• Data integrity: Ensures stored data remains unchanged.
• Compliance: Meets regulatory and legal requirements efficiently.
• Auditability: Enforces logging of all access or operations on the data.
• Compliance: Meets regulatory and legal requirements efficiently.
• Auditability: Enforces logging of all access or operations on the data.
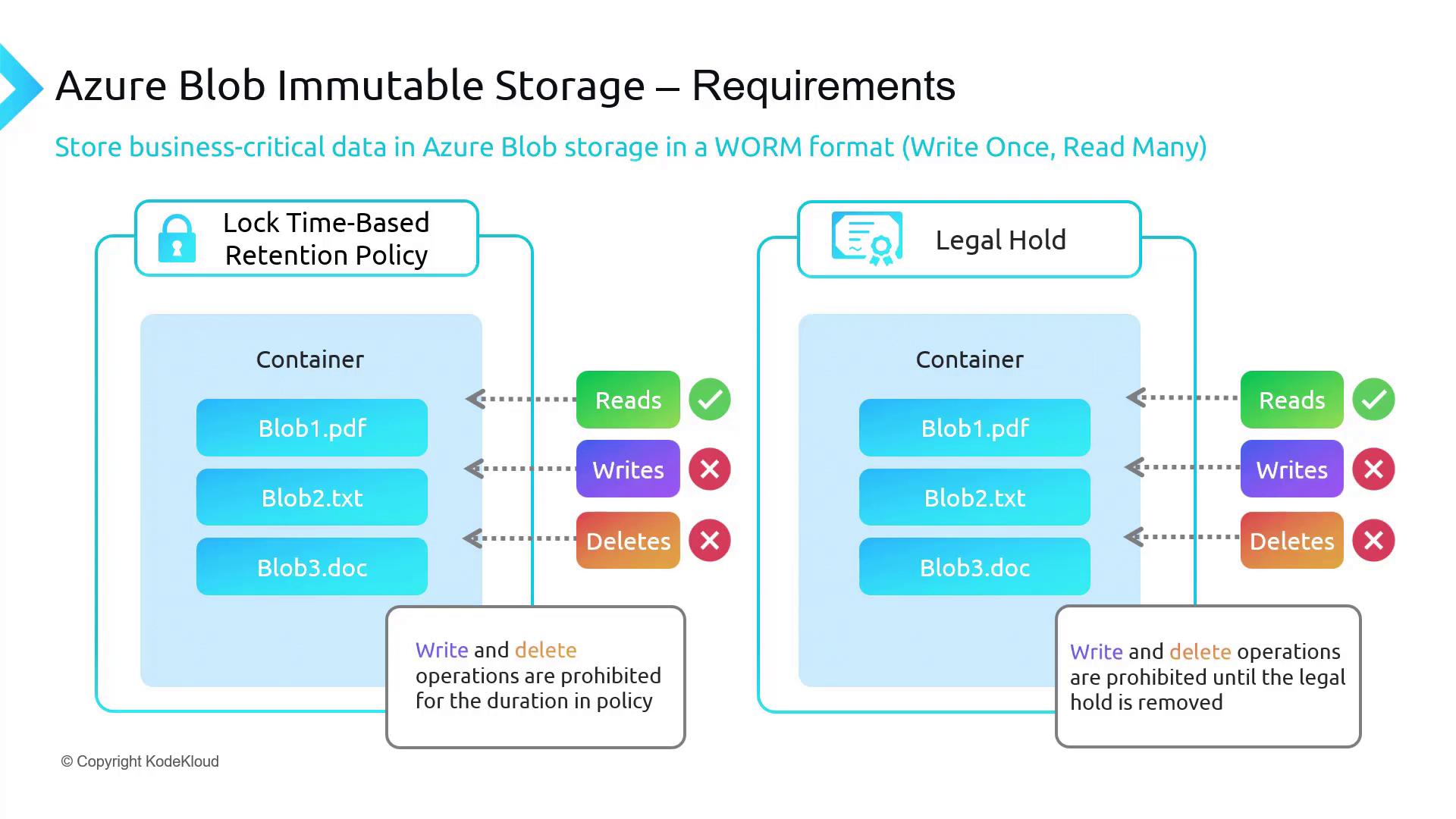
Features of Azure Blob Immutable Storage
There are two primary features of Azure Blob Immutable Storage:-
Container-Level Policies
Immutability policies at the container level impact every blob within the container. Once a policy is in place, any operation performed on the data is logged, creating a robust audit trail. For instance, a company may enforce a two-year retention policy on a container holding financial data, ensuring that any access or modifications are thoroughly recorded. -
Policy Scope
The immutability policy applies to both existing blobs and new uploads once implemented. For example, if a media company configures an immutable policy for its video container, all videos—whether uploaded before or after the policy is set—will adhere to the defined retention constraints.
