The Snapshot Agent requires Consul Enterprise. If you’re on OSS Consul, implement external scripting for snapshots.
Key Features

- Custom intervals: e.g., hourly, six-hourly, daily
- Retention policies: automatically purge old snapshots
- Storage backends: local filesystem, S3-compatible (AWS S3, MinIO), Azure Blob, Google Cloud Storage
Configure
snapshot.interval (e.g., 24h) and snapshot.retain (e.g., 48) to control scheduling and purge behavior.Supported Storage Backends
By default, manual snapshots are written locally. The Snapshot Agent lets you offload backups to resilient, off-node stores:| Backend | Use Case | Example Setting |
|---|---|---|
| S3-Compatible | AWS S3, MinIO, DigitalOcean Spaces | aws_storage.s3_bucket = "consul-snapshots" |
| Azure Blob Storage | Enterprise-grade Blob management | azure_storage.account = "myaccount" |
| Google Cloud Storage | GCS buckets for global redundancy | gcs_storage.bucket = "consul-gcs-snapshots" |
| Local Filesystem | On-node backups (default for CLI/API) | filesystem.path = "/var/consul/snapshots" |
Benefits

- Automated snapshots on a defined schedule
- High availability via agent-level leader election
- Automatic failover: a new leader takes over if the current one fails
- Consistent backups: only one snapshot per interval cluster-wide
- Service registration & health checks for monitoring leader status
Configuration
Setup involves two files: a JSON config for the agent and a systemd unit to manage the service.1. Snapshot Agent JSON
Save as/etc/snapshot.d/snapshot.json:
http_addr: Consul HTTP API addresstoken: ACL token withsnapshotscopedatacenter: Optional target datacentersnapshot.interval: Interval between snapshotssnapshot.retain: Number of snapshots to keepsnapshot.deregister_after: Deregister unhealthy agent after this duration- Storage blocks: one of
aws_storage,azure_storage,gcs_storage, orfilesystem
2. systemd Unit
Create/etc/systemd/system/consul-snapshot.service:
Process Overview
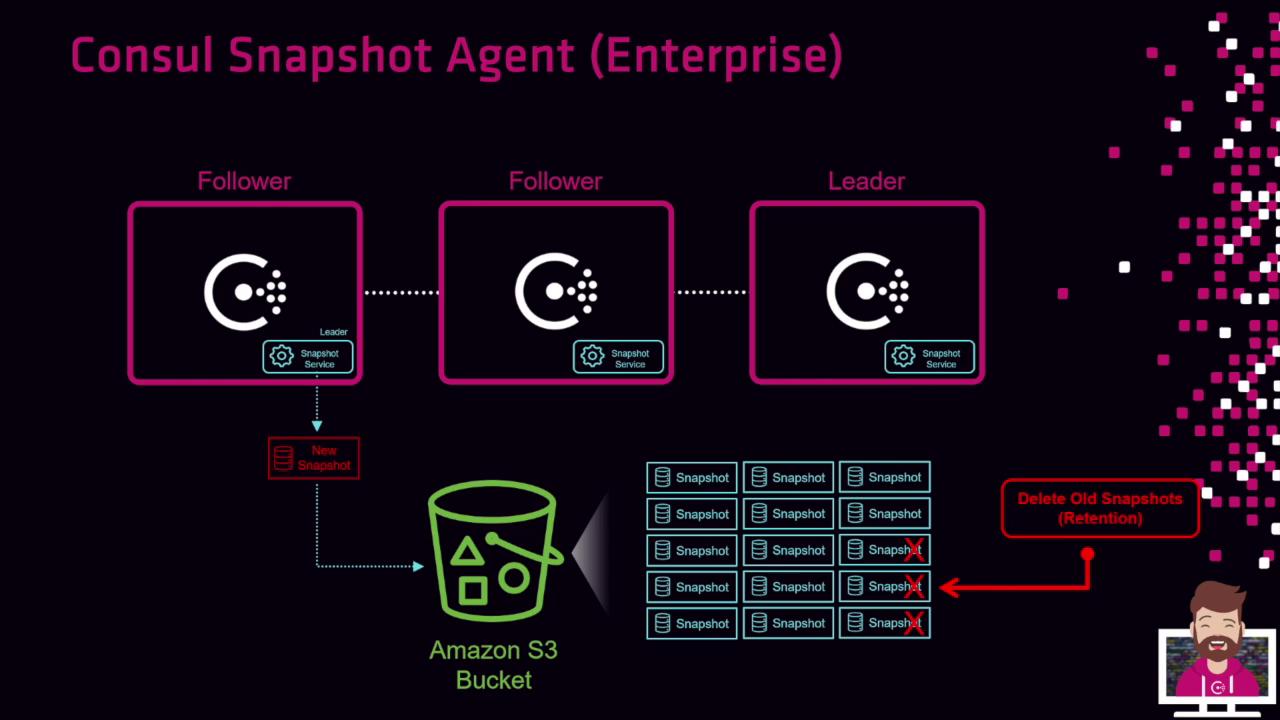
- All nodes run the Snapshot Agent.
- Agents hold a leader election each interval.
- The leader captures the snapshot and uploads it to storage (e.g., S3).
- The retention policy deletes older snapshots beyond the configured limit.