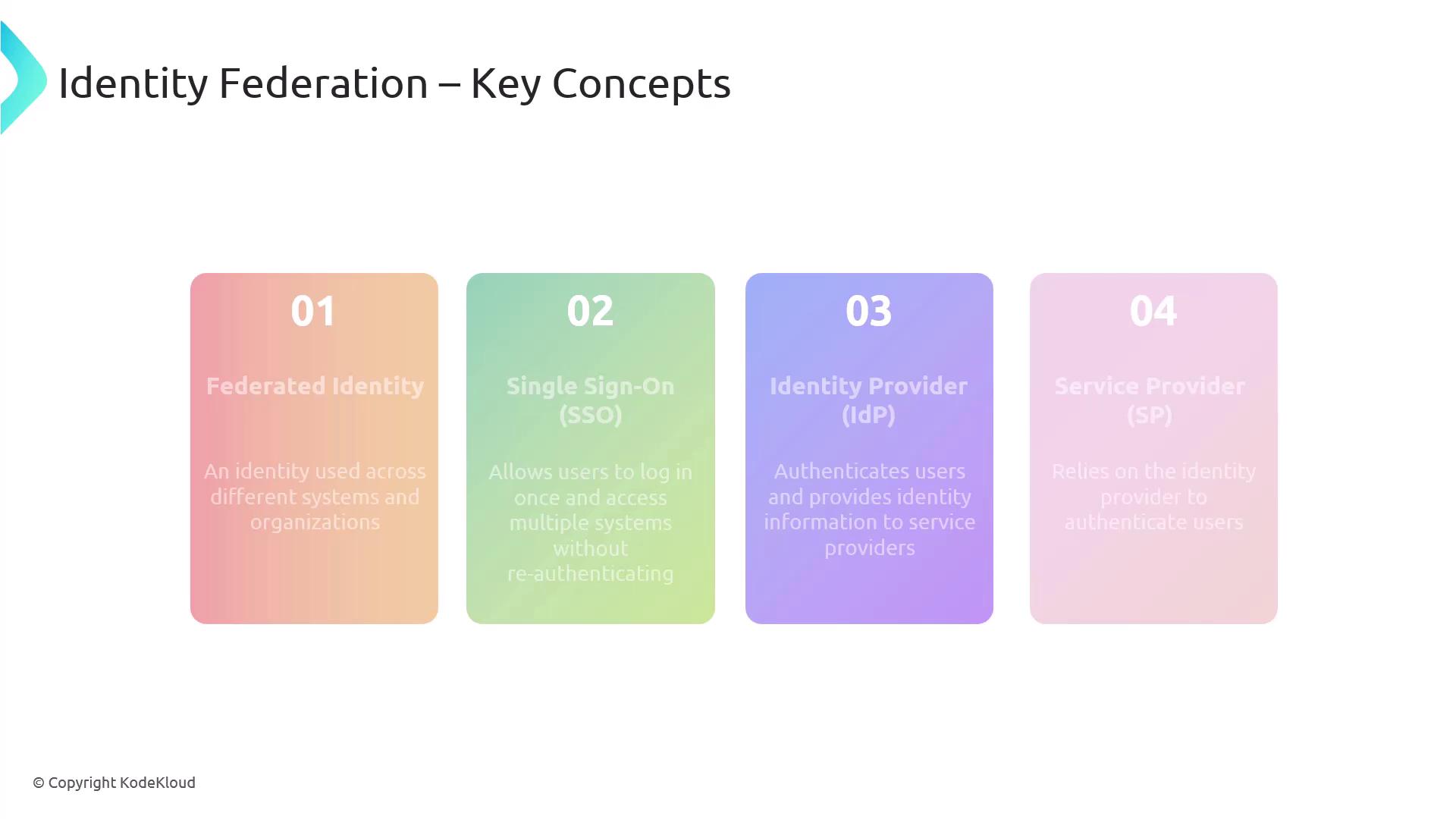
- Federated Identity: An identity used consistently across multiple systems and organizations.
- Single Sign-On (SSO): A feature enabling users to log in once and access multiple systems without re-authentication.
- Identity Provider (IdP): The entity responsible for authenticating users and supplying identity data to service providers.
- Service Provider (SP): The system that relies on the identity provider’s verification to grant user access to resources.
