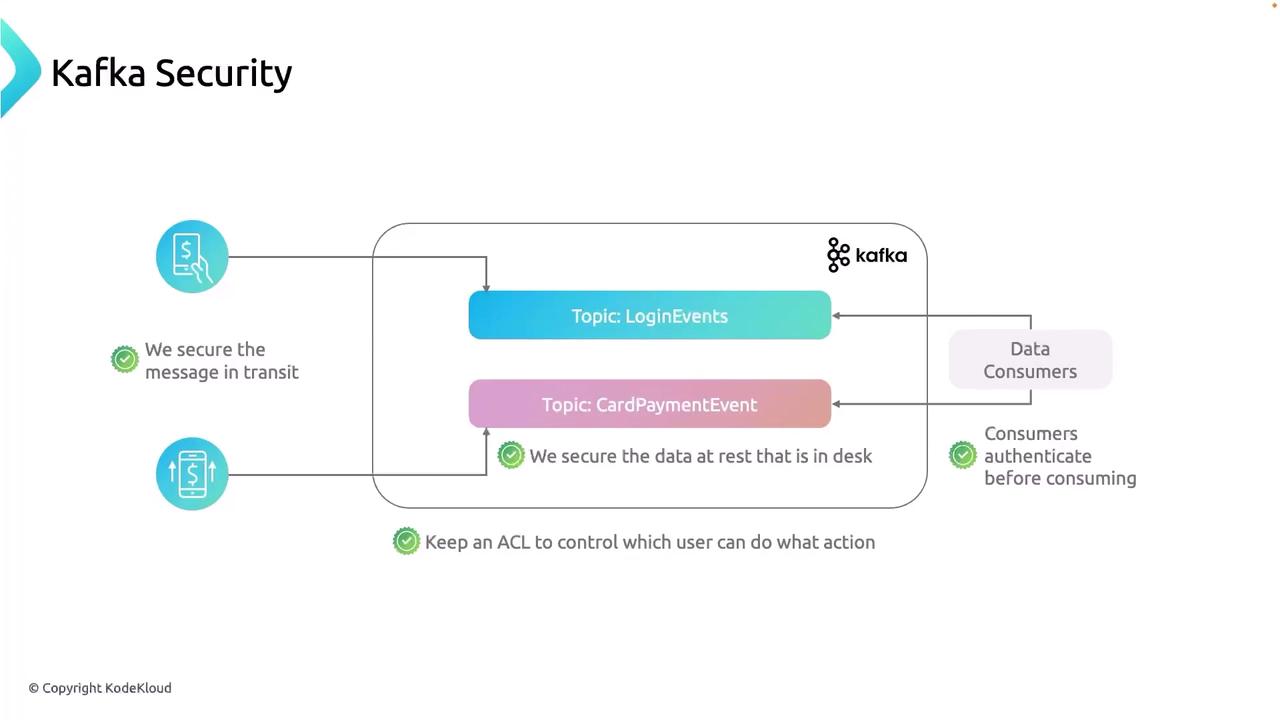
1. Authentication Methods
Applications and microservices must prove their identity before accessing Kafka topics. Here are the three most common authentication mechanisms:| Method | Pros | Cons | Recommended Use |
|---|---|---|---|
| Username/Password | Easy setup, minimal overhead | Credentials can be compromised | Development, QA |
| Kerberos | Strong, enterprise-grade security | Complex KDC installation & upkeep | Large organizations with dedicated security teams |
| SSL/TLS | End-to-end encryption, certificate management | Moderate operational effort | Production |
Use Username/Password for quick testing and non-sensitive workloads. For production, prefer SSL/TLS unless you have experts managing a Kerberos KDC.
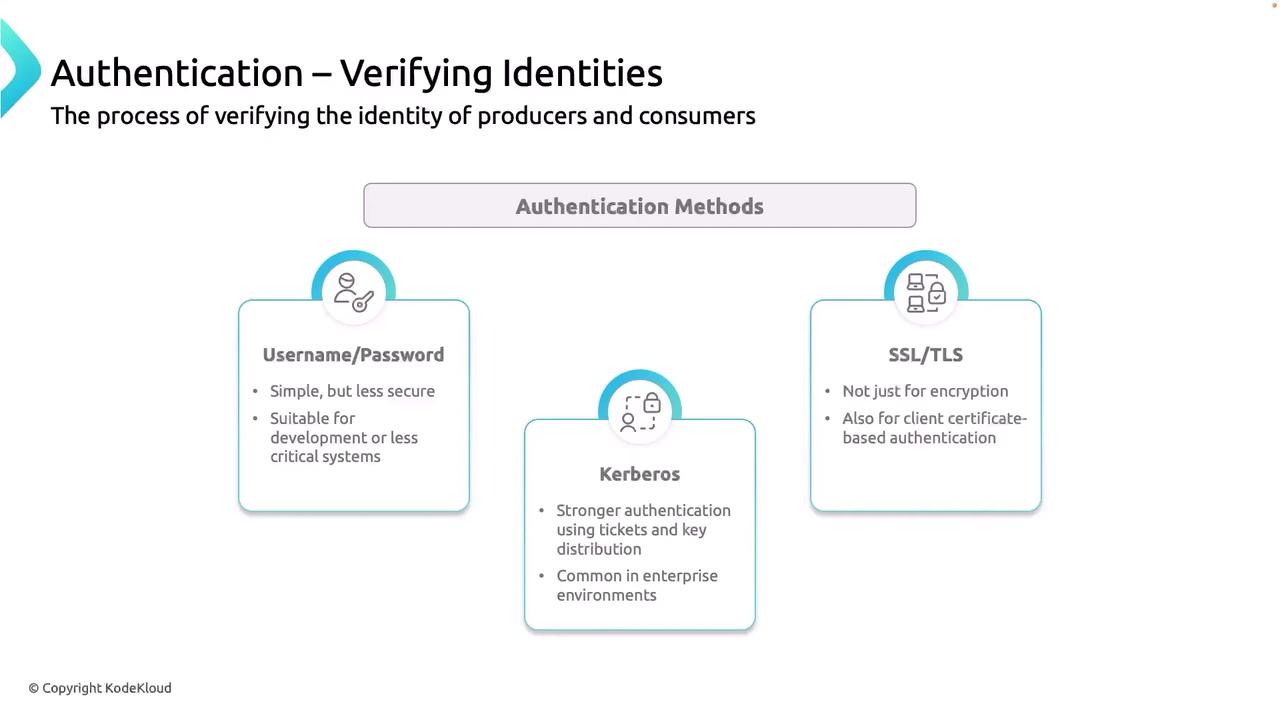
2. Authorization with Access Control Lists (ACLs)
After verifying identity, enforce fine-grained permissions by defining Kafka ACLs. ACLs control which principals can performREAD, WRITE, or DESCRIBE operations on resources such as topics and consumer groups.
