Challenges with Static Secrets
Static secrets are credentials you create manually (e.g., a “password never expires” service account in Active Directory, an on-prem or RDS database user, or a long-lived vendor API key). While common, they introduce significant security and operational drawbacks:| Issue | Impact |
|---|---|
| Expiration | Often never expire by design, increasing exposure if compromised. |
| Secrecy & Sharing | Replicated across servers or shared among teams—effectively non-secret. |
| Accountability | Impossible to audit usage when multiple users share the same credential. |
| Always Valid | Valid 24/7, even when not needed—prime target for automated scanners and attackers. |
| Rare Rotation | Manual and infrequent rotation increases the window of vulnerability. |
| Long-Lived Secrets | Linger indefinitely and often go unrevoked when staff or applications retire. |

Using static credentials at scale without strict rotation policies can lead to compliance violations and increased breach risk.
Benefits of Dynamic Secrets
Dynamic secrets are generated on-demand by Vault and tied to a configurable lease (TTL). They solve the drawbacks of static credentials:- On-Demand Generation
Secrets only exist when needed (e.g., a Terraform run requests API keys at execution time). - Configurable Leases
Each secret has a TTL. Once expired, Vault revokes the credential at the source (e.g., drops the database user). - Defined Validity
Set initial and maximum TTLs to enforce strict lifespan limits. - Automatic Revocation
Vault automatically cleans up unused or orphaned credentials, preventing “technical debt.” - Fine-Grained Renewal
Control which secrets can be renewed and for how long—supporting both short-lived jobs and long-running services.
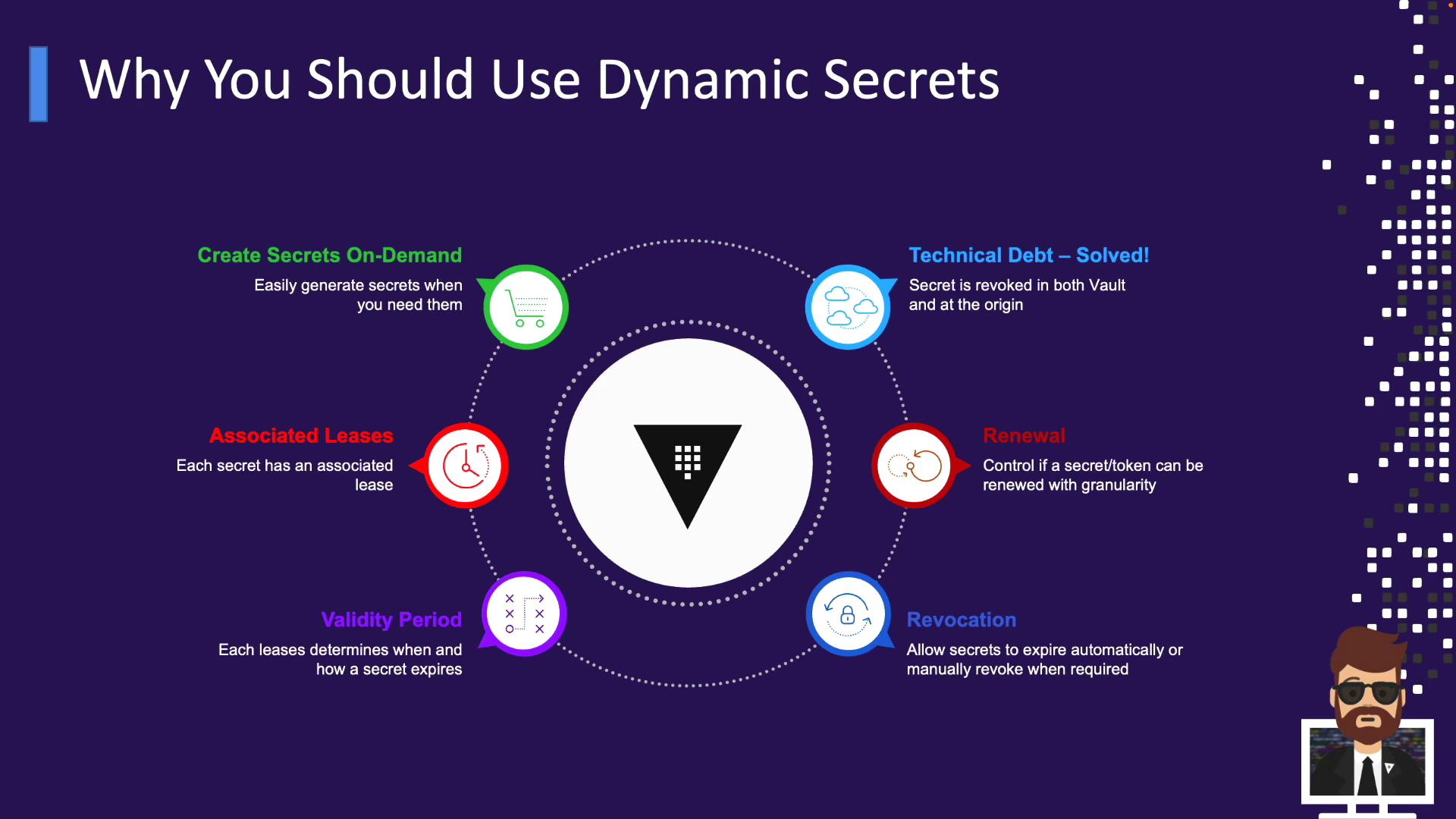
Dynamic secrets enhance security posture by minimizing manual intervention and reducing the lifetime of exposed credentials.
