CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Physical Attacks
Welcome back. In this article, we delve into physical attacks in cybersecurity—an often overlooked yet critical threat vector. While digital breaches dominate the headlines, physical attacks can exploit vulnerabilities in an organization’s infrastructure and assets. Below, we explore key attack types including brute force attacks, RFID cloning, and environmental attacks, along with recommended strategies to prevent and mitigate these risks.
Physical attacks target tangible infrastructure or devices. Unlike remote cyberattacks, these involve direct physical interaction—gaining unauthorized access or sabotaging facilities, devices, or systems.
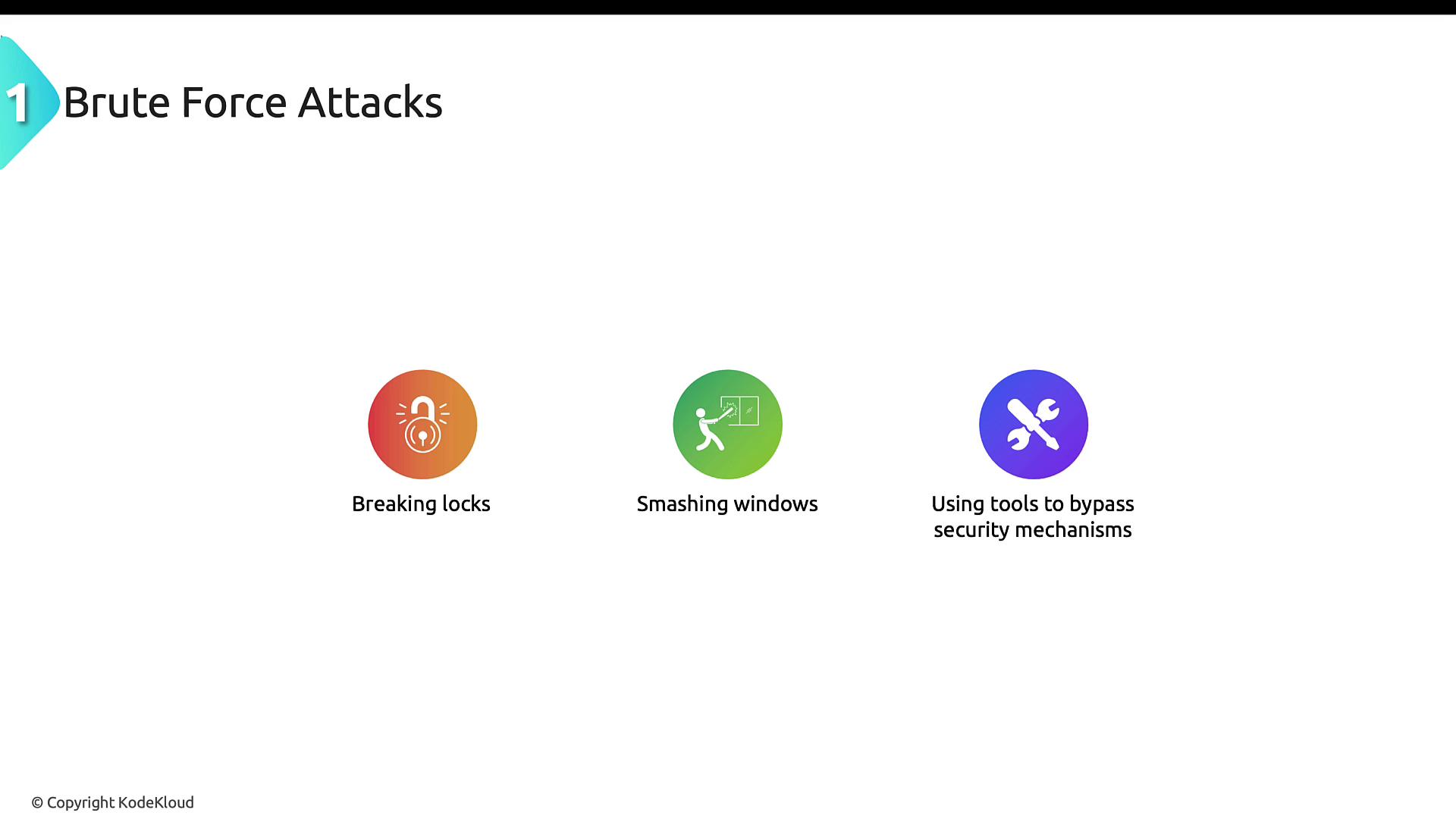
Brute Force Attacks
Brute force attacks in a physical context involve using physical force or tools to gain access to restricted areas or equipment. This type of attack typically exploits weak physical barriers—such as inadequately secured locks or windows—to compromise facilities. It is important to distinguish these attacks from digital brute force methods like password cracking.
