Patching
Patching is the systematic process of applying updates to software, operating systems, and applications to address known vulnerabilities and enhance overall security. This proactive measure helps eliminate bugs, fix security flaws, and close potential avenues for attackers. The patching process includes the following steps:- Identification: Security teams review and determine which patches are available and necessary for the organization’s software and systems.
- Testing: Patches are deployed in a controlled environment to ensure they do not introduce additional issues.
- Deployment: After testing, patches are applied across production systems to address vulnerabilities.
- Verification: Continuous monitoring ensures that each patch has been successfully implemented and that no side effects occur.
A robust patch management process minimizes exposure to vulnerabilities and is critical for maintaining system security.
Monitoring
Monitoring involves the continuous observation of systems, networks, and applications to detect and respond to security threats in real time. Proactive monitoring can uncover anomalies, unauthorized access, and potential security breaches before they escalate into serious incidents. For example, Security Information and Event Management (SIEM) systems collect and analyze log data from various sources—such as servers, firewalls, and applications—to identify unusual behaviors. When unusual login attempts occur, the SIEM system triggers alerts, prompting immediate investigation by the security team.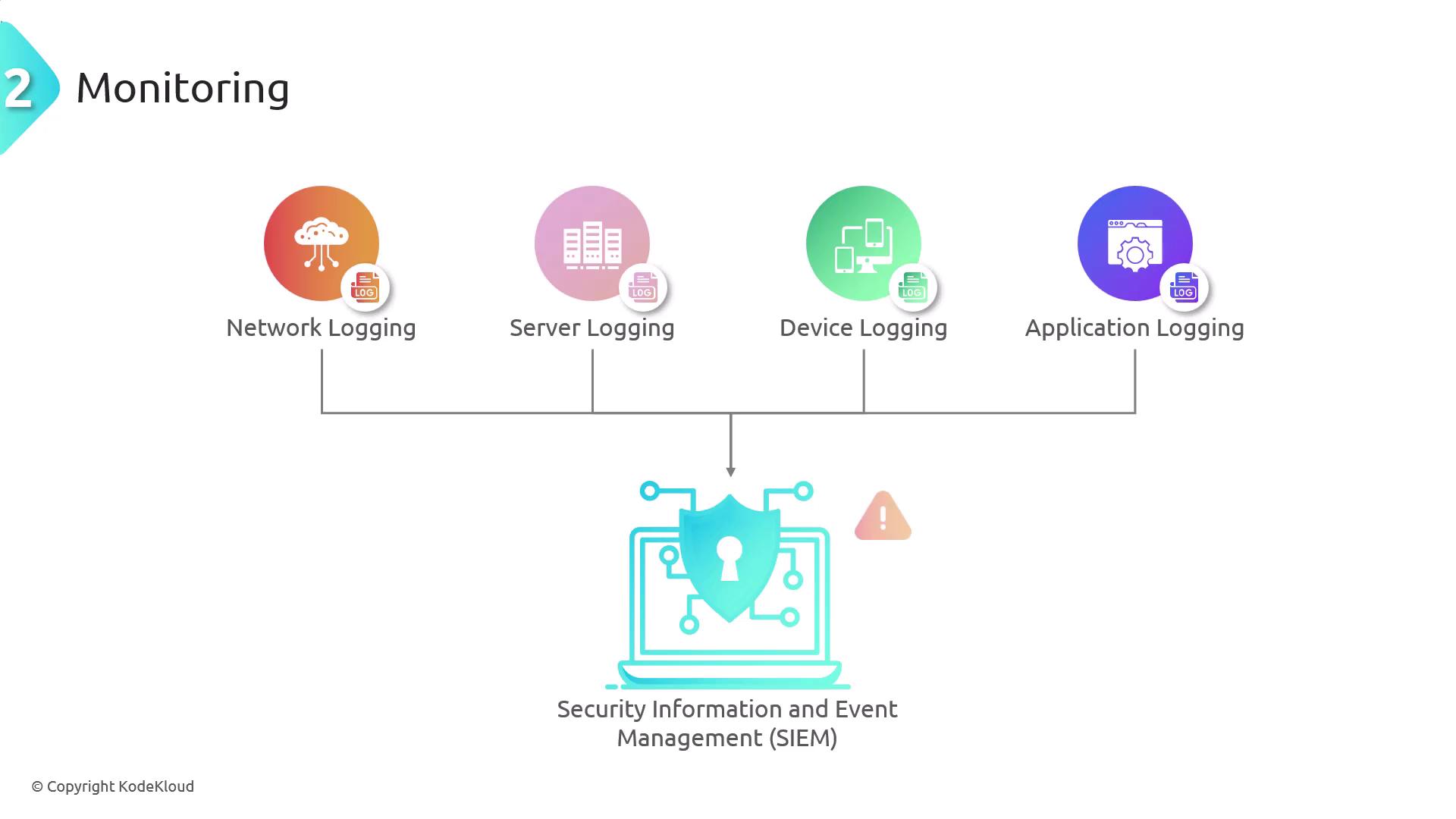
- Ensuring all critical systems and networks are covered.
