Demystifying DNS
DNS as a Protocol
DNS as a Protocol
DNS as a protocol involves understanding the structure of requests, responses, and the nuances governing its behavior. At its core, DNS is a network protocol—a set of agreed-upon rules that define how devices communicate. Just like protocols such as TCP or UDP in computer networking, DNS establishes standards for data exchange and interpretation between devices.
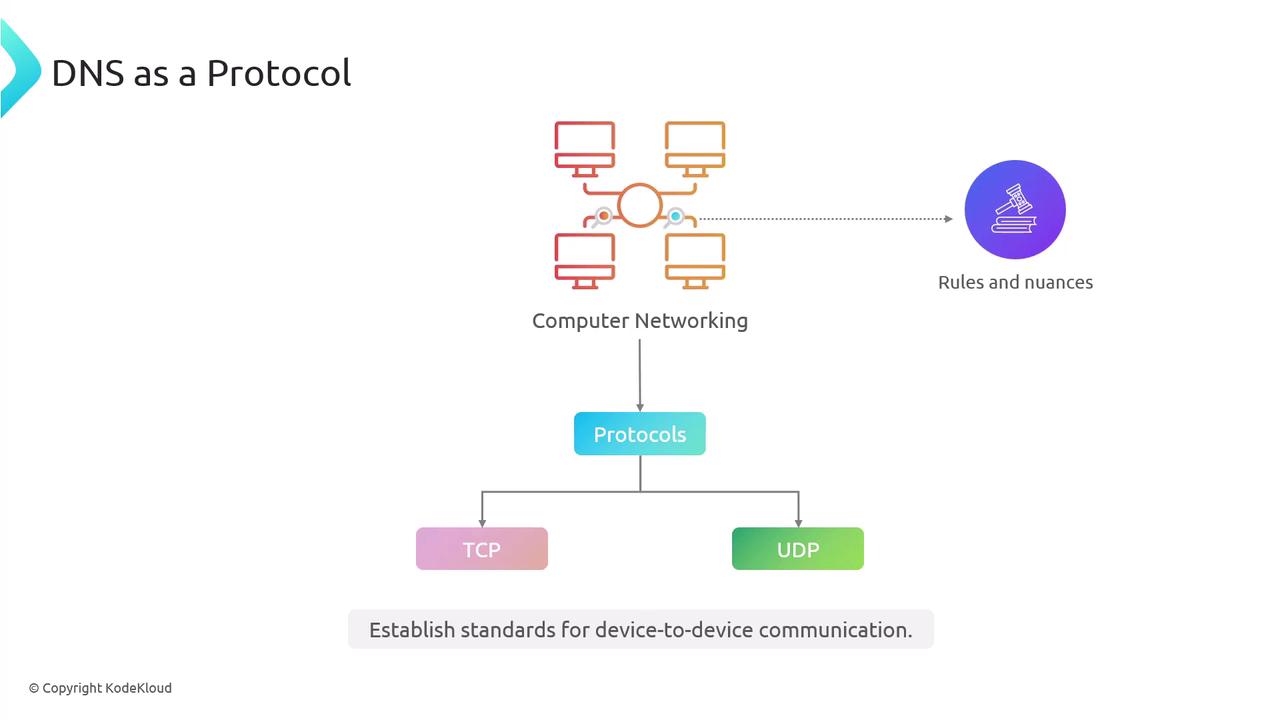
DNS operations run over either TCP or UDP, making it essential to consider these transport protocols when analyzing DNS behavior. Protocols also have hierarchical relationships where higher-level protocols build upon lower-level ones to add specialized functionality. For example, basic transport mechanisms offer the groundwork on which services are layered.
