- Vendor Monitoring
- Questionnaires
- Rules of Engagement
Vendor Monitoring
Vendor monitoring is an ongoing process that evaluates a vendor’s performance, security practices, and adherence to contractual obligations. This continuous evaluation provides assurance, early detection of potential issues, and accountability. Proactive vendor monitoring enables early intervention if deviations occur, ensuring vendors meet your organization’s quality and security standards.
- Performance Reviews:
Regular performance reviews measure vendors against predefined metrics and service-level agreements (SLAs). For example, quarterly performance reviews with a cloud service provider might assess uptime, response times, and support quality.
- Security Audits:
Conducting security audits assesses vendors’ security controls and practices. This process confirms that vendors have the necessary measures in place to protect sensitive data and comply with contractual and regulatory requirements. An annual security audit for a vendor handling sensitive customer data is a typical example.
- Continuous Monitoring:
Using tools to monitor a vendor’s security posture and performance in real time helps proactively manage potential risks. For instance, a continuous monitoring solution can detect anomalies or vulnerabilities in a vendor’s network before they escalate.
Regular vendor monitoring not only maintains security standards but also builds trust and accountability between your organization and its vendors.
Questionnaires
Questionnaires are structured sets of questions designed to gather detailed information about a vendor’s security practices, policies, and compliance status. They offer deep insights into a vendor’s security posture while providing a standardized method for assessing multiple vendors.
-
Security Practices:
These questions evaluate the vendor’s security policies, procedures, and controls, ensuring robust measures are in place. Common inquiries cover areas such as data encryption, access control, and incident response procedures. -
Compliance:
This section explores whether the vendor adheres to relevant laws, regulations, and industry standards. Questions might address GDPR compliance, specific industry standards, and the vendor’s certification status.
- Risk Management:
These questions assess the vendor’s methods for identifying, assessing, and mitigating risks. Typical topics include risk assessment processes, risk mitigation strategies, and the vendor’s incident history.
Utilizing questionnaires helps create a consistent evaluation framework for comparing the security and compliance levels of different vendors.
Rules of Engagement
Establishing clear rules of engagement is a critical process for managing third-party risks. These guidelines and protocols define the interactions and expectations between your organization and its vendors, ensuring structured communication and effective risk management.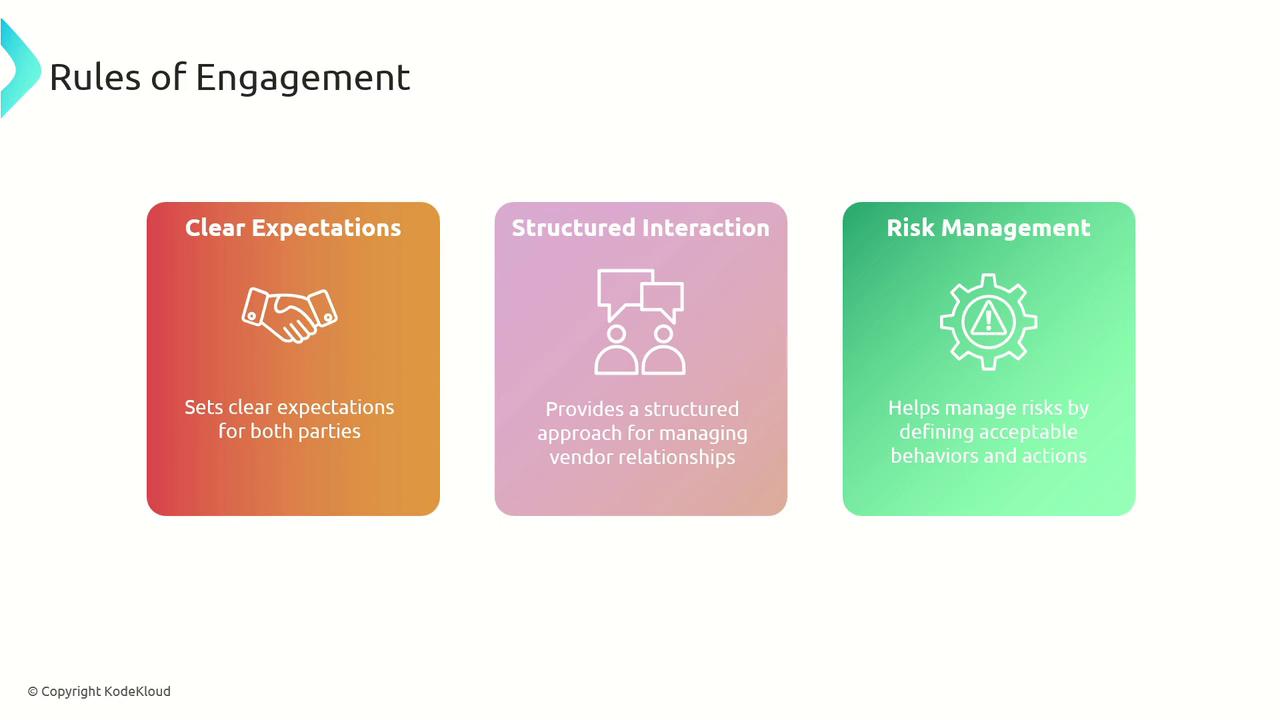
-
Contractual Obligations:
Defined obligations in the contract ensure that vendors meet specific requirements, thus providing legal protection and reinforcing accountability. Contracts may include clauses specifying data protection requirements, service levels, and penalties for non-compliance. -
Communication Protocols:
Clear communication channels facilitate effective collaboration and prompt resolution of issues. Regular meetings, reporting requirements, and established communication protocols keep interactions transparent and aligned with business objectives. -
Security Requirements:
Specifying mandatory security measures ensures that vendors adhere to defined standards. Requirements might include using multi-factor authentication, conducting regular security training, and maintaining up-to-date security certifications.
Ensure that all rules of engagement are clearly documented and agreed upon by both your organization and the vendors to avoid potential misunderstandings that may lead to compliance issues.
Conclusion
Effective third-party risk assessment and management are crucial to maintaining high security and performance standards. By implementing robust vendor monitoring, comprehensive questionnaires, and well-defined rules of engagement, your organization can mitigate risks, ensure ongoing compliance, and foster successful vendor relationships.