Overview of Virtualization
Virtualization is the process of creating virtual instances of physical resources such as servers, storage devices, and networks. This technology allows multiple virtual machines (VMs) to run on a single physical host, with each VM operating as an isolated system.
Benefits of Virtualization
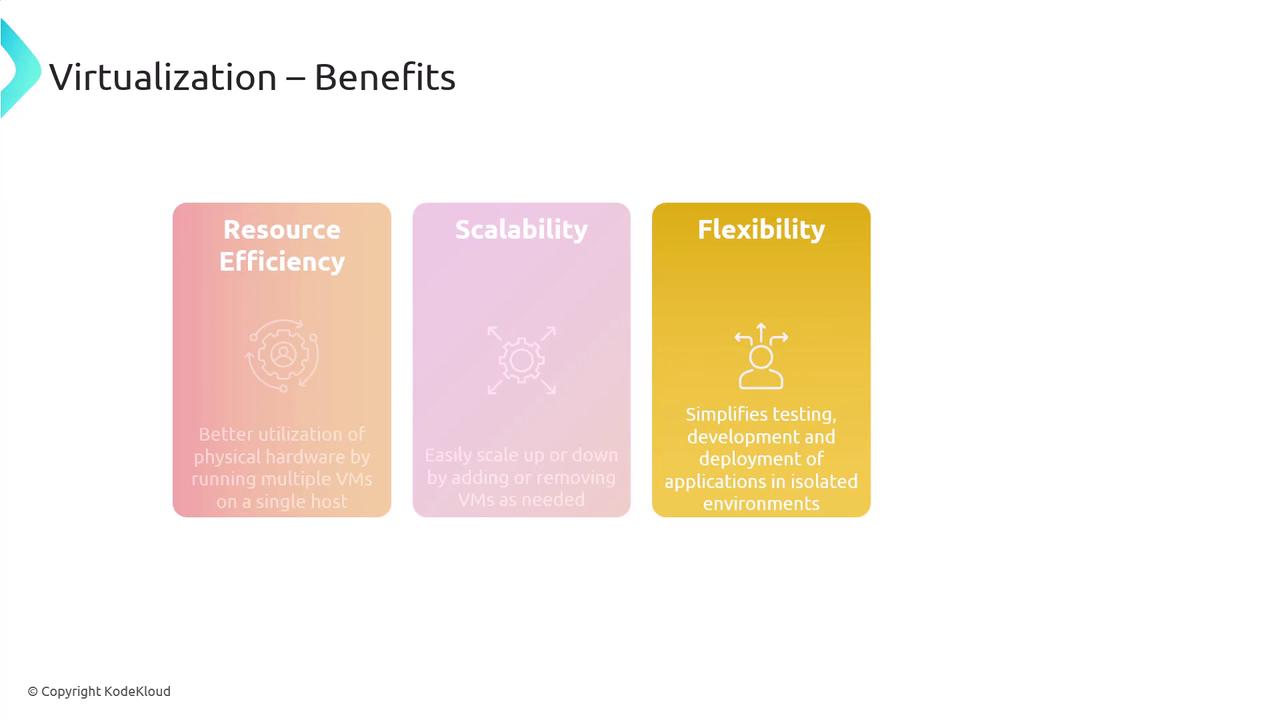
Virtualization brings several key advantages:- Resource Efficiency: Maximizes the use of physical hardware by hosting multiple VMs on a single system.
- Scalability: Simplifies the process of scaling your environment by adding or removing VMs as required.
- Flexibility: Enables isolated testing, development, and deployment environments, along with features like VM snapshots and replication for effective disaster recovery.
Components of Virtualization
Virtualization relies on several critical components, such as hypervisors and virtual machines. The hypervisor is a software layer that facilitates the operation of multiple VMs on a single physical host.
- Type 1 (Bare-Metal): Runs directly on the hardware. Examples include VMware ESXi and Microsoft Hyper-V.
- Type 2 (Hosted): Operates on top of an existing operating system, such as Oracle VM VirtualBox or VMware Workstation.

