CompTIA Security+ Certification
Security Operations
Response Remediation and Reporting
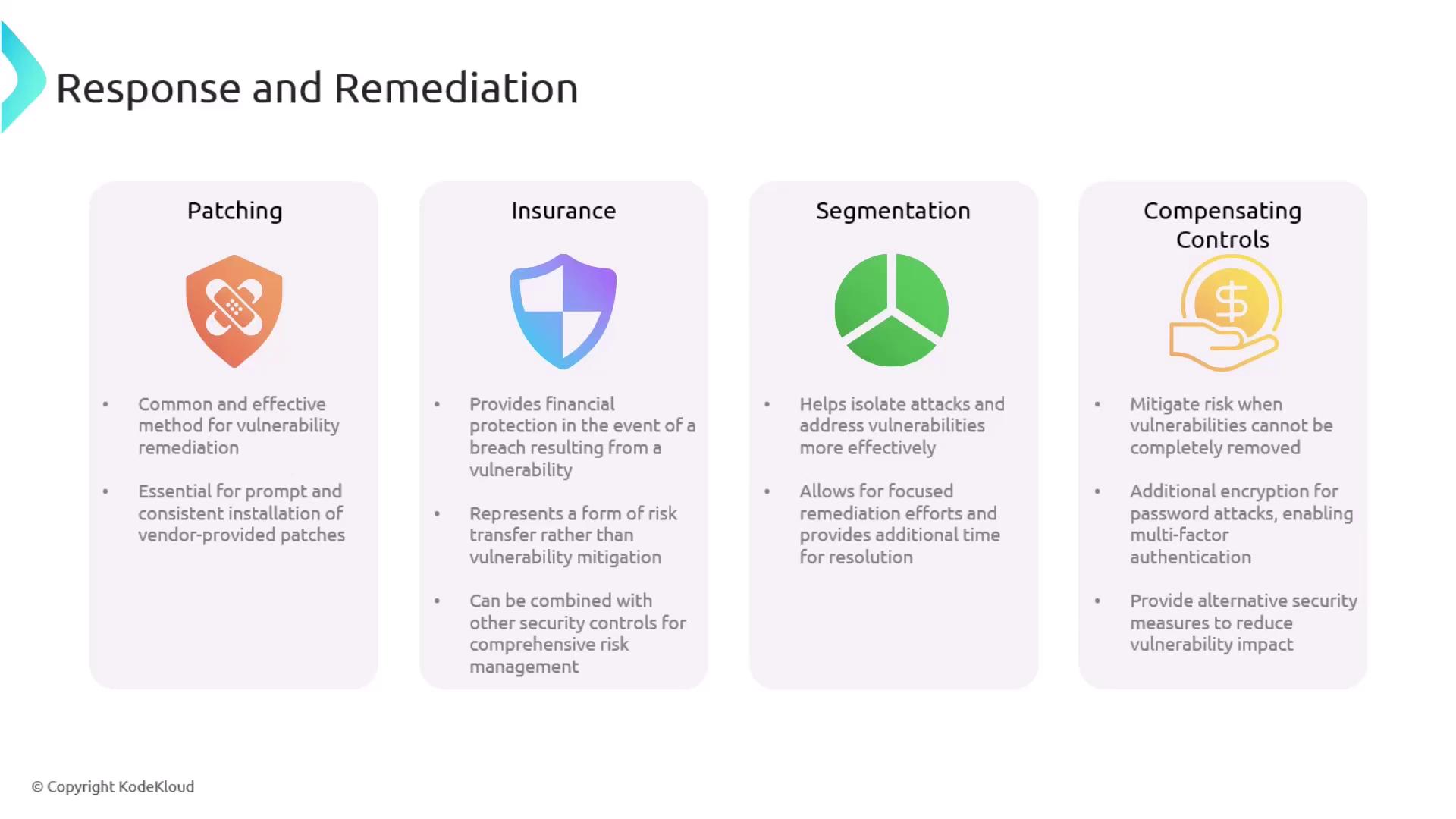
Effectively addressing vulnerabilities involves a combination of proactive strategies and robust risk management practices. Below are key approaches to vulnerability management that can help strengthen your cybersecurity posture.
Centralized Patching
Patching remains one of the most common and effective remediation methods. Implementing a centralized patch management process ensures that vendor-provided patches are deployed promptly and uniformly across all systems. This consistency minimizes the window of exposure and maintains overall system integrity.
Cybersecurity Insurance
Cybersecurity insurance provides financial protection in the event of a breach by transferring some of the risk. Although it does not mitigate or eliminate vulnerabilities directly, insurance can be an important component in a comprehensive risk management strategy when combined with other security controls.
Network Segmentation
Proactive network segmentation isolates critical systems from compromised segments, limiting the potential impact of an attack. This strategy is particularly useful when immediate remediation is not possible, as it helps contain the breach and protects vital assets.
Note
Isolating vulnerable segments can significantly reduce the spread of attacks while remediation efforts are underway.
Compensating Controls
In cases where vulnerabilities cannot be entirely eliminated, compensating controls can help mitigate the associated risks. For instance, enhancing encryption protocols or enabling multi-factor authentication can provide additional layers of defense against password attacks or other threats.
Post-Remediation Validation
After vulnerabilities have been remediated, it's crucial to validate that the solutions have effectively resolved the issues. This validation process may include:
- Re-scanning systems to ensure no vulnerabilities remain.
- Conducting audits to assess the overall security posture.
- Performing manual or automated checks to confirm the efficacy of applied remediations.
Adopting these strategies in your vulnerability management plan not only helps in rapidly addressing security issues but also strengthens your organization's resilience against future threats.
Watch Video
Watch video content