HashiCorp Certified: Vault Associate Certification
Vault Replication
Demo Disaster Replication Configuration
In this guide, you’ll learn how to enable and configure performance replication in Vault Enterprise. Performance replication lets you distribute Vault policies, secrets engines, authentication methods, and audit configurations across multiple clusters for active-active read scalability, while routing write operations to a single primary.
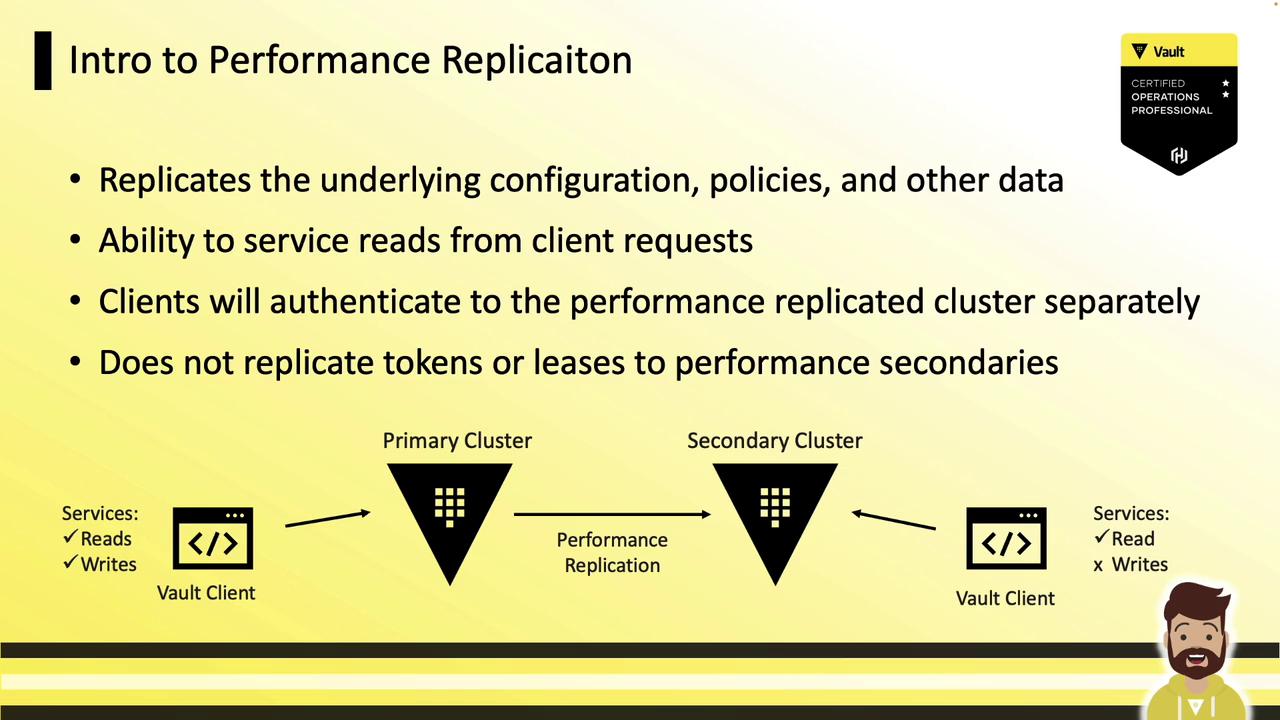
Key Concepts
- Active-Active Workloads: Read operations (authentication, secret reads, dynamic secret generation) are served locally on each replica.
- Centralized Writes: All write requests (policy changes, configuration updates) are forwarded to the primary cluster.
- Independent Authentication: Tokens and leases created on a performance secondary are local and are not replicated from the primary. Clients must re-authenticate on each cluster.
