Key Rotation for Keys
Key rotation for keys is straightforward. In Azure, you can enable an auto-rotation policy directly from the key settings. This feature allows you to specify both the rotation interval and exact time for rotation, as well as configure notifications via Event Hub. For example, if your key has an expiry time, you can configure the system to trigger auto-renewal a few days (e.g., 7 days) before the actual expiration. This proactive approach helps ensure that a new key is generated before any potential compromise.Key Rotation for Secrets
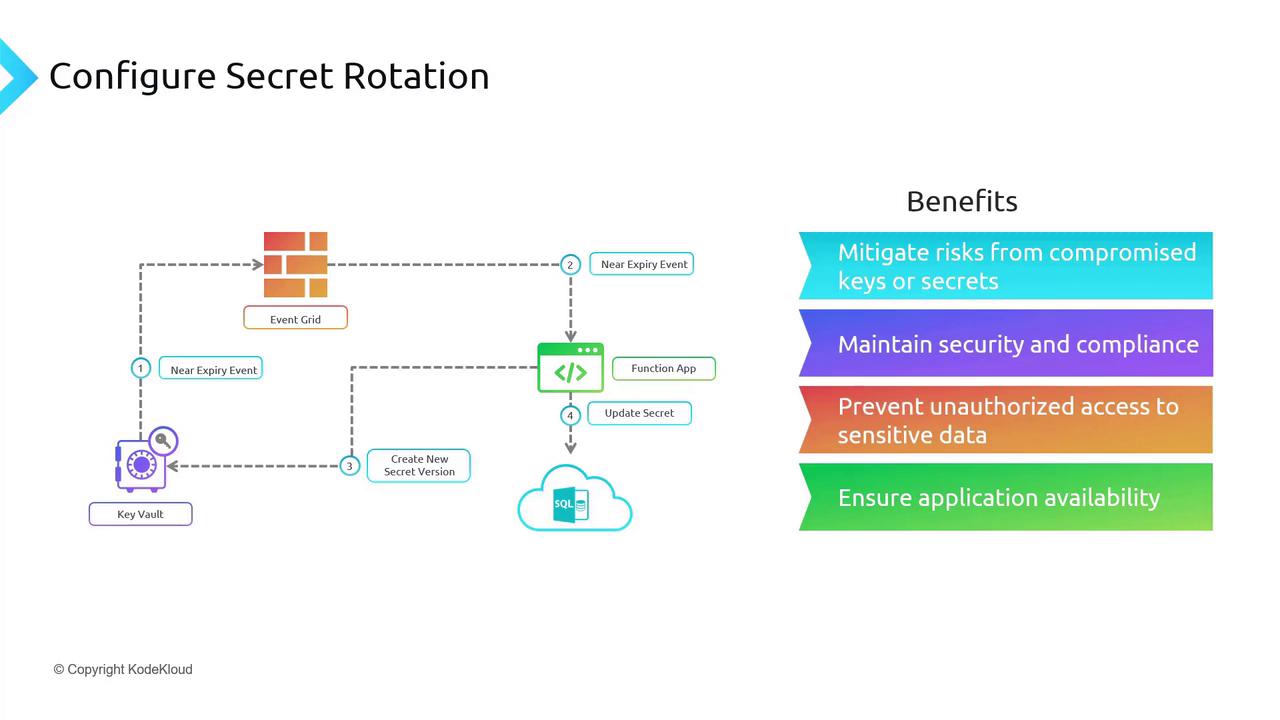
Unlike keys, Azure does not offer built-in secret rotation. Instead, you can automate secret rotation by integrating Azure Key Vault with Azure Event Grid. When the Key Vault detects events related to secret expiry, Event Grid publishes these events. A Function App, authenticated by either a managed identity or service principal, is then triggered to create a new version of the secret. With the correct Role-Based Access Control (RBAC) permissions, the updated secret is pushed automatically to your databases and applications.Why Rotate Keys and Secrets?
Rotating keys and secrets is essential for keeping your systems secure. Here are the primary benefits:- Mitigate Risks: Frequent rotation reduces the chance of exposure when keys or secrets are compromised.
- Enhance Security and Compliance: Many organizations mandate periodic key and secret changes. Automated rotation meets such compliance requirements.
- Prevent Unauthorized Access: Regularly updating credentials minimizes the risk of unauthorized or ex-employee access.
- Maintain Application Availability: Updated keys and secrets ensure that your applications always run with current credentials, leading to more reliable operations.
Rotating keys and secrets helps secure your applications by proactively addressing potential vulnerabilities and maintaining compliance with security policies.
