CKA Certification Course - Certified Kubernetes Administrator
Security
Security Section Introduction
Hello, and welcome to this comprehensive article on Kubernetes security. My name is Mumshad Mannambeth, and in this guide, we will begin by exploring the security primitives of Kubernetes. We will explain how access is granted to a Kubernetes cluster, how various actions are controlled, and review the different authentication mechanisms available. Additionally, we will examine the default configurations of a cluster and demonstrate how to view the configurations of an existing cluster.
Below is an example CSV file containing user details:
user-details.csv
password123,user1,u0001
password123,user2,u0002
password123,user3,u0003
password123,user4,u0004
password123,user5,u0005
We then discuss TLS certificates and the role they play in securing components within the cluster. If you are a Kubernetes administrator setting up a cluster on your own, you might encounter challenges related to certificate management. This article covers the basics of certificates from the ground up.
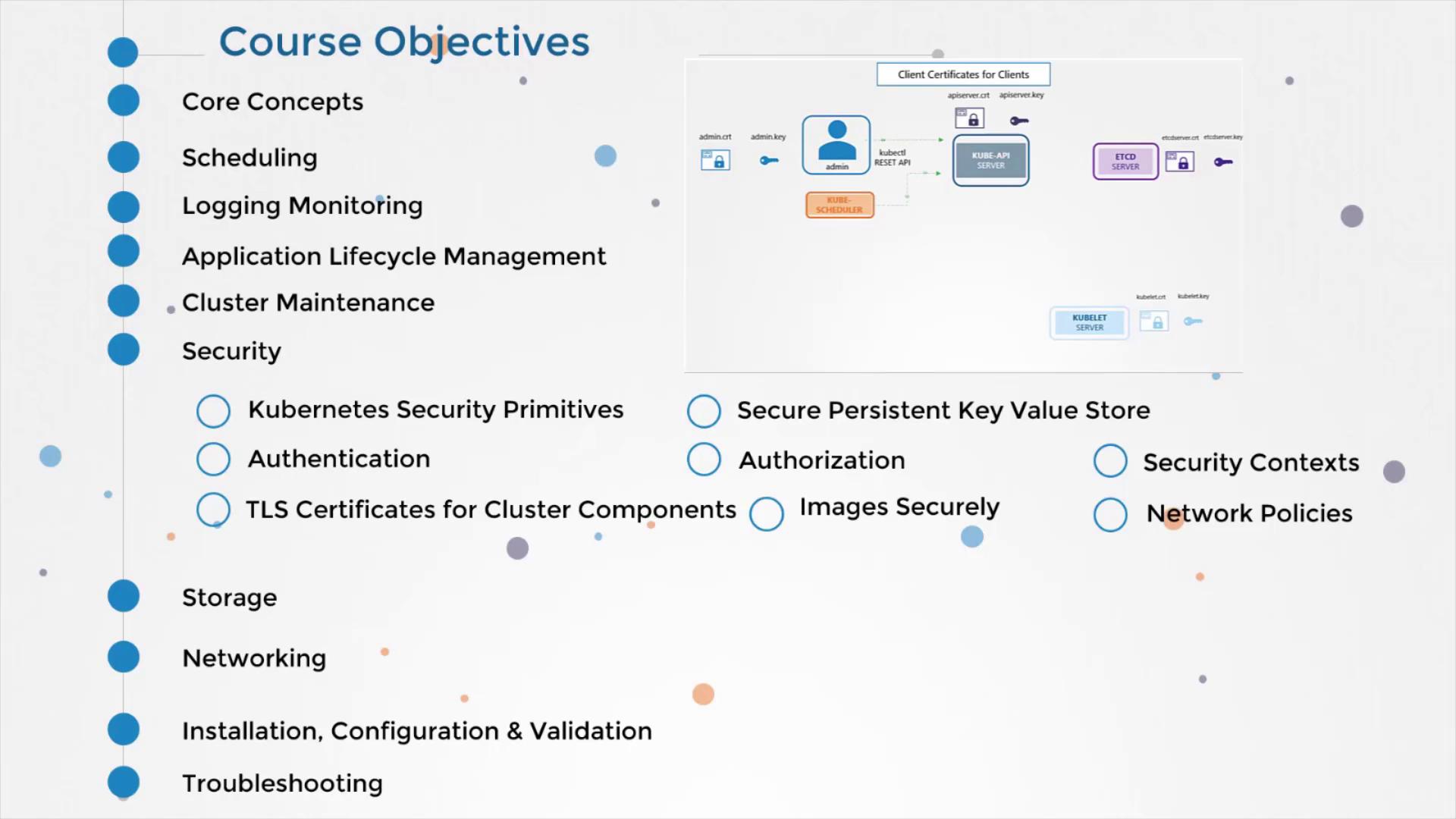