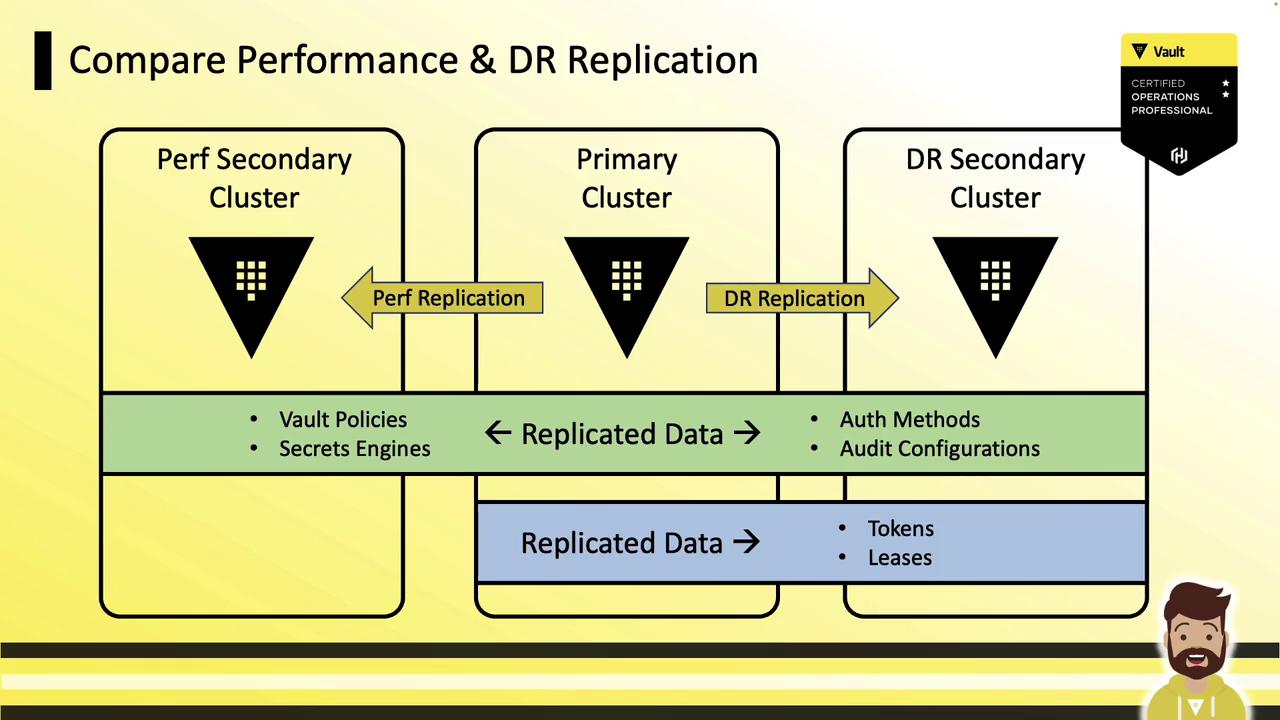
Performance vs. Disaster Recovery (DR) Replication
| Feature | Performance Replication | DR Replication |
|---|---|---|
| Policies & Config | ✓ | ✗ |
| Secrets Engines & Auth | ✓ | ✗ |
| Audit Configurations | ✓ | ✗ |
| Tokens & Leases | ✗ | ✓ |
| Use Case | Active-active, low-latency reads | Failover and disaster recovery |
| Write Path | Forwarded to primary | Forwarded to primary |
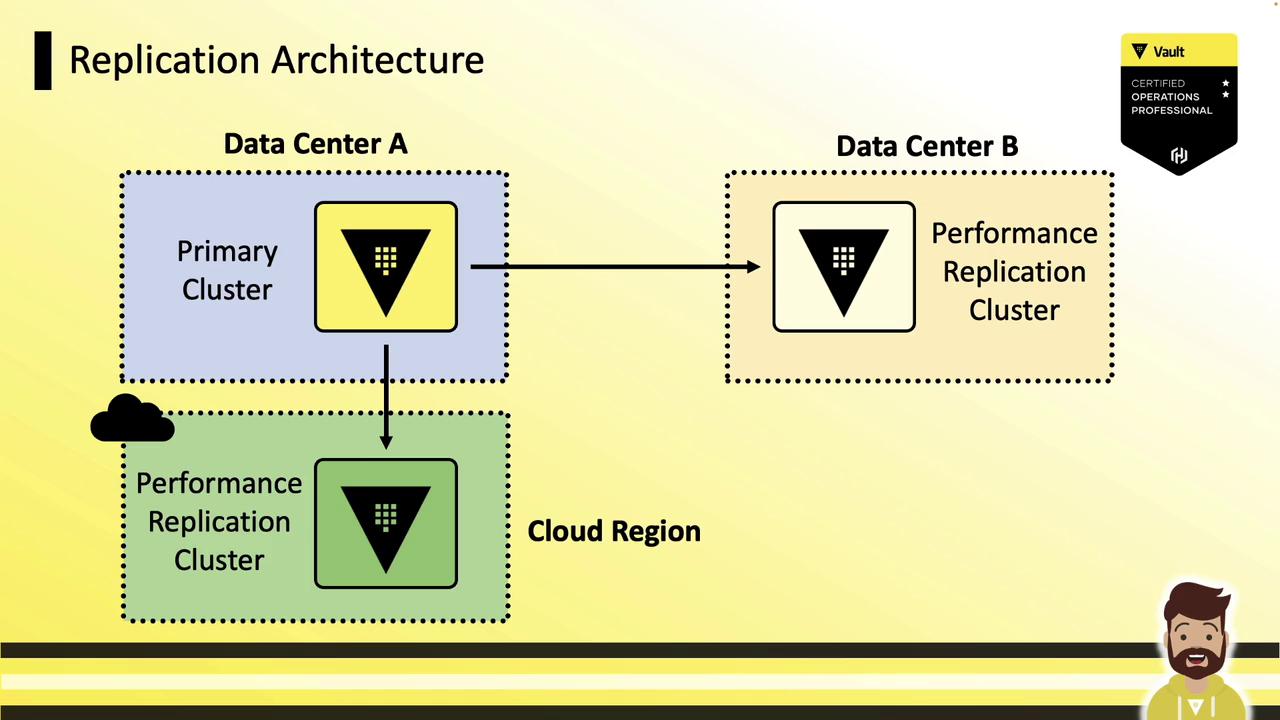
Example Architecture: Data Centers & Cloud Regions