Security Challenges in Virtualization
While virtualization offers many benefits, it also introduces critical security challenges. One major concern is VM escape, wherein an attacker breaks out of an isolated VM to access the hypervisor or other VMs.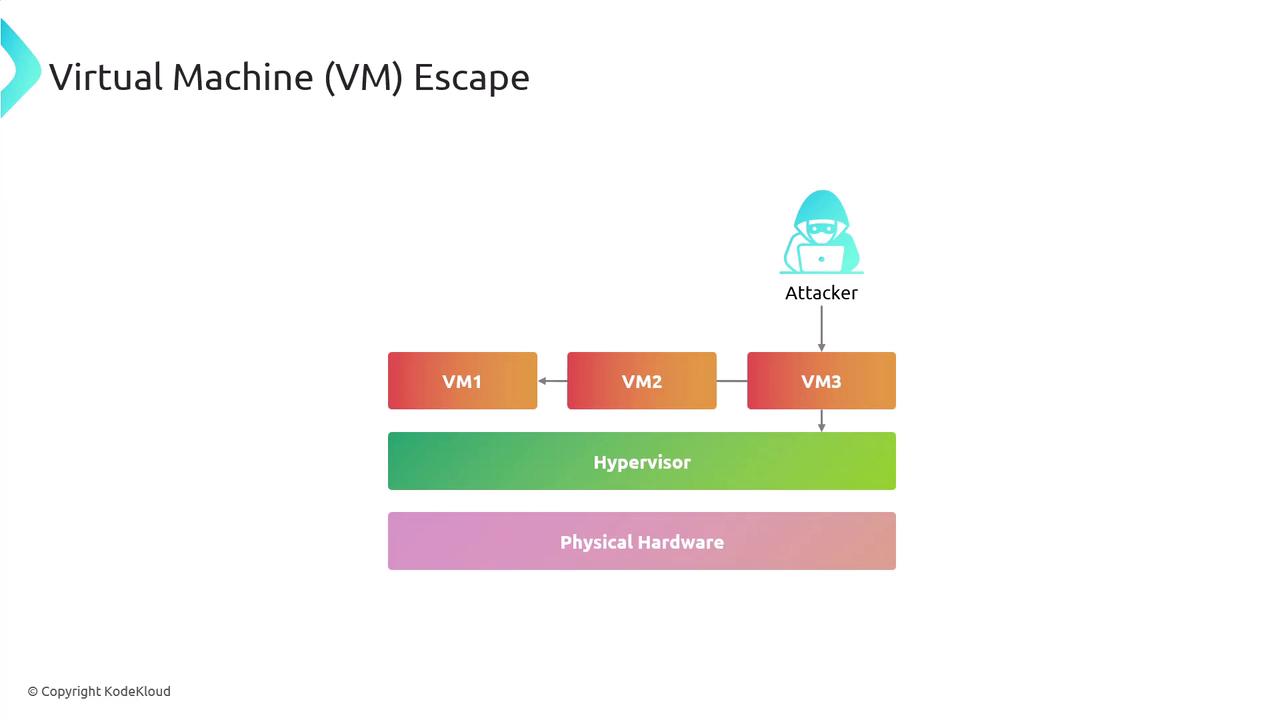
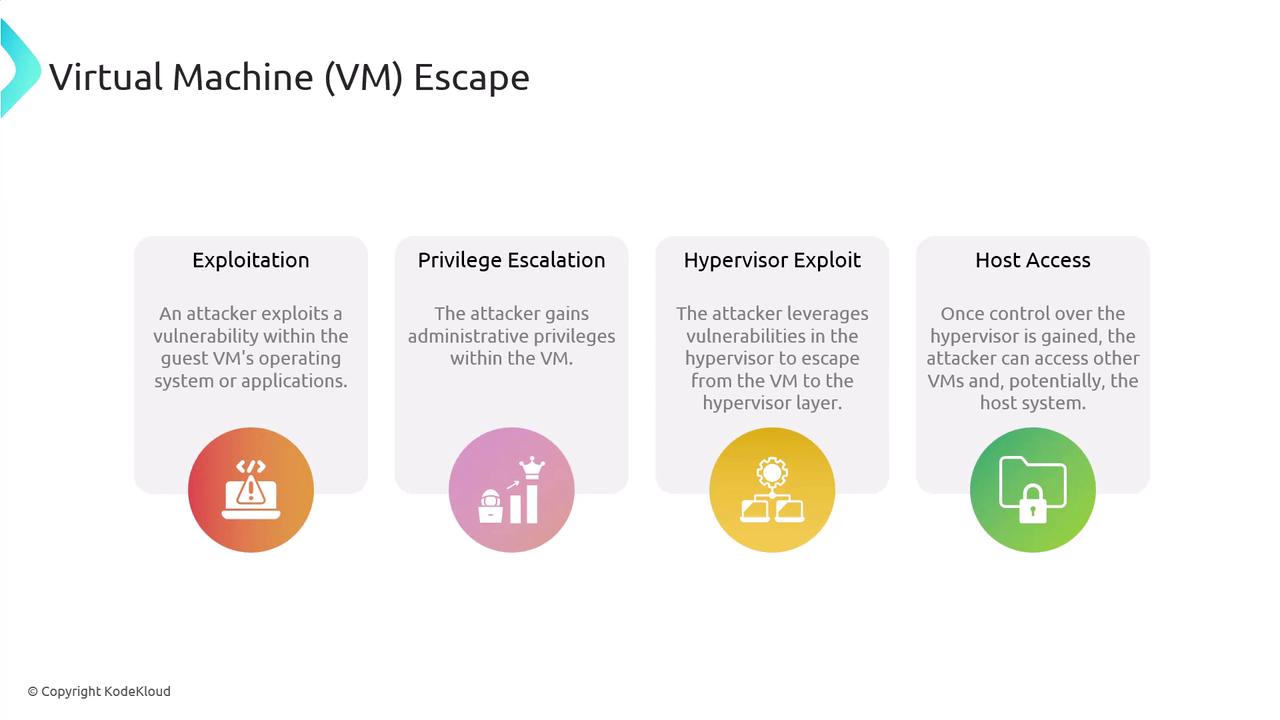
Understanding VM Escape
VM escape typically involves multiple steps:- Exploitation: An attacker discovers and exploits a vulnerability within the guest VM’s operating system or application.
