Service Mesh
A Service Mesh is a dedicated infrastructure layer for handling service-to-service communication in microservices environments. Offloading networking logic to the mesh lets developers focus on application code, while the mesh provides:- Traffic Management
- Security
- Observability
Service Mesh isn’t part of Company X’s current stack, but understanding it is crucial for complex microservices landscapes.

Key Benefits
| Benefit | Description |
|---|---|
| Traffic Management | Canary releases, A/B testing, blue/green deployments |
| Security | mTLS encryption, automatic certificate rotation, policy enforcement |
| Observability | Metrics, logs, distributed tracing for deep insights |
Popular Providers
| Provider | Description | Website |
|---|---|---|
| Istio | Rich feature set, Envoy integration for complex environments | istio.io |
| Linkerd | Lightweight, high-performance, minimal operational overhead | linkerd.io |
| Cilium | eBPF-powered mesh combining networking and security | cilium.io |

Core Architecture
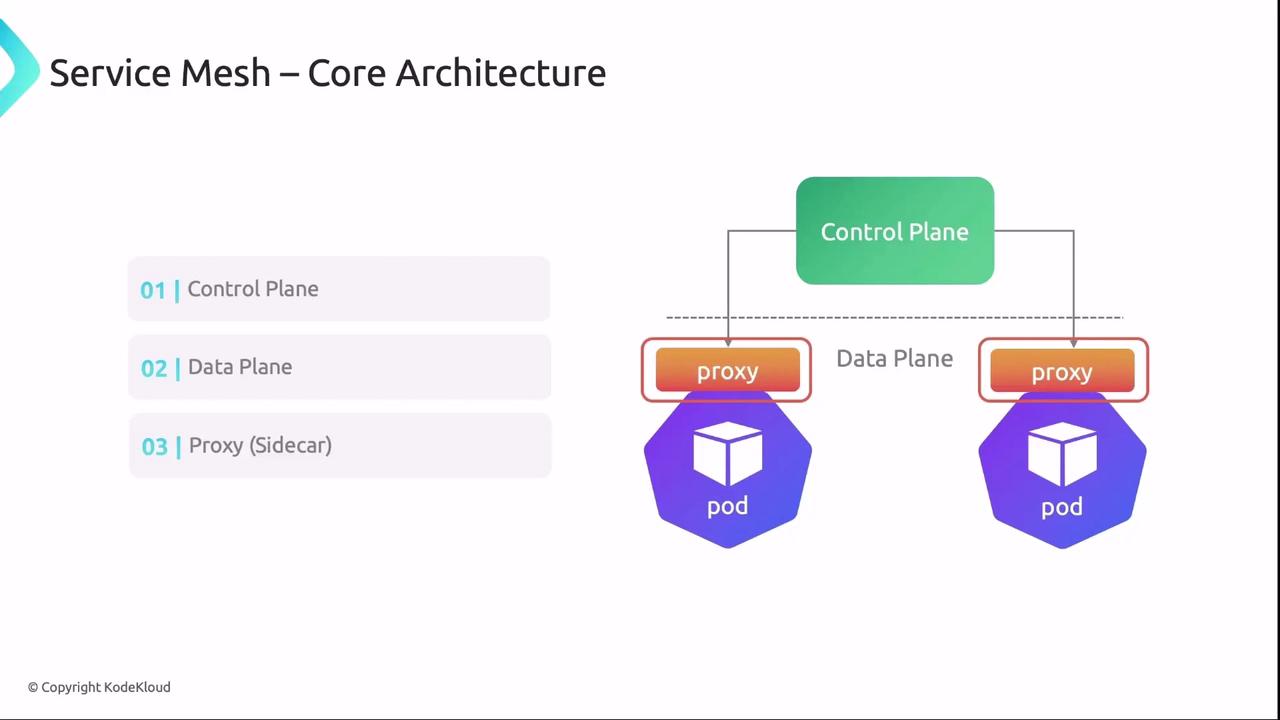
Service Mesh consists of three main components:- Control Plane
Manages service discovery, configuration distribution, policy enforcement, and telemetry aggregation. - Data Plane
Sidecar proxies (e.g., Envoy) intercept and control all network traffic for each service instance. - Sidecar Proxy
Enforces routing rules, load balancing, security policies, and collects telemetry in each pod.