Multi–Data Center Deployment
A primary cluster in Data Center A replicates to performance secondaries in Data Center B and a cloud region. Local applications read and authenticate against their nearest replica, while writes go to the primary.
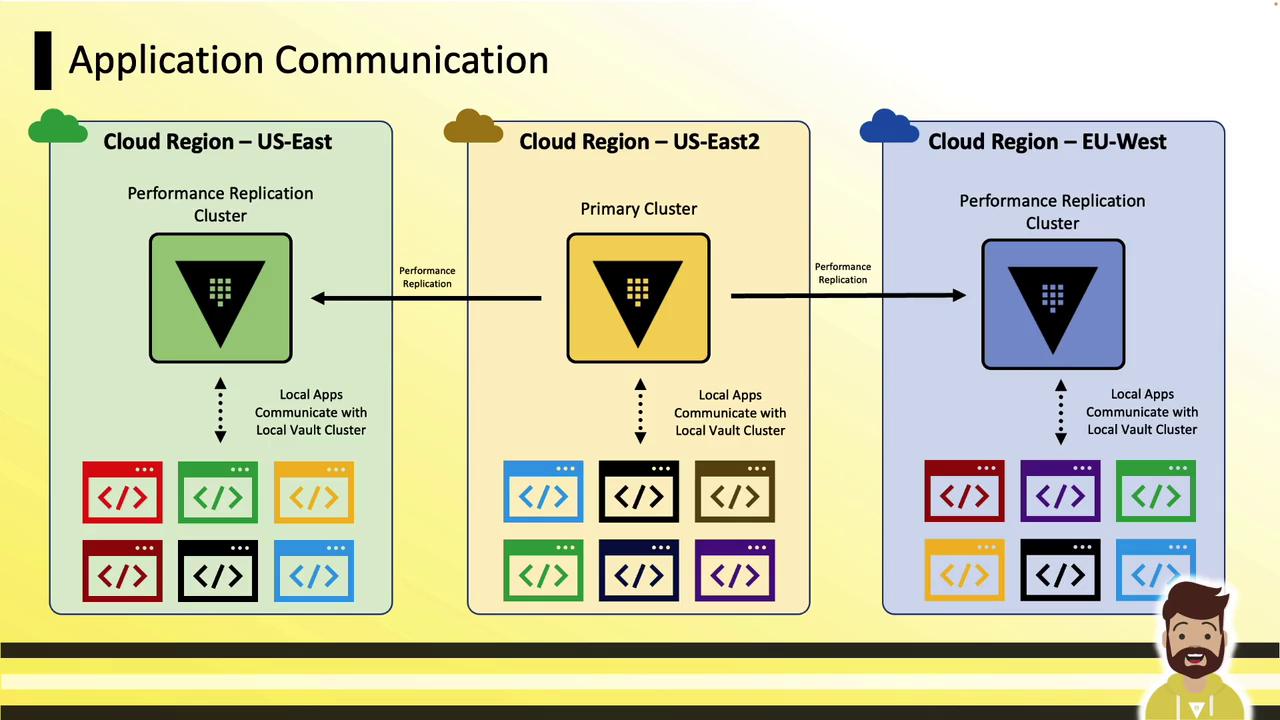
Global Cloud Deployment
In a cloud setup, the primary (US-East2) replicates to secondaries in US-East and EU-West. Applications in each region authenticate to their local replica for reads; writes are sent back to the primary and propagated.
