Chaos Engineering
Chaos Engineering on Database Aurora
Demo Pre requisite for FIS experiment Create IAM role and Current State
In this guide, we’ll verify the configuration of our Aurora PostgreSQL cluster and set up the IAM role required for AWS Fault Injection Simulator (FIS).
1. Review Aurora PostgreSQL Cluster Configuration
Ensure your Aurora PostgreSQL cluster is deployed regionally with the following setup:
| Instance Role | Availability Zone | Status |
|---|---|---|
| Writer | us-east-1a | Available |
| Reader | us-east-1b | Available |
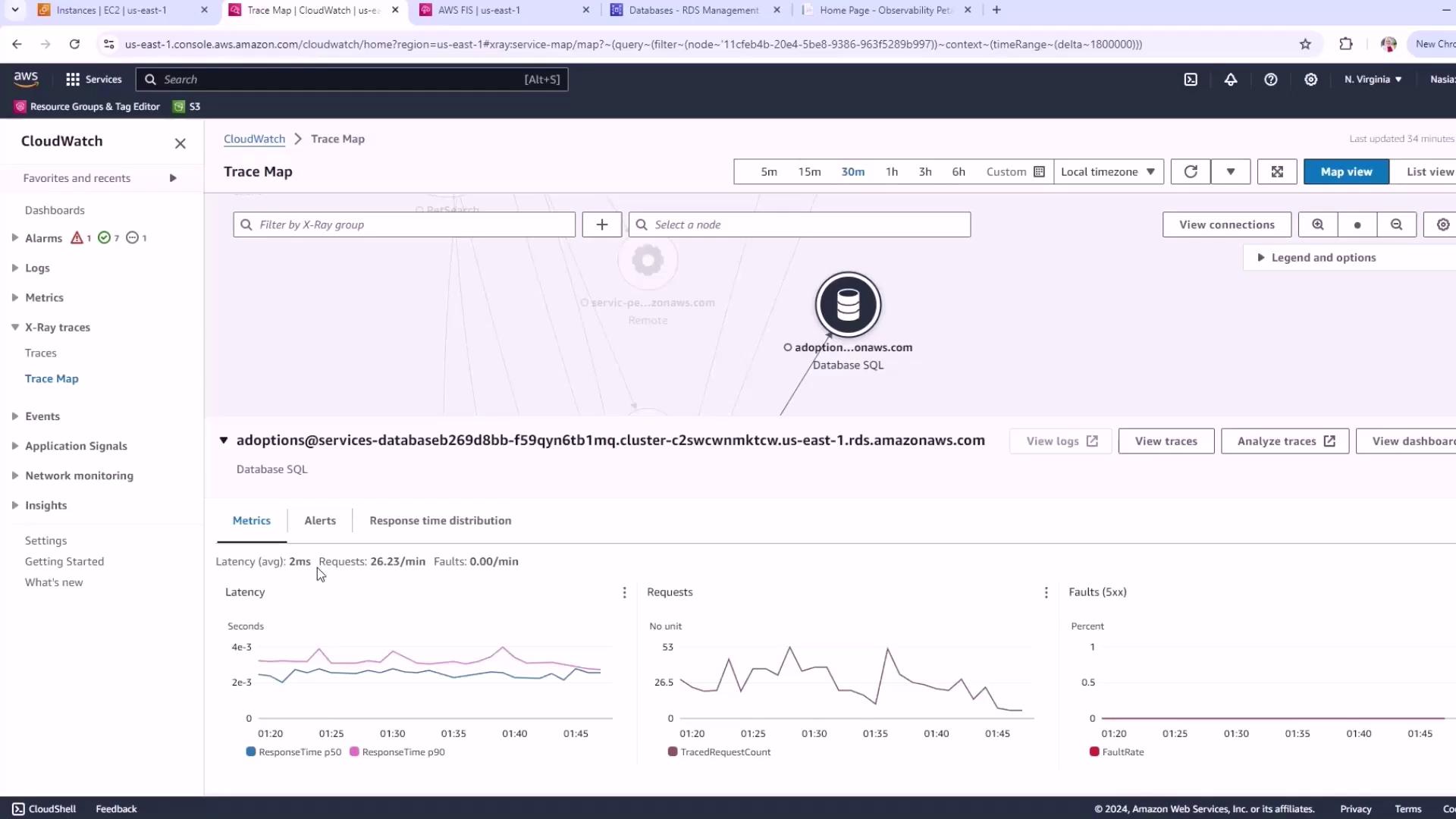
2. Establish Baseline Metrics in CloudWatch
Before running an FIS experiment, capture steady-state performance metrics:
- Open the AWS Console and navigate to CloudWatch → X-Ray Trace Map.
- Select your target database (e.g., the
adoptionPostgreSQL cluster). - Set the time range to the last 30 minutes.
