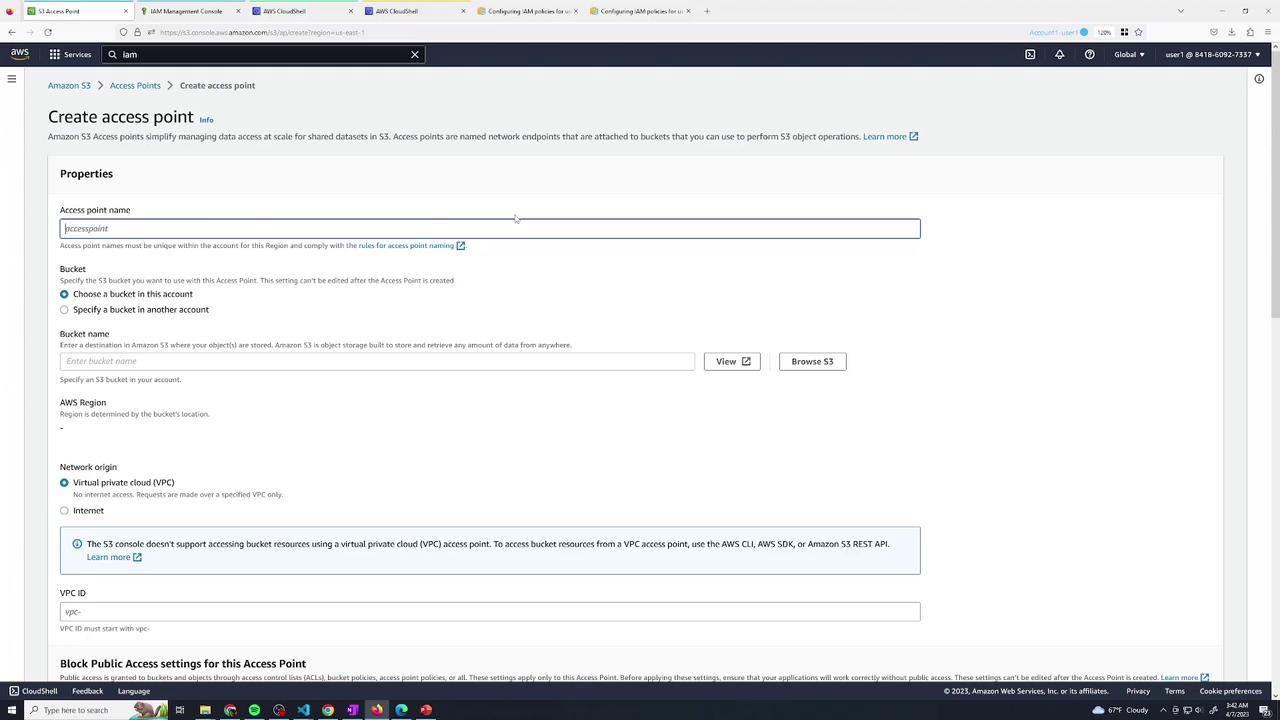
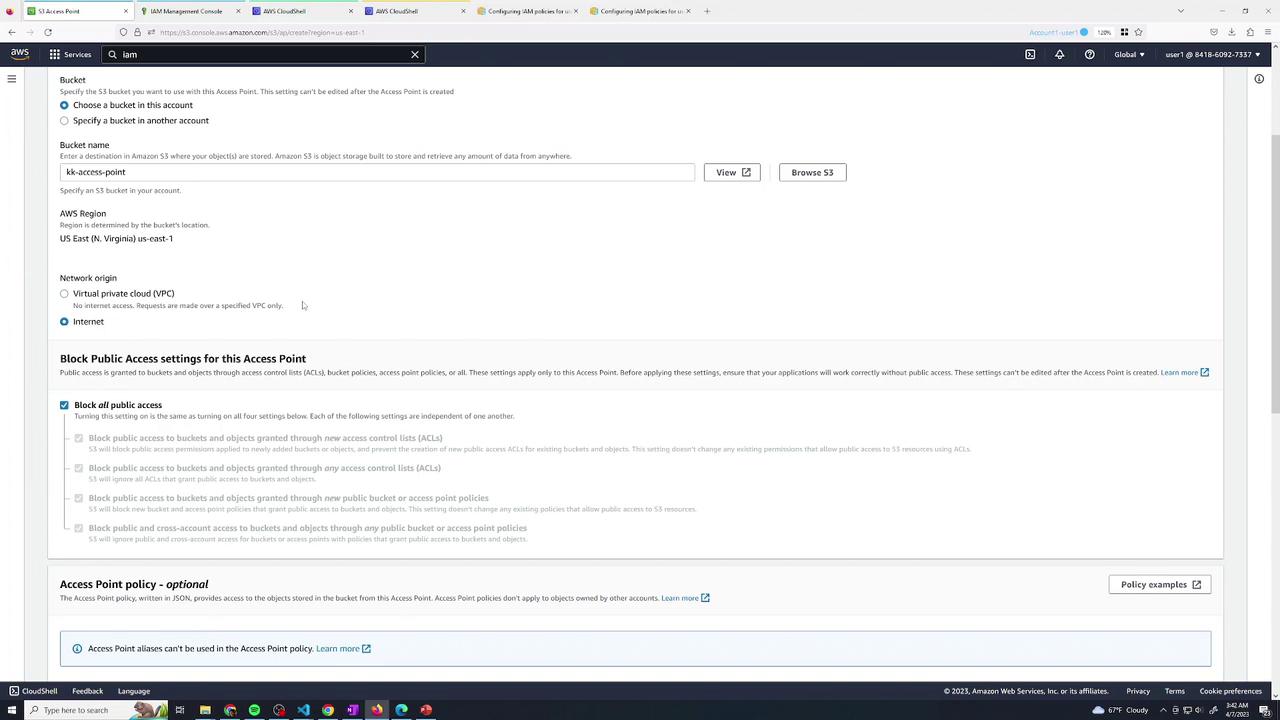
3. Create Access Points
Navigate to Amazon S3 → Access points and create two points:
- developers (for user2)
- finance (for user3)
Select kk-accesspoint as the data source, choose Internet for Network origin, and keep public access blocking enabled.
Public Access
Always keep Block all public access enabled on buckets and access points to prevent accidental exposure.
4. Delegate Bucket Permissions to Access Points