Example ACL definitions:
Restricting each service to only its allotted topics reduces the impact of compromised credentials.
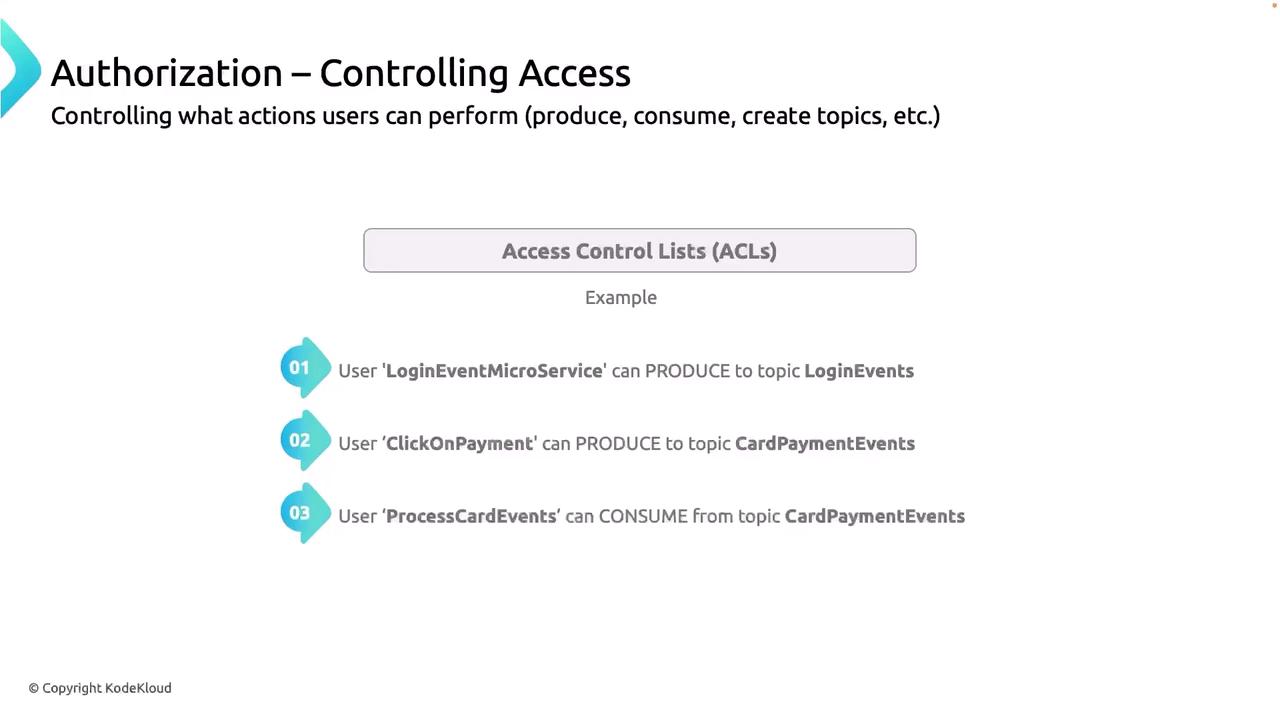
3. Data Protection (Encryption at Rest)
Kafka retains messages on disk, so encrypting “data at rest” is essential. Depending on your environment, you can choose:| Encryption Layer | Tools / Services | Use Case |
|---|---|---|
| Operating System-Level | LUKS (Linux), BitLocker (Windows) | On-prem servers |
| Hardware-Level (Self-Encrypting Drives) | SED-A, Intel® QLC SSDs | Dedicated appliances |
| Cloud-Provider Disk Encryption | AWS EBS, Azure Disk Encryption | Public cloud deployments |
For AWS-based Kafka brokers, attach encrypted EBS volumes and enable AWS Key Management Service (KMS) for key rotation.
4. End-to-End Security Posture
A robust Kafka security architecture integrates all layers:- Authentication – Use SSL/TLS or Kerberos (or Username/Password in non-prod).
- Authorization – Apply ACLs to limit topic and group access.
- Encryption (at rest) – Enable disk encryption via OS, hardware, or cloud provider.
Do not skip ACL enforcement or disk encryption in production—failure to secure any layer can expose sensitive data.