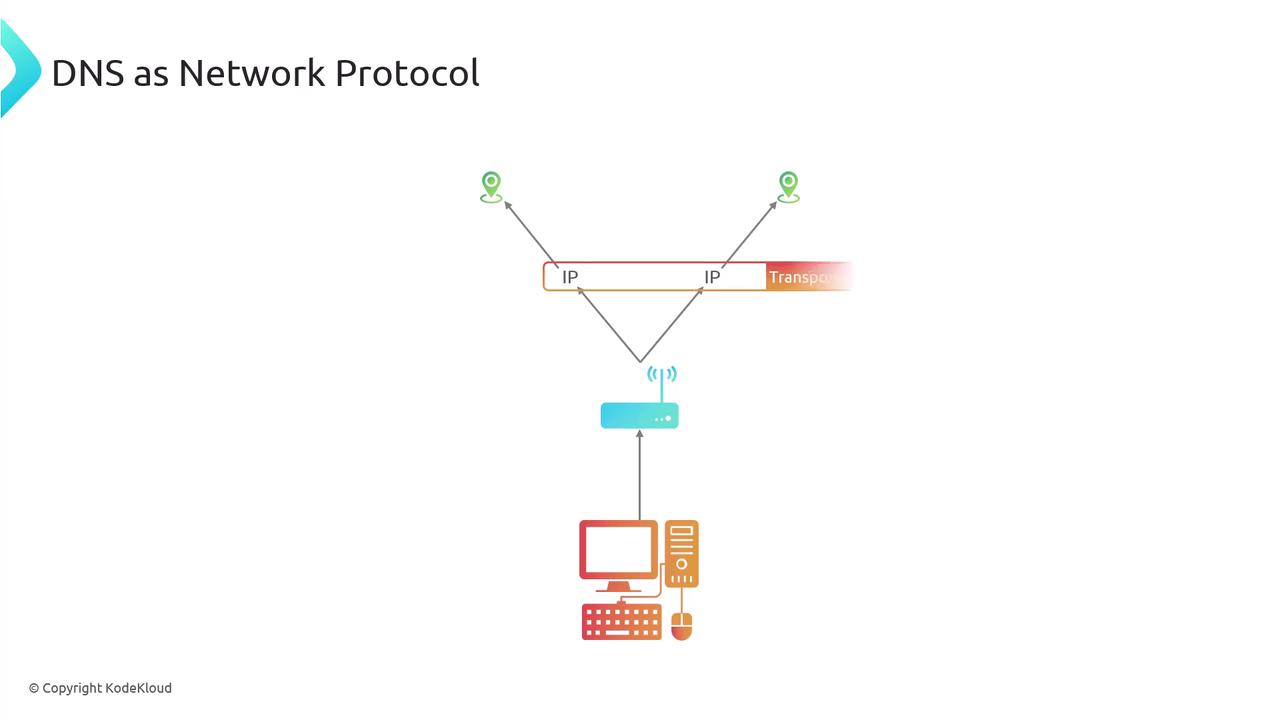
At the base of network communication is IP, which routes data across the Internet using IP addresses. TCP and UDP work with IP to ensure data reaches its destination.
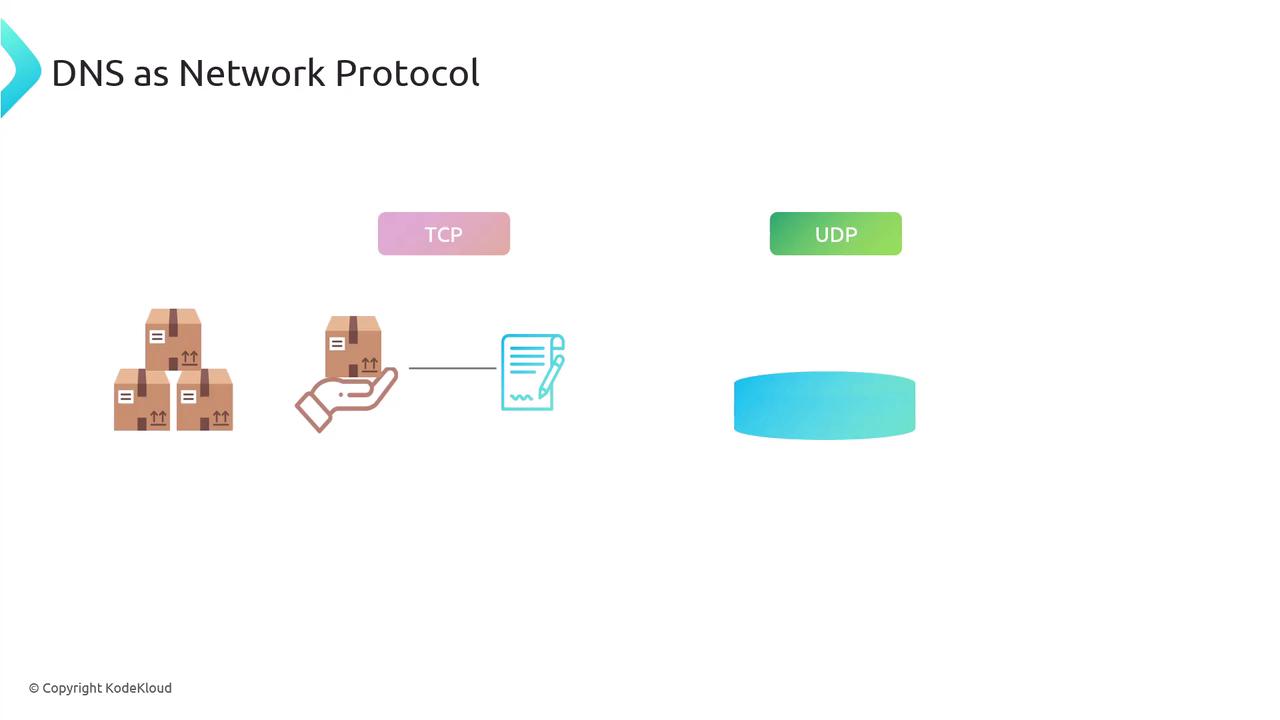
Think of TCP and UDP as two different delivery methods:
- TCP acts like a delivery service that requires a signature for each package, ensuring every packet is received and assembled in the correct order.
- UDP is akin to dropping off all packages at once without confirmation, making it faster but less reliable.
Understanding TCP
TCP ensures reliable delivery through packet identification and acknowledgments:
- Large data is split into smaller chunks, each with unique IDs for proper reassembly.