To let your access points list bucket contents, add this bucket policy. Replace 123456789012 with your AWS account ID:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::kk-accesspoint",
"Condition": {
"StringEquals": {
"s3:DataAccessPointAccount": "123456789012"
}
}
}
]
}
Apply under Bucket → Permissions → Bucket policy:
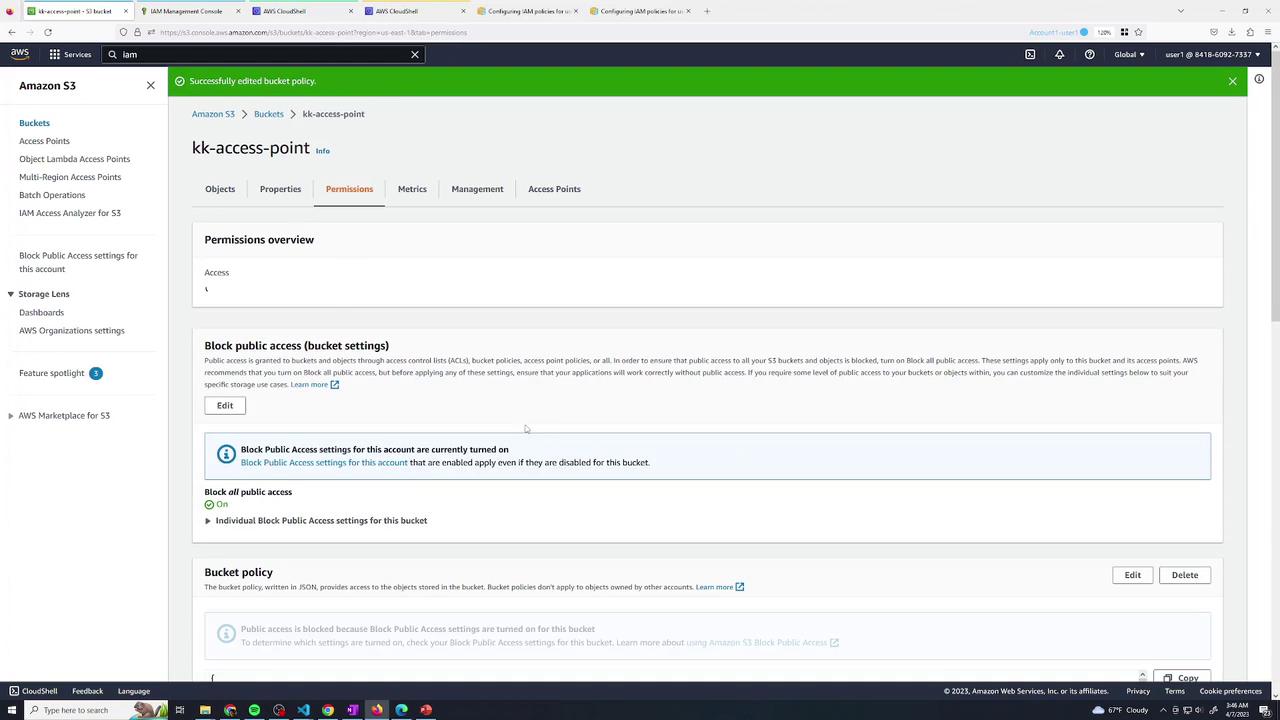
5. Define Access Point Policies
5.1 Developer Access Point Policy
Go to Access points → developers → Permissions → Edit and paste:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:user/user2"
},
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:us-east-1:123456789012:accesspoint/developers",