- Implementing real-time alert mechanisms.
- Utilizing behavioral analysis to promptly detect abnormalities.
- Regularly reviewing and updating monitoring parameters for optimal performance.
Configuration Enforcement
Configuration enforcement is the practice of establishing and maintaining secure, consistent settings across all applications, devices, and systems. This process starts with creating a secure baseline configuration that outlines the necessary security parameters. Configuration management tools are then used to monitor compliance with this baseline continuously. Any deviations are quickly remediated to preserve system integrity.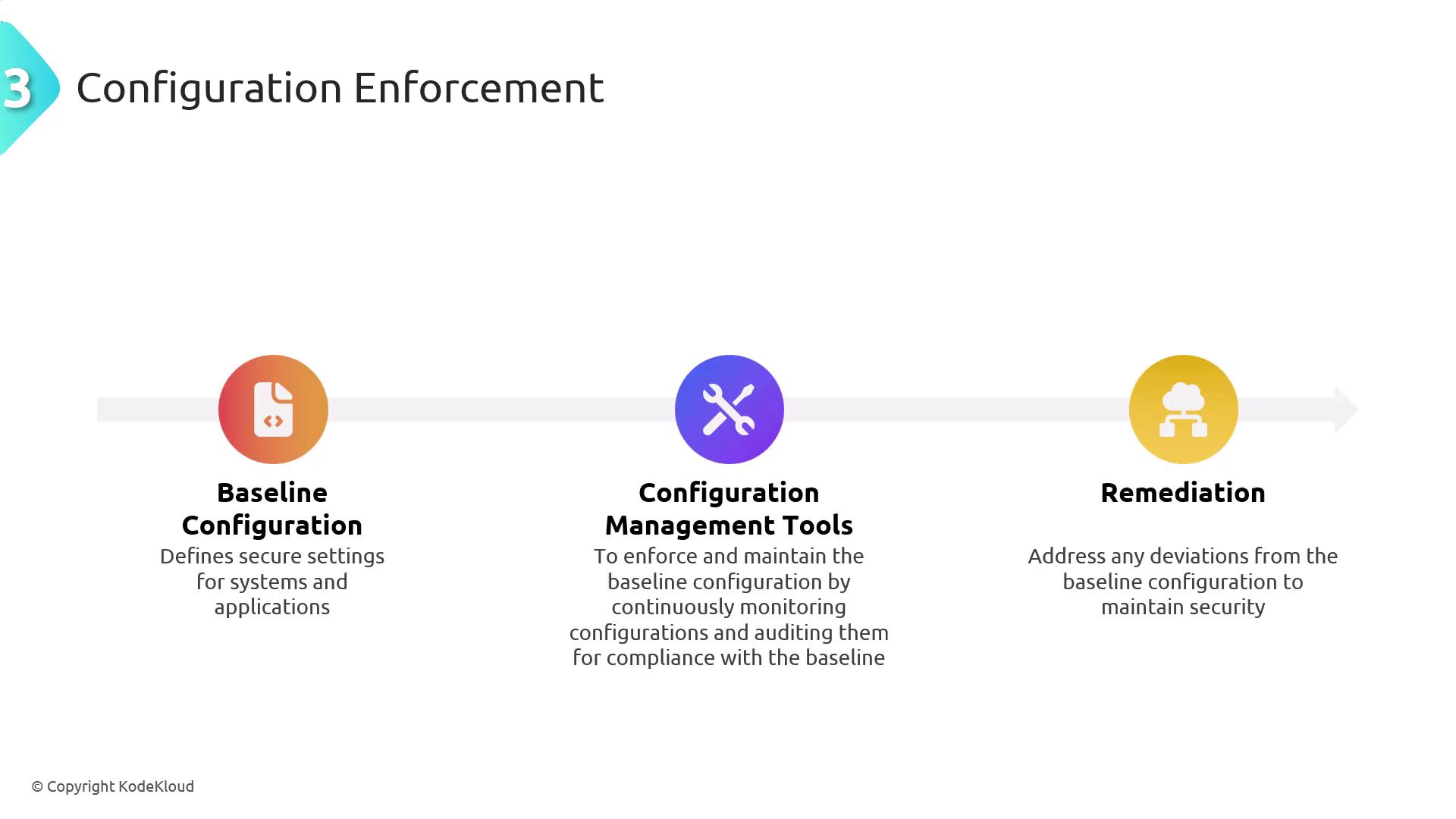
Failing to enforce consistent configurations can expose systems to vulnerabilities and increase the risk of breaches.
