Jenkins
Securing Jenkins
Access Control for Builds
Securing your build process is essential, especially when deploying your builds across multiple virtual machines. In previous sections, we emphasized agent security to ensure that only authorized operations are executed during builds, thereby maintaining the overall integrity and security of your environment.
To enhance security within your Jenkins setup, consider installing specialized plugins. Follow these steps:
- Navigate to Manage Jenkins > Manage Plugins.
- Search for "Pipeline" to explore a variety of options that can reinforce your pipelines.
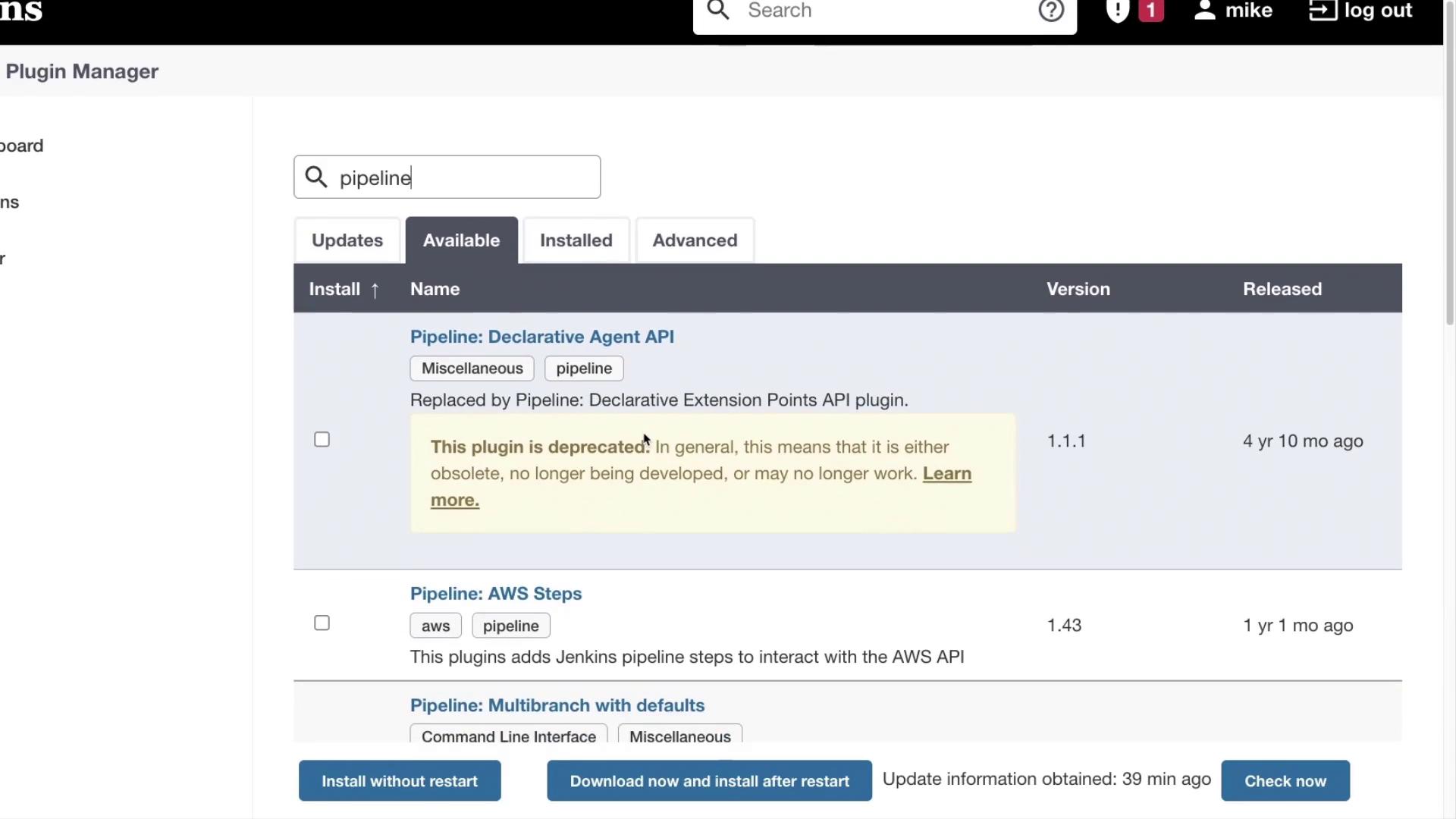
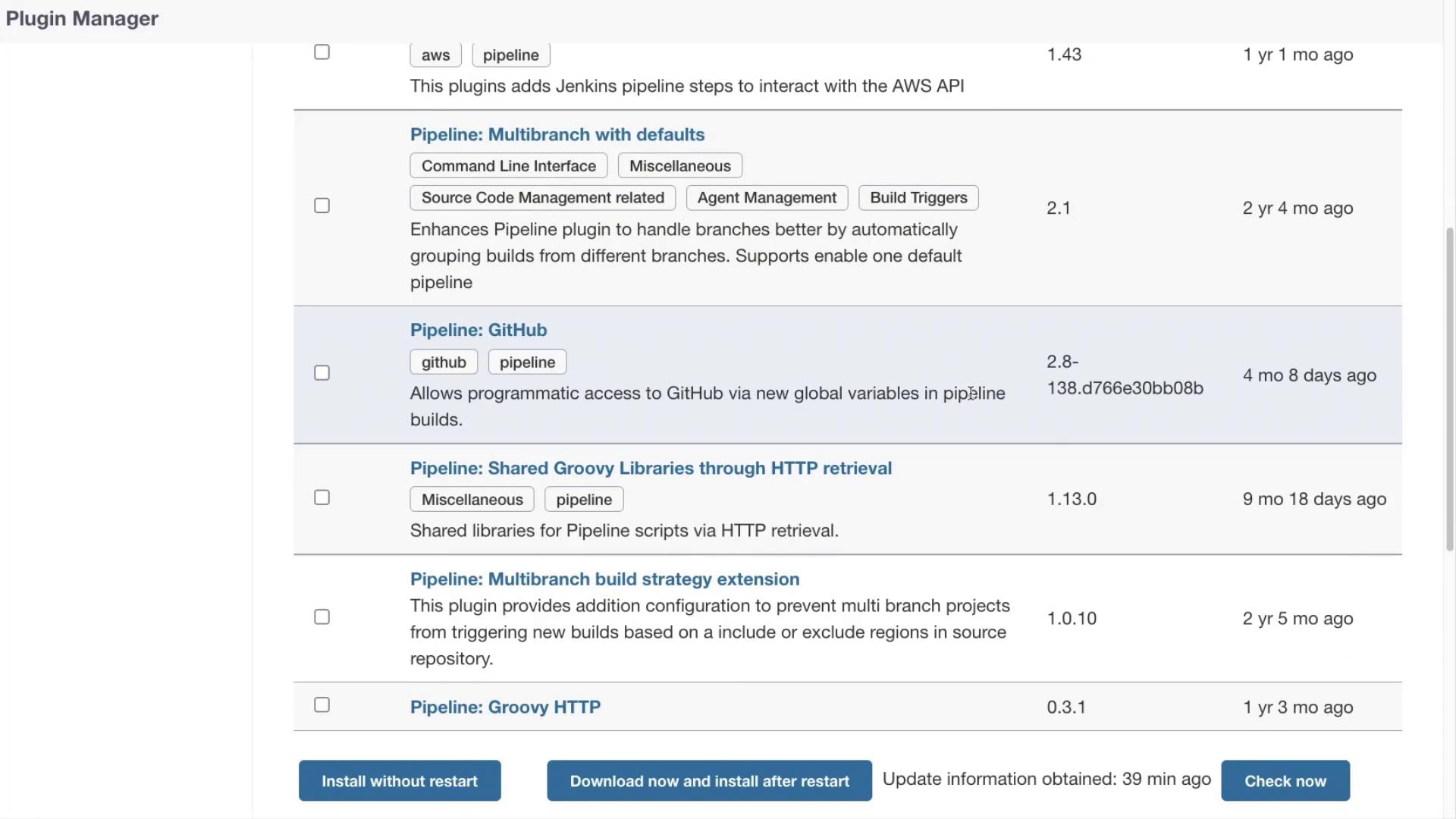
Some of the notable plugins include Declarative Pipeline API, AWS Steps (enabling interaction with the AWS API), Pipeline for GitHub, and several multi-branch build strategies. These plugins are designed to address various requirements, providing you with versatile tools to tailor your build process.
