- Valid authentication mechanisms (username/password or SSH key-based).
- Port 22 open between your client and the remote server.
In complex environments featuring multiple clients and servers interconnected by various routers and switches, implementing robust network security is essential. You can secure the network using external firewall appliances or apply filtering rules directly on each server with tools like iptables, firewalld on Linux, or the built-in firewalls on Windows.
| Device | IP Address |
|---|---|
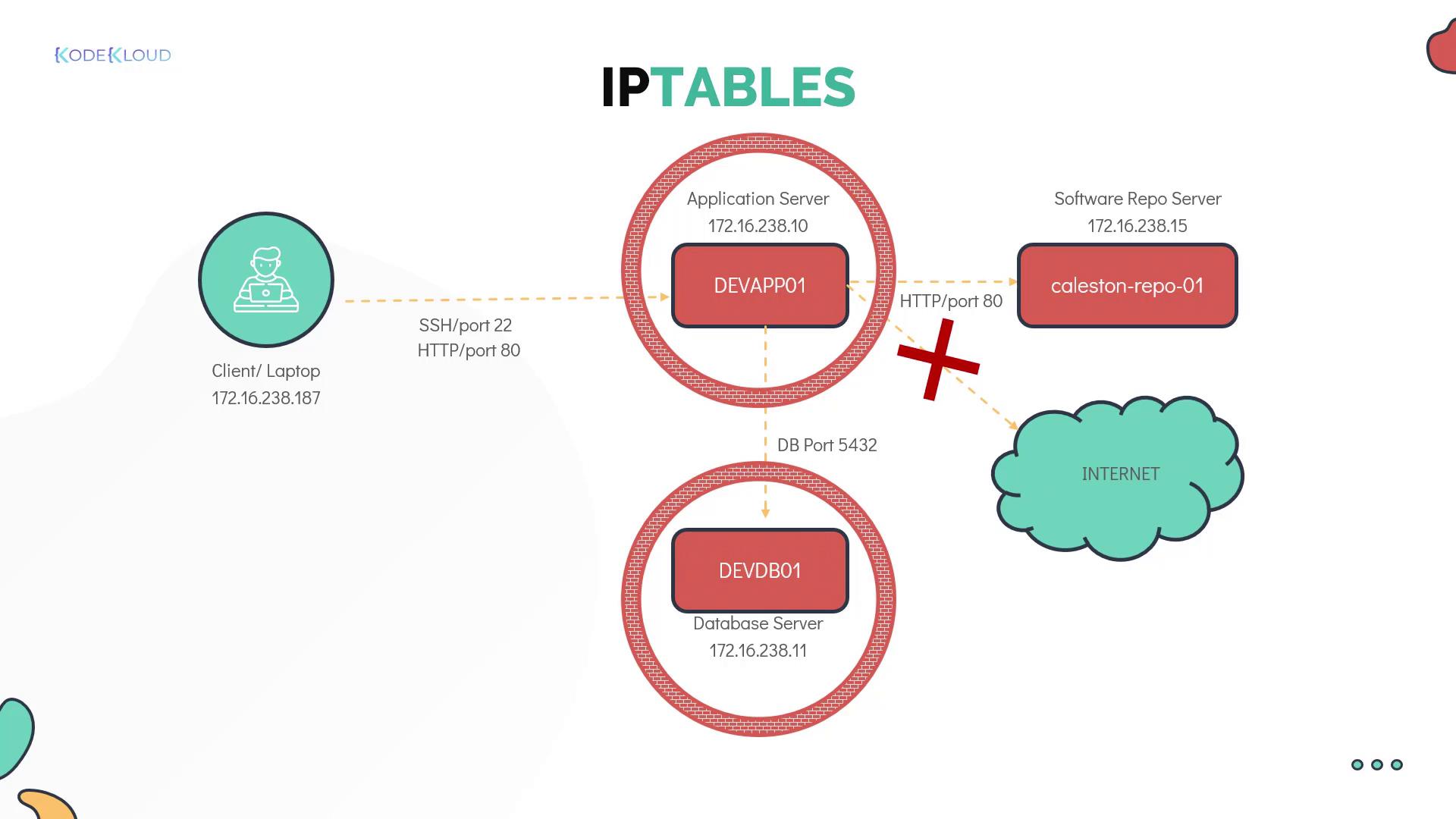
| Client laptop | 172.16.238.187 |
| Application server | 172.16.238.10 |
| Database server | 172.16.238.11 |
- Allow SSH access from your laptop to the application server.
- Permit HTTP access (port 80) to the application server only from the client laptop, blocking other servers (e.g., devdb01).
- Allow the application server to connect to the database server on port 5432 for database operations.
- Grant the application server HTTP access to the software repository server (kailston-repo-01).
- Block outgoing internet access from the application server.
- Restrict the database server to accept connections on port 5432 solely from the application server.
