Istio Service Mesh
Security
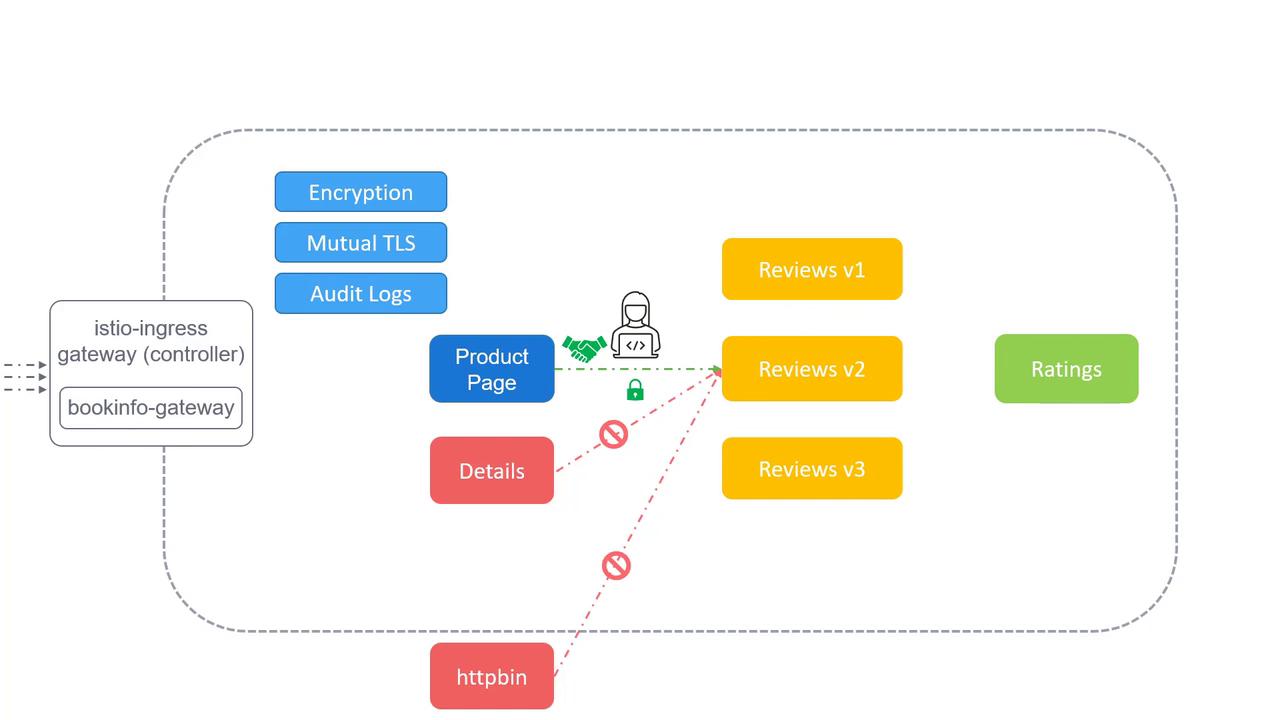
Security in Istio
This article offers a comprehensive overview of security in Istio, a cornerstone for protecting modern microservices architectures. In distributed systems, ensuring secure communication between services is not just important—it’s essential.
Securing Microservices Communication
Microservices come with unique security challenges. When one service communicates with another, there is a risk that an attacker could intercept or alter the traffic (commonly known as a man-in-the-middle attack). To prevent such threats, encrypting the communication channels between services is paramount.
Equally important is implementing strict access control policies. For example, you might restrict access so that only the product page service can interact with the review service, while denying access to other services like the details service. Istio addresses these needs by providing mutual TLS (mTLS) for robust encryption and fine-grained access control policies to ensure that only authorized services can communicate with each other.
Audit Logging with Istio
Istio supports comprehensive audit logging, enabling you to track who performed specific actions and when they occurred. This feature is vital for maintaining transparency and security compliance in your environment.
What’s Next
In the upcoming sections, we will explore each of these security aspects in detail. You will learn how to configure mutual TLS for secure communications, set up precise access control policies, and leverage audit logging for enhanced security monitoring.
By following these guidelines, you can harness the full capabilities of Istio to ensure your microservices architecture remains secure and resilient against modern threats.
Watch Video
Watch video content