Benefits of Federation
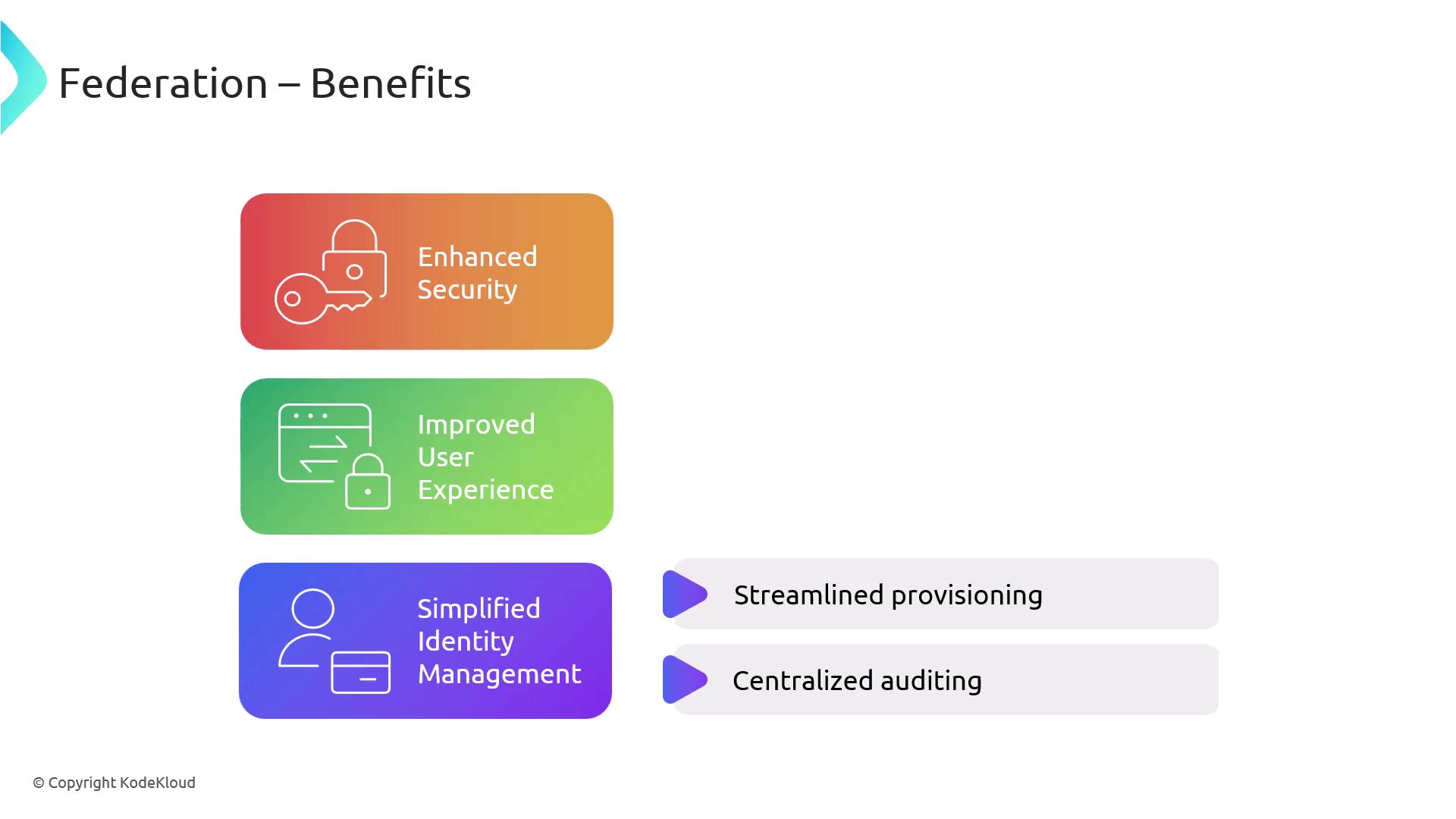
Employing federation brings several advantages:- Enhanced Security: Centralized authentication enforces uniform security policies and reduces the number of passwords, thereby minimizing the attack surface.
- Improved User Experience: With fewer credentials to manage, users enjoy seamless access across multiple systems without repeated logins.
- Simplified Identity Management: Federation streamlines the processes of provisioning and deprovisioning users and offers a centralized perspective for auditing and compliance.
- Streamlined Provisioning and Centralized Auditing: These additional benefits help simplify user management and ensure secure operations across systems.