- Although TCP can support packets up to 65,535 bytes, practical packet sizes are usually around 1,500 bytes due to Ethernet’s Maximum Transmission Unit (MTU).
- Even single-packet data transfers involve sending an acknowledgment (ACK) to confirm receipt.
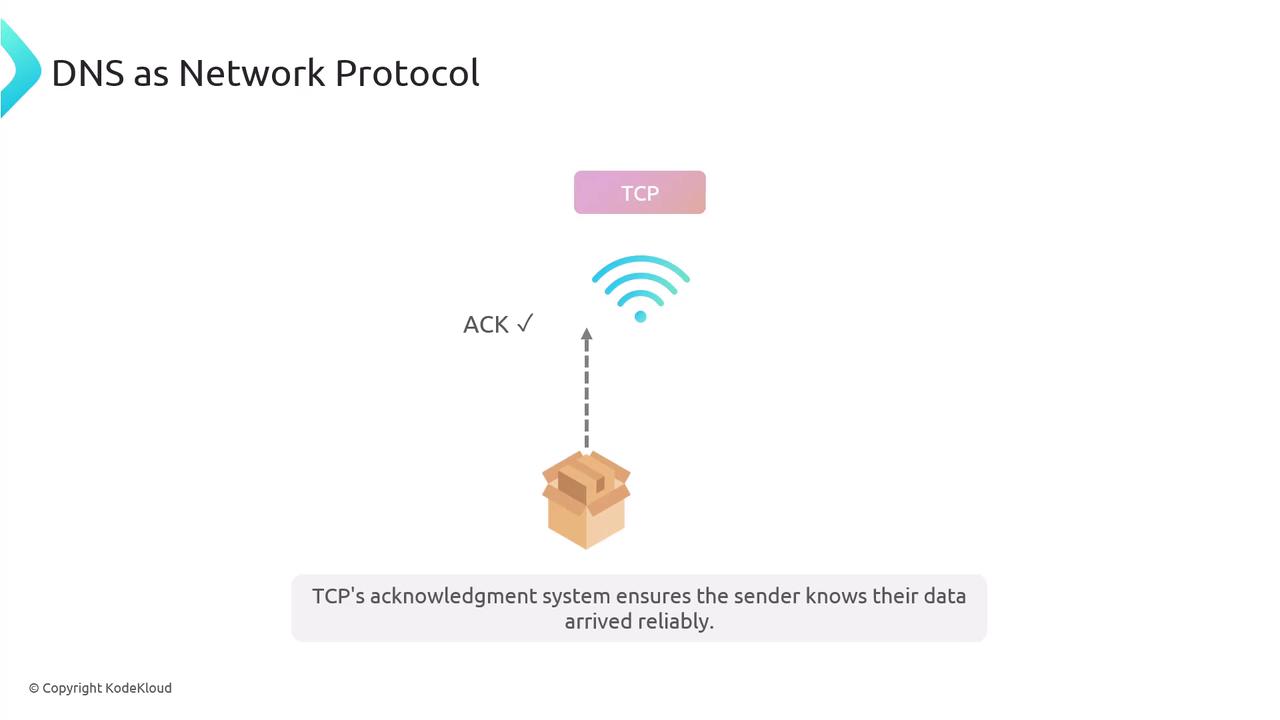
This acknowledgment system is crucial for data-intensive activities such as file downloads, where correctly assembled packets are necessary for retrieving usable files.
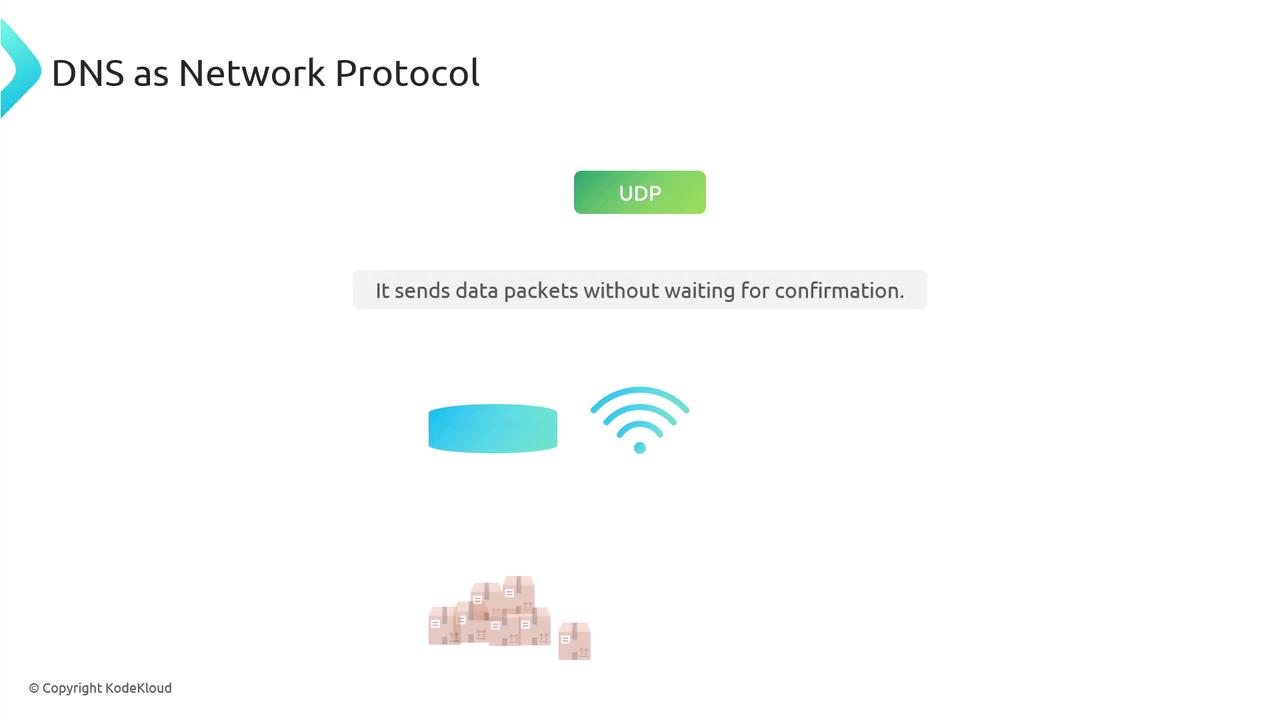
Understanding UDP
UDP transmits data packets without waiting for confirmations, processing packets in the order they are received. Because of its speed, UDP is best suited for applications where timely data delivery is more important than perfect reliability, such as live streaming or gaming.
DNS and Packet Size Constraints