Types of Immutability Mechanisms in Azure Storage
Azure Storage offers various immutability mechanisms to safeguard your data:-
Time-Based Retention Policies:
This policy enforces a fixed period during which data in a blob container cannot be modified or deleted. For example, an organization might lock annual financial reports for one year, ensuring that the files (e.g., blob1.pdf, blob2.txt) remain unaltered. -
Legal Holds:
Legal holds prevent any modifications or deletions until they are explicitly removed, even if the time-based retention period has expired. This mechanism is particularly useful during litigation. For example, a company involved in legal proceedings can maintain documents such as blob3.doc in their original state by applying a legal hold.
Implementing Immutable Storage Policies in the Azure Portal
Follow these steps to configure immutability policies on your Azure Blob Storage:-
Access Your Storage Account:
Open the Azure Portal and navigate to the storage account you created. -
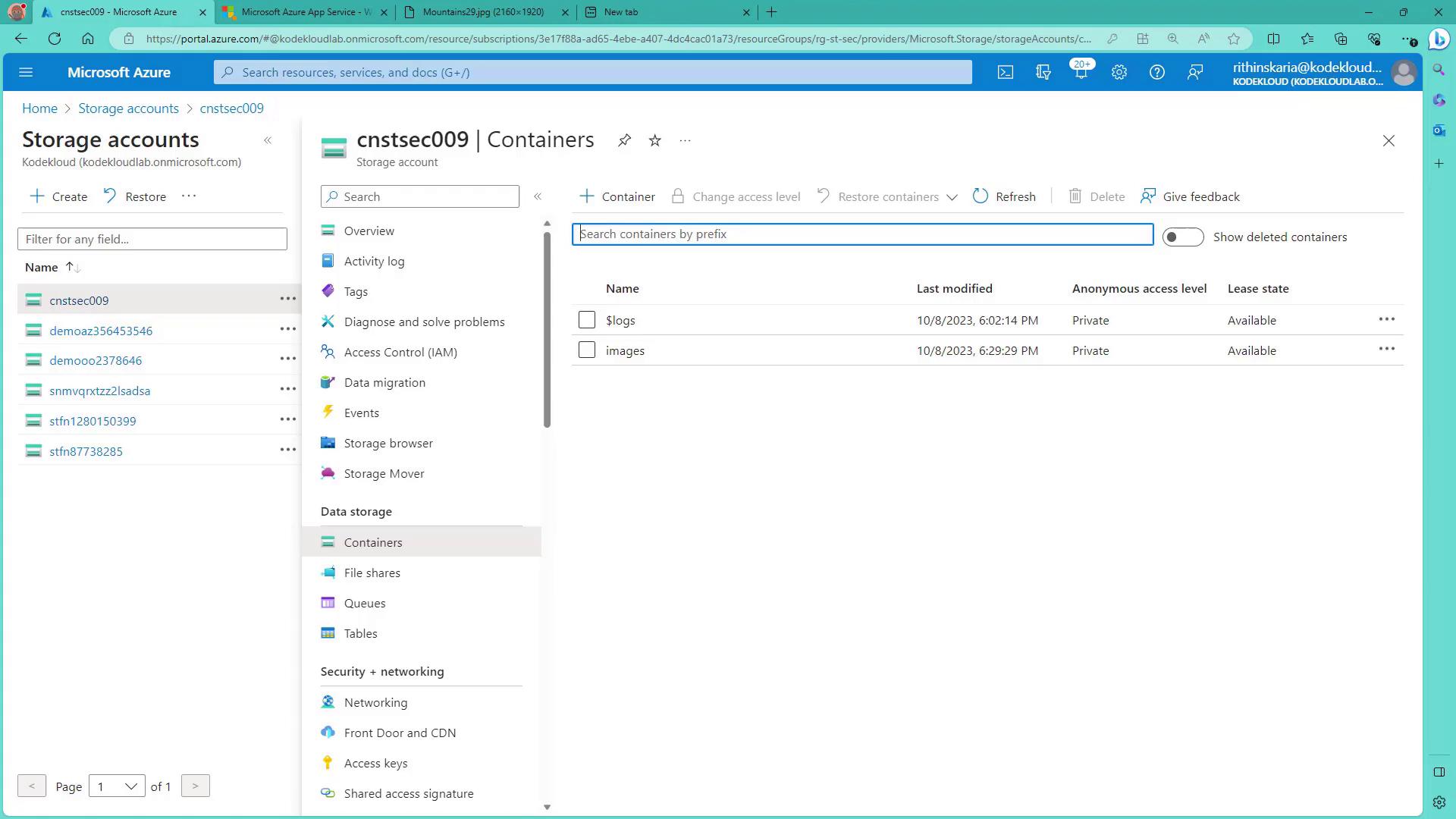
Navigate to Containers:
Go to the “Containers” section. You should see containers such as “images” and “$logs”.
-
Select the Desired Container:
Click on your selected container and choose “Access Policy” from the available options. -
Configure Access Policies:
In the stored access policies section, locate the immutable Blob Storage options and click “Add Policy” to create a new policy.- For a legal hold, you might assign a tag like “litigation” to indicate legal review, along with additional metadata such as a case number.