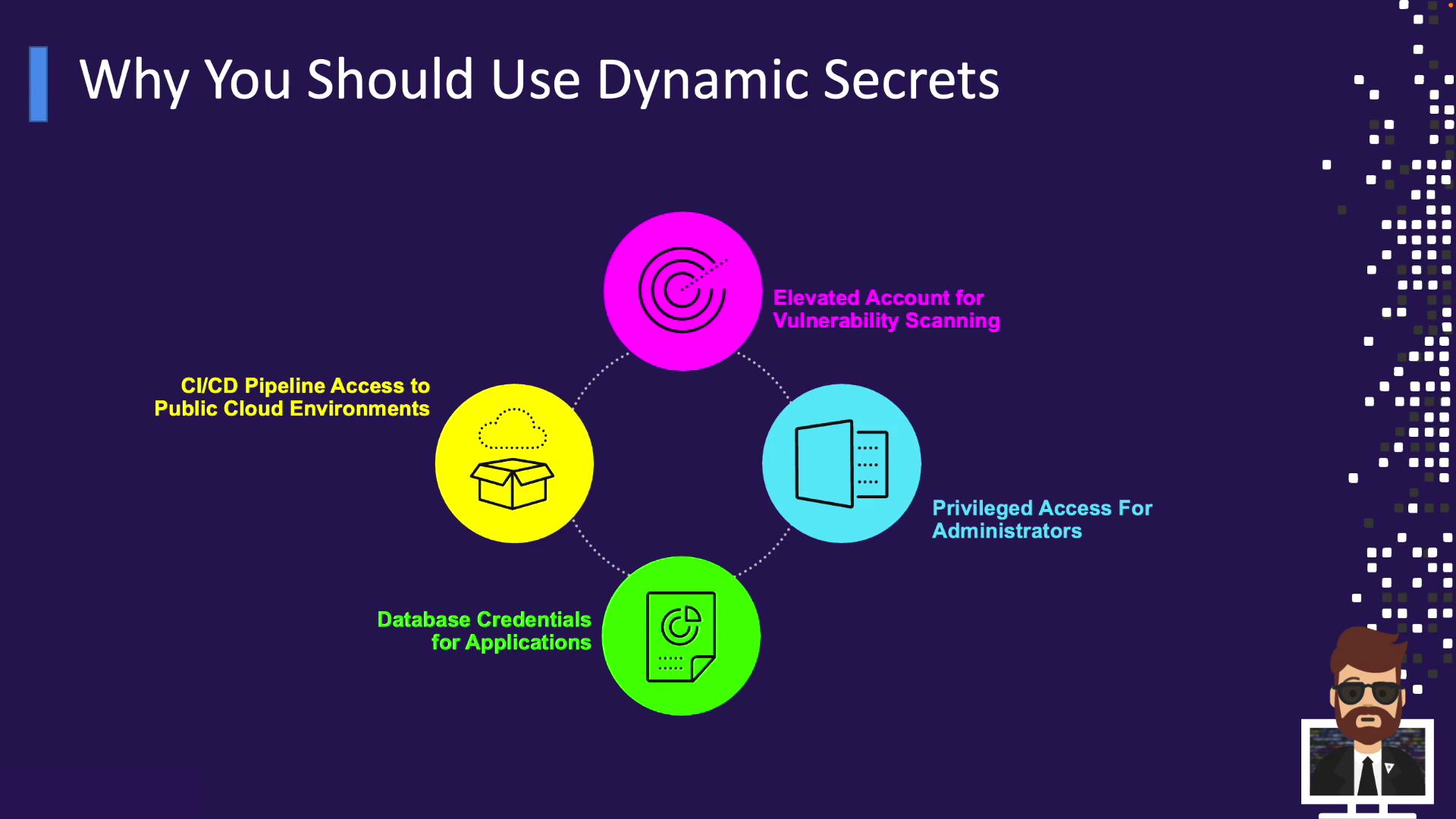
Dynamic Secrets Use Cases
Vault’s dynamic secrets support a wide range of production workflows:- CI/CD Pipelines
Short-lived credentials for provisioning AWS, Azure, GCP, or on-prem resources. - Vulnerability Scanning
Temporary elevated accounts for tools like Rapid7 or Nessus, revoked post-scan. - Administrative Access
Time-bound privileged accounts for ops teams, auto-rotated and revoked daily. - Application Database Access
Apps fetch dynamic DB credentials at startup and release them when done.