Key Components of Federation
Federation consists of three core components:-
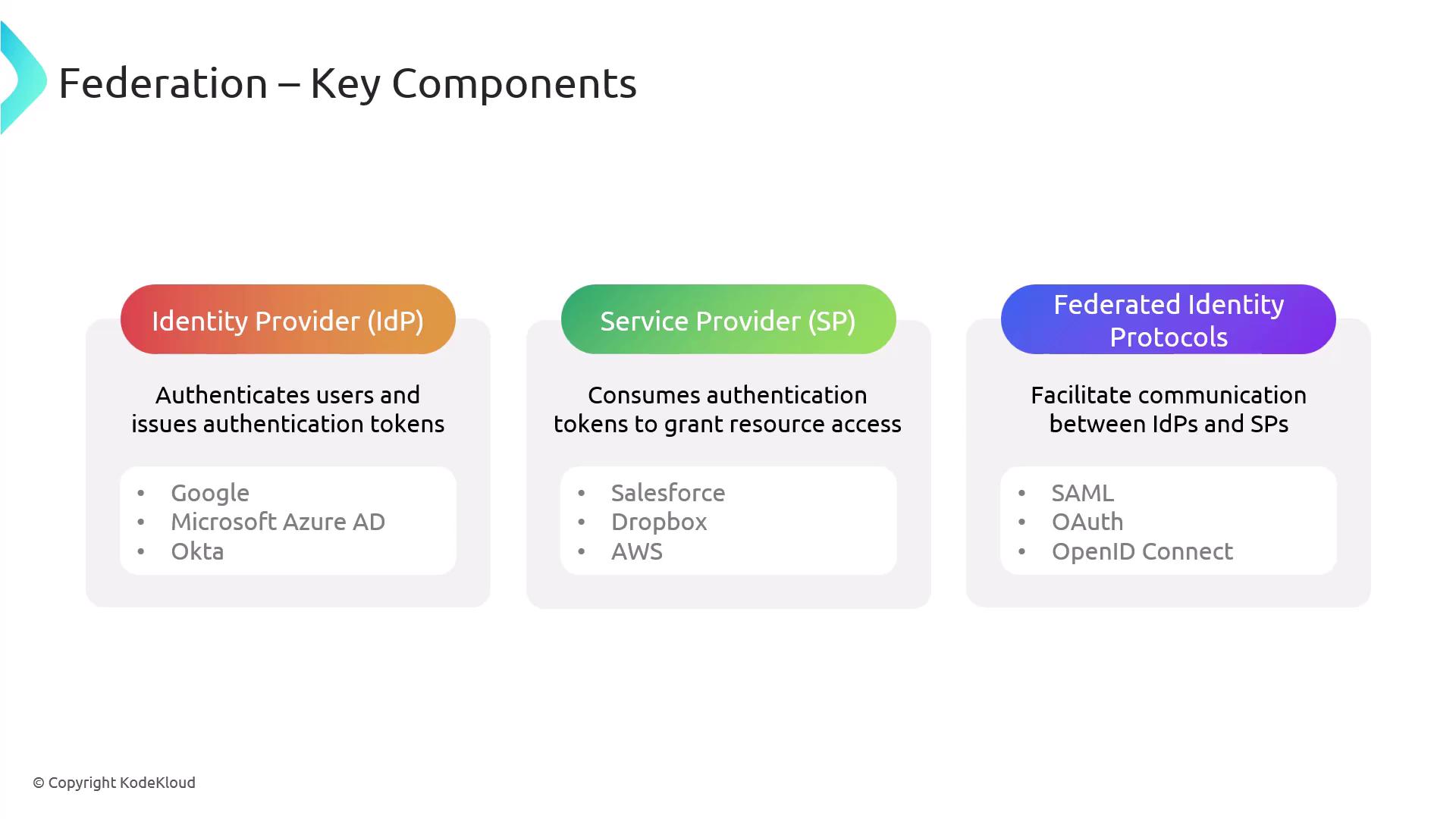
Identity Provider (IdP)
- Authenticates users and issues authentication tokens or assertions.
- Examples include Google and Microsoft Azure AD.
-
Service Provider (SP)
- Leverages the tokens or assertions from the IdP to grant access to resources.
- Examples include Salesforce, Dropbox, and AWS.
-
Federated Identity Protocols
- Establish standards for communication between identity providers and service providers.
- Common protocols include:
- SAML: An XML-based protocol for secure exchange of authentication and authorization data.
- OAuth: An open standard for access delegation, widely used for token-based authentication and authorization.
- OpenID Connect: An authentication layer built on OAuth 2.0 that facilitates user identity verification.