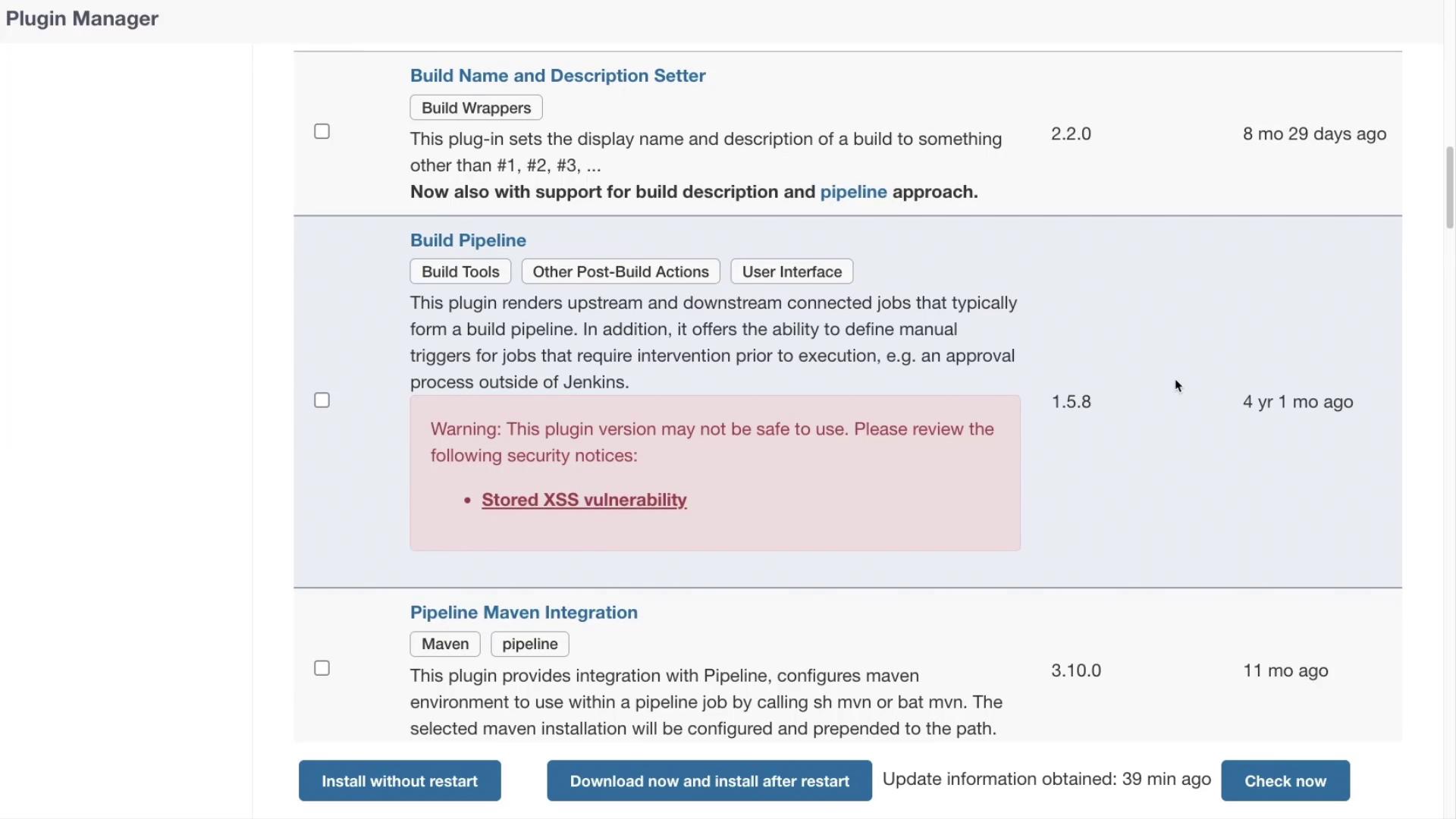
For build-specific stages, the "Build Pipeline" plugin is often highlighted because it visually connects upstream and downstream jobs to create a complete build pipeline. However, it's important to be aware that this plugin has a known security vulnerability related to stored cross-site scripting (XSS).
Warning
The "Build Pipeline" plugin is vulnerable to stored XSS attacks. It is recommended to consider alternative solutions, such as SSH Pipeline Steps, to secure your build and agent processes.
By leveraging the wide range of available Pipeline plugins, you can establish robust access controls and fortify each stage of your build process. Empower your Jenkins environment with the right tools to enhance operational security throughout all build activities.
Now, let's apply these concepts through hands-on exercises.
Watch Video
Watch video content