"arn:aws:s3:us-east-1:123456789012:accesspoint/developers/object/*"
]
}
]
}
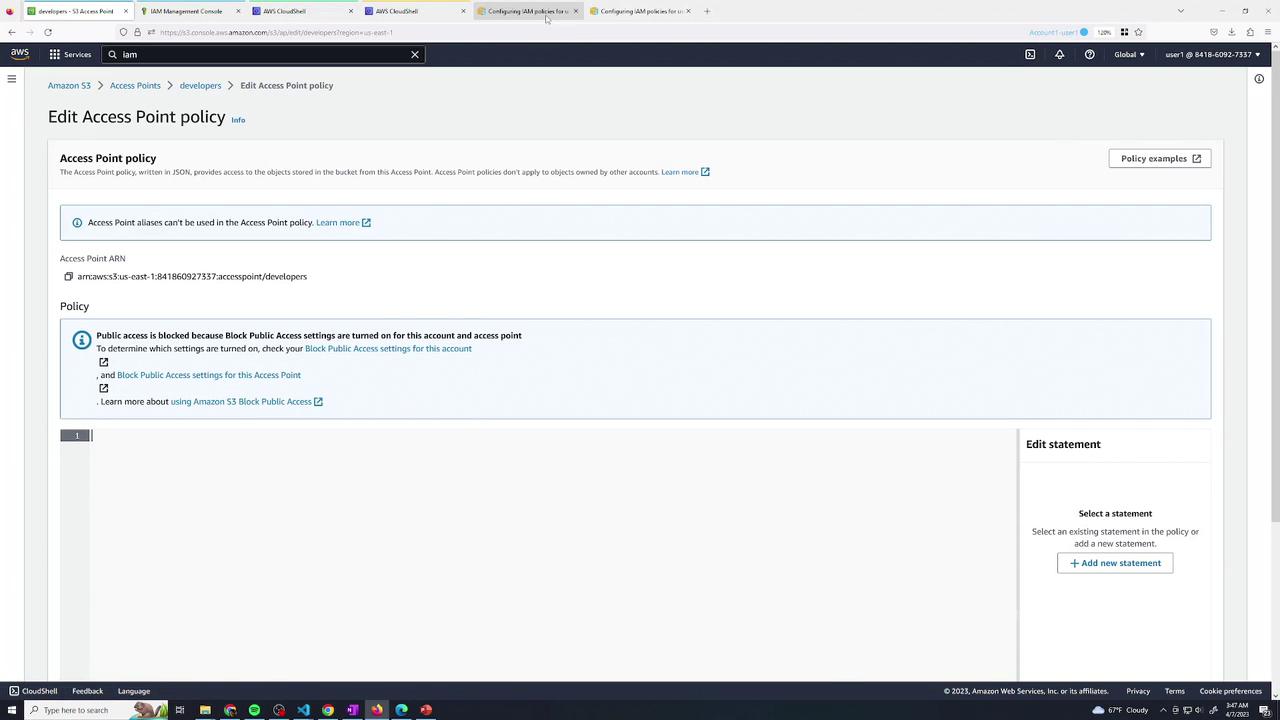
5.2 Finance Access Point Policy
For finance, allow user3:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:user/user3"
},
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:us-east-1:123456789012:accesspoint/finance",
"arn:aws:s3:us-east-1:123456789012:accesspoint/finance/object/*"
]
}
]
}
After saving, review each access point’s overview:
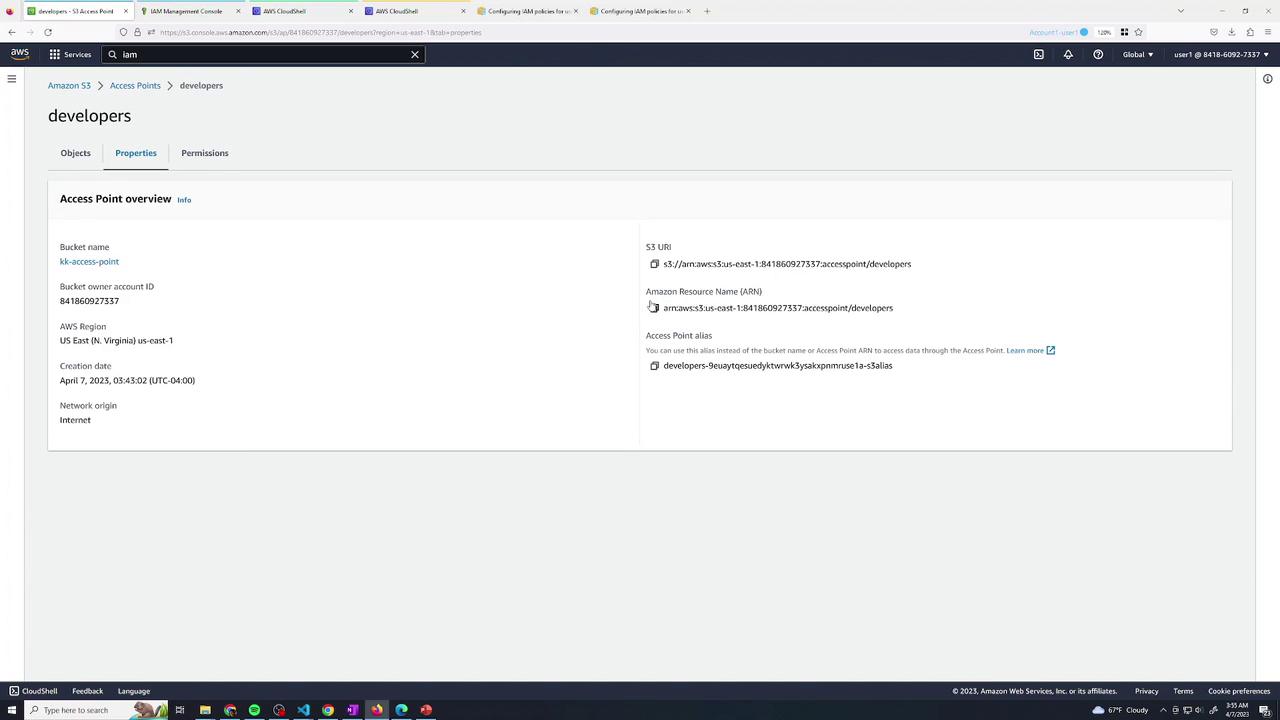
Access Point Summary
| Access Point | Principal | Actions |
|---|---|---|
| developers | arn:aws:iam::123456789012:user/user2 | List, GetObject, PutObject |
| finance | arn:aws:iam::123456789012:user/user3 | List, GetObject, PutObject |
6. Test Access via Access Points
6.1 Developer (user2)
In AWS CloudShell as user2, list and copy via the developers access point ARN:
# List via developers access point
[cloudshell-user@... ~]$ aws s3 ls s3://arn:aws:s3:us-east-1:123456789012:accesspoint/developers
2023-09-04 07:39:25 2879314 beach.jpg
# Download the object
[cloudshell-user@... ~]$ aws s3 cp s3://arn:aws:s3:us-east-1:123456789012:accesspoint/developers/beach.jpg .