You should observe metrics similar to these:
| Metric | Typical Value |
|---|---|
| Latency | ~2 ms |
| Request Rate | ~26 requests/min |
| Faults | None |
Note
Recording baseline metrics is essential for measuring the impact of your FIS experiments. Always capture steady-state data first.
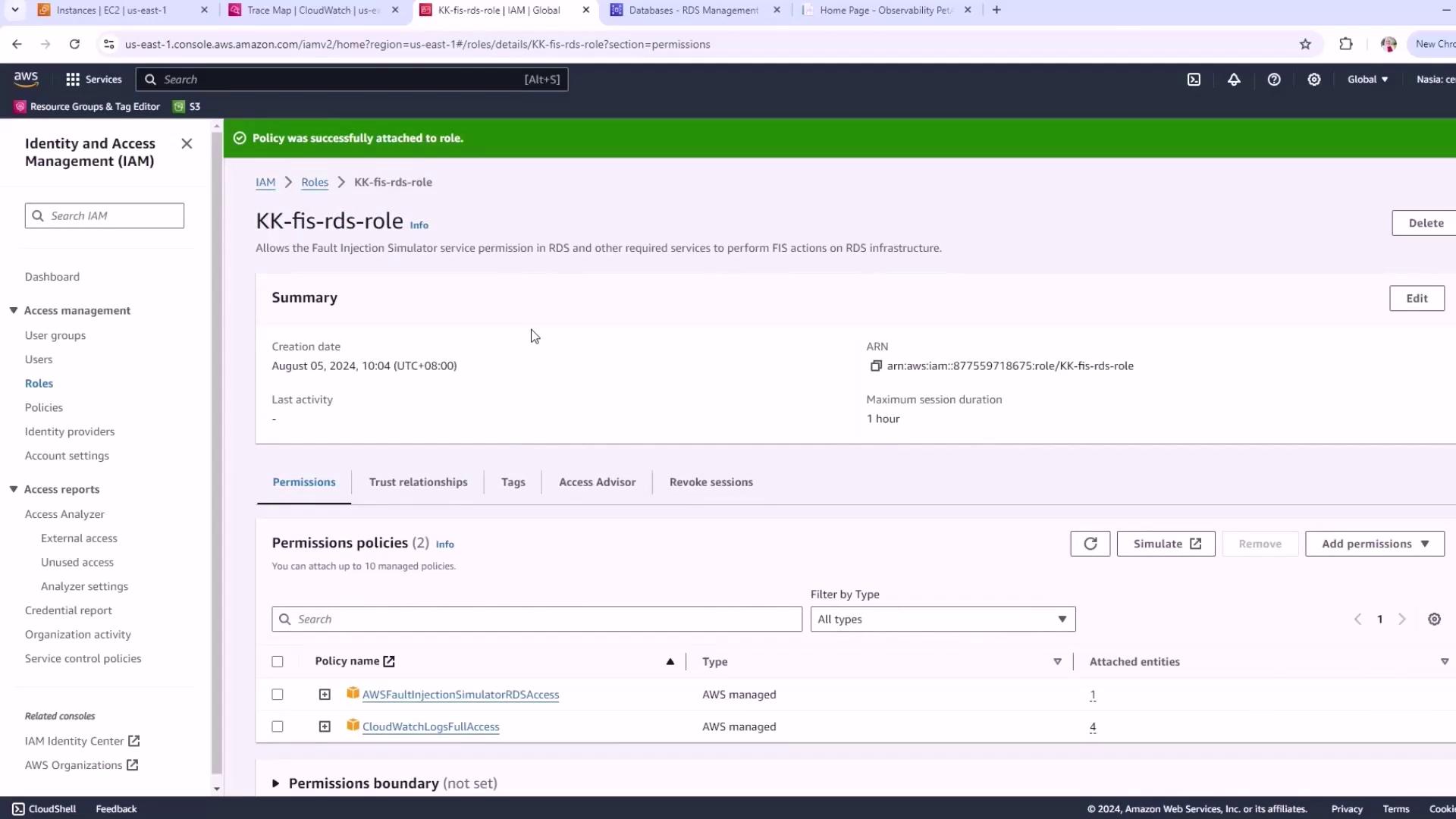
3. Create an IAM Role for FIS
AWS FIS needs permission to act on your RDS resources and write logs. Follow these steps:
Navigate to IAM → Roles → Create role.
Under Trusted entity, choose AWS service, then select FIS.
For Use case, pick RDS.
Name the role
FISRDSRole.In the Trust policy editor, replace the JSON with:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": ["sts:AssumeRole"], "Principal": { "Service": ["fis.amazonaws.com"] } } ] }Attach the managed policy
CloudWatchLogsFullAccess(or a least-privilege equivalent) to enable logging.
Your IAM role is now ready to be selected when you configure and run your FIS experiment.
Warning
Always follow the principle of least privilege. Grant only the permissions necessary for your FIS experiments to reduce security risks.
References
Watch Video
Watch video content