Encryption Challenges in the Enterprise
Consider a typical three-tier application flow: web tier → app tier → database tier. When data (for example, name, credit card number, expiration date, date of birth) is stored in clear text, any compromise of a tier exposes sensitive information.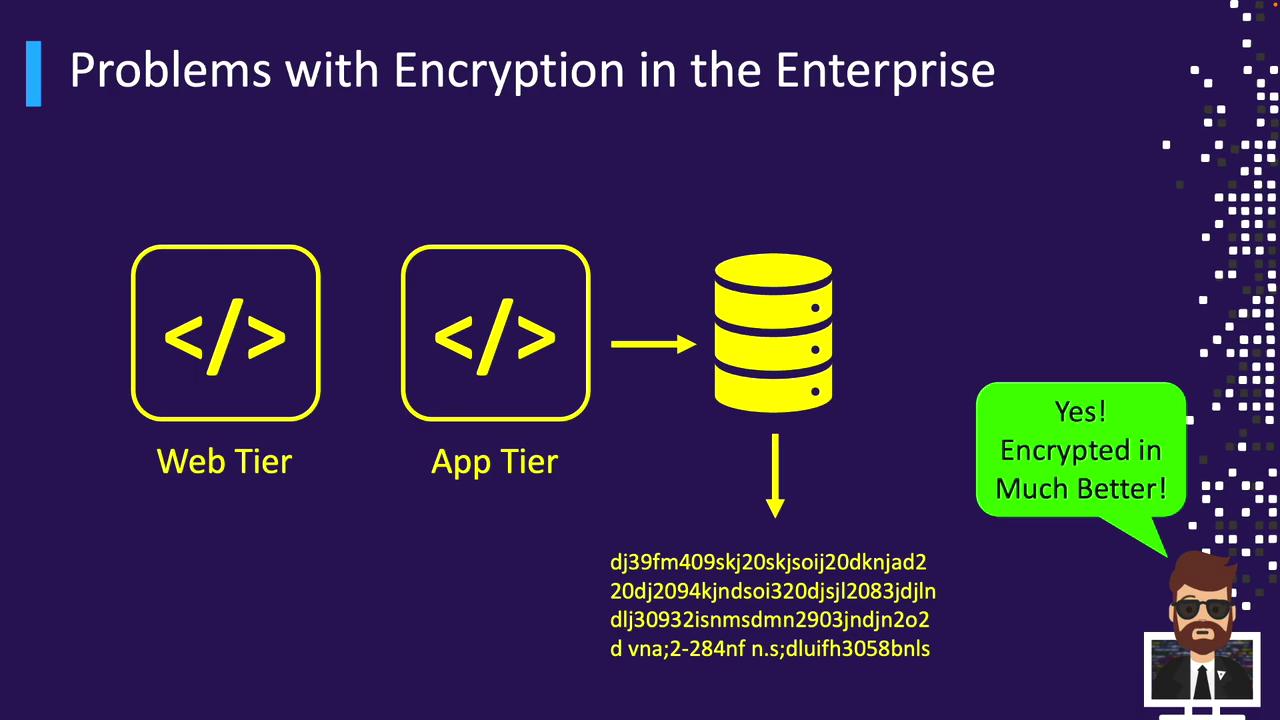
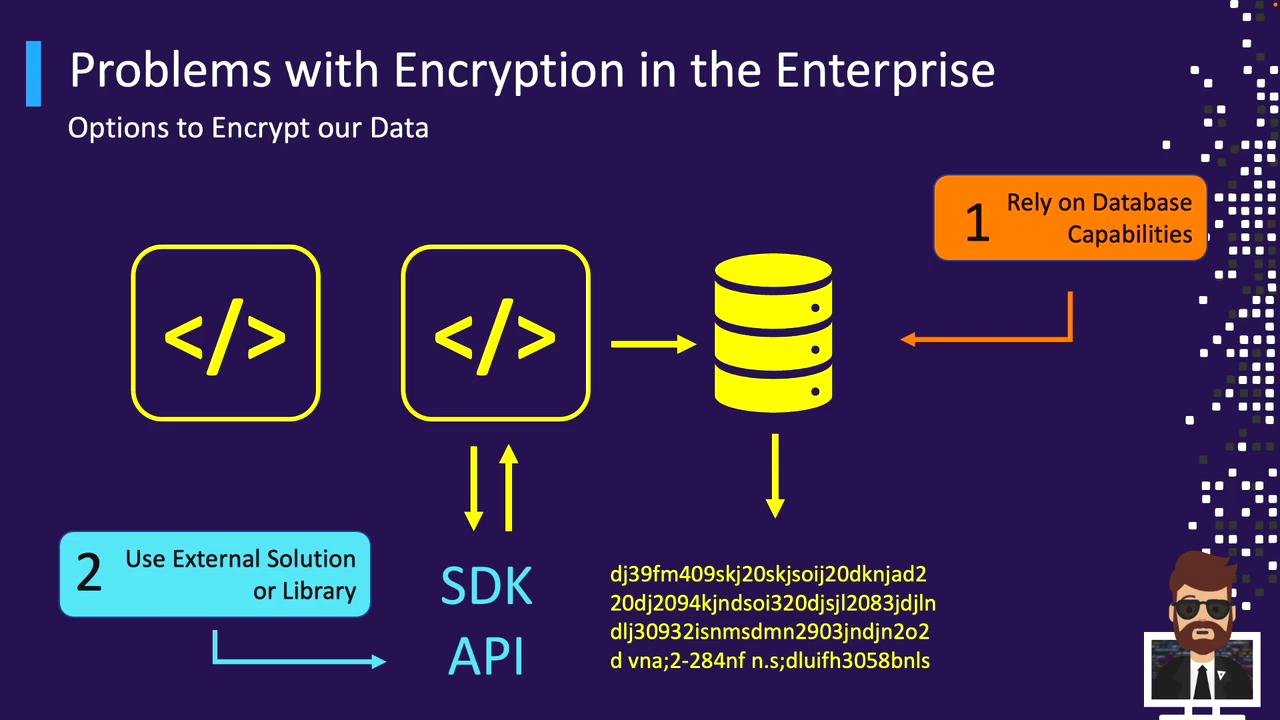