Originally, DNS was designed to use UDP with a strict 512-byte limit per packet. This size was chosen based on IPv4 standards, which require every host to handle packets up to 576 bytes. The breakdown is as follows:
- Up to 60 bytes for IP headers.
- 8 bytes for UDP headers.
- Leaving 512 bytes for DNS data.
This 512-byte design decision even influences infrastructure, such as why there are exactly 13 root name servers—the number of server names that fit within this constraint.
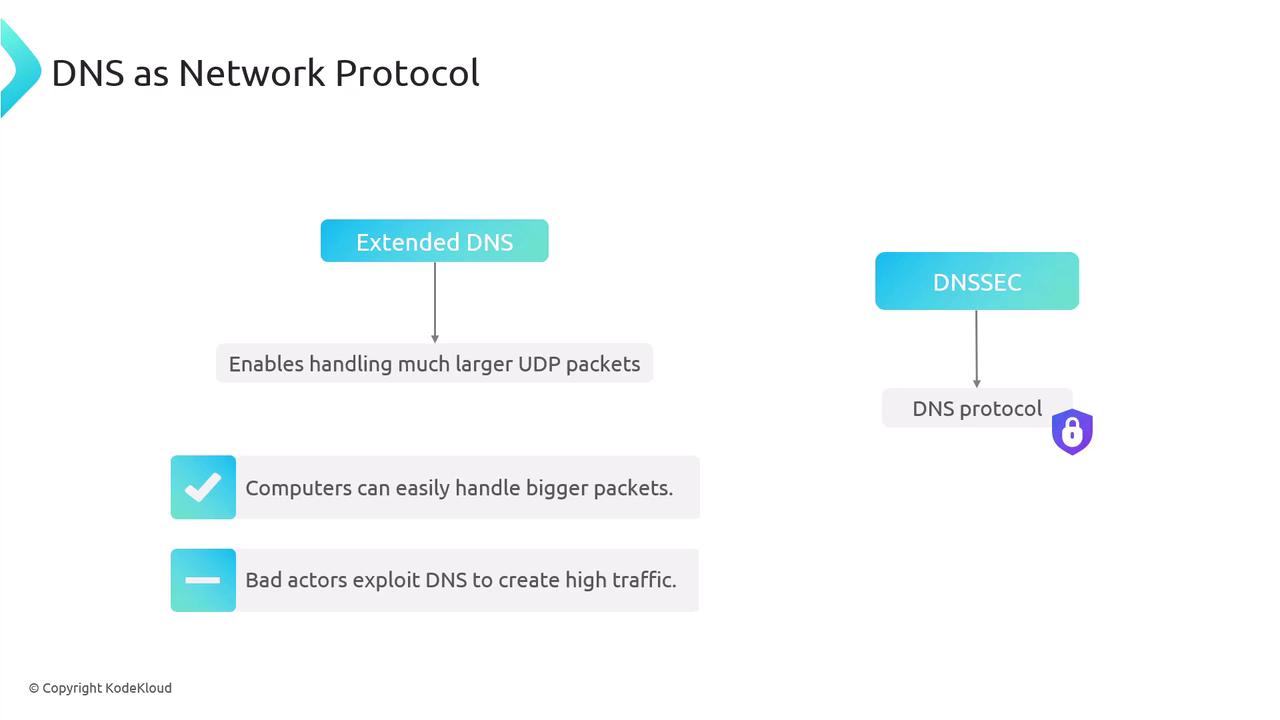
With the advent of Extended DNS (EDNS), larger UDP packets are now supported. EDNS addresses the growing needs of protocols like DNSSEC, which include extra security data in DNS responses. However, the increase in packet size also makes DNS servers vulnerable to amplification attacks.
