CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Software Vulnerabilities
Understanding software vulnerabilities is critical to securing your IT infrastructure. Vulnerabilities are one of the most significant attack vectors, often stemming from coding flaws that can be exploited if not corrected. As software evolves with new features and continuous updates, the risk of introducing vulnerabilities increases.
Addressing these vulnerabilities requires a robust patching system that rapidly identifies issues, thoroughly tests patches, and implements fixes promptly.
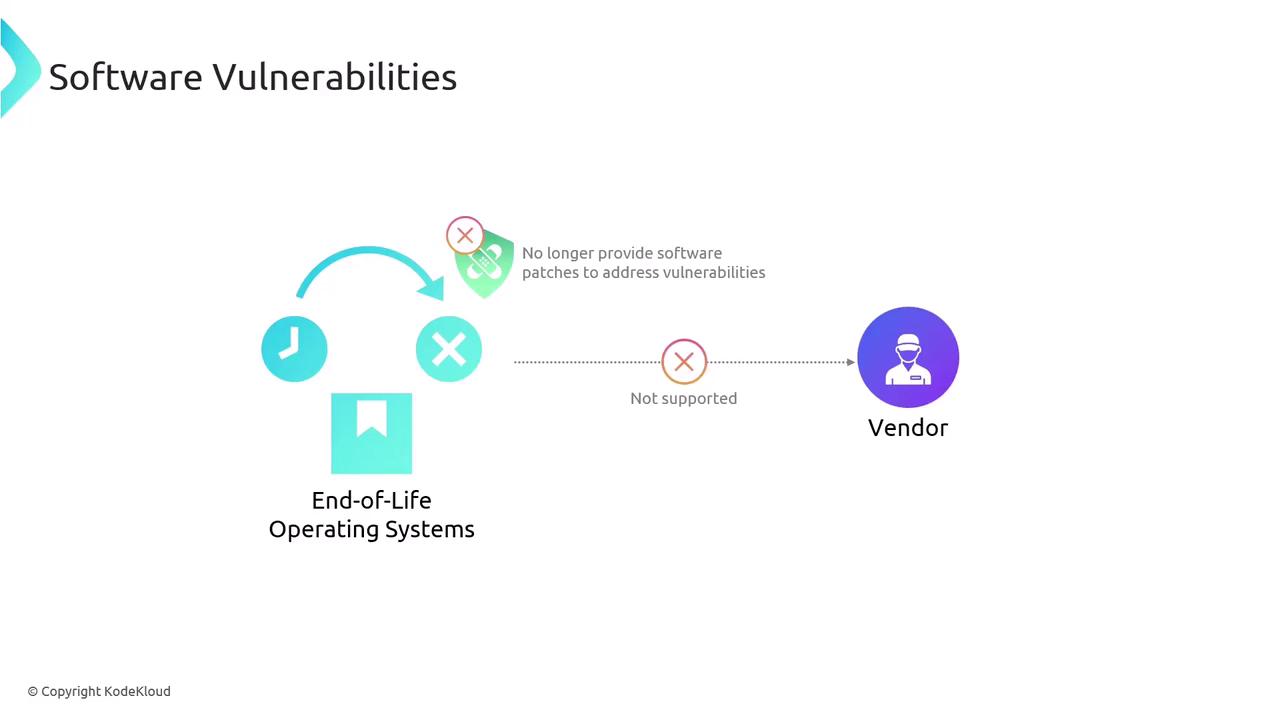
A particular area of concern is end-of-life operating systems. These systems no longer receive vendor support or regular security patches, leaving them especially vulnerable to exploitation. In many instances, while supported products benefit from patches provided by the vendor, unsupported systems are left without this crucial safety net.
Important
Unsupported products and systems can become critical attack vectors. It is essential to either remove, isolate, or remediate these systems promptly to mitigate the risk.
Before effectively addressing software vulnerabilities, it is essential to identify and discover them. There are two primary methods for vulnerability scanning:
- Software agents are installed on each client machine. These agents continuously monitor the system and report vulnerabilities back to a centralized management server.
- Agentless scanning relies on a central server to scan each client directly without installing additional software.
Both approaches offer significant benefits by enabling companies to detect potential threats proactively. However, it is crucial to recognize that these scanning tools can also be exploited by threat actors if not adequately secured, particularly the agentless solutions.
By implementing a solid patch management system and using effective vulnerability scanning tools, organizations can significantly reduce their exposure to risks while continually adapting to the rapidly evolving threat landscape.
Watch Video
Watch video content