CompTIA Security+ Certification
Security Architecture
Data Considerations
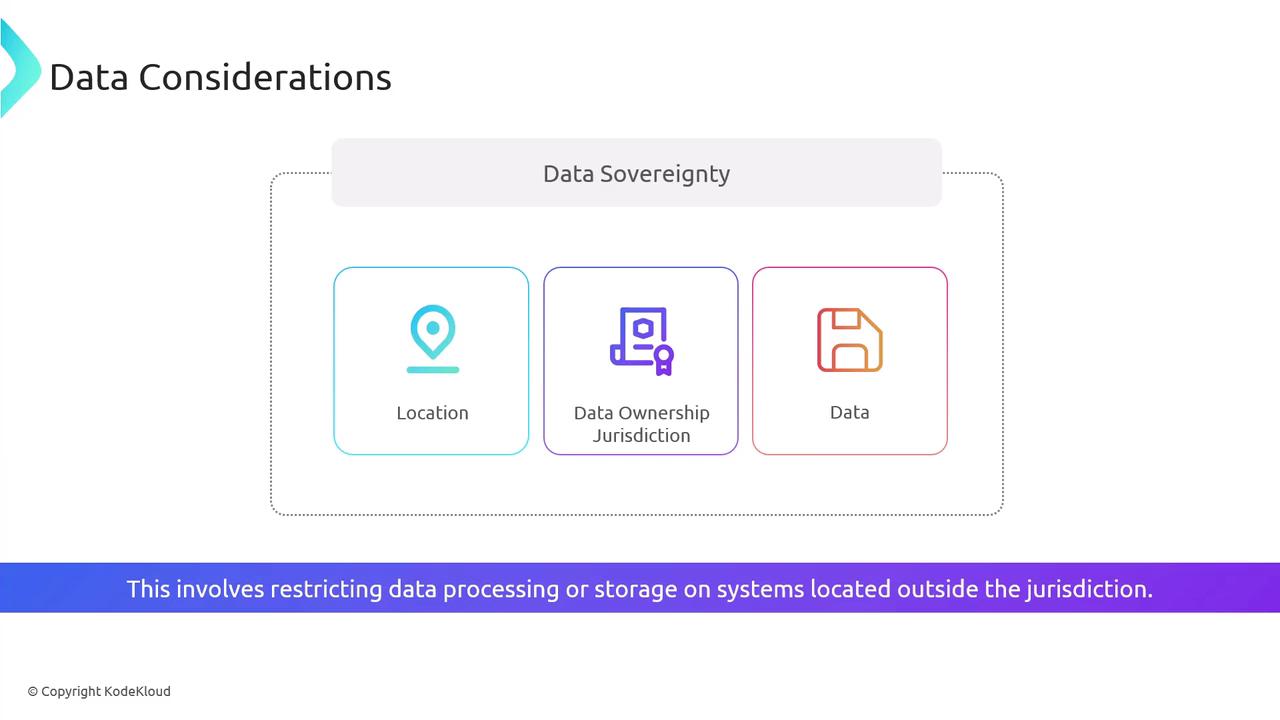
In this article, we explore essential data considerations, with a particular focus on data sovereignty. Data sovereignty refers to the legal and geographic constraints governing the processing and storage of data based on the location of its owner or the data itself. These constraints often influence how and where organizations can manage their information.
Understanding Data Sovereignty
Data sovereignty plays a critical role in global operations. Organizations must be aware of local laws and regulations when processing data internationally, especially in cloud-based environments.
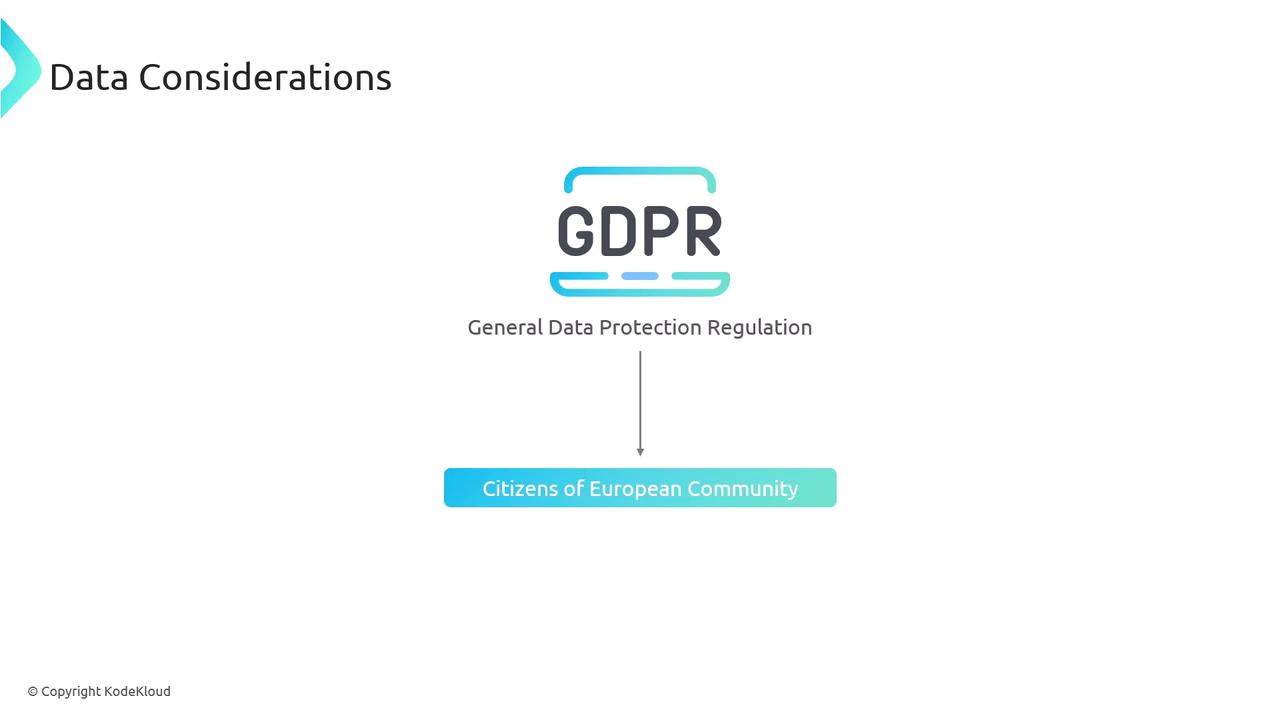
This issue is particularly important for cloud services, where regulatory requirements might mandate that data be stored in designated regions. A notable example is the General Data Protection Regulation (GDPR), which, although specifically designed to protect the citizens of the European Community, has implications that extend beyond EU borders. Any company that handles the data of EU citizens, regardless of its location, must comply with GDPR.
Compliance Alert
Non-compliance with data sovereignty regulations like GDPR can lead to severe legal and financial penalties. Ensure that your data processing and storage practices meet all relevant regional and international requirements.
Additionally, securing data is crucial to safeguard against unauthorized access and breaches. Consider implementing various security strategies, including:
- Data masking
- Encryption
- Hashing
- Geographic restrictions
- Obfuscation
- Tokenization
- Segmentation
- Permission controls
Employing these methods not only enhances data security but also supports compliance with jurisdictional regulations and industry standards.
Watch Video
Watch video content