- Privilege Escalation: The attacker acquires administrative privileges within the VM.
- Hypervisor Exploit: Vulnerabilities in the hypervisor are exploited to breach the VM boundary.
- Host Access: After compromising the hypervisor, the attacker can access other VMs and the host system.

Ensure your hypervisors, guest systems, and applications are regularly updated to mitigate VM escape risks.
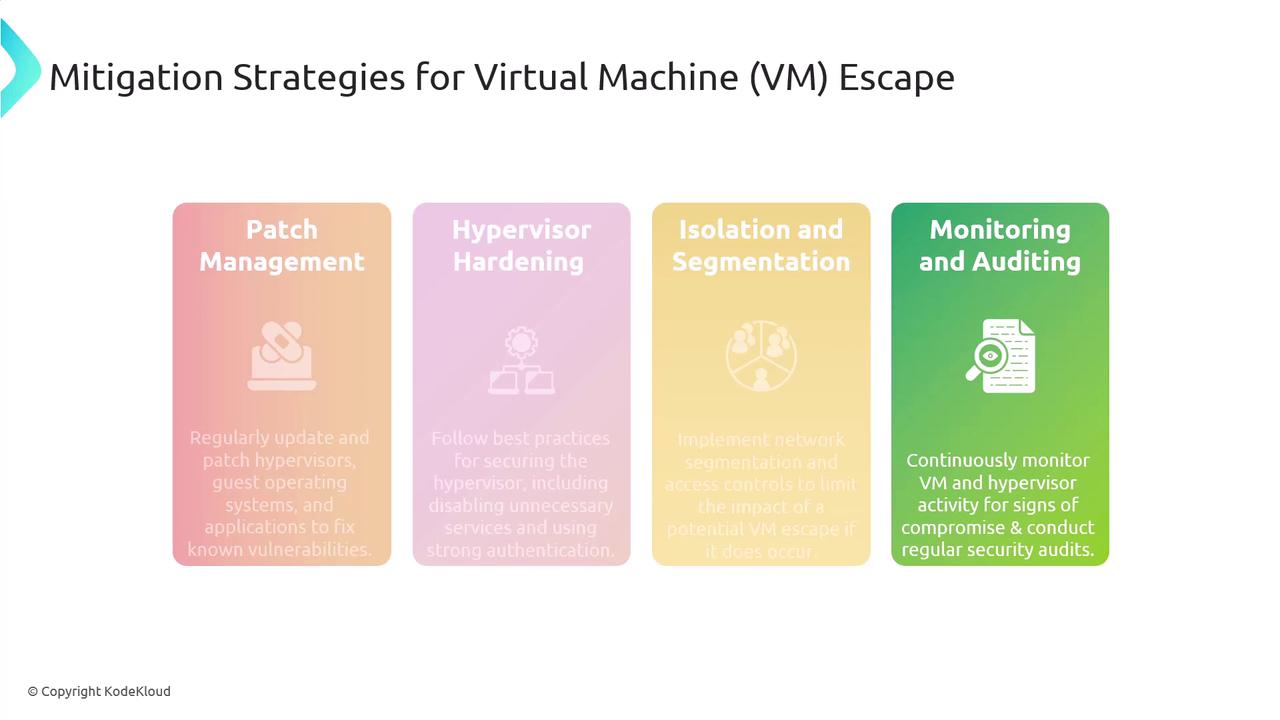
Mitigation Strategies for VM Escape
Several strategies can help prevent VM escape:- Patch Management: Regularly update and patch your hypervisors, guest operating systems, and applications.
- Hypervisor Hardening: Follow industry best practices, such as disabling unnecessary services and enforcing strong authentication on your hypervisor.
