CompTIA Security+ Certification
Controls and Security Concepts
Change Management Processes
In this article, we conclude our series on change management by examining its procedures, business impacts, and technical implications. We will explore both the high-level aspects of change management and the more granular change control processes.
Understanding the difference between change control and change management is essential. Change control involves the specific procedures for requesting and approving changes before they are implemented. This process is a critical component of the overall change management framework, ensuring that every modification is properly evaluated and authorized.
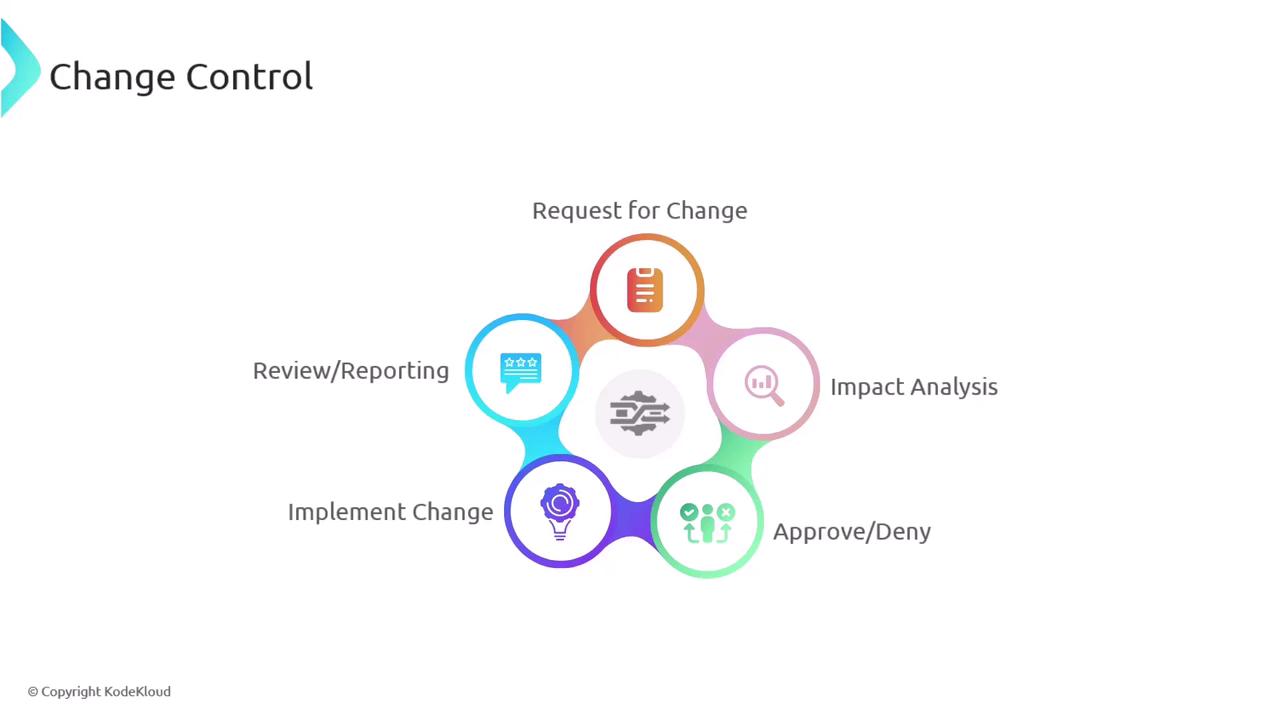
The broader change management process provides a roadmap for planning and executing changes, with a focus on minimizing negative impacts on various parts of the business.

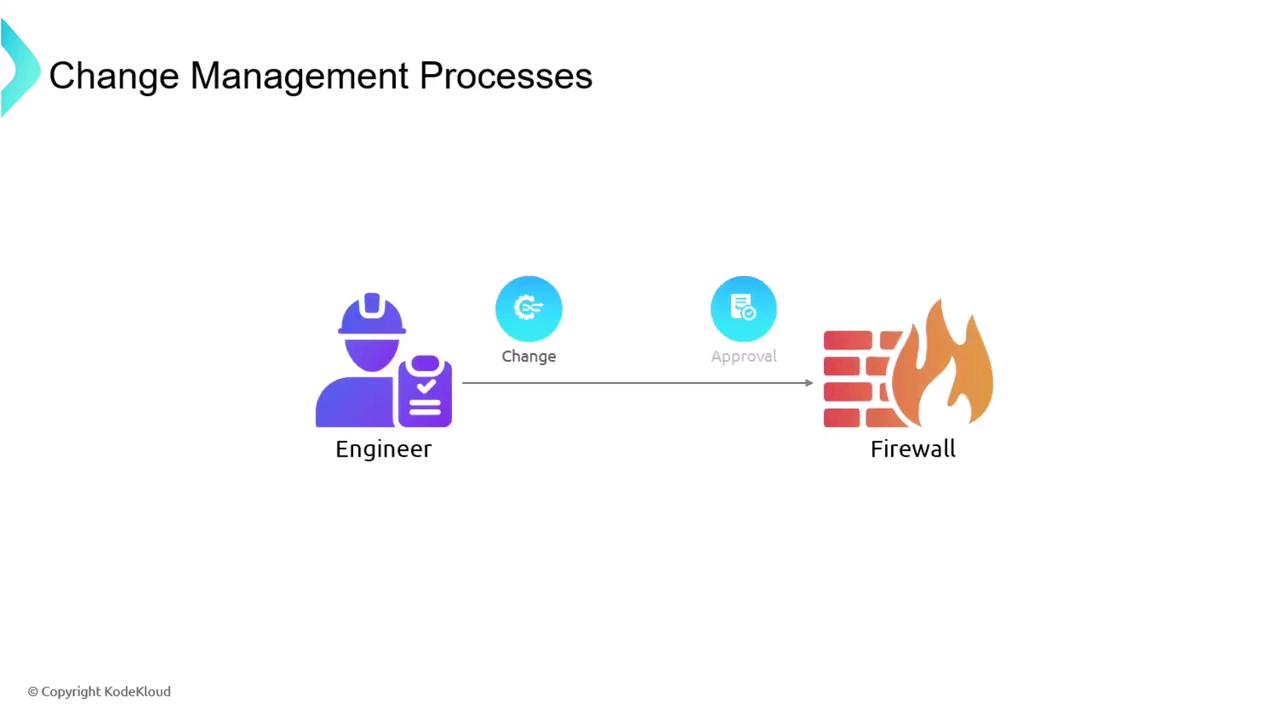
For example, when an engineer proposes adding new rules to the firewall, the change management procedure requires them to present detailed information about the proposed change and secure approval before any implementation occurs. This might involve participating in a dedicated change management meeting to address any follow-up questions.
