Resource Types: Vaults and Managed HSMs
Azure Key Vault supports two main resource types for handling cryptographic keys:-
Vaults
Standard key vaults allow you to store keys with two protection methods:- Software protected: Keys secured within the Azure infrastructure using advanced software protection.
- HSM protected: Keys processed in a Hardware Security Module (HSM) for an extra layer of security (available with the premium SKU).
-
Managed HSMs
Managed HSMs offer dedicated hardware from a third-party vendor, ensuring continuous HSM protection. This resource type provides the highest level of cryptographic key protection.
- For vaults:
https://<thevaultname>.vault.azure.net - For managed HSMs:
https://<hsmname>.managedhsm.azure.net
Key Types and Protection Methods
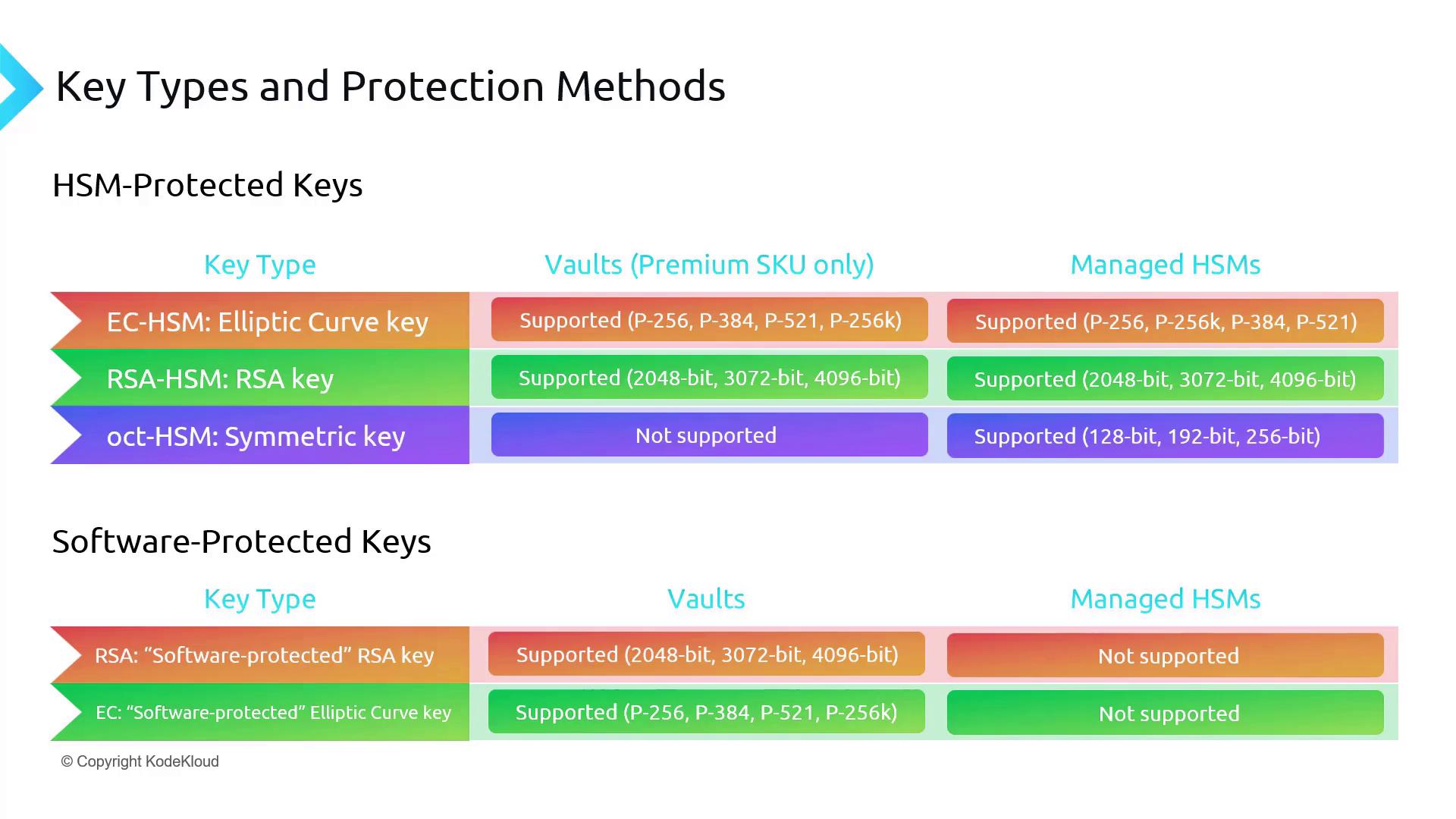
Key types in Azure Key Vault are categorized based on two protection methods: HSM protected keys and software protected keys.HSM Protected Keys
There are three main key types supported as HSM keys:- Elliptic Curve (EC)
- RSA
- Octet
Only the premium SKU of Key Vault supports HSM protected keys. While the premium SKU offers various key sizes for most types, Octet HSM is not supported here. Managed HSM supports all the premium SKU options, including Octet HSM.