Protocol Stacking and the HTTP Example
Protocols are often layered to meet new communication demands. For instance, HTTP is built atop TCP:
- A TCP packet carries essential details like source and destination ports, sequence numbers, and checksums.
- HTTP builds on this by adding headers that specify information about the requested resource, content type, and browser details.
- Standard HTTP response codes (such as 404 for "Not Found" or 504 for "Gateway Timeout") ensure consistent behavior across applications.
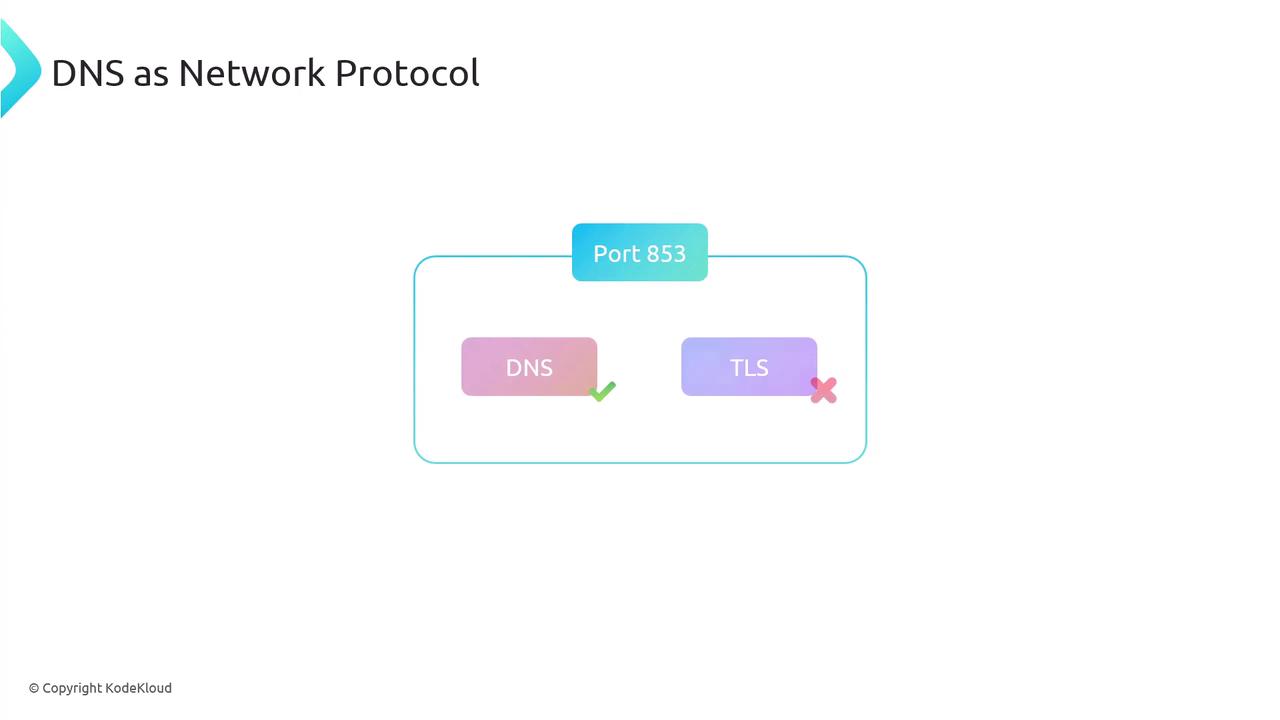
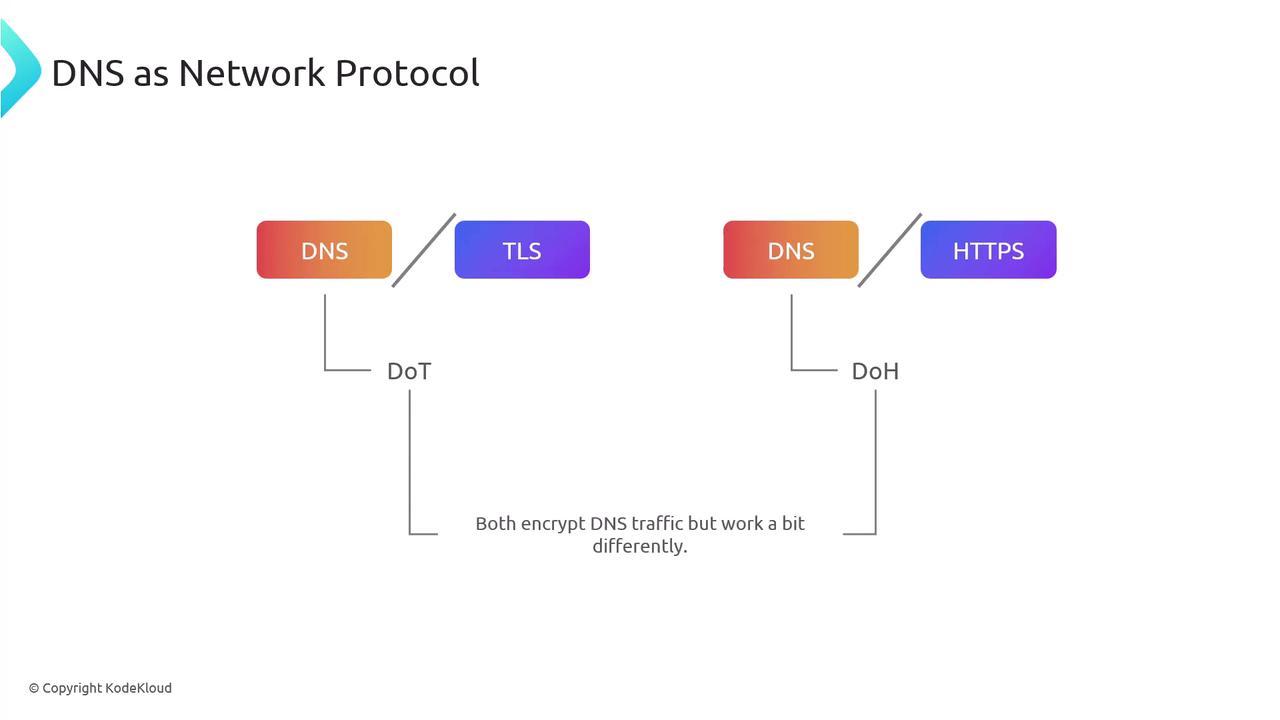
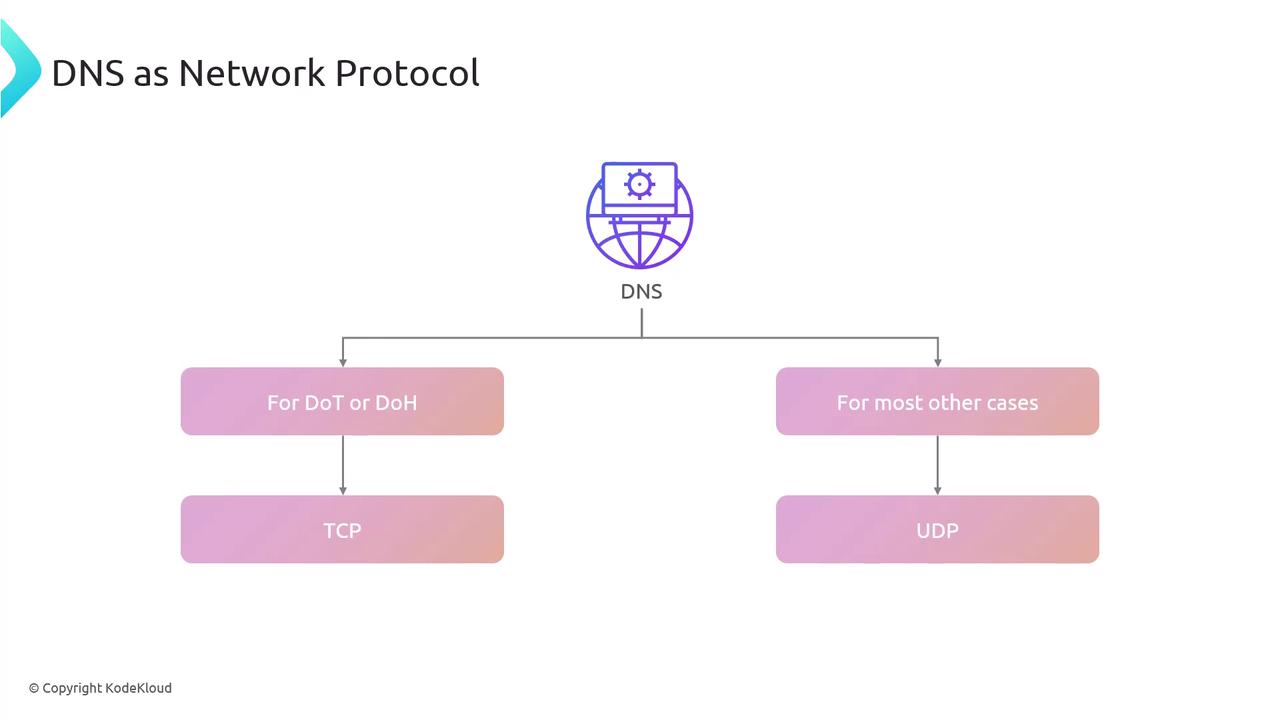
Similarly, DNS standardizes its requests and responses, typically using UDP for speed. By design, DNS responses on UDP are transmitted on port 53, with port 853 reserved for DNS over TLS (DoT).