Proper certificate lifecycle management is critical for mTLS. Misconfigured certificates can lead to downtime or security gaps.
Use Cases
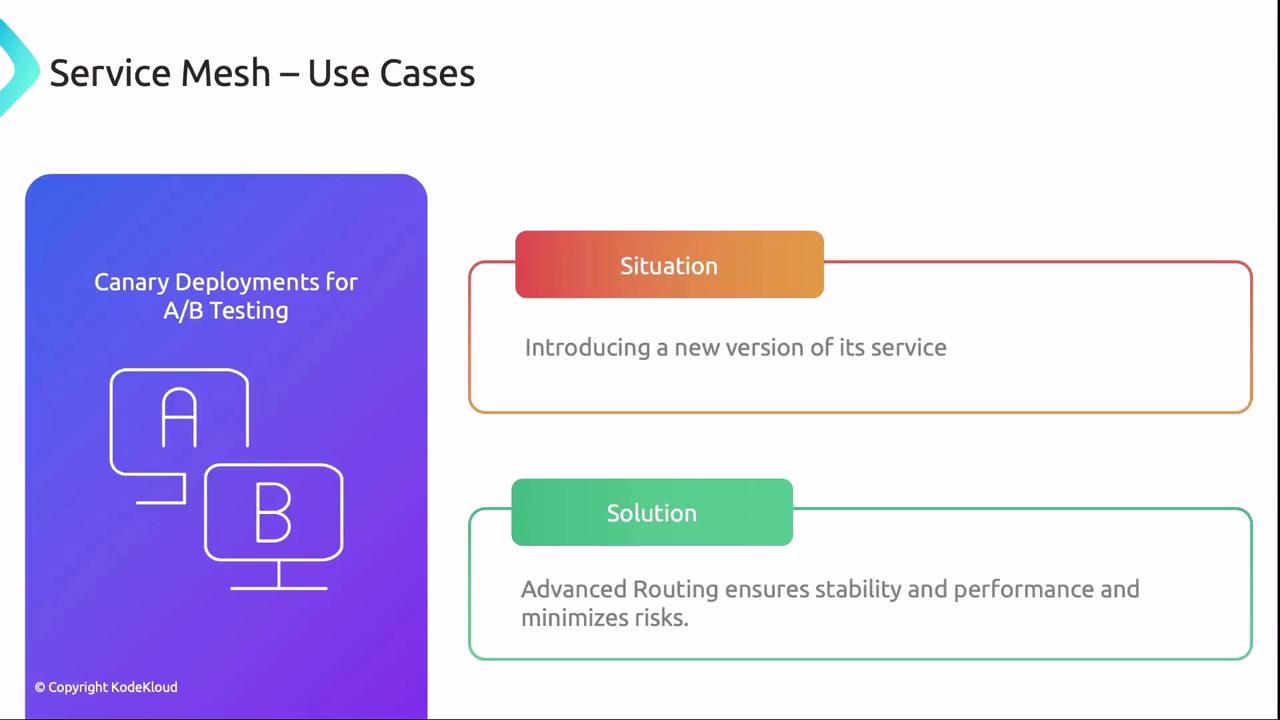
- Canary Deployments for A/B Testing
Gradually shift a small percentage of traffic to a new version before full rollout.
