CompTIA Security+ Certification
Controls and Security Concepts
Categories of Controls
Understanding the different categories of security controls is critical for developing a robust security strategy. In this article, we break down these controls into two primary segments: those implemented by people and those enforced through technical and physical measures.
People-Based Controls
People-based controls are divided between managerial and operational functions.
Managerial Controls:
These controls involve policies and directives established by organizational leadership. They encompass security policies, guidelines, and procedures that employees are required to follow.Operational Controls:
These controls are executed by non-managerial staff, such as security personnel who handle tasks like data labeling and classification. They are essential in maintaining day-to-day security protocols.
Technology and Physical Controls
The next category includes controls that are implemented through technical means and physical measures.
Technical Controls:
These are enforced by hardware, software, or firmware. Key examples include firewalls, anti-malware software, virus protection applications, and other specialized security applications.Physical Controls:
Physical controls refer to tangible security measures such as walls, fences, barricades, and secure entry points. These measures are vital in preventing unauthorized physical access to facilities and mitigating risks.Note
Effective physical security measures might also incorporate access control vestibules to prevent tailgating, proper use of badges, sufficient lighting, and video surveillance.
Deception as a Security Measure
An advanced strategy to detect and counteract attackers involves the use of deception. By deliberately implementing deceptive tactics, organizations can gain vital insights into attackers' identities, capabilities, and methodologies.
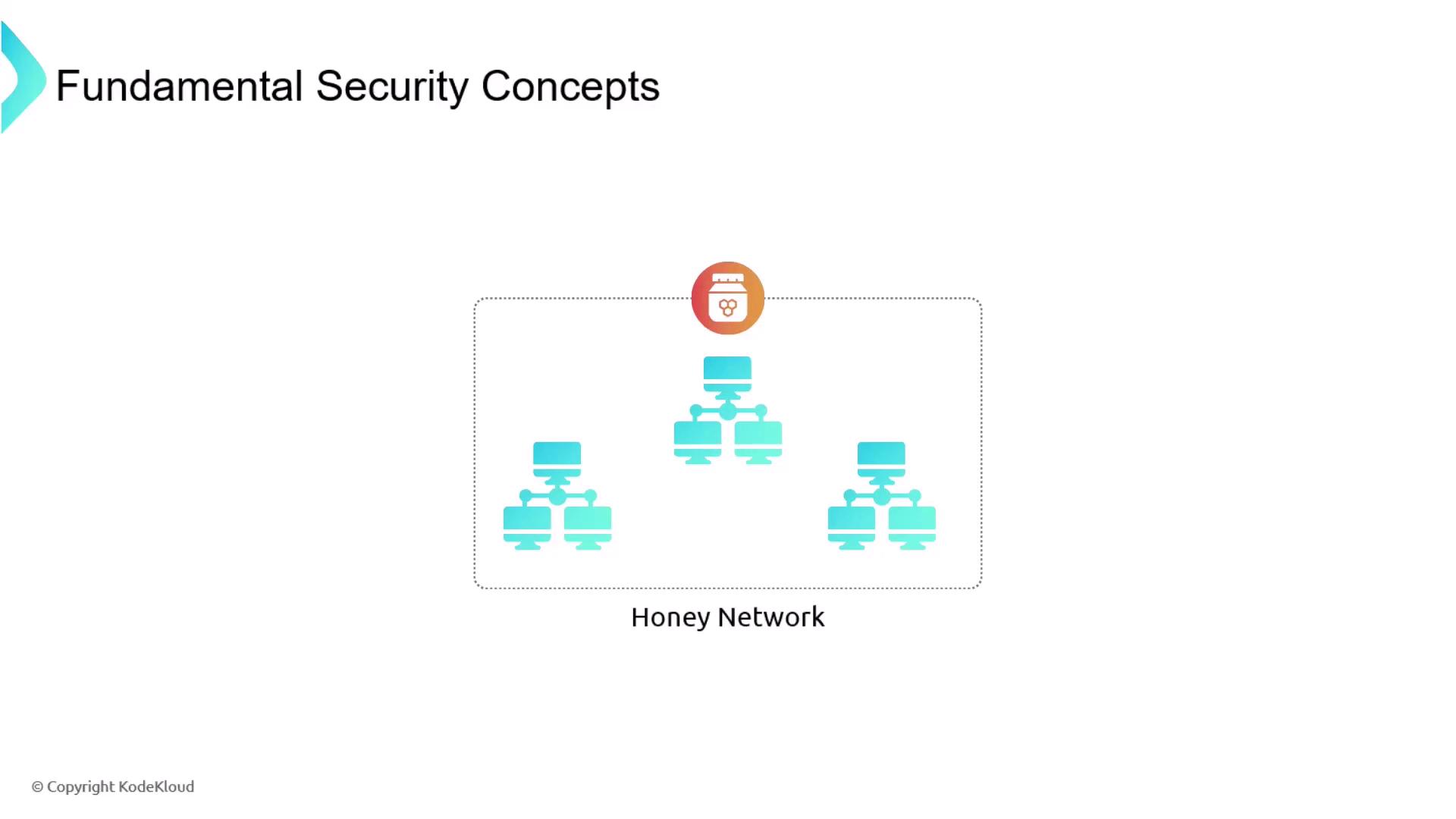
A common and effective deceptive measure is the deployment of a honeypot. A honeypot is a purposely vulnerable system intended to attract attackers, thereby allowing for careful monitoring of their actions and strategies. It is crucial to isolate the honeypot from your main production environment to avoid potential breaches.
This concept can be extended to create a full-fledged honey network or even a strategically placed honey file, significantly enhancing your overall security posture.
Watch Video
Watch video content