- Isolation and Segmentation: Employ network segmentation and strict access controls to limit the impact of a potential attack.
- Monitoring and Auditing: Continuously monitor system activities and perform regular security audits to detect any signs of compromise.
Resource Reuse Issues
Besides VM escape, virtualization may lead to resource reuse vulnerabilities, where sensitive data from one VM might inadvertently become exposed to another due to improper management of shared resources.How Resource Reuse Issues Arise
Resource reuse vulnerabilities often stem from:- Shared Resources: Physical resources like CPU, memory, and storage are commonly shared among VMs.
- Improper Isolation: Inadequate isolation mechanisms might leave residual data from one VM accessible to others.
- Data Leakage: Information from a terminated VM session may be exposed to a new VM if the physical resource is not adequately cleared.

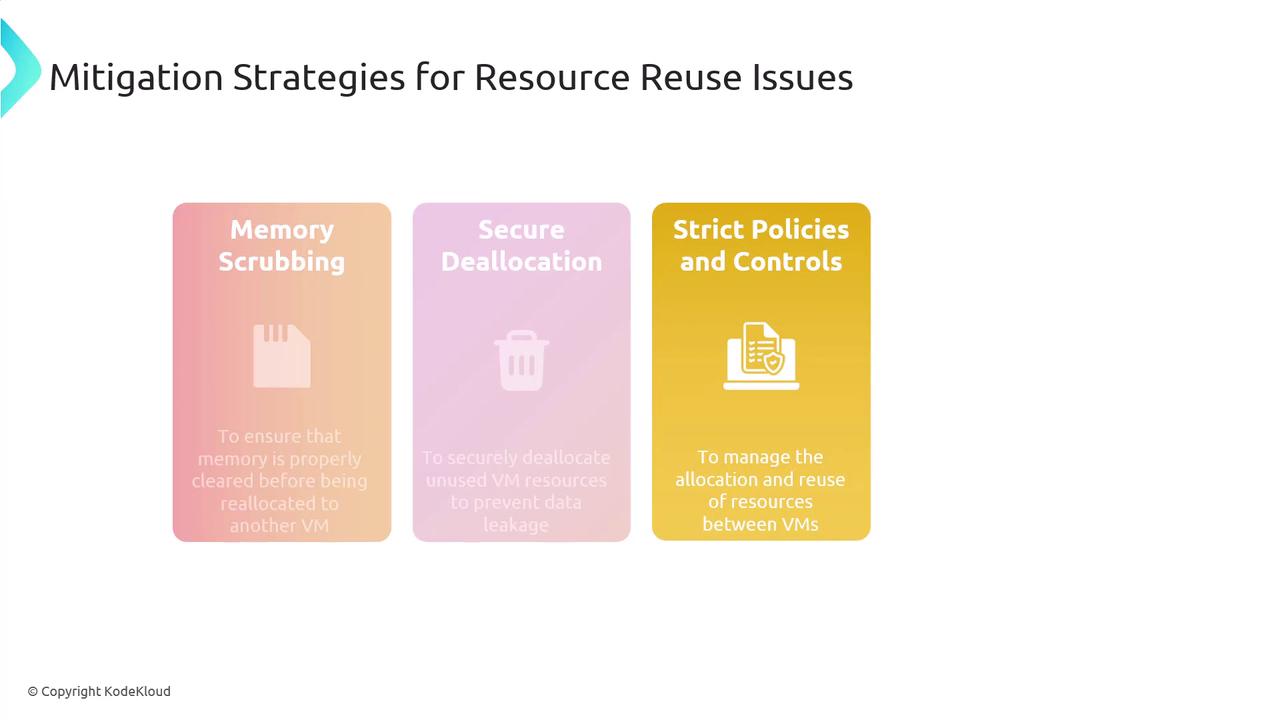
Mitigation Strategies for Resource Reuse
To address resource reuse issues, consider the following strategies:- Memory Scrubbing: Clear memory thoroughly before it is reallocated to another VM.
- Secure Deallocation: Implement secure deallocation protocols for CPU, memory, and storage resources.
- Strict Resource Management: Enforce strict policies to govern the allocation and reuse of resources among VMs.
- Hypervisor Security Features: Leverage built-in security features such as memory isolation and data scrubbing.
Always verify that your virtualized environment enforces data clearance and secure deallocation processes to prevent leakage between VMs.
Conclusion
Virtualization offers tremendous advantages for IT infrastructure, yet it also brings specific security risks. Understanding and addressing challenges like VM escape and resource reuse is essential for protecting your virtualized environments. By implementing best practices in hypervisor hardening, VM management, and resource security, you can fully leverage virtualization while mitigating potential threats.