Decommissioning
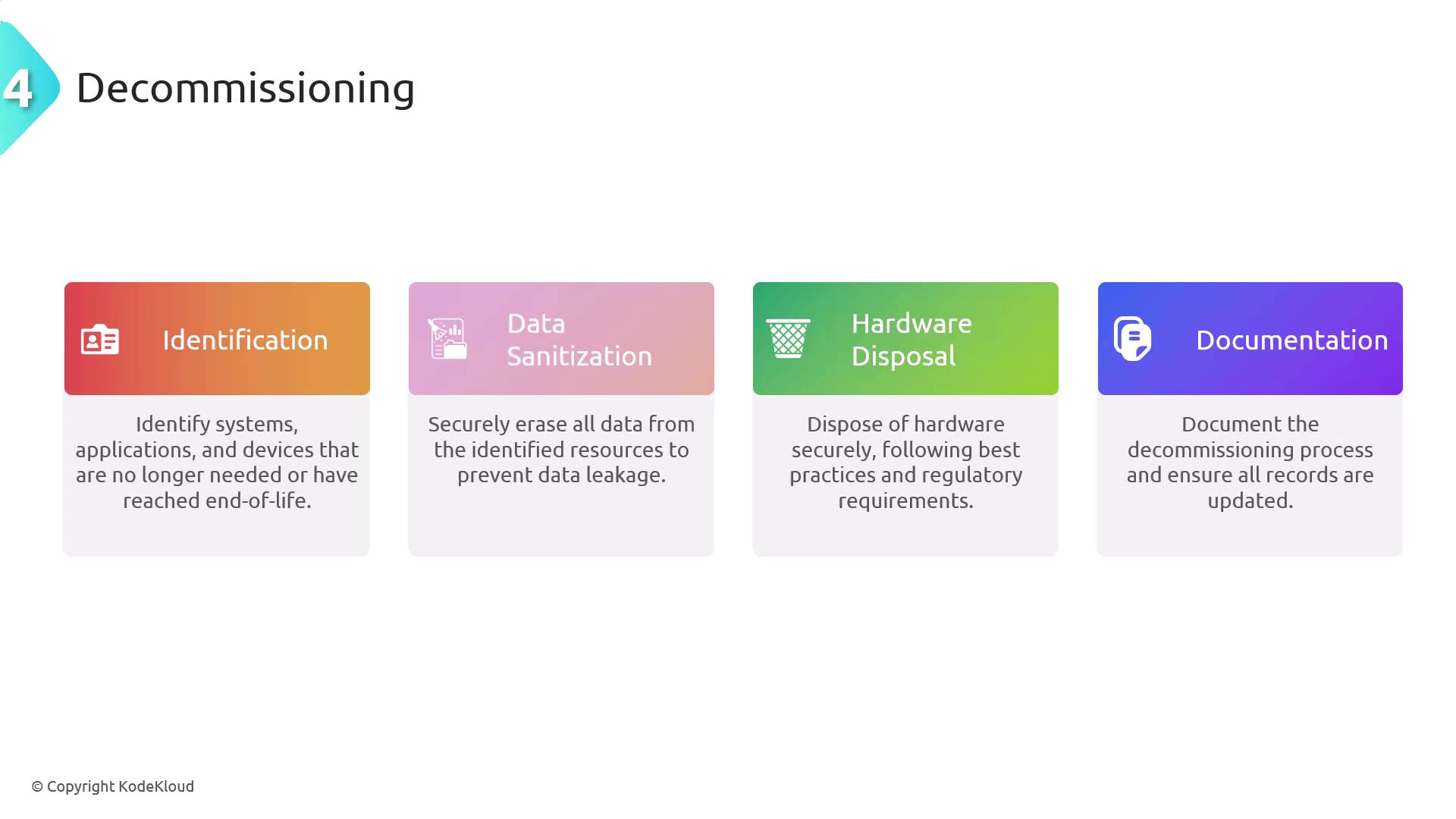
Decommissioning deals with the secure retirement and disposal of outdated or unused systems, applications, and devices. This critical process helps ensure that sensitive data does not remain accessible beyond its intended lifecycle. The decommissioning process involves several key steps:- Identification: Recognize which systems, applications, or devices are obsolete or no longer in use.
- Data Sanitization: Securely erase all data from these resources to prevent data leakage.
- Hardware Disposal: Dispose of hardware in compliance with regulatory guidelines and best practices.
- Documentation: Record the decommissioning steps for compliance, auditing, and future reference.
Conclusion
In summary, implementing effective mitigation techniques—namely patching, monitoring, configuration enforcement, and decommissioning—is essential for securing the IT environment. These strategies enable organizations to reduce vulnerabilities, rapidly detect threats, maintain secure configurations, and safely retire outdated resources.