In a typical physical brute force scenario, an adversary may, for example, use a crowbar to force open a locked door to a data center, thereby exposing sensitive equipment and data.
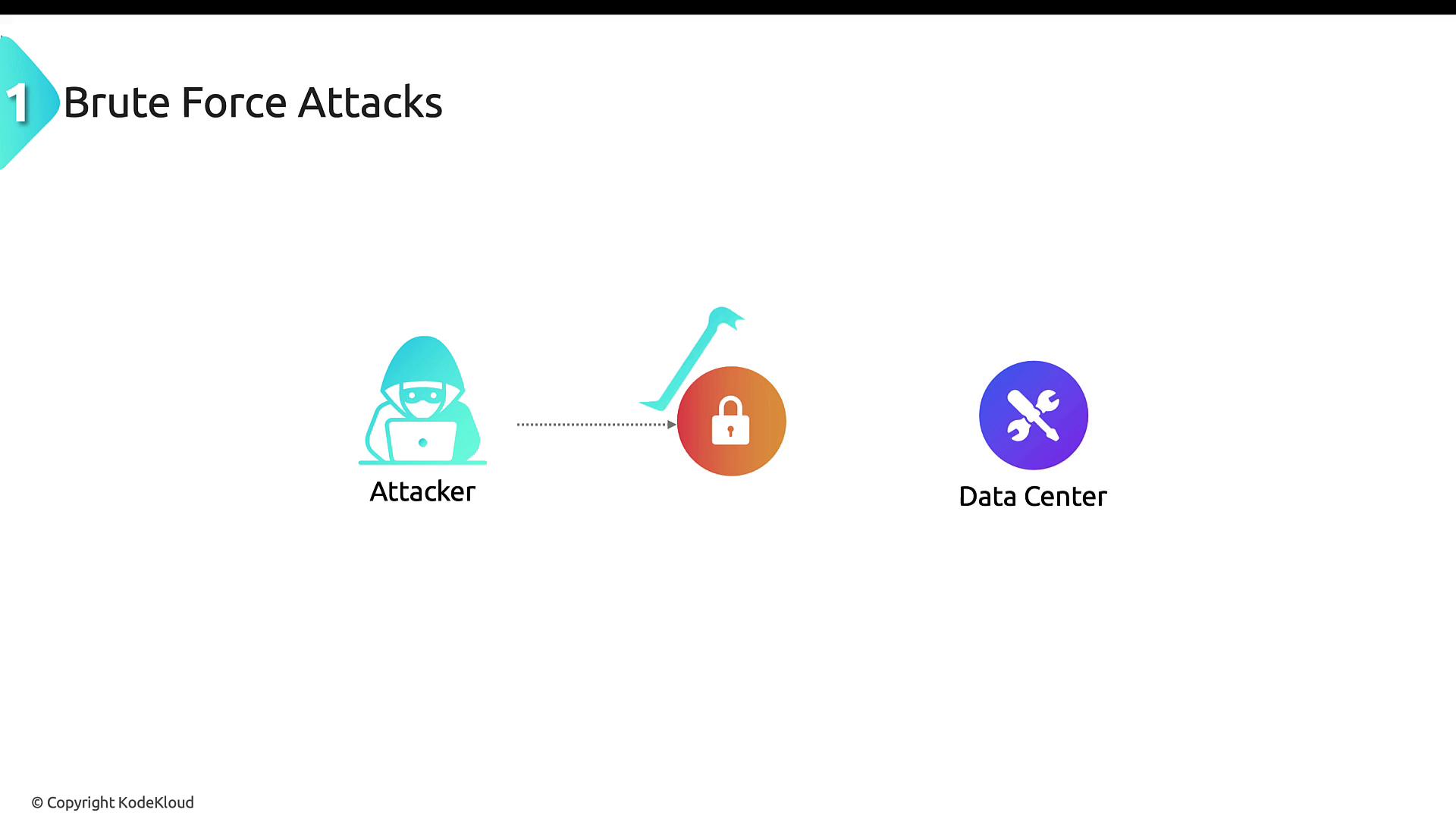
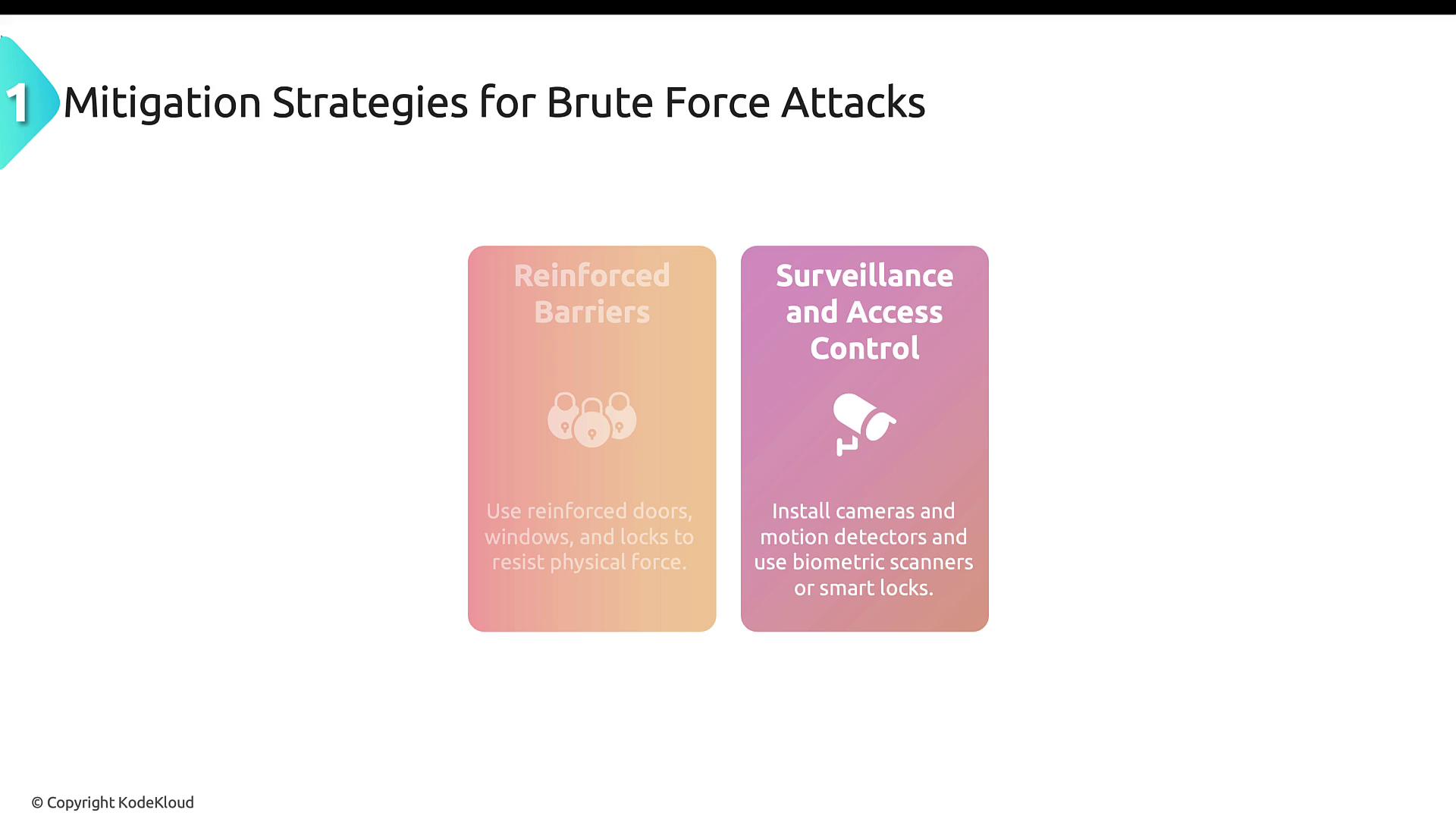
Organizations can mitigate these risks by:
- Reinforcing physical barriers: Use robust doors, windows, and locks that can resist forceful entry.
- Implementing surveillance: Deploy cameras and motion detectors to deter unauthorized access.
- Upgrading access controls: Incorporate advanced mechanisms such as biometric scanners and smart locks.
RFID Cloning
RFID cloning exploits vulnerabilities in employee badges and access cards equipped with RFID chips or magnetic stripes. Attackers use RFID readers to capture signals from these chips, and then duplicate the data onto blank chips to create counterfeit access credentials.
