CompTIA Security+ Certification
Security Architecture
Architectural Models
Welcome back to our in-depth exploration of architectural models and their significance in cybersecurity. In this lesson, we delve into the core principles of network architecture, infrastructure models, and essential design considerations that help safeguard your digital assets. Understanding these models is crucial for both IT professionals and cybersecurity enthusiasts.
Network architecture defines how you select and organize devices, protocols, and other assets—both physical and digital—to align with your business objectives. Because different business units have unique workflows and processes, architectural designs are often customized to meet these specific needs. Typically, security zones and physical isolation strategies form integral parts of these designs.
Note
Remember, a well-planned network architecture not only improves operational efficiency but also strengthens your overall security posture.
Security zones extend the concept of network segmentation by grouping multiple IP subnets and services together. Think of a security zone as a mini-network or a cluster of networks within a larger enterprise environment. This strategy effectively divides the infrastructure into segments with similar security requirements.
A common approach in many organizations is to segment the network into distinct zones:
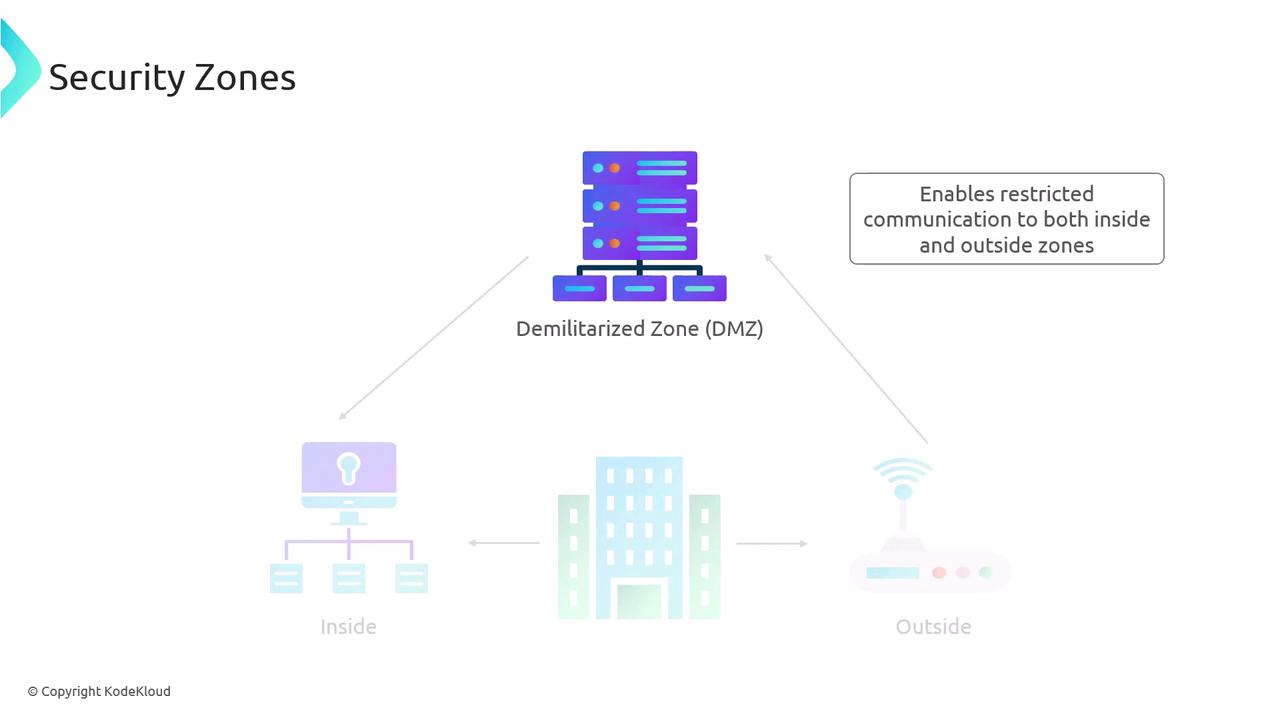
- The "outside zone" typically encompasses the internet and other public-facing connections.
- The "inside zone" contains private networks and internal resources.
Often, a Demilitarized Zone (DMZ) is introduced as a controlled intermediary that facilitates secure communication between these two zones. For example, when a customer places an online order, the request originates from the outside zone. The web server handling the transaction, usually located in the DMZ, acts as a bridge. If the transaction requires access to sensitive data housed in the inside zone, the DMZ serves as a secure intermediary.
In addition to implementing security zones, a robust architectural design emphasizes the physical isolation of resources. This isolation minimizes the attack surface by restricting the propagation of potential threats across different parts of the infrastructure.
By understanding and implementing these architectural strategies, organizations can build resilient networks that not only operate efficiently but also defend against cyber threats effectively.
For further insights into building secure networks, explore more about Kubernetes Basics and other cybersecurity topics in our extensive documentation.
Watch Video
Watch video content