CompTIA Security+ Certification
Threats Vulnerabilities and Mitigations
Threat Vectors and Attack Surfaces
Hi, and welcome back!
In this lesson, we explore the critical concepts of threat vectors and attack surfaces in cybersecurity. Later, we will identify various types of threat actors along with the attributes and motivations that distinguish them. There's a lot to cover, so let's dive in.
Imagine your house with its multiple entry points—doors, windows, balconies, and even a garage. These entry points represent the attack surfaces. Similarly, in cybersecurity, attack surfaces include public-facing websites, applications, network ports, and system users.
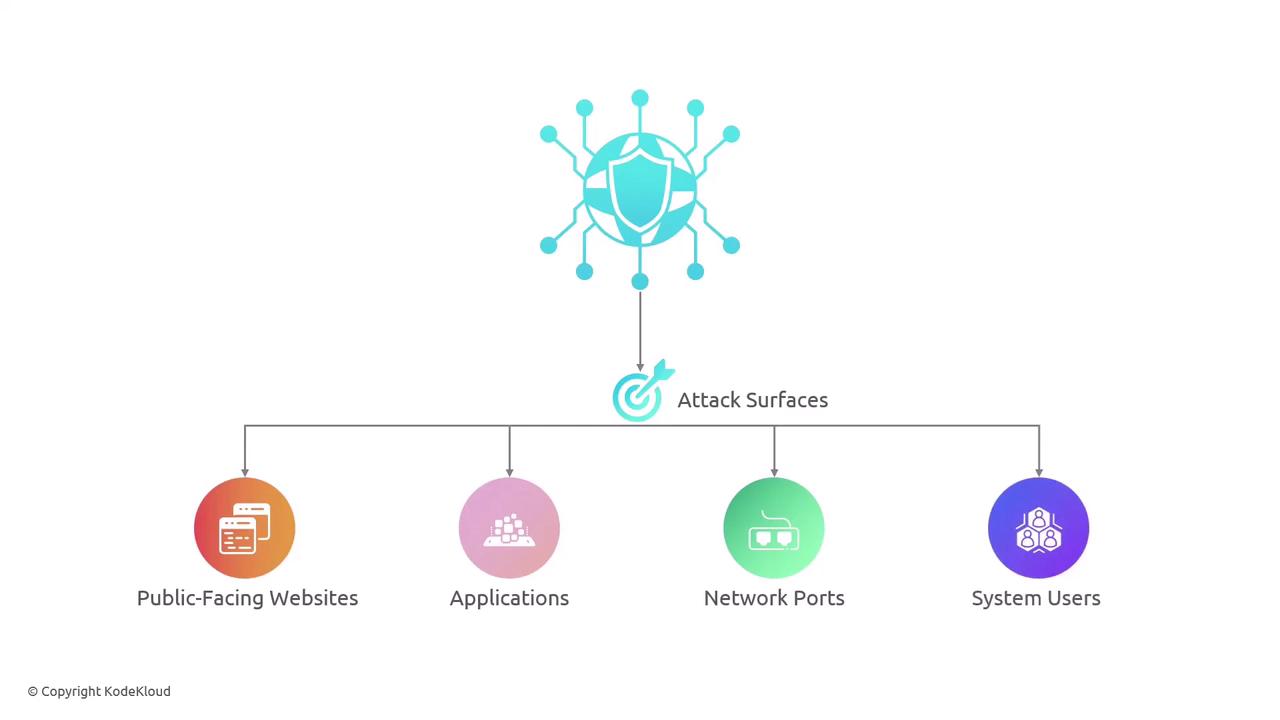
Each of these surfaces must be carefully evaluated for vulnerabilities that attackers could exploit to gain unauthorized access. A threat vector, on the other hand, is the path that an attacker takes to infiltrate the system. Every attack surface forms a part of this overall vector. In many cases, threat actors exploit multiple vectors during a single attack.
This concept is much like burglars attempting to enter a home through several possible points simultaneously.
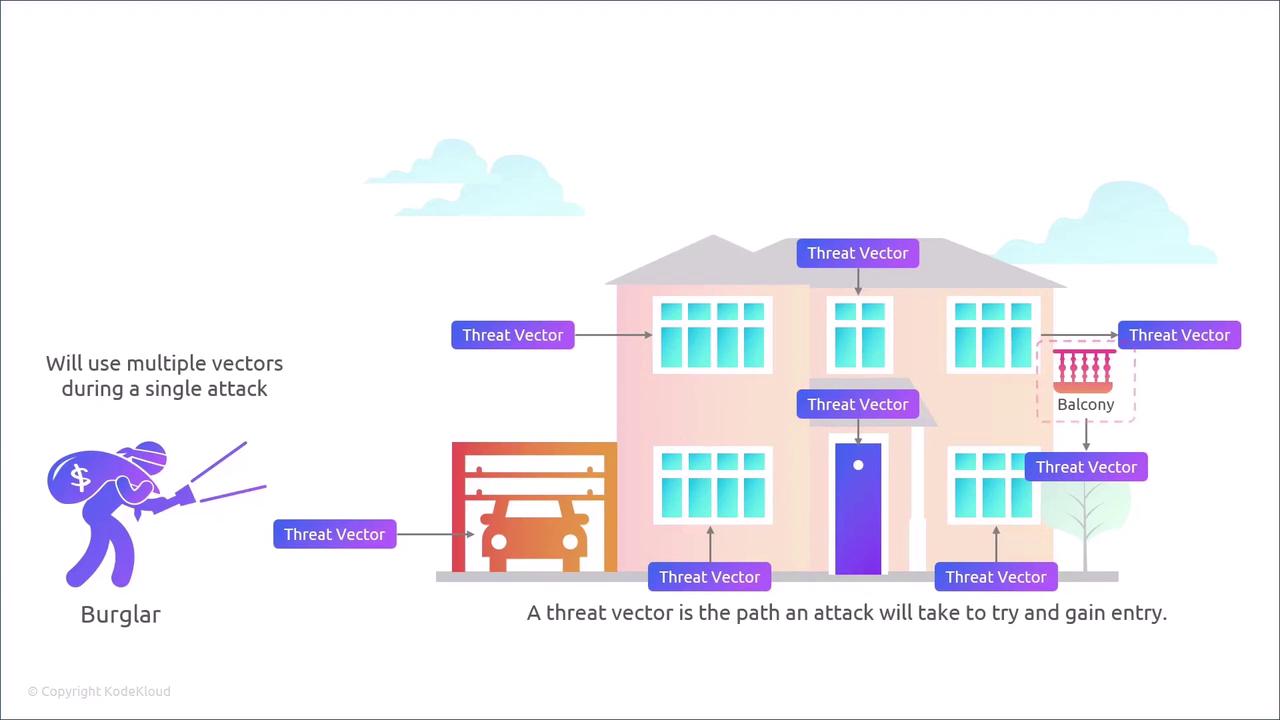
Attackers enhance their chances of success by gathering as much information as possible about a system, thereby increasing the number of potential vectors available for exploitation.
Key Takeaway
Understanding the relationship between attack surfaces and threat vectors is essential in building a robust cybersecurity defense. Regular assessments and vulnerability testing help protect against potential weaknesses.
Watch Video
Watch video content