Key Rotation Considerations
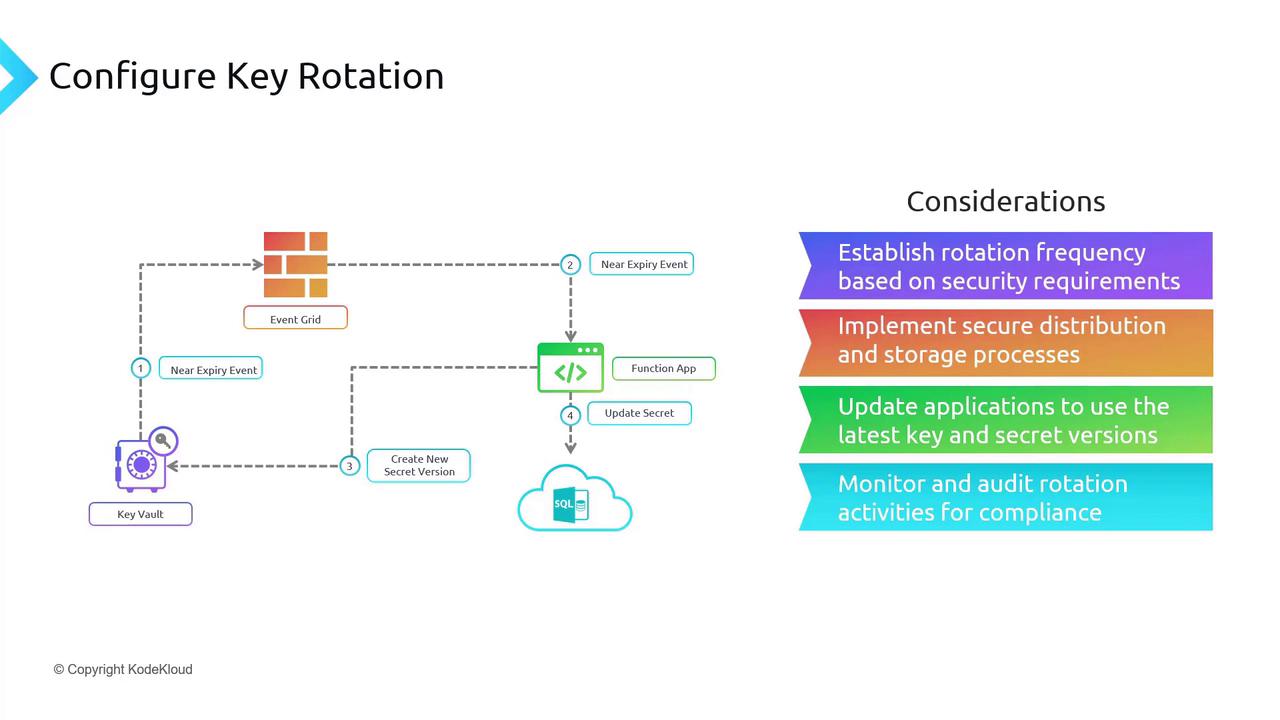
Before implementing key rotation, keep the following factors in mind:- Rotation Frequency: Determine a key rotation schedule based on your organization’s security requirements. Some organizations opt for intervals of four months, while others choose six months.
- Secure Distribution and Storage: Ensure that newly rotated keys are securely transmitted to your applications.
- Application Updates: Automate application updates using Azure DevOps or pipelines, ensuring that your services always reference the latest keys or secrets.
- Monitoring and Auditing: Implement thorough monitoring and auditing mechanisms to track key rotation activities and support compliance reporting.
Configuring Key and Secret Rotation in the Azure Portal
Follow these steps to set up key and secret rotation in the Azure portal:Configuring Key Rotation
- Open your Azure Key Vault in the Azure portal.
- Select the key you want to configure.