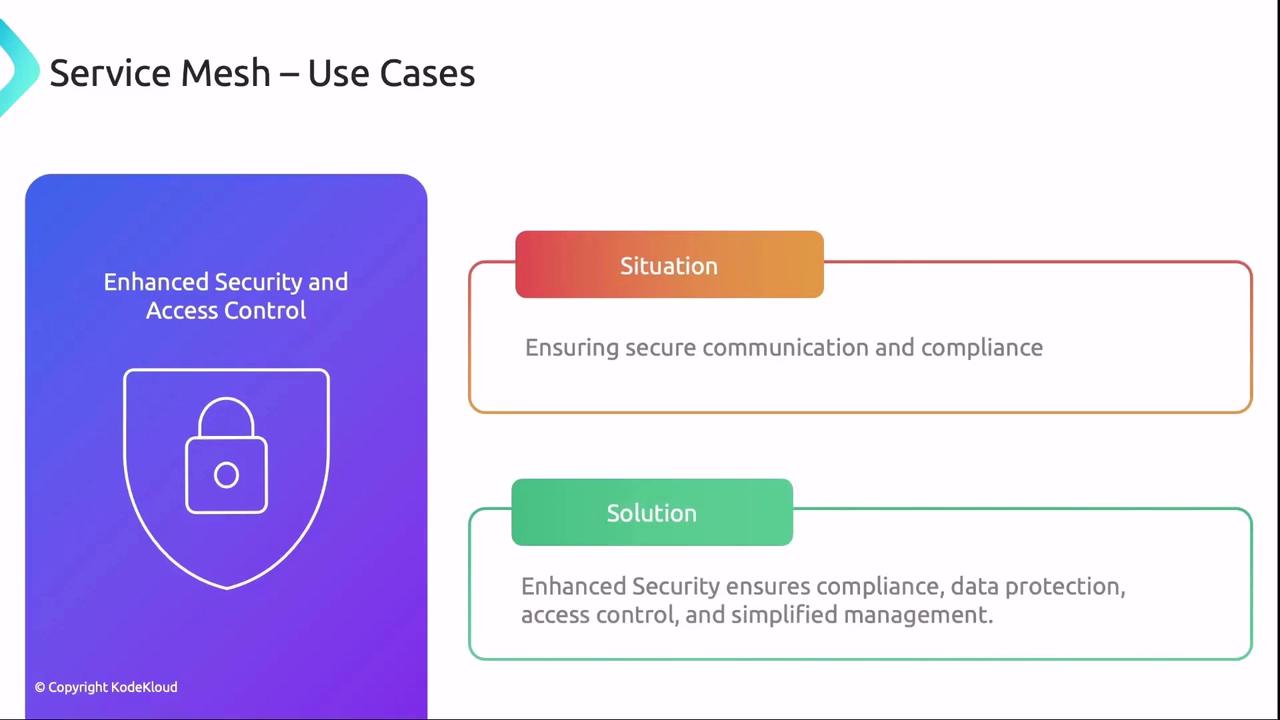
- Enhanced Security & Compliance
Automatically enforce mTLS, RBAC, and network policies for sensitive data flows.
- High Availability
Detect unhealthy instances and reroute traffic to healthy pods, ensuring continuous service.
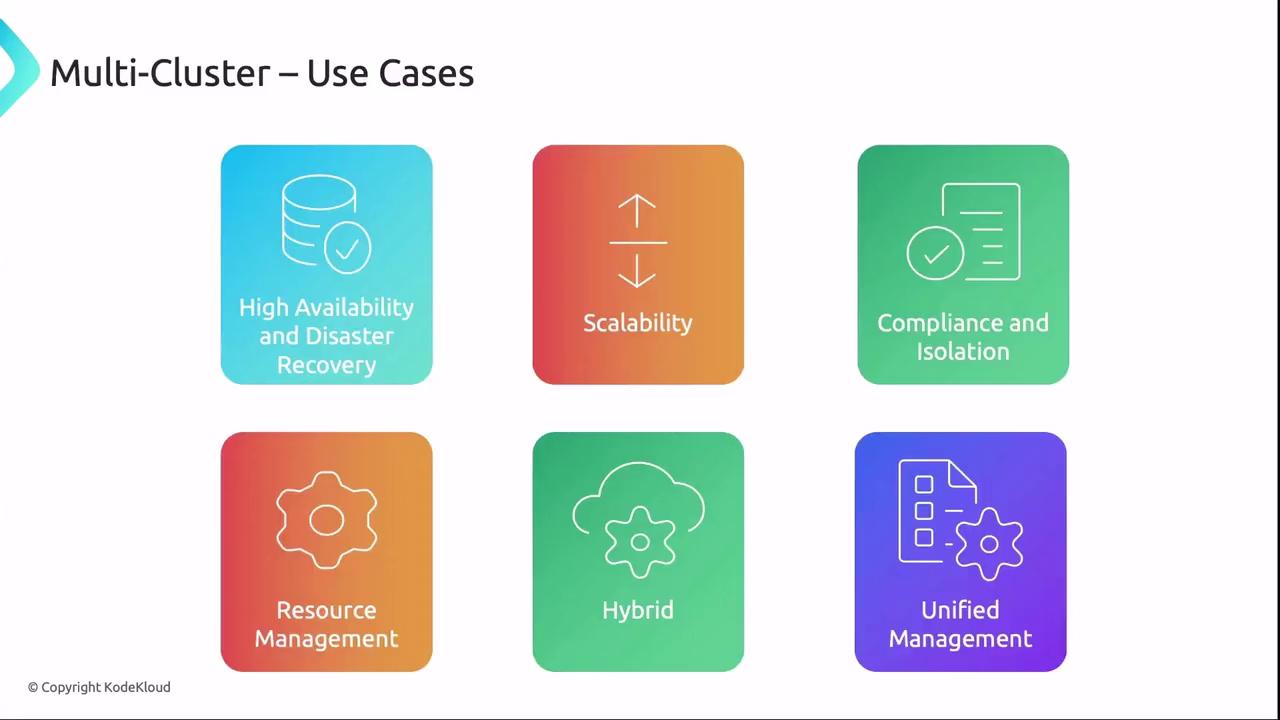
Multi-Cluster
Operating multiple Kubernetes clusters—either independently or as a cohesive system—enables:| Use Case | Benefit |
|---|---|
| High Availability & DR | Regional distribution with automatic failover |
| Scalability | Horizontally scale workloads across clusters |
| Compliance & Isolation | Dedicated clusters for regulated or sensitive workloads |
| Resource Management | Tailor clusters for specific performance or cost requirements |