6.2 Finance (user3)
As user3, perform the same steps and upload a new file:
# List via finance access point
[cloudshell-user@... ~]$ aws s3 ls s3://arn:aws:s3:us-east-1:123456789012:accesspoint/finance
2023-09-04 07:39:25 2879314 beach.jpg
# Download the object
[cloudshell-user@... ~]$ aws s3 cp s3://arn:aws:s3:us-east-1:123456789012:accesspoint/finance/beach.jpg .
# Upload a test file
[cloudshell-user@... ~]$ touch test1
[cloudshell-user@... ~]$ aws s3 cp test1 s3://arn:aws:s3:us-east-1:123456789012:accesspoint/finance/test1
# Verify both files
[cloudshell-user@... ~]$ aws s3 ls s3://arn:aws:s3:us-east-1:123456789012:accesspoint/finance
2023-09-04 07:39:25 2879314 beach.jpg
2023-09-04 07:40:10 0 test1
7. Final Permissions Overview
Inspect the finance access point’s permissions tab:
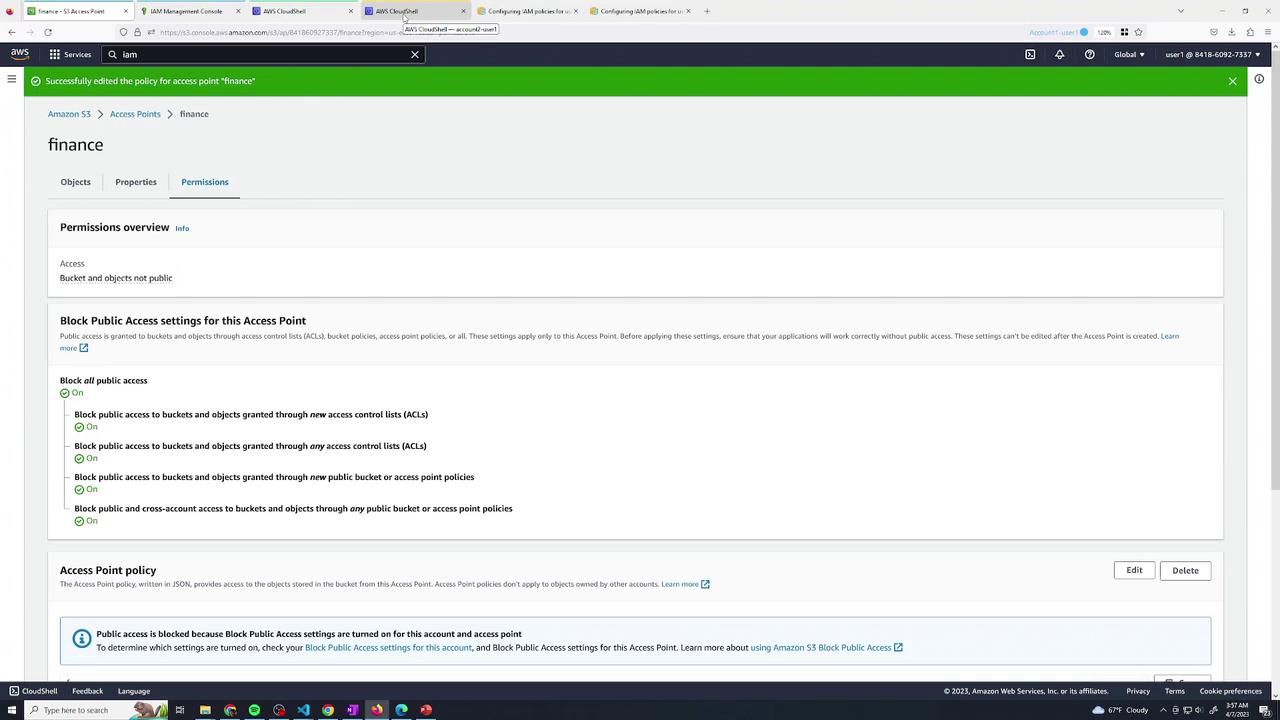
8. Conclusion
By leveraging S3 Access Points, you can:
- Delegate access control to distinct teams without modifying the main bucket policy.
- Create isolated entry points with tailored permissions.
- Simplify management when multiple user groups share a bucket.
This approach improves security posture and operational efficiency in multi-team environments.
9. Links and References
Watch Video
Watch video content