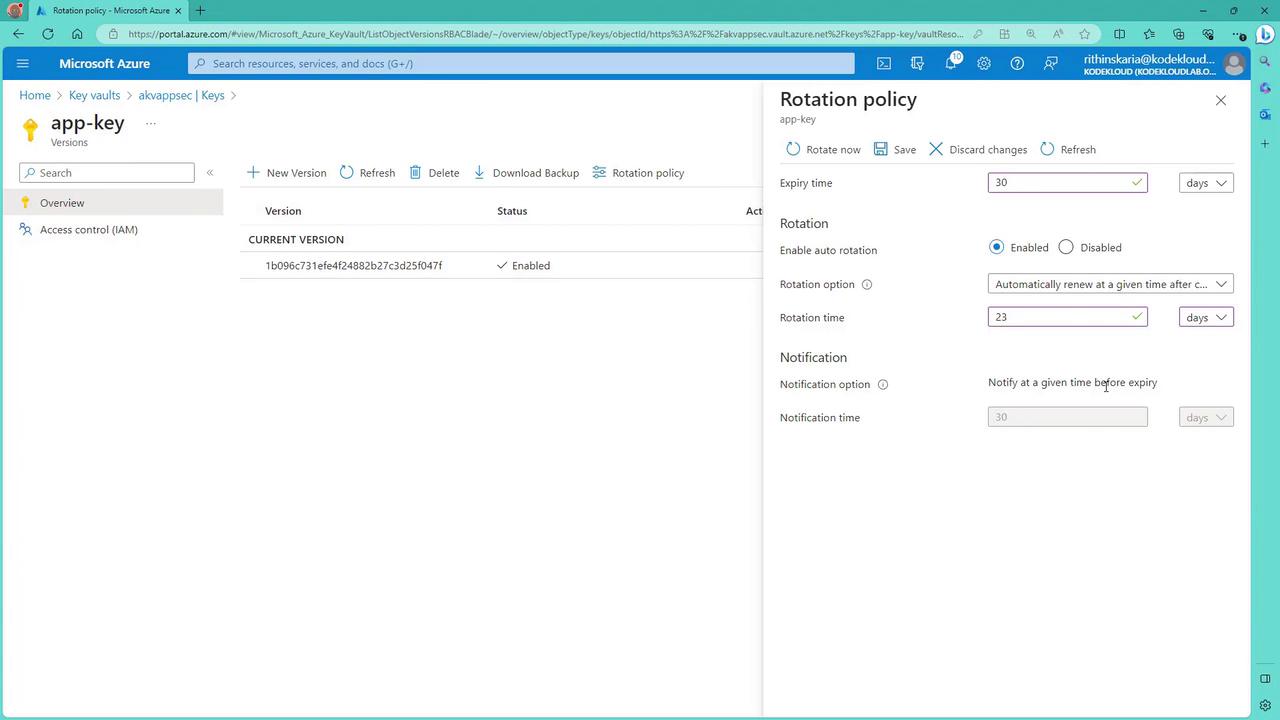
- In the top section, locate the “Rotation Policy” panel.
- Enable the rotation policy (disabled by default).
- If the key currently lacks an expiry setting, set an expiry (e.g., 30 days) so that auto-rotation can trigger at least seven days before expiration (e.g., on day 23).
- Optionally, set up notifications (e.g., 30 days before expiry) to plan maintenance or immediate changes.
- Utilize the “Rotate Now” button if you need to immediately rotate the key.
Configuring Certificate Rotation
To configure certificate rotation, navigate to the issuance policy section in your Azure portal. Here, you can manage certificate renewal settings, including triggering automatic renewal when the certificate has reached a specified portion (for example, 80%) of its validity period.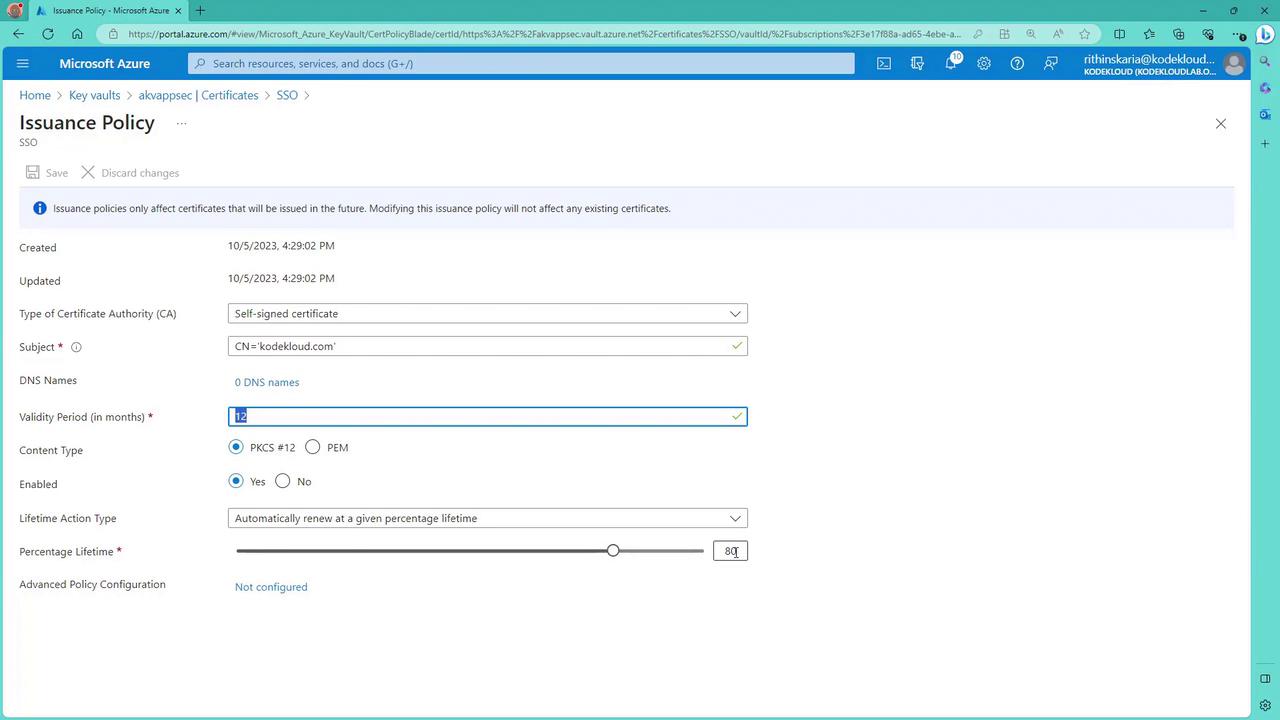
Automating Secret Rotation
Since Azure does not offer a built-in secret rotation mechanism, you can automate the process using the following steps:- In your Key Vault portal, access the “Events” section.