Software Protected Keys
For vaults that support both premium and standard SKUs, the supported software protected key types are:- RSA
- Elliptic Curve (EC)
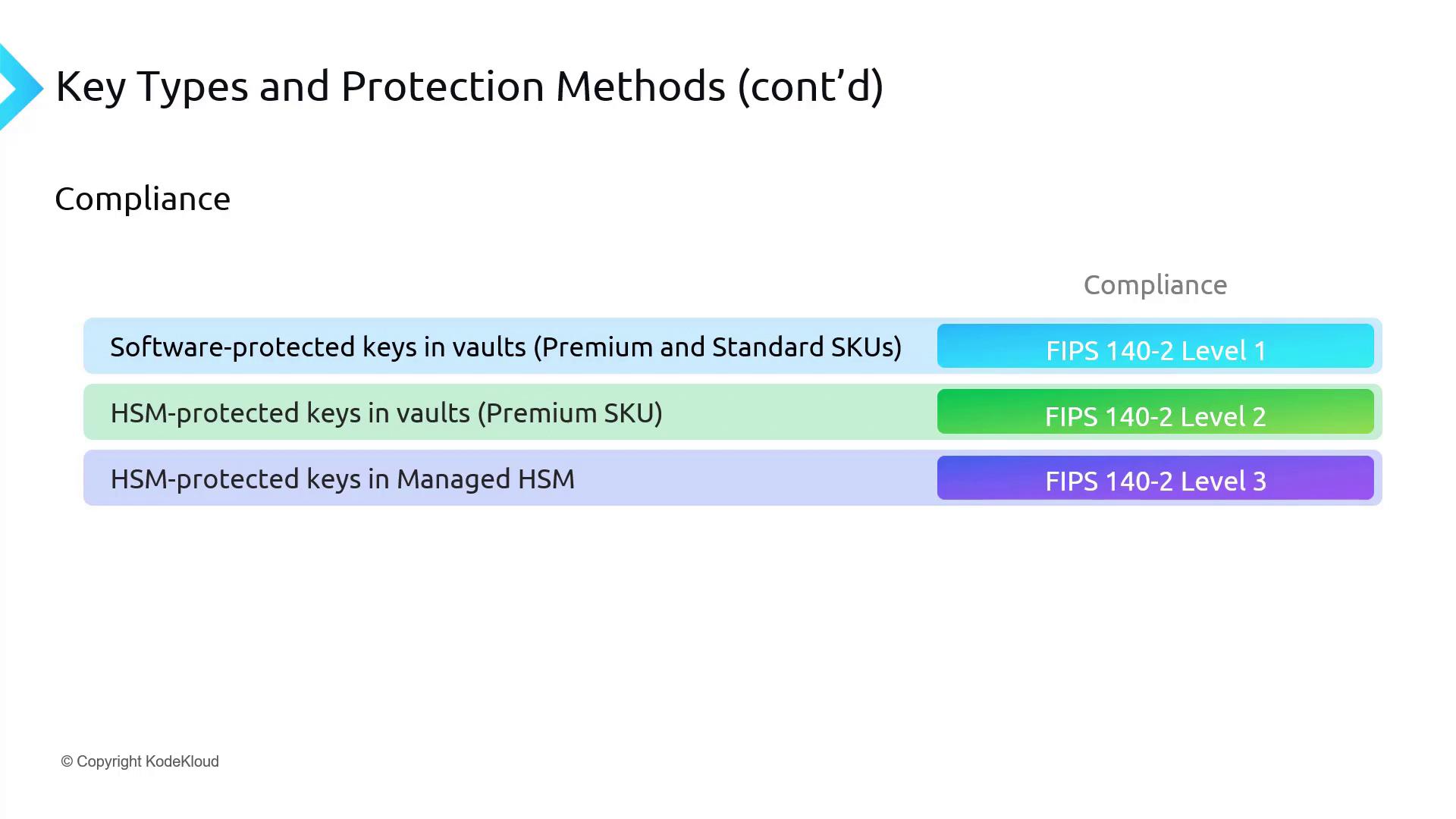
Compliance Levels
Compliance requirements can significantly influence your choice of SKUs and key protection methods:-
Software Protected Keys in Vaults
These keys comply with FIPS 140-2 Level 1, offering basic security suitable for general applications. -
HSM Protected Keys in Vaults (Premium SKU)
These keys achieve FIPS 140-2 Level 2 compliance. They incorporate physical tamper evidence and role-based authentication, providing enhanced security over Level 1. -
HSM Protected Keys in Managed HSM
Managed HSM keys comply with FIPS 140-2 Level 3, offering advanced tamper resistance suitable for highly sensitive operations.
Summary
Azure Key Vault provides a comprehensive framework for managing cryptographic keys with different levels of protection and compliance. The decision to choose between vaults and Managed HSMs—as well as the selection of software or HSM protected keys—should be based on your organization’s specific security requirements and compliance mandates.The discussion on cryptographic keys is now complete. The following sections will cover Azure Key Vault secrets and certificates. Once you’ve reviewed all three aspects, we will proceed to the Azure portal to deploy and interact with the Key Vault solution. Let’s move forward and explore Azure Key Vault secrets.