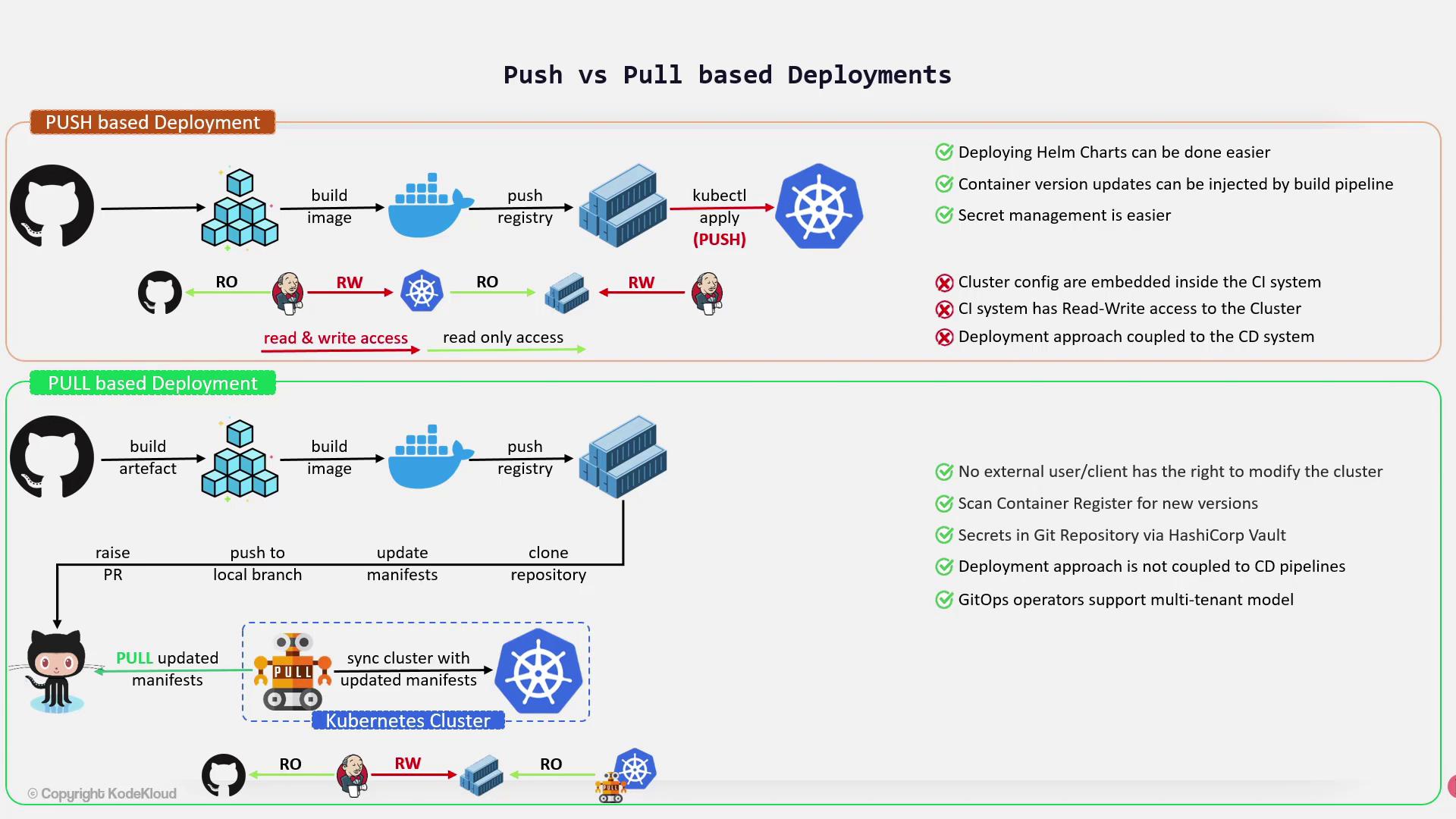
Push-Based Deployment
Push-based deployment is commonly used in CI/CD pipelines. With this approach, the application code goes through various stages within the CI pipeline before updates are pushed directly to the Kubernetes cluster.Key Characteristics
- The CI system requires read-write access to the Kubernetes cluster, which means Kubernetes credentials are stored in the CI system outside the cluster. This arrangement may introduce potential security risks.
- Typically, the CI system has read-only access to the Git repository and read-write access to the container registry, while the Kubernetes cluster itself only has read-only access to the registry.
- Deployments can leverage a variety of plugins and tools. For instance, Jenkins can use multiple plugins or approaches, and Helm plugins further simplify the deployment of Helm charts.
Storing Kubernetes credentials in the CI system exposes a potential security risk, as these credentials grant read-write access to the cluster.
Challenges
- The deployment configuration is tightly coupled with the CI system. Migrating from one CI platform to another (for example, switching from Jenkins to a different platform) often requires reworking many deployment configurations.
- Embedding cluster credentials in the CI system increases the risk of unauthorized access if the CI system is compromised.