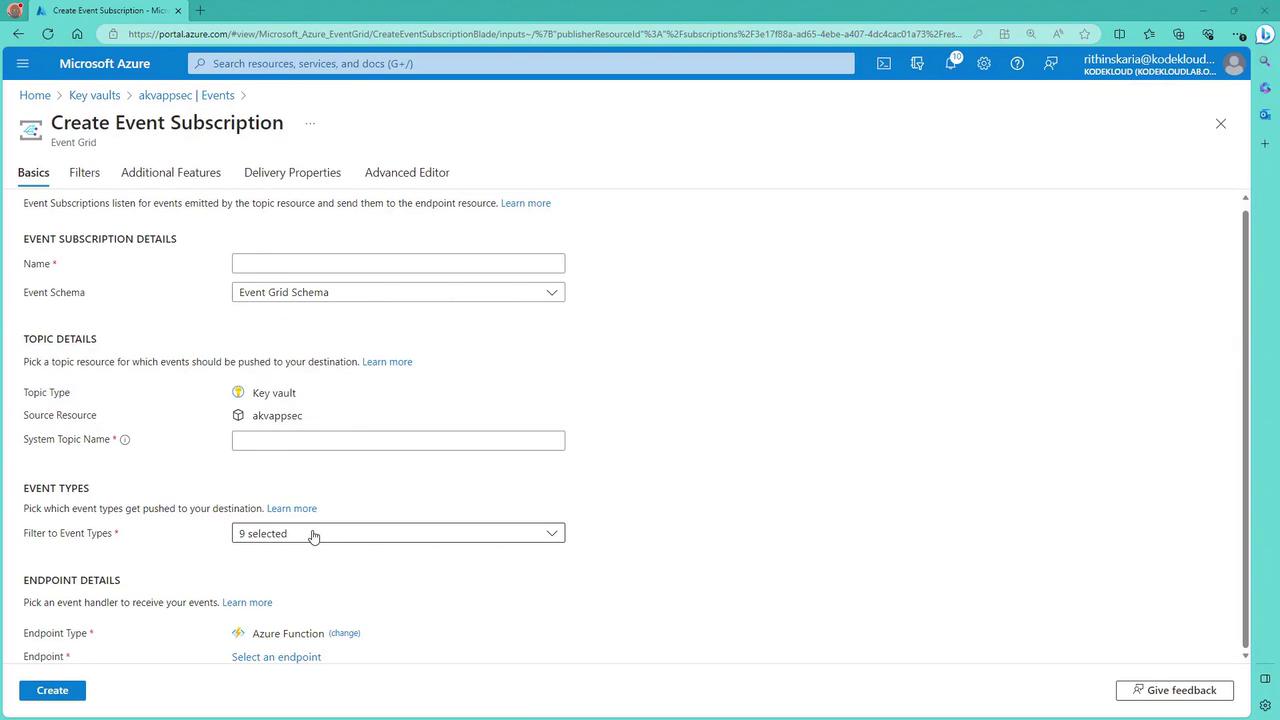
- Create an event subscription to link with Azure Logic Apps or Azure Functions, specifically targeting near-expiry secret events.
- Configure the event subscription via the Event Grid interface. When a secret is nearing expiry, the event triggers a Function App to generate a new secret version and update your applications accordingly.
Summary
Effective key, certificate, and secret rotation is essential for maintaining high levels of security, ensuring compliance, and keeping your applications available. In this guide, we discussed:- Enabling key auto-rotation and configuring expiry settings in the Azure portal.
- Automating secret rotation using Azure Event Grid and Functions.
- Best practices including secure distribution, automated application updates, and continuous monitoring.