Note
During change management meetings, requesters are often asked to provide supporting documentation such as updated diagrams, revised policies, or new procedures. Common steps in the process include:
- Obtaining necessary approvals
- Communicating with stakeholders
- Submitting impact analyses
- Presenting test results
- Proposing backup plans for risk mitigation
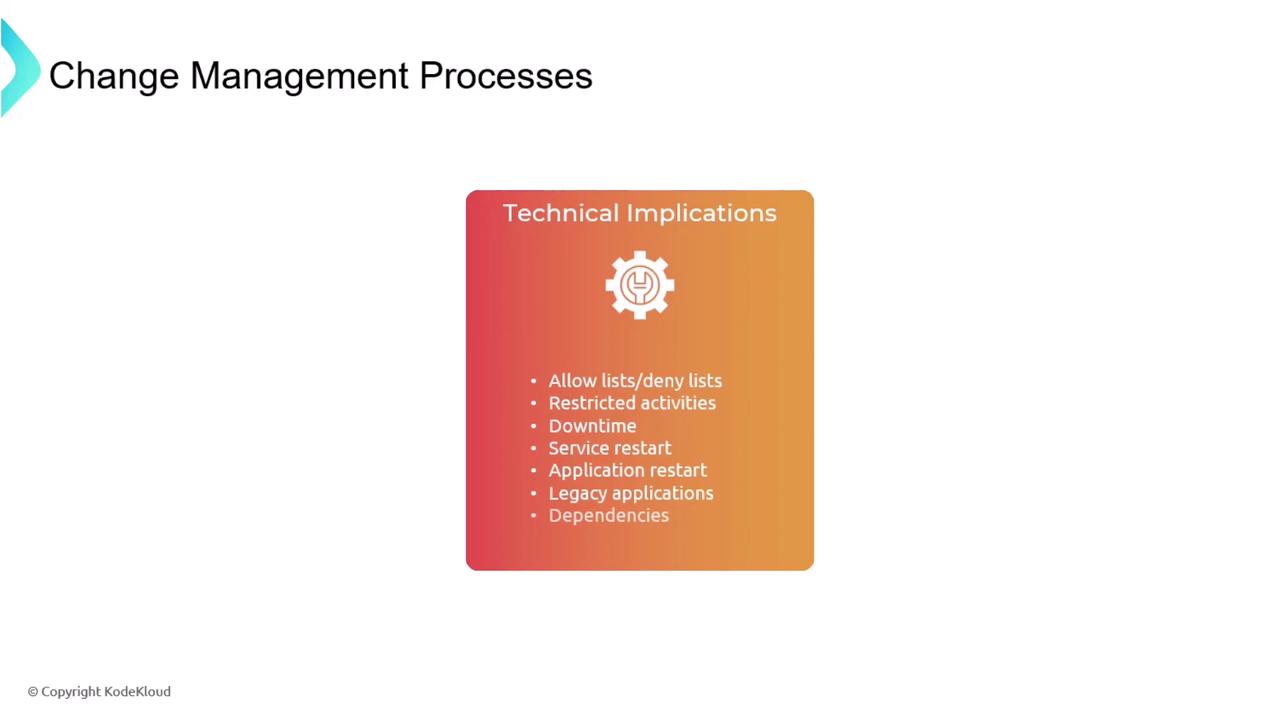
Technical considerations are integral to the change management process. For instance, changes may affect firewall allow lists or deny lists and endpoint protection systems. An allow list permits only the traffic that is explicitly specified, while a deny list blocks specified items and allows all other traffic.
Other practical questions that arise before approving a change include:
- Will the implementation require downtime?
- Is a service restart necessary?
- Are there dependencies that could impact other applications?
As we conclude this section, here is a quick recap of the key points discussed:
- An overview of security controls and their importance
- The definition and significance of control categories and types
- The critical role of physical security measures
- The importance of the Confidentiality, Integrity, and Availability (CIA) triad in safeguarding data
- Additional concepts such as non-repudiation, honeypots, and key elements of Zero Trust
- Detailed insights into change management processes and their technical implications

The insights presented here establish a strong foundation for our upcoming topics on threats, vulnerabilities, and mitigations, and provide a comprehensive approach to how attackers exploit system weaknesses. Continue learning about these essential exam preparation topics in our next sections.
For further reading, consider exploring:
Watch Video
Watch video content