| Hybrid Deployments | Combine on-premises and multiple clouds to avoid vendor lock-in |
| Unified Management | Centralized control via Federation or Anthos |
- Kubernetes Federation (docs)
- Google Anthos (cloud.google.com/anthos)
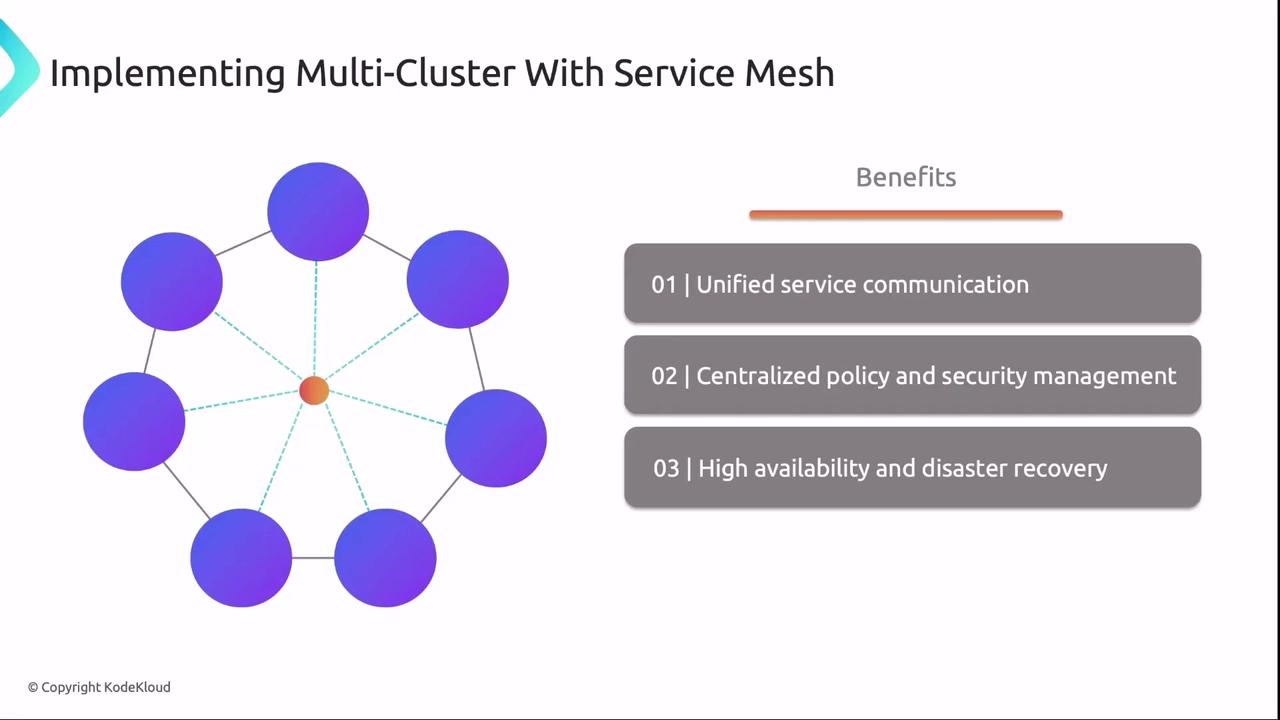
Combining Service Mesh and Multi-Cluster
Merging Service Mesh with Multi-Cluster delivers:- Unified Service Communication
Cross-cluster service discovery and secure connectivity. - Centralized Policy & Security
Single policy definition enforced across all clusters with mTLS. - Global High Availability
Dynamic traffic routing ensures uptime even if an entire cluster fails. - Consolidated Observability
Centralized logging, metrics, and tracing from every cluster.