- Use the database’s built-in encryption.
- Integrate an external crypto library or SDK in the app tier.
Limitations of Database Encryption
High-performance stores like Cassandra often lack advanced encryption capabilities, forcing teams to choose legacy platforms (e.g., MSSQL) solely for encryption support.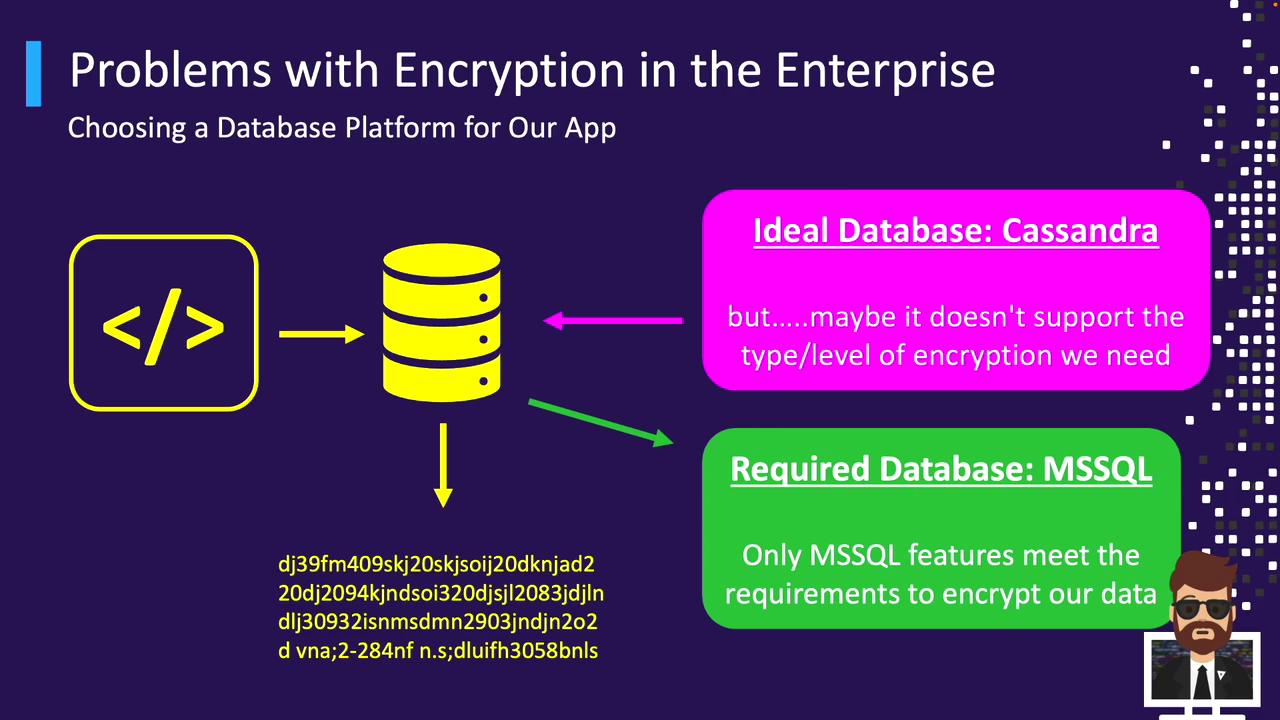
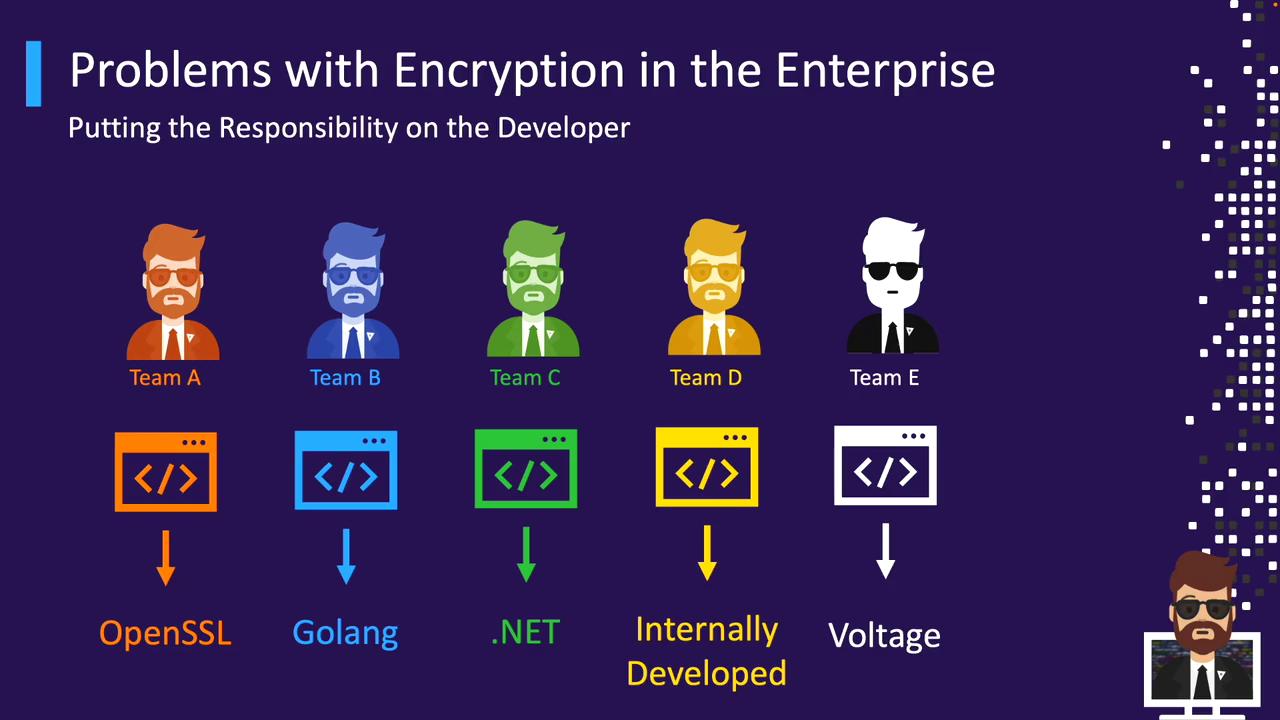
Drawbacks of Custom Libraries
When each team picks its own solution—OpenSSL, Go’s crypto, .NET libraries, in-house code, or tools like Voltage—you end up with:- Multiple custom implementations
- Inconsistent security practices
- Fragmented audit and compliance
Decentralized encryption makes it hard to enforce policies, rotate keys, and audit usage.