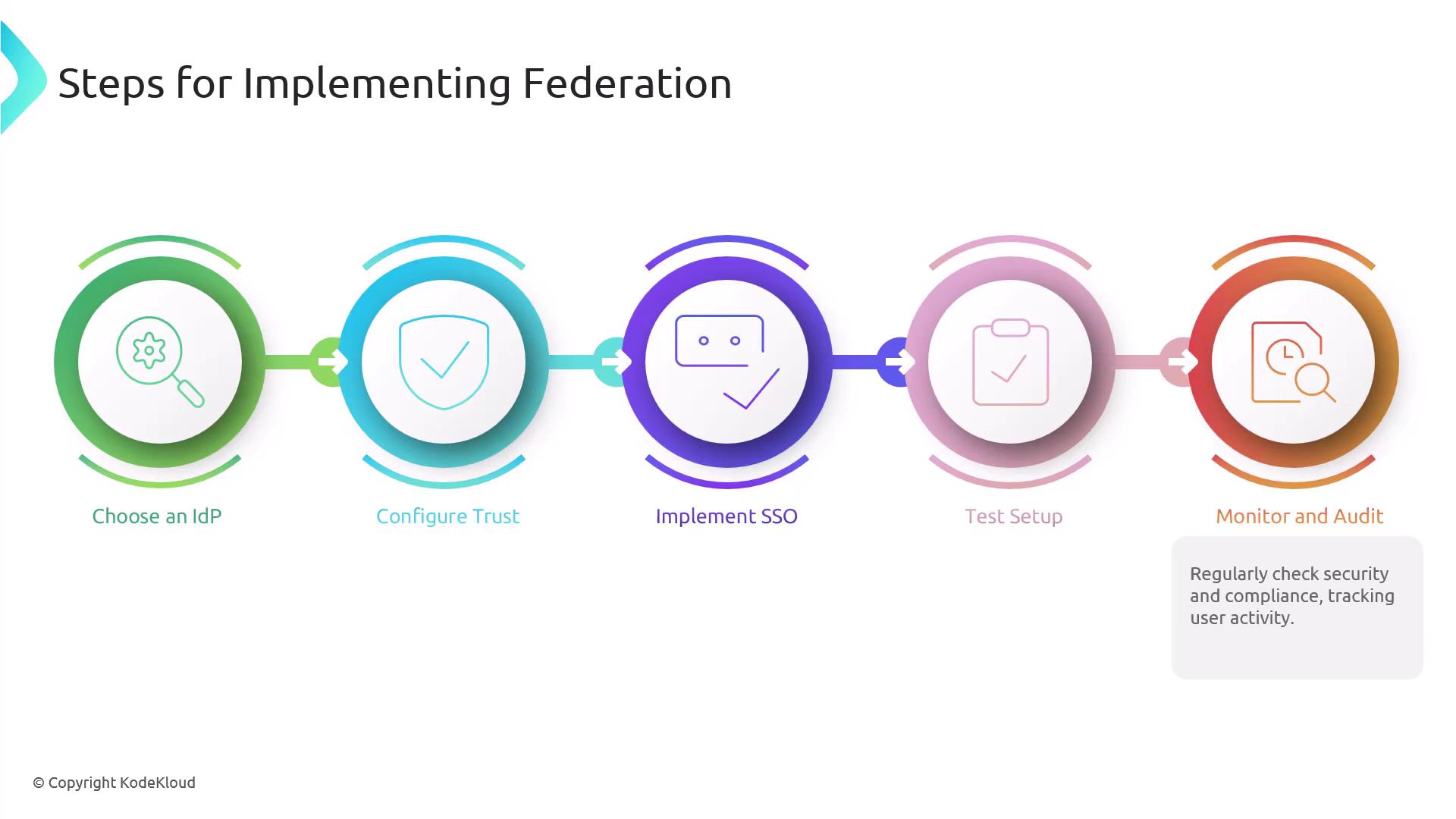
Steps to Implement Federation
Implementing federation involves the following steps:- Select an IdP that supports required protocols and integrates with your exist…
Select an IdP that supports required protocols and integrates with your existing systems. Popular choices include Microsoft Azure AD and Google Identity.
- Establish trust relationships between your IdP and your service providers
Establish trust relationships between your IdP and your service providers. This setup involves metadata exchange, certificate configuration, and trust settings.
- Configure SSO to ensure that users can log in just once and access multiple s…
Configure SSO to ensure that users can log in just once and access multiple services seamlessly. This typically involves protocols such as SAML, OAuth, or OpenID Connect.
-
Test the Federation Setup:
- Conduct comprehensive testing to verify that the federation setup works as expected.
- Ensure the solution allows users to log in a single time and access all integrated services without additional authentication.
-
Monitor and Audit:
- Regularly monitor and audit your federation environment for security and compliance.
- Use logging and monitoring tools to track user activities and quickly identify any anomalies.