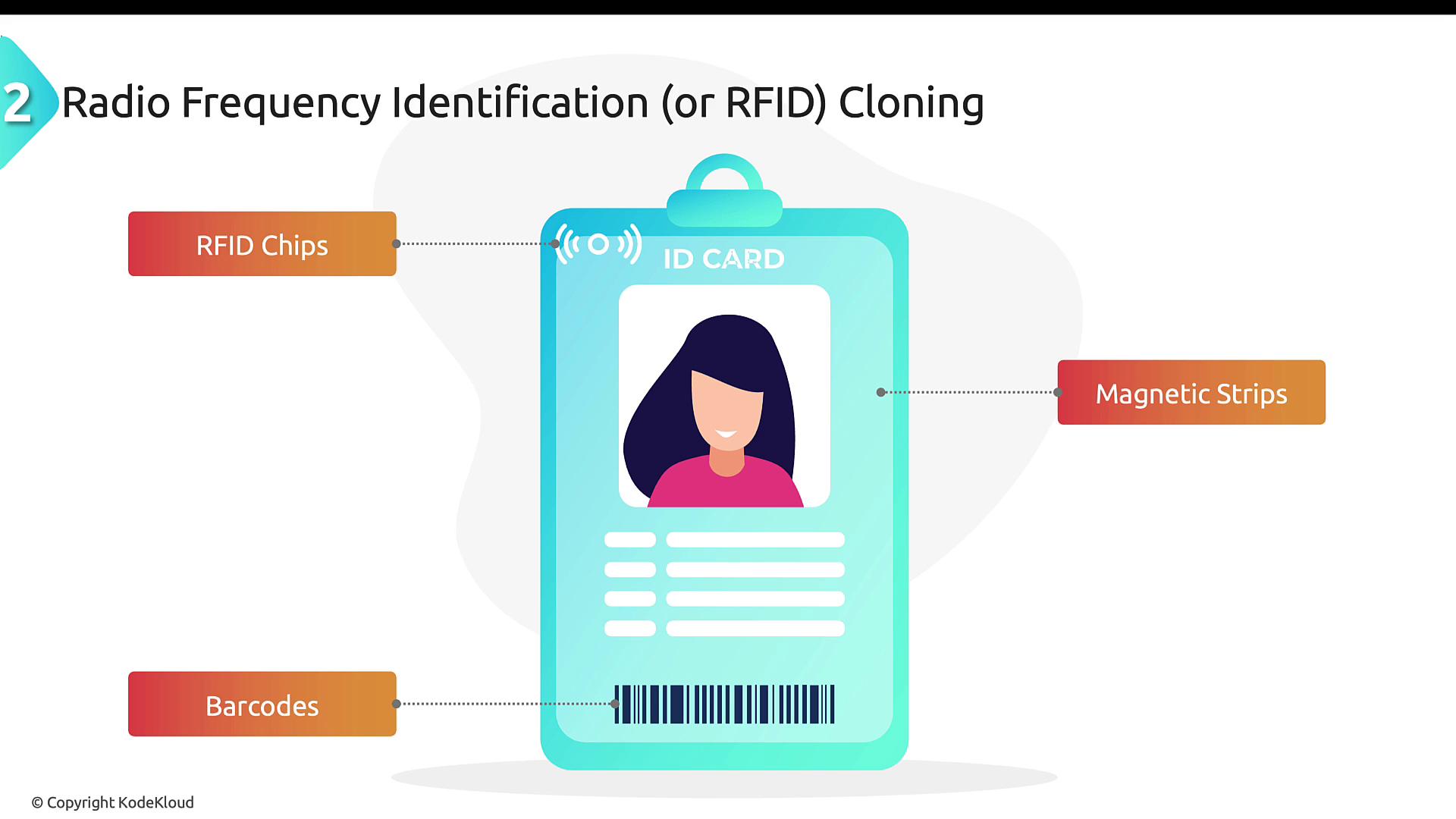
In an RFID cloning attack, the attacker’s goal is to replicate the unique identifier stored on the chip. Once cloned, the duplicate badge permits unauthorized entry, bypassing established security protocols.