Secure DNS
Ensuring security for DNS transmissions is achieved through encryption methods such as DNS over TLS (DoT) and DNS over HTTPS (DoH). Both encrypt DNS traffic, though they have operational differences. When using DoT or DoH, DNS communications shift to TCP instead of UDP. In other cases, DNS typically defaults to UDP but falls back to TCP when:
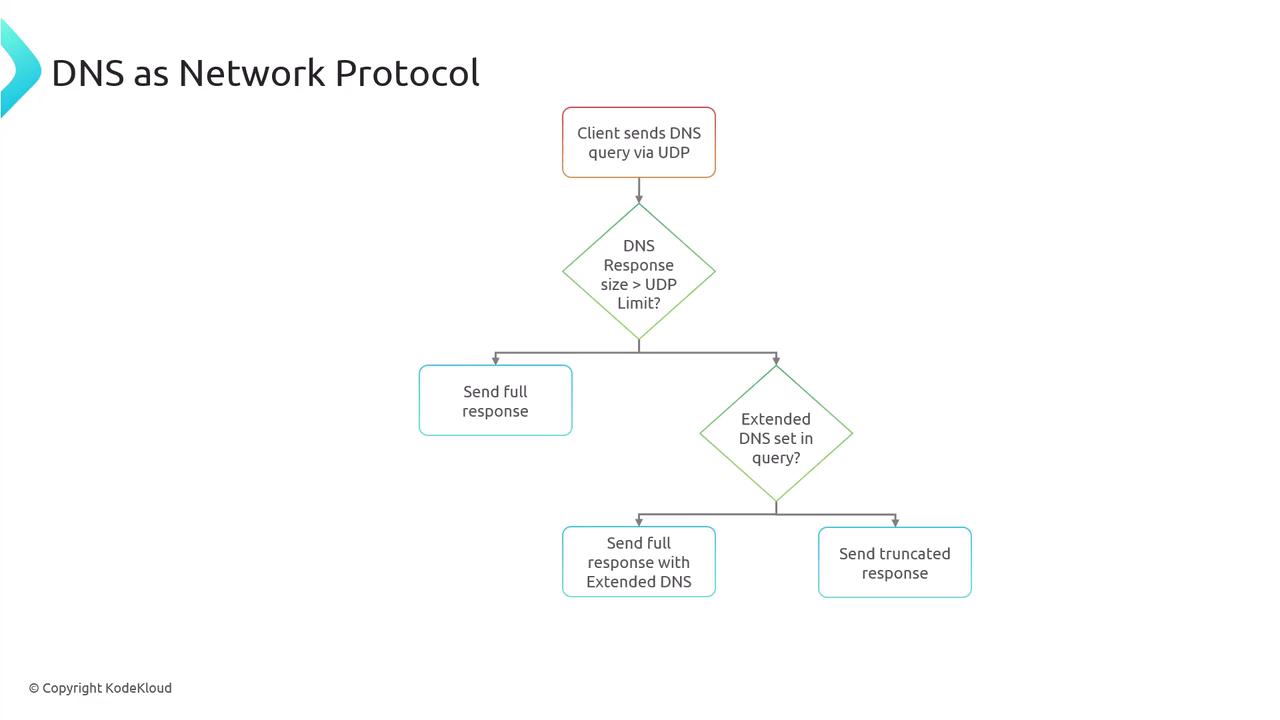
- A response exceeds the 512-byte limit and extended DNS is not supported.
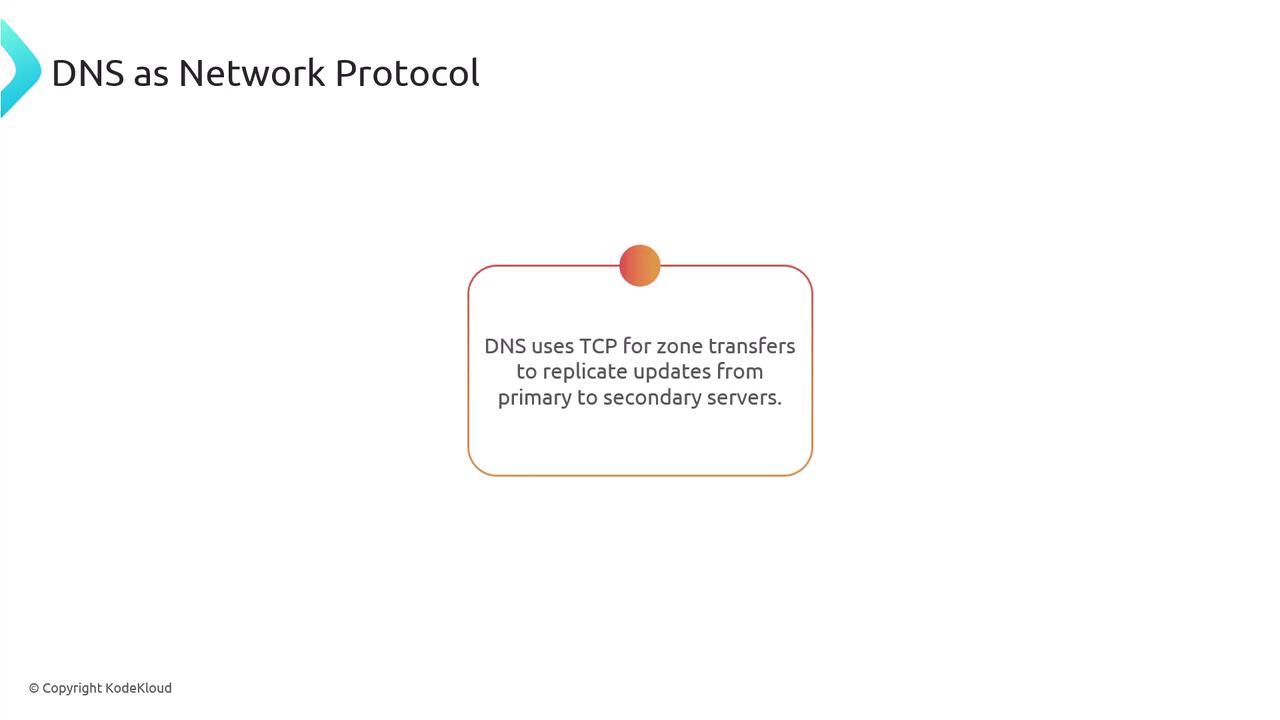
- Zone transfers occur during the replication of data from a primary nameserver to secondary servers.