- Optionally, you can configure protected append rights for block or append blobs. Setting these rights to “none” ensures the data remains immutable.
-
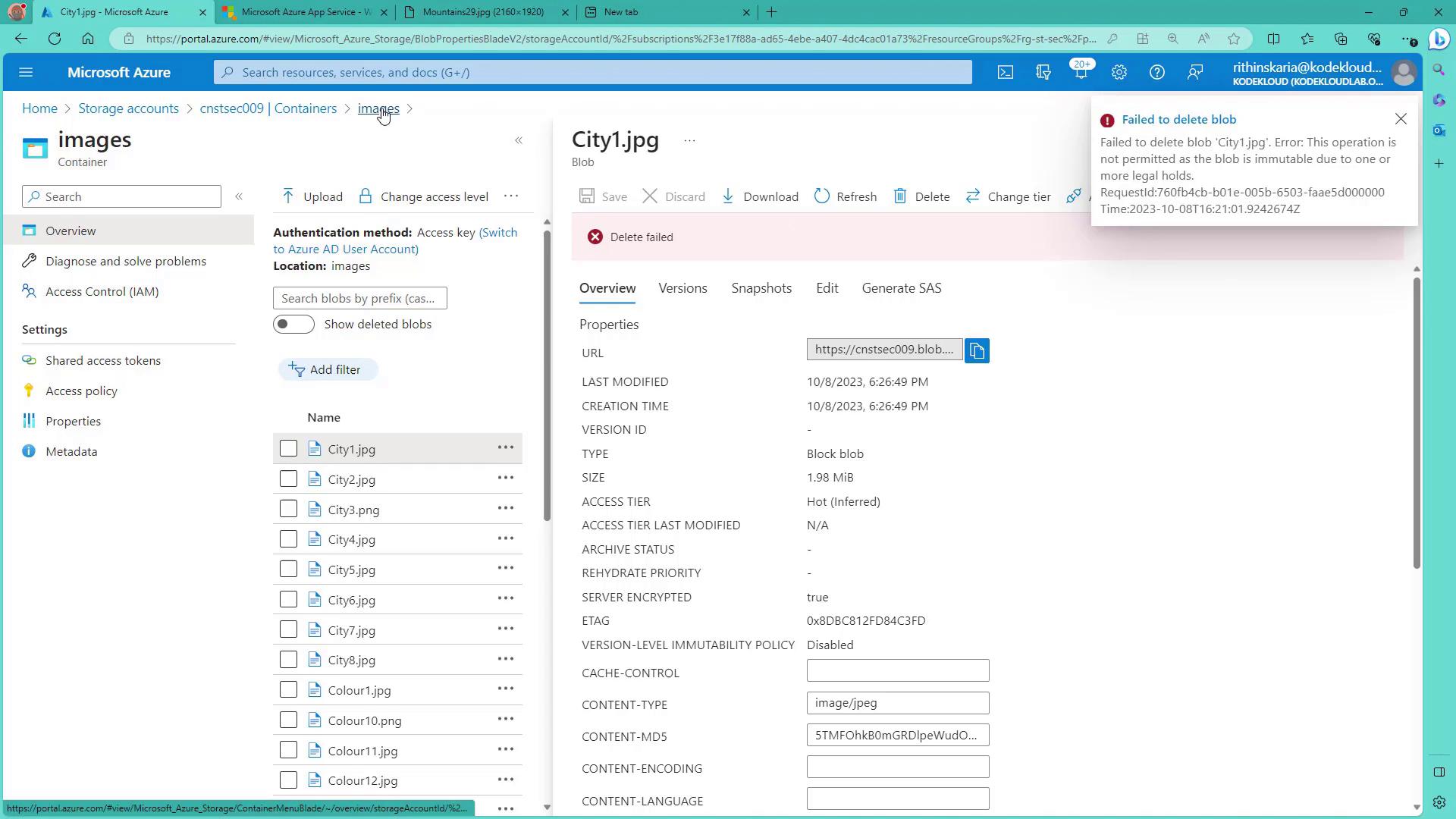
Test the Immutable Setting:
When attempting to access a blob (for instance, by clicking on an image) and then trying to copy or delete it, the deletion will fail due to the enforced immutability from one or more legal holds.
- Modify or Delete Blobs:
To change or remove a blob, you must first remove the applicable legal hold from the access policies.
- Click “Add Policy” and select the time-based retention option.
- Specify the retention duration (e.g., 10 days). During this period, the blob remains immutable and cannot be altered.
Transitioning to Azure Files Authentication
Now that you have a clear understanding of Blob Storage immutability and Azure AD authentication, let’s explore Azure Files authentication next. Note that Azure Files does not support Azure AD authentication directly; instead, it integrates with Azure AD Domain Services or on-premises Active Directory. The next lesson will delve into the configuration process for Azure Files authentication.For additional details and best practices, please refer to the Azure Blob Storage documentation and explore further resources on Azure Security.