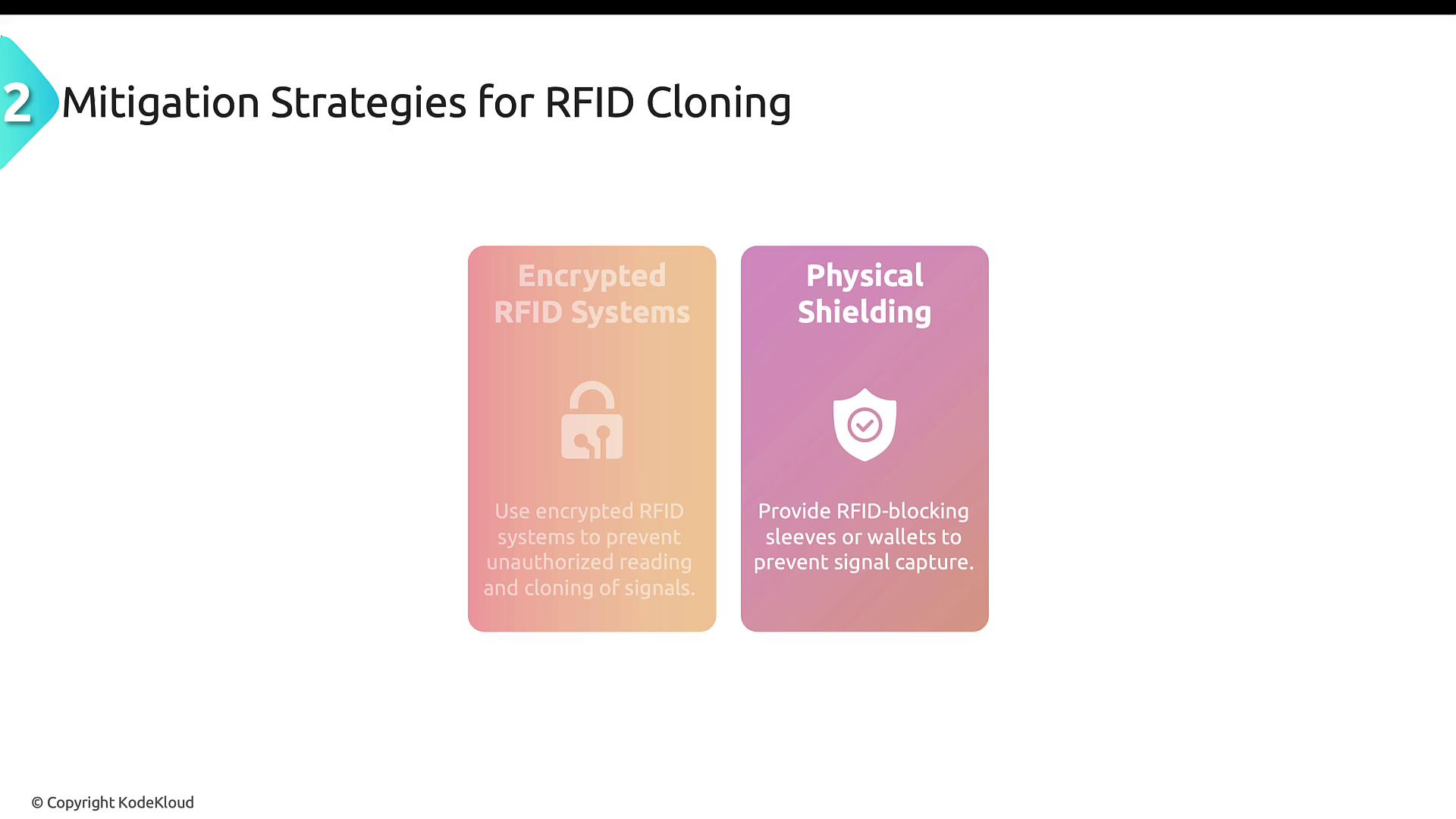
Mitigation measures include:
- Encrypted RFID systems: These prevent unauthorized reading and duplication by encrypting the data.
- Physical shielding: Use RFID-blocking sleeves or wallets to prevent signal interception.
Environmental Attacks
Environmental attacks focus on exploiting external factors—such as temperature, humidity, and power supply—to disrupt or damage systems. These attacks specifically target the availability aspect of the CIA triad.
In an environmental attack, adversaries manipulate environmental conditions to compromise system integrity. For instance, an attacker could gain access to a data center’s HVAC system and alter temperature settings, potentially leading to overheating and equipment failure.
To defend against environmental attacks, organizations should:
- Monitor critical conditions: Deploy sensors to continuously track temperature, humidity, and power supply variations.
- Implement redundant systems: Ensure backup HVAC, power, and environmental controls are in place.
- Strengthen access control: Secure both physical and remote access to environmental control systems.
Note
Implementing layered physical security measures not only mitigates the risk of environmental attacks but also strengthens your overall infrastructure resilience.
Conclusion
Physical attacks present a significant risk to organizational security. Understanding the nuances of brute force attacks, RFID cloning, and environmental attacks is essential for building a robust security perspective. By adopting reinforced physical barriers, advanced surveillance, encrypted and shielded RFID solutions, and comprehensive monitoring systems, organizations can effectively reduce vulnerability and ensure operational continuity.
For further insights into cybersecurity best practices, review our additional resources on modern access control and physical security strategies.
Watch Video
Watch video content