Mitigation Strategies
Implementing the following strategies can greatly reduce the risk of brute force attacks:- Strong Passwords: Use complex, unique passwords that are difficult to guess.
- Multi-Factor Authentication (MFA): Require additional verification beyond just a password.
- Account Lockout Policies: Automatically lock accounts after a predetermined number of failed login attempts.
- Continuous Monitoring: Regularly inspect logs and set up automated alerts for any unusual login attempts.
- Cybersecurity Awareness: Educate users on the importance of proper password practices.
- Regular Updates: Keep systems updated by installing security patches, using intrusion prevention systems, and incorporating threat intelligence to detect evolving attack patterns.
Detection with Microsoft Defender for Cloud
Microsoft Defender for Cloud is an effective tool in detecting brute force attacks. It notifies you through security alerts when potential brute force activities are identified. These alerts are displayed in the security alerts section, offering a centralized view of potential security threats.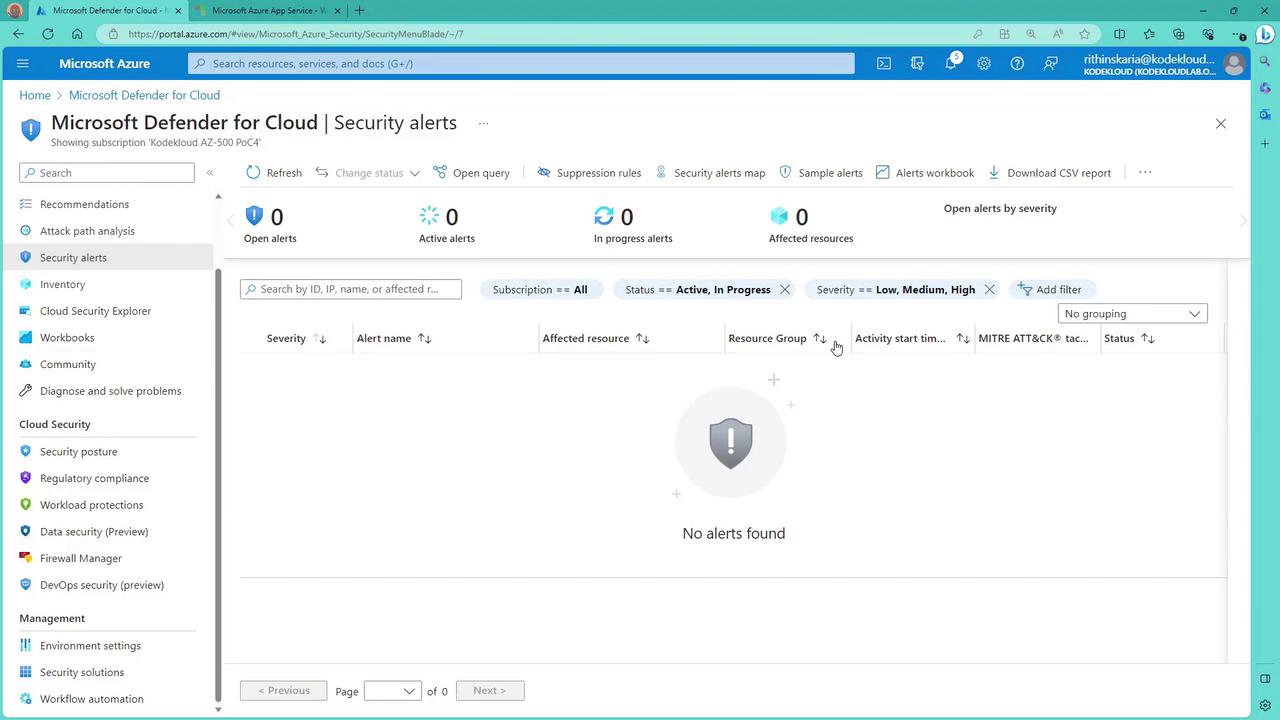
Configuring Alert Notifications
To ensure you receive prompt notifications of any significant security alerts, including brute force attack alerts, configure email notifications within your environment settings:- Navigate to the environment settings in Microsoft Defender for Cloud.
- Select and customize the email notification rules.
- Add additional email addresses as needed.
- Choose the appropriate alert severity levels (e.g., high or medium) to tailor the notifications.
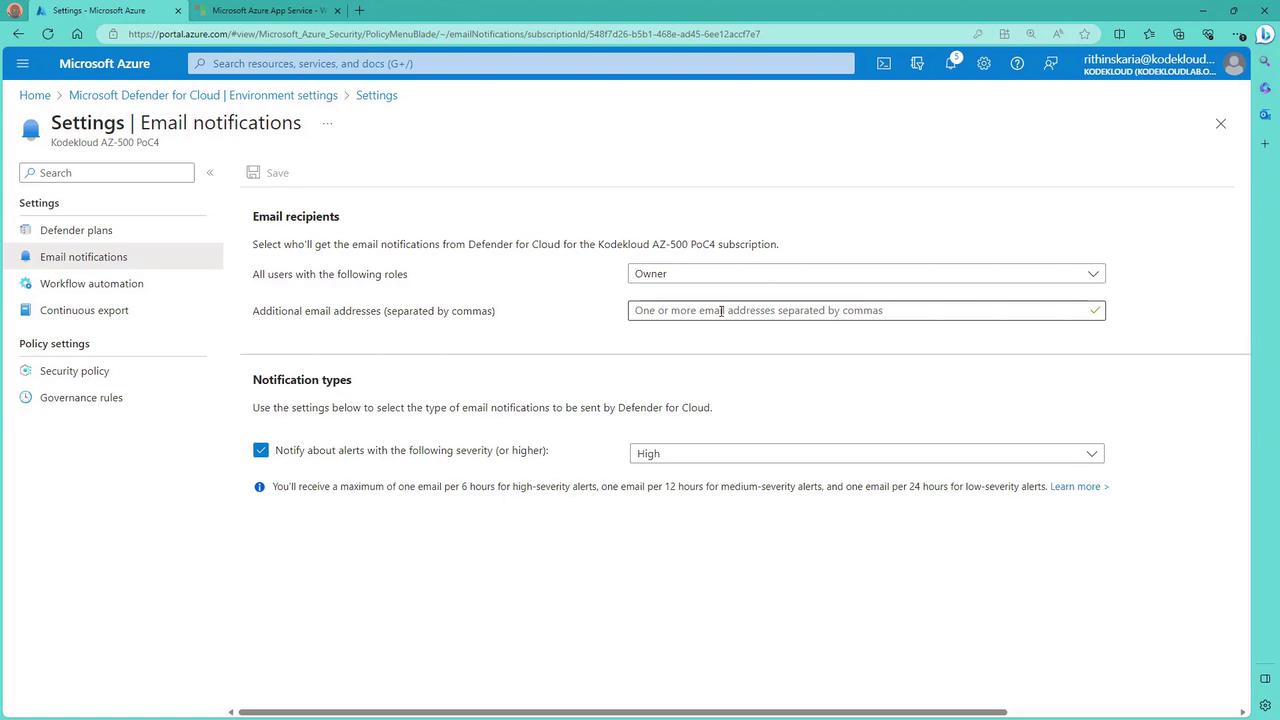
Configuring these settings ensures that you are immediately informed of any significant security events, allowing for quick response actions.