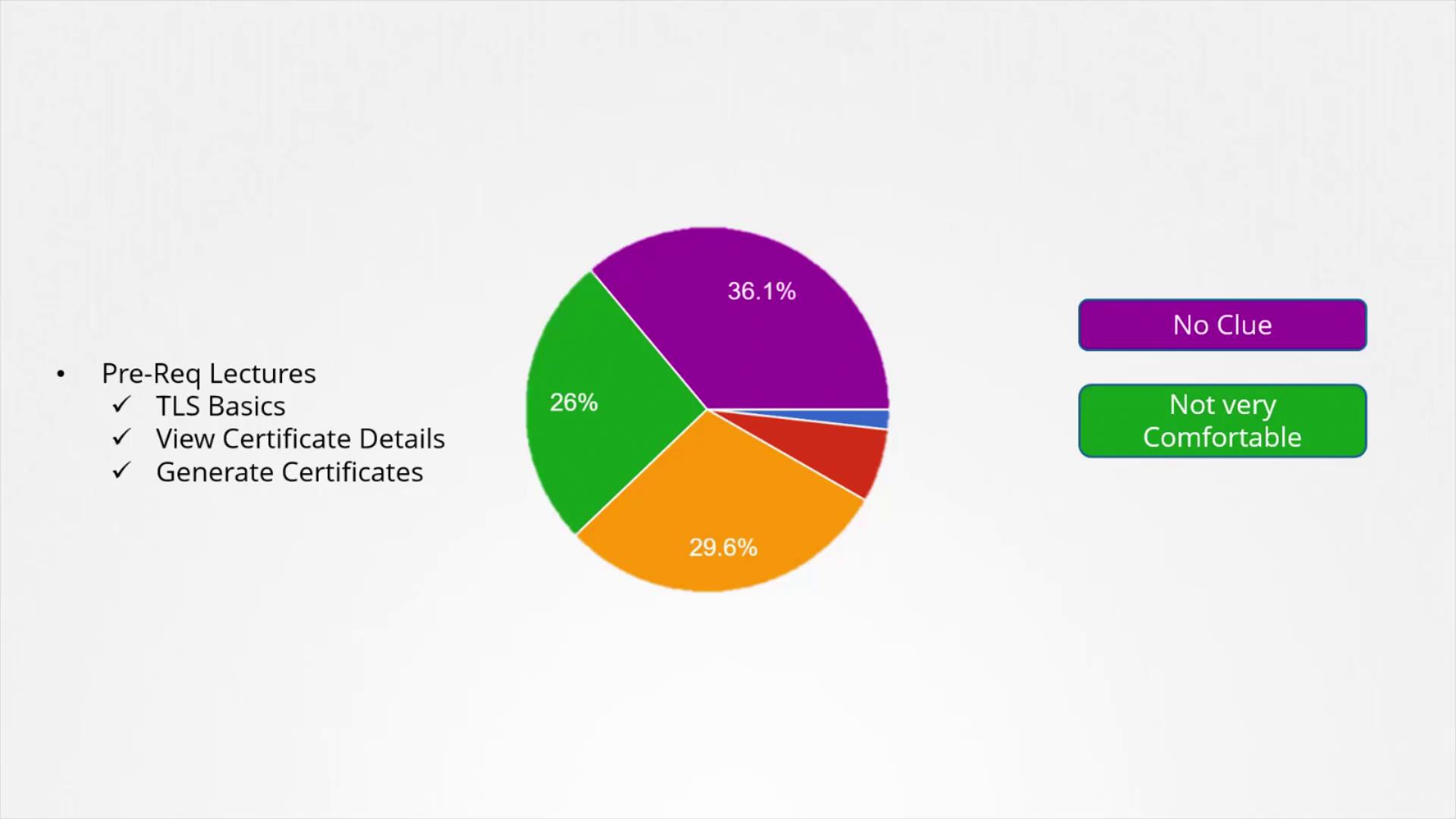
One of the key sections in this article simplifies the core concepts of certificates. For beginners, several prerequisite lectures have been included to build a strong foundation. A poll conducted among the audience revealed that most respondents were new to TLS certificates. This valuable feedback prompted a detailed explanation of how certificates are used within Kubernetes, a topic that often confuses newcomers.
Note
The prerequisite lectures and accompanying practice tests are designed to help you bridge any gaps in your understanding of TLS certificates. Depending on your level of expertise, you might choose to skip some of these sessions.
Later in this article, we will dive into authorization with a specific focus on various mechanisms, including role-based access control (RBAC). We will also cover essential topics such as securing container images, implementing security contexts, and configuring network policies. There is a wealth of lectures and practice tests ahead, so take your time and enjoy the learning process.
Watch Video
Watch video content