Handling Large DNS Responses
When a DNS response exceeds the 512-byte limit—and extended DNS is not indicated—a truncated UDP response is sent. The client then retries the request over TCP. Additionally, TCP is used for zone transfers, ensuring that updates are accurately replicated from primary to secondary nameservers.
Wrapping Up: DNS in the Network Stack
DNS is a sophisticated protocol that powers a globally distributed system, incorporating principles from computer networking, system design, high-performance databases, and global internet routing. It shares similarities with database sharding by distributing load across multiple nameservers.
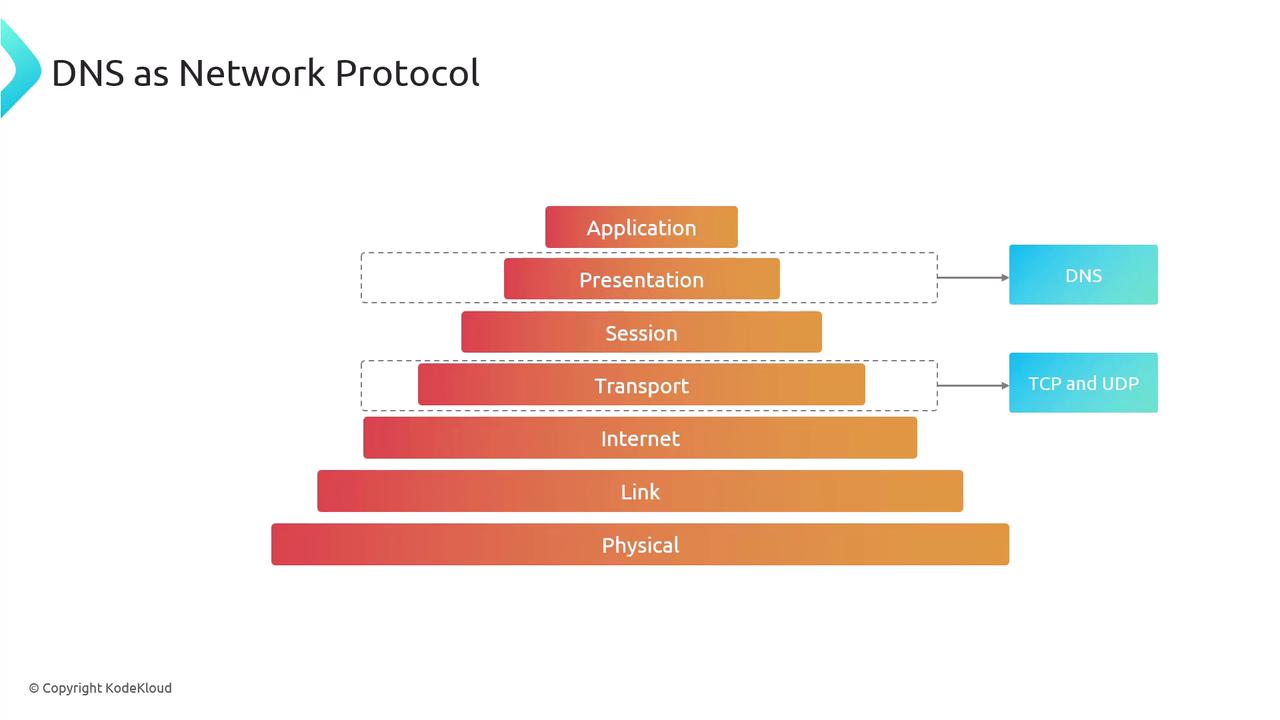
A quick note on its placement in the OSI model: DNS typically operates at the application layer (layer 7), while TCP and UDP function at the transport layer (layer 4).
Note
Later, we will delve deeper into how DNS requests and responses are formed, further enhancing your understanding of tools like dig.
Watch Video
Watch video content