Introducing the Transit Secrets Engine
Vault’s Transit Secrets Engine provides a centralized encryption service. Applications send plaintext to Vault, request encryption, and store the returned ciphertext wherever they choose. Vault never persists the encrypted data.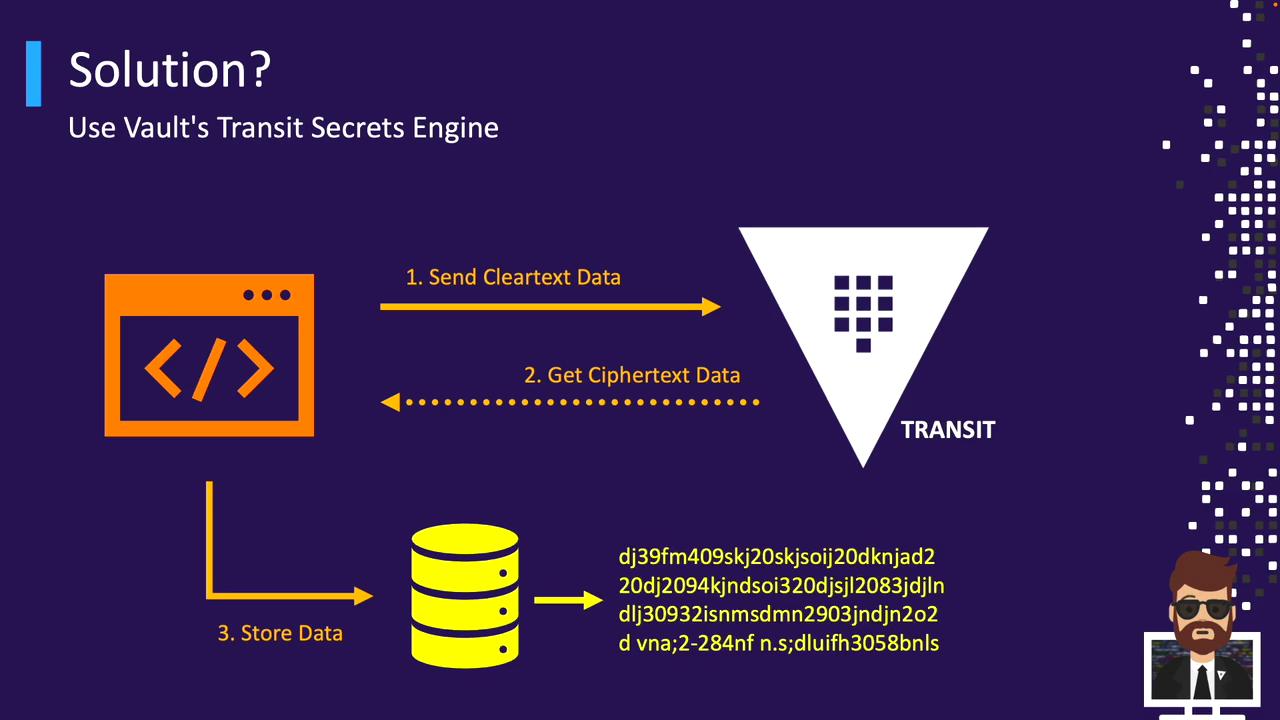
How It Works
Vault exposes simple API endpoints under/transit:
- Authenticate and obtain a token scoped to specific keys.
