HashiCorp Certified: Vault Associate Certification
Learning the Vault Architecture
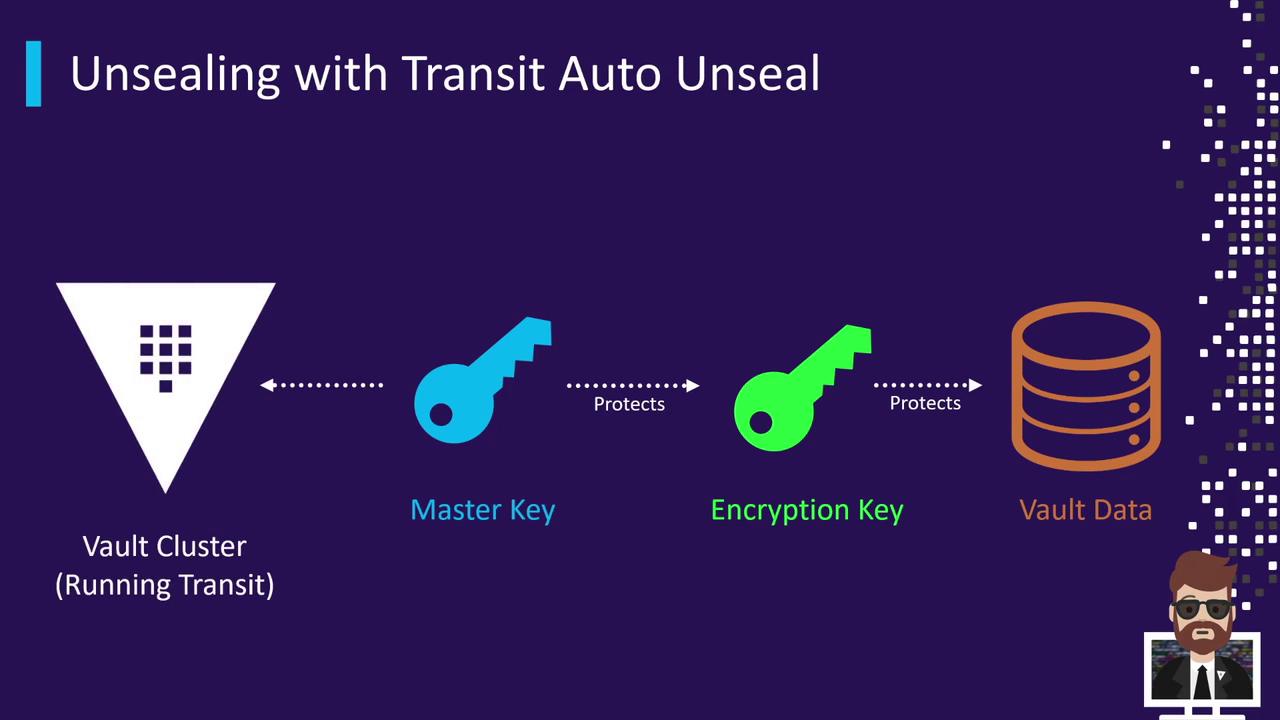
Unsealing with Transit Auto Unseal
Vault’s Transit Auto Unseal method offloads unseal operations to a dedicated Transit Secrets Engine running in a separate Vault cluster. This approach protects the master key and enables automatic unsealing of dependent clusters on startup.
Architecture Overview
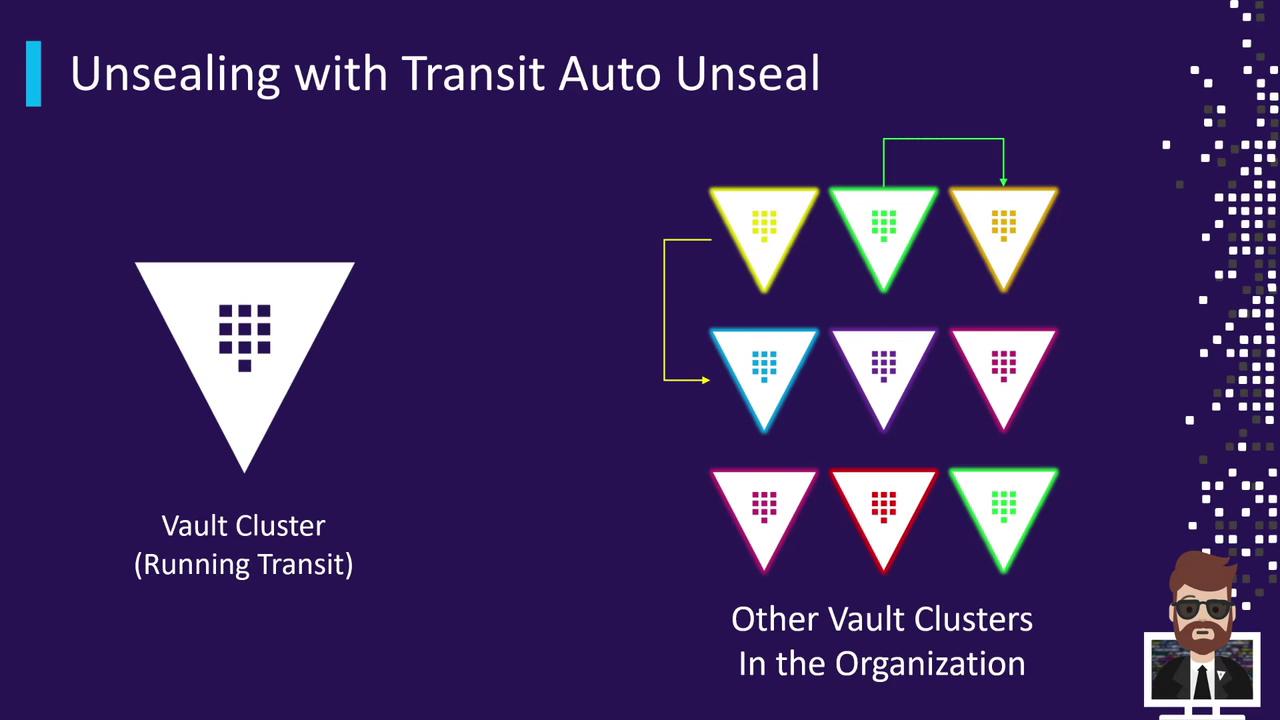
One Vault cluster (the “unsealer”) runs the Transit Secrets Engine and holds the encryption key for unsealing. Other clusters delegate their unseal operations to this central cluster:
Each dependent cluster connects to the Transit cluster using the configured key. You can chain dependencies (green unseals from orange, red from green, etc.), but the core pattern remains: one cluster auto-unseals from another.