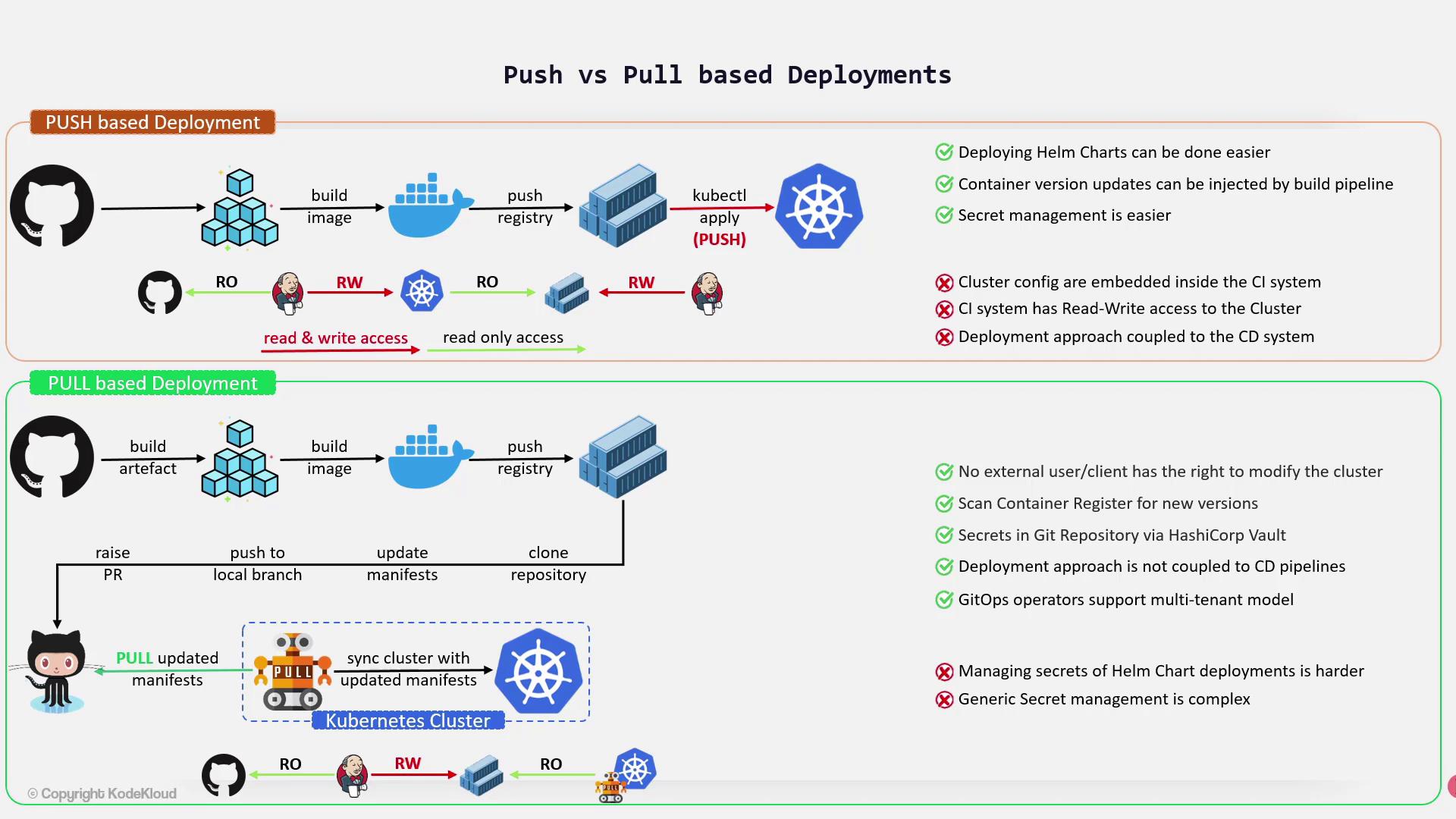
Pull-Based Deployment
Pull-based deployment, frequently associated with GitOps, employs an operator running within the Kubernetes cluster. This operator monitors for changes—either in a container registry for new images or in a Git repository for updated manifests—and then autonomously deploys those changes.Key Characteristics
- The CI/CD system only needs read-write access to the container registry, without requiring direct access to the Kubernetes cluster.
- Deployments are executed internally from within the cluster, enhancing security by minimizing external access.
- GitOps operators are particularly supportive of multi-tenant environments, allowing teams to manage multiple repositories and namespaces. For example, different teams can maintain separate Git repositories and corresponding namespaces for their deployments.
- Secrets can be securely managed by encrypting them using tools like HashiCorp Vault or Bitnami Sealed Secrets. These encrypted secrets are stored in Git or decrypted during the deployment process.
- GitOps operators can monitor container registries for newer image versions and automatically trigger deployments of the latest images.
While GitOps encourages declarative management—including secrets—in Git, the process often requires additional tools and steps (e.g., encryption and decryption) to ensure security, especially with Helm chart deployments.
Challenges
- Managing secrets and configurations can be more complex compared to the push-based model. Although GitOps principles promote a declarative approach, handling encrypted credentials adds an extra layer of complexity.
Visual Comparison
Summary
| Deployment Strategy | Pros | Cons |
|---|---|---|
| Push-Based | - Direct integration with CI/CD pipelines - Flexible deployment configurations using various tools and plugins | - Requires CI system to have cluster credentials - Tightly coupled to specific CI systems, making migrations challenging |
| Pull-Based (GitOps) | - Enhanced security by limiting external access - Supports multi-tenant environments and automated image updates | - More complex secret management - Additional tools required for encrypting and decrypting configurations |