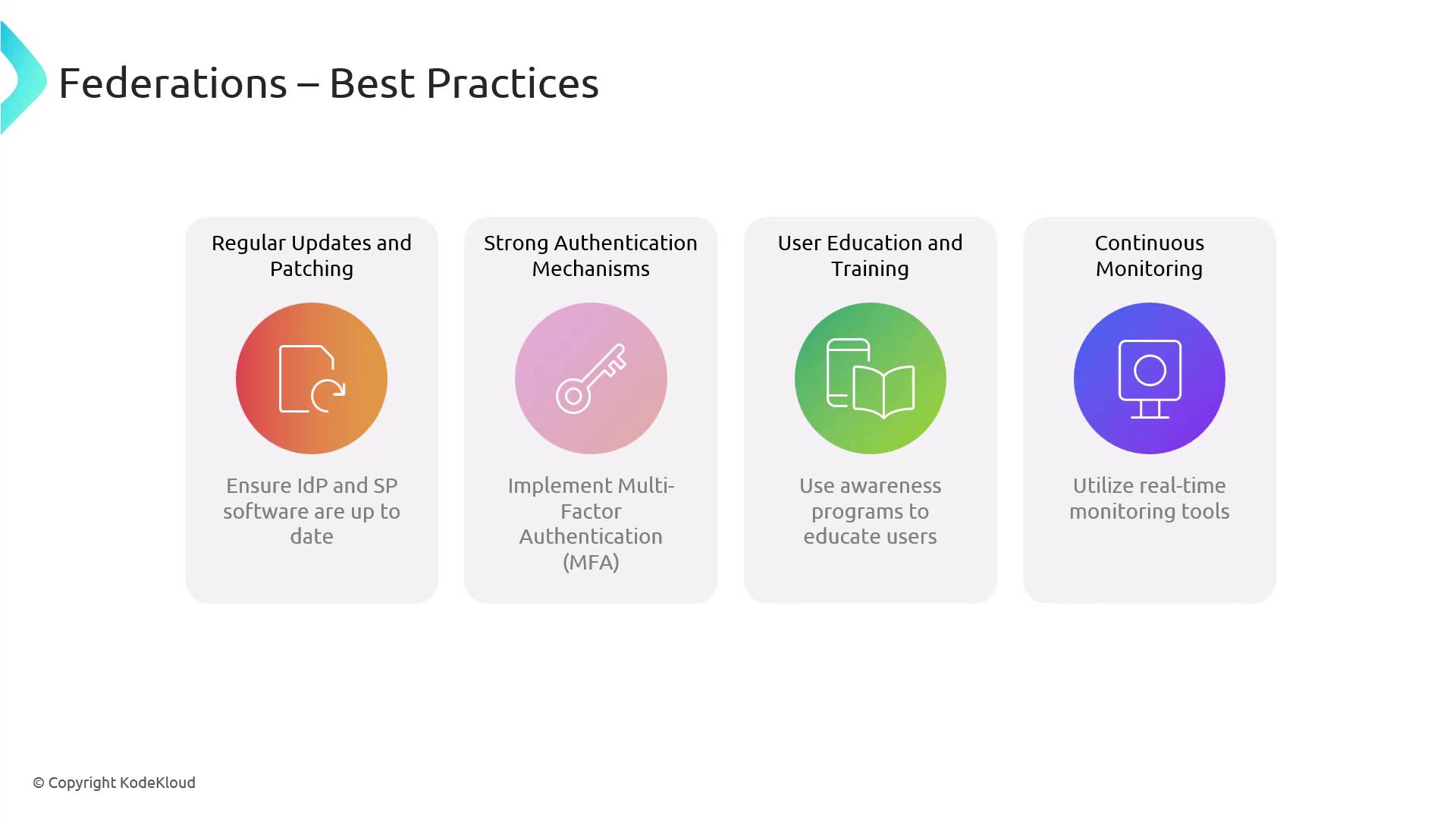
Best Practices for Federation
When setting up federation, keep these best practices in mind:- Regular Updates and Patching: Ensure that both identity providers and service providers are always up-to-date to protect against vulnerabilities.
- Strong Authentication Mechanisms: Implement multi-factor authentication (MFA) to add an extra layer of security during the authentication process.
- User Education and Training: Launch awareness programs to educate users about the benefits of federation and the secure use of SSO.
- Continuous Monitoring: Use real-time monitoring tools to keep an eye on user activity and quickly identify any suspicious behavior.
Conclusion
Identity federation is a robust approach that enhances security, improves user experience, and simplifies identity management across diverse systems and organizations. By leveraging federated identity protocols such as SAML, OAuth, and OpenID Connect, organizations can efficiently enable secure and seamless access for their users.