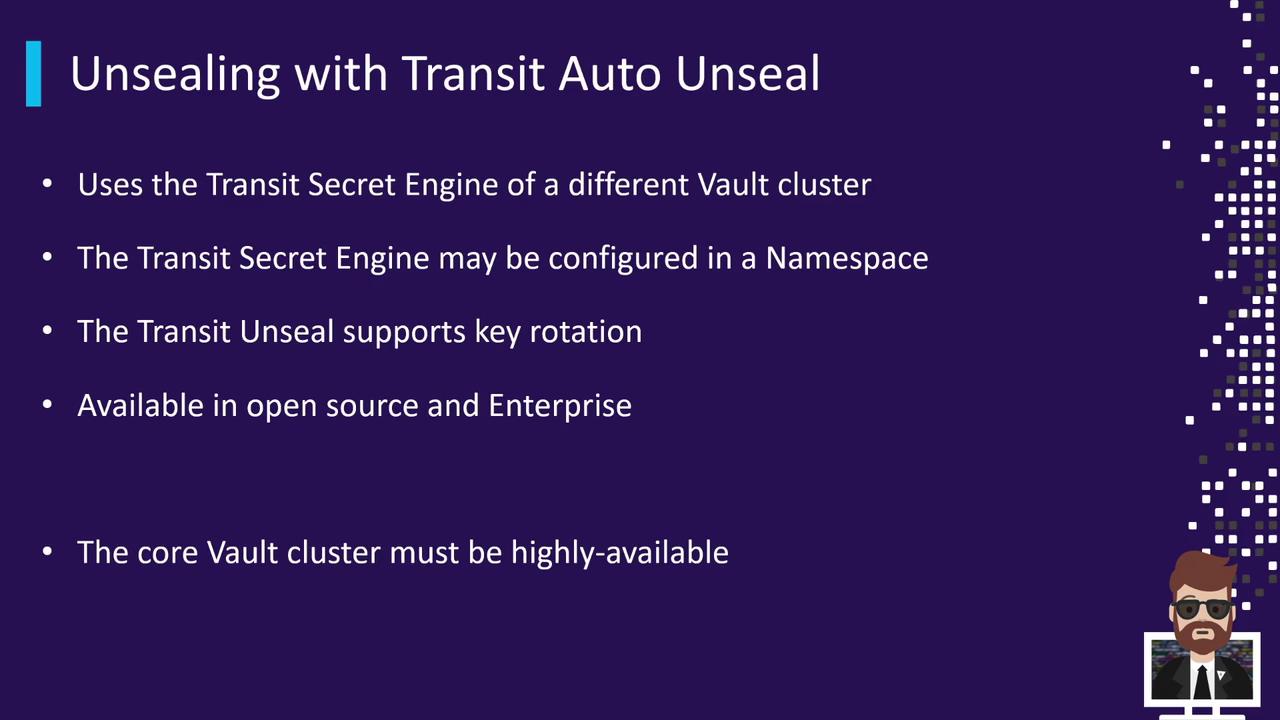
Key Features
| Feature | Description |
|---|---|
| Dedicated Transit Engine | Uses a separate Vault cluster’s Transit Secrets Engine for master key protection. |
| Key Rotation Support | Rotate the unseal key regularly to meet compliance and security requirements. |
| Open Source & Enterprise Ready | Available in Vault OSS and Enterprise editions without additional plugins. |
| High Availability Requirement | The Transit cluster must be HA with a resilient backend; downtime halts auto-unseal actions. |
Warning
If the central Transit cluster becomes unavailable, all dependent Vault clusters will fail to unseal. Ensure your Transit cluster is highly available and monitored.
Configuration
To enable Transit Auto Unseal, add a seal stanza to your Vault configuration file:
seal "transit" {
address = "https://vault.example.com:8200"
token = "s.Qf1s5zigZ4OX6akYjQXJC1jY"
disable_renewal = "false"
# Key configuration
key_name = "transit_key_name"
mount_path = "transit/"
namespace = "ns1/"
# TLS Configuration
tls_ca_cert = "/etc/vault/ca_cert.pem"
tls_client_cert = "/etc/vault/client_cert.pem"
tls_client_key = "/etc/vault/client_key.pem"
tls_server_name = "vault"
tls_skip_verify = "false"
}
addressandtokenpoint to the central Vault cluster running Transit.key_name,mount_path, andnamespaceidentify which key to use.- TLS settings ensure secure communication between clusters.
Links and References
Watch Video
Watch video content