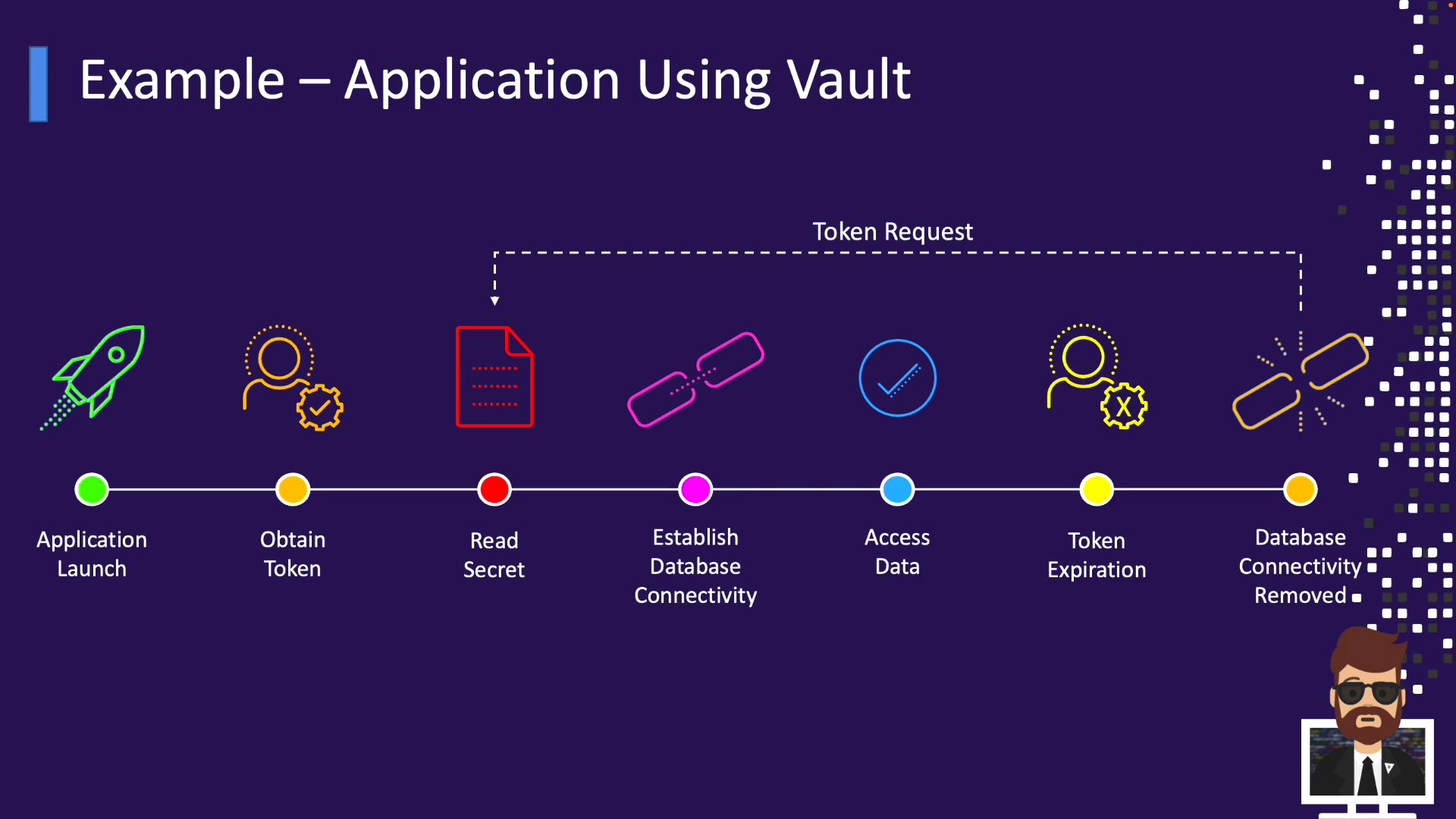
Example: Application Integration with Vault
A typical flow for an application retrieving secrets at startup:- Application launches.
- It authenticates to Vault (AppRole, Kubernetes, AWS, Azure, or GCP auth methods).