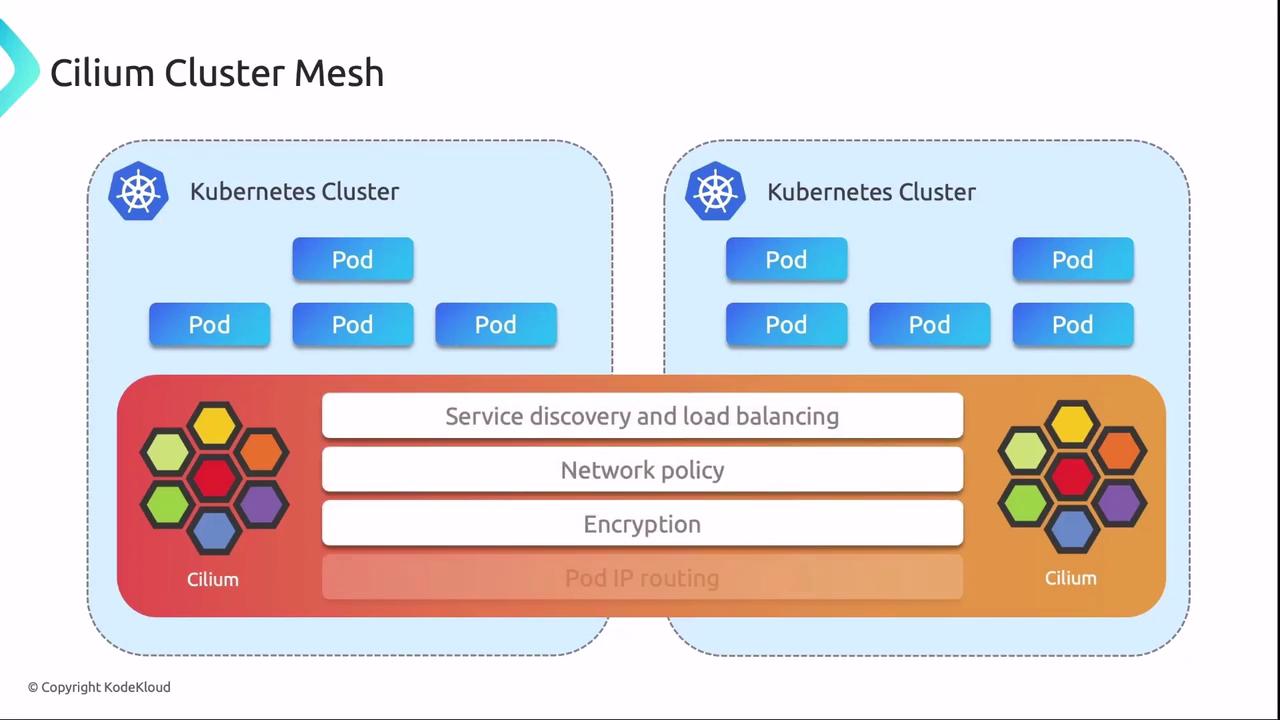
Cilium Cluster Mesh
Since Company X uses Cilium as its CNI, Cilium Cluster Mesh extends networking and security across clusters with eBPF:- Seamless service discovery and connectivity
- Consistent network policies and encryption
- Cross-cluster load balancing and failover
- Unified observability
Cilium Cluster Mesh requires host kernel support for eBPF features.
Conclusion
Service Mesh and Multi-Cluster architectures provide:- Advanced traffic management, mTLS security, and observability
- Geographic high availability, scalability, and operational flexibility
- A unified, resilient platform when used together, especially with Cilium Cluster Mesh