- Encrypt: send Base64-encoded plaintext to
/transit/encrypt/<key>→ receive ciphertext. - Store ciphertext in any datastore (database, object store, etc.).
- Decrypt: send ciphertext to
/transit/decrypt/<key>→ receive Base64 plaintext.

Vault’s Transit engine does not store ciphertext—it simply encrypts or decrypts and returns the result.
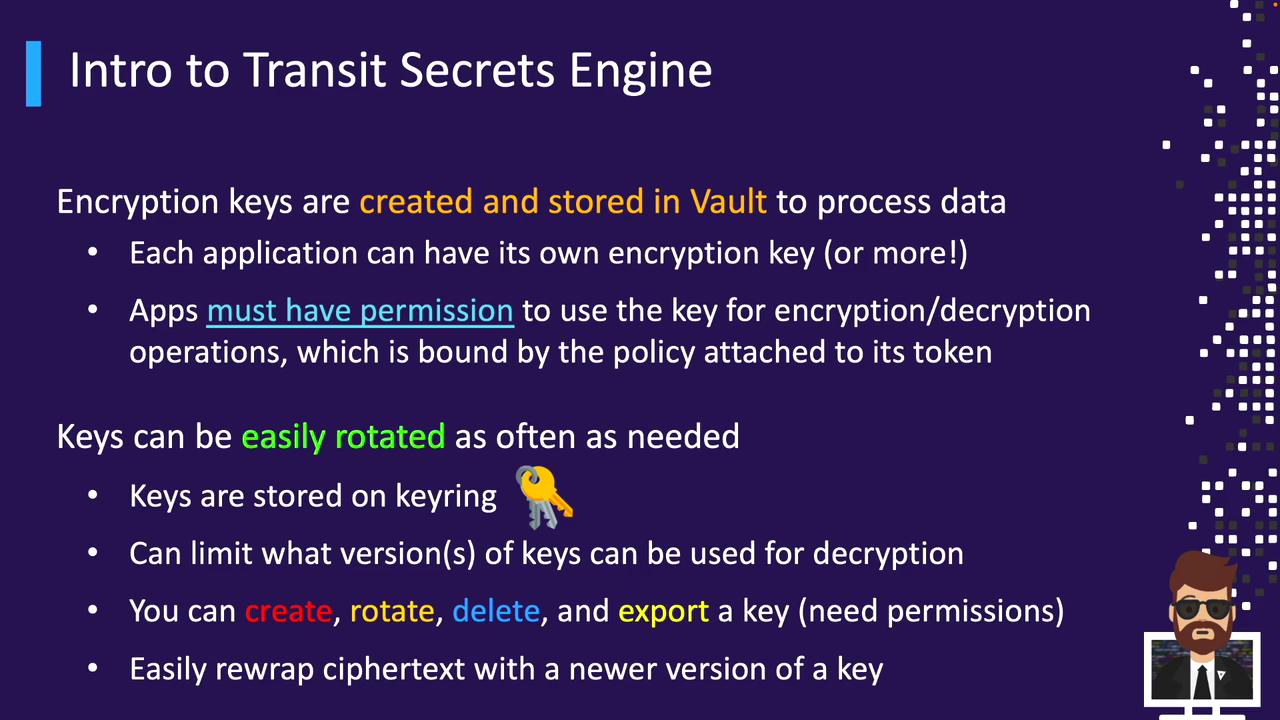
Key Management and Rotation
Vault manages your keys and their versions:- Secure storage: Keys live only in Vault.
- Versioning: Rotate keys by adding new versions to the key ring.
- Backward compatibility: Old versions remain available to decrypt legacy data.
- Access control: Enforce version-based decryption limits (e.g., only allow versions ≥ 3).
Re-wrapping Ciphertext
To upgrade ciphertext to the latest key version without exposing plaintext:- Call
/transit/rewrap/<key>with existing ciphertext. - Vault returns new ciphertext using the current key version.