- Vault issues a short-lived token.
- The app uses the token to read required secrets (static or dynamic).
- It connects to the database or service.
- Token or lease expires—access is revoked automatically.
- Optionally, the application renews the lease or requests a new token.
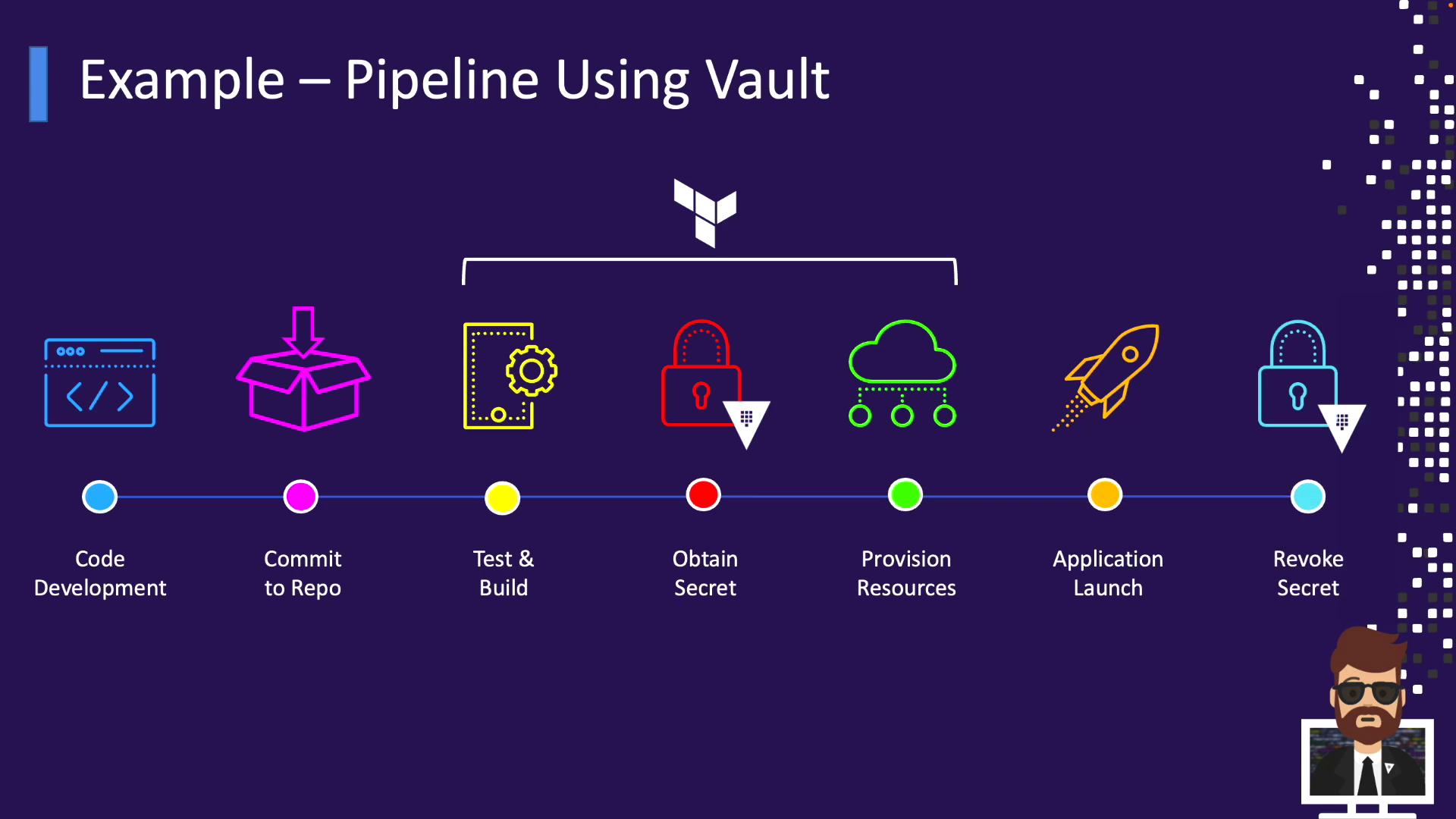
Example: CI/CD Pipeline with Vault
In a CI/CD workflow, Vault provides secure, temporary credentials for provisioning:- Developer pushes code to the repository.
- Automated build and tests run.
- Pipeline authenticates to Vault and obtains a dynamic secret.
- Terraform (or similar) uses this secret to create infrastructure.
- Applications are deployed.
- Pipeline revokes the secret at job completion.
By shifting from static credentials to Vault’s dynamic secrets, you automate secret lifecycle management, tighten access controls, and boost overall security.