Establishing SSH Connectivity
Begin by establishing an SSH connection to the devapp01 server from your client. Once connected, you will use iptables to filter network traffic. On Red Hat and CentOS, iptables is installed by default. On Ubuntu, installation may be required:Understanding IPTABLES Chains
Iptables uses three main chains, each serving a distinct purpose:- INPUT Chain: Manages incoming traffic. For instance, adding a rule here allows SSH connections from your client laptop.
- OUTPUT Chain: Controls traffic originating from the server, including outbound connections like database queries.
- FORWARD Chain: Typically used by network routers to forward traffic between devices. Standard Linux servers rarely use this chain.
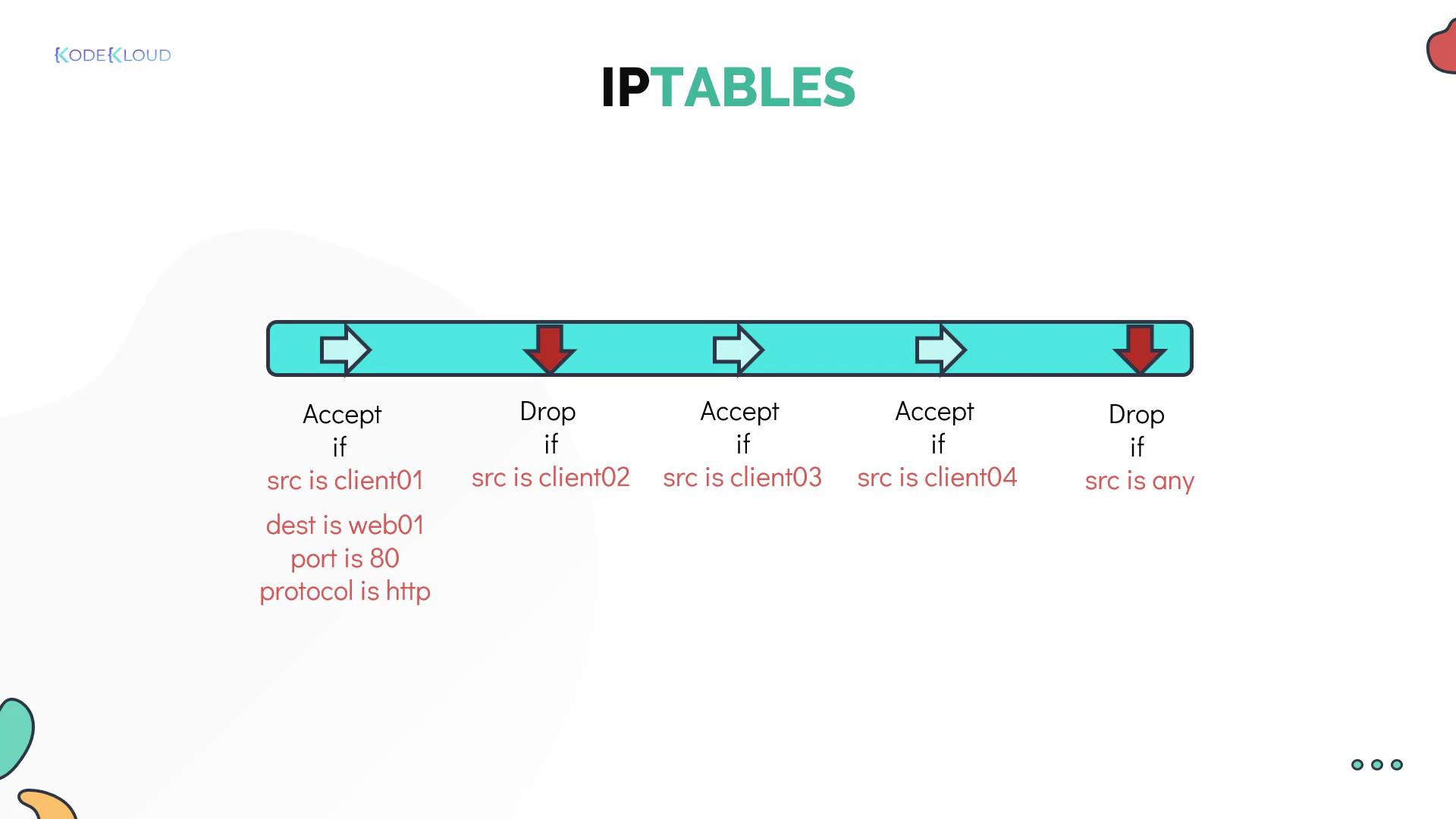
A “chain” is essentially a list of rules. Each rule checks network packets and decides whether to accept or drop them based on defined conditions such as source IP, destination IP, port number, or protocol. If a packet does not match any rule, it continues to the next rule until it either matches one or reaches the chain’s end.
- A packet from client 01 meets the first rule in the INPUT chain and is accepted.
- A packet from client 02 does not match the first rule and is evaluated by subsequent rules.
- A packet from client 05 might not match any allow rules and is eventually dropped by a default drop rule.