How Performance Replication Works
Active-Active Authentication
Each performance replica handles logins locally. Tokens and leases exist only on the cluster where they were issued.Local Dynamic Secrets
Replicas generate dynamic credentials (e.g., database passwords, AWS keys) without contacting the primary:

External Service Interactions
Connections to AWS, databases, and other external services occur directly from each replica: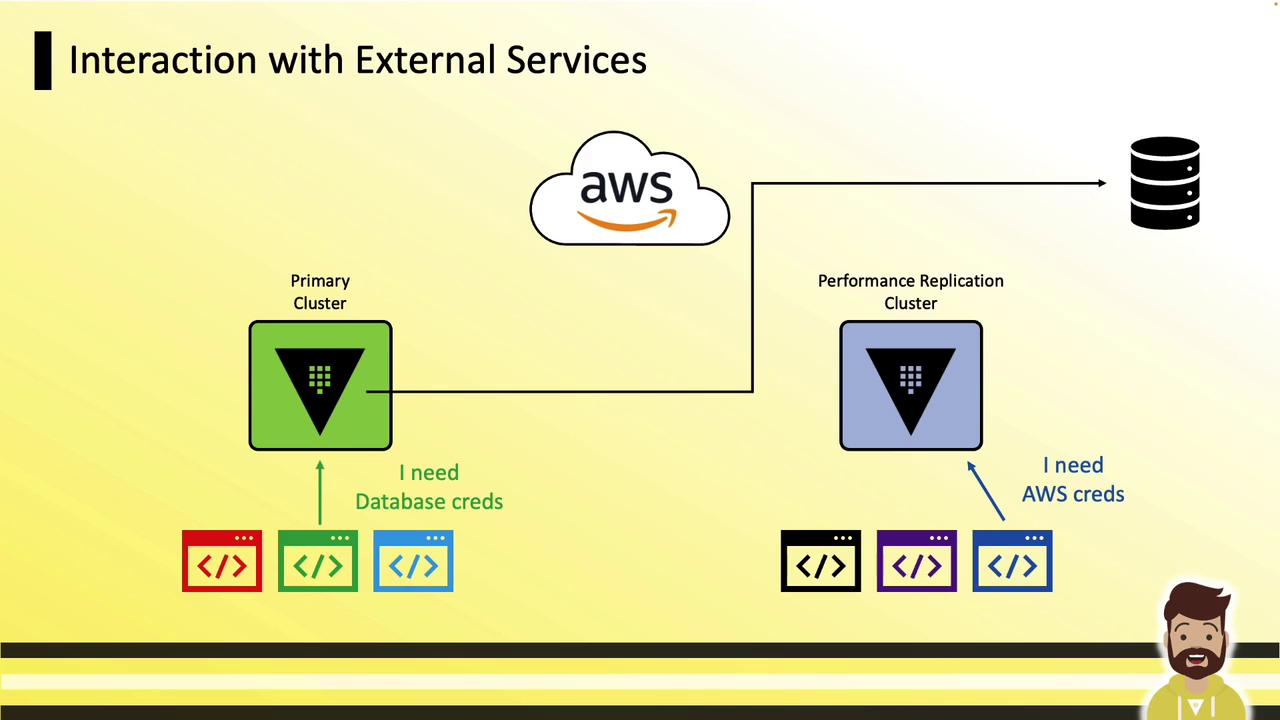
Setup Process
Follow these four steps to configure performance replication:
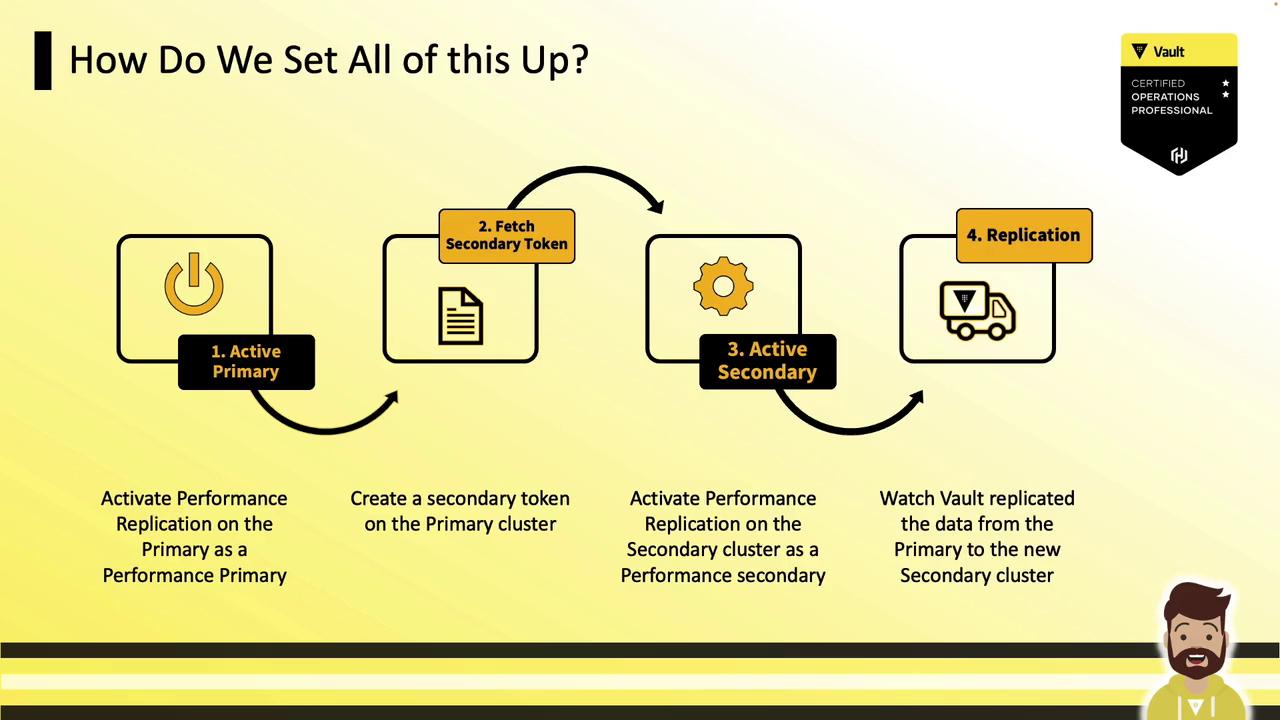
- Enable performance replication on the primary.
- Generate a secondary token.
- Enable the secondary using the token.
- Monitor the replication status.
CLI Commands
# 1. Enable performance replication on the primary
vault write -f sys/replication/performance/primary/enable
# 2. Generate a secondary token on the primary
vault write sys/replication/performance/primary/secondary-token id="secondary-id"
# 3. Activate the performance secondary with the token
vault write sys/replication/performance/secondary/enable token="secondary-token"
Warning
Enabling a secondary will purge its local data (including unseal and recovery keys) and sync entirely from the primary.
Monitoring Replication
# View overall replication status
vault read --format=json sys/replication/status
# View performance replication status
vault read --format=json sys/replication/performance/status
# View DR replication status
vault read --format=json sys/replication/dr/status
After setup, verify that changes—such as enabling a new auth method—on the primary cluster appear on each performance secondary.
References
Watch Video
Watch video content