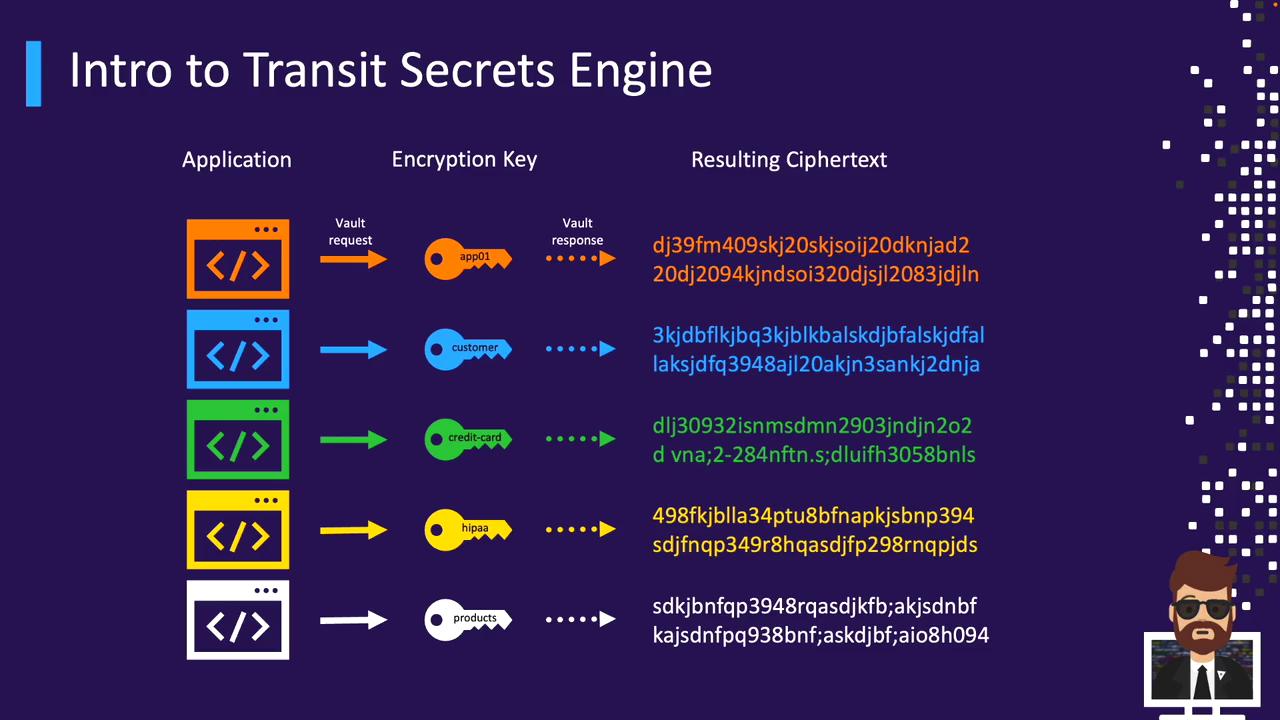
Application-Specific Keys
Assign each service its own encryption key. Your token policy can grant only the necessary operations:- A customer-facing service might have encrypt permissions only.
- A billing service could have both encrypt and decrypt permissions.
Supported Key Types
Vault supports a variety of key algorithms. By default, it usesaes256-gcm96. Choose according to your security requirements:
| Key Type | Use Case |
|---|---|
| aes256-gcm96 | Default: AES-GCM with 96-bit nonce |
| chacha20-poly1305 | ChaCha20-Poly1305 |
| ed25519 | EdDSA signatures |
| ecdsa-p256 | ECDSA P-256 signing |
| rsa-2048 | RSA encryption/signing with 2048-bit modulus |

Convergent Encryption Mode
Enable convergent encryption to ensure that encrypting the same plaintext with the same key always yields identical ciphertext. This feature is useful for searchable encryption but requires supported key types like AES-GCM or ChaCha20-Poly1305.Base64 Encoding Requirement
All plaintext sent to Transit must be Base64 encoded to support arbitrary binary data (PDFs, images, etc.). Remember, Base64 is reversible encoding, not encryption.For a hands-on experience, try the lab to enable Transit, create keys, and perform encrypt, decrypt, and rewrap operations.