- It facilitates connectivity, which is the backbone of the internet and other networks.
- It supports data exchange between disparate systems, enabling applications like web browsers, email clients, and streaming services.
- It provides remote access to resources such as cloud storage or remote desktop applications.
- It helps build scalable applications capable of handling many simultaneous connections—a necessity for modern web services.
Overview of Network Protocols: TCP and UDP
To appreciate network programming, it is essential to grasp the two primary network protocols: TCP and UDP. These protocols establish the rules for data formatting and transmission over a network, ensuring that any information sent is accurately interpreted by the recipient.
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
Transmission Control Protocol (TCP)
TCP is a connection-oriented protocol, meaning it creates a reliable connection between a client and a server before data is exchanged. Think of it as establishing a two-way tunnel where data flows securely in both directions. TCP ensures data integrity by:- Confirming that data reaches its destination accurately and sequentially.
- Retransmitting lost packets to maintain completeness.
- Utilizing error checking mechanisms.
- Implementing flow control and congestion control to adjust the transmission rate based on network conditions.
Think of TCP like a phone call where both parties ensure clear communication before proceeding with the conversation.
TCP Connection Process
-
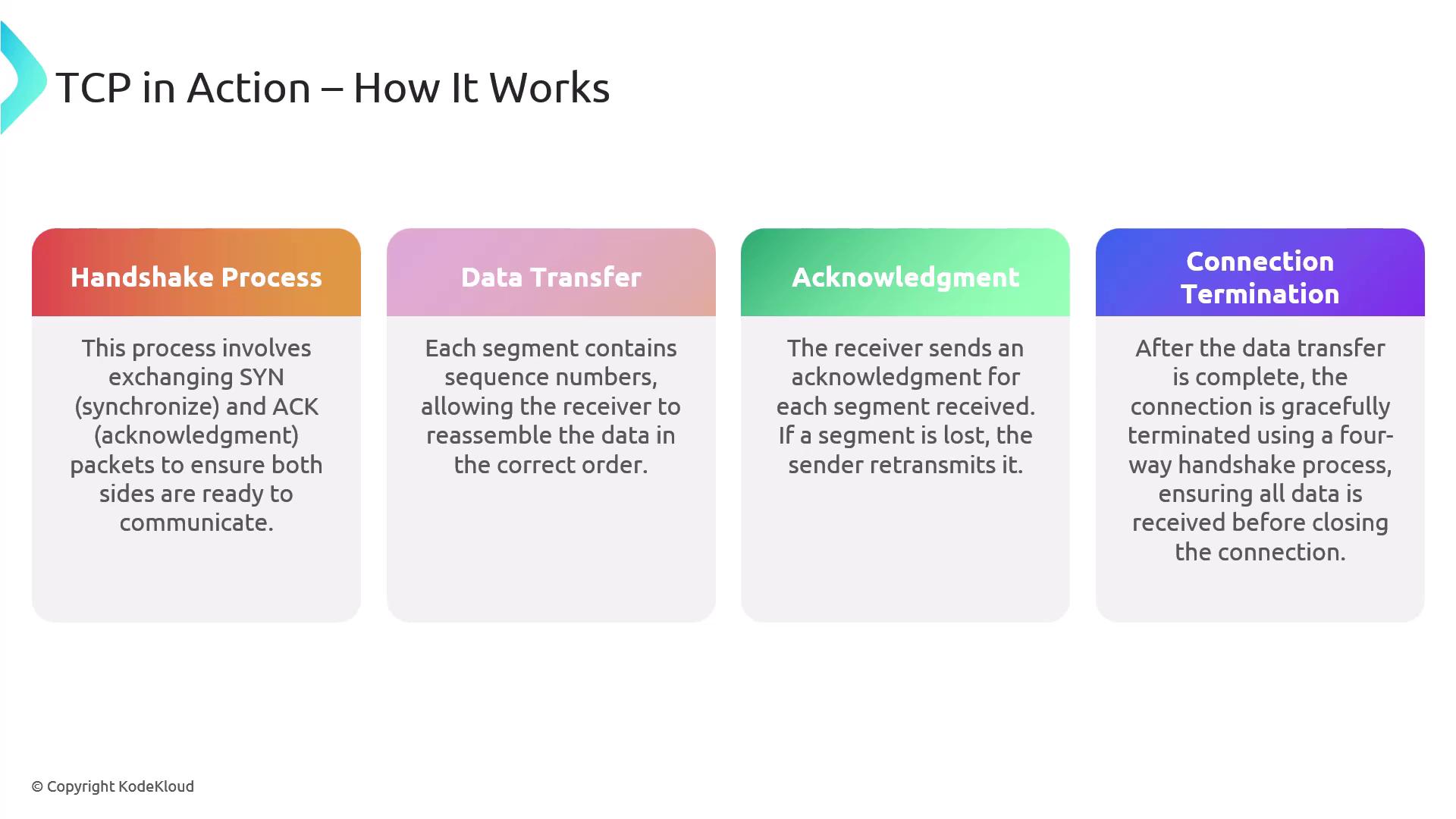
Handshake Process:
Before any data is sent, a three-way handshake is executed between the client and server. This involves the exchange of synchronization (SYN) and acknowledgment (ACK) packets to ensure both ends are ready to communicate. -
Data Transmission:
Once the connection is established, data is sent in units called segments. Sequence numbers are assigned to each segment for proper ordering at the receiver’s end, which acknowledges each received segment. Lost segments are retransmitted. -
Connection Termination:
After data exchange, the connection is gracefully terminated using a four-way handshake, ensuring that all data has been received before closure.
User Datagram Protocol (UDP)
UDP is a connectionless protocol that sends packets, known as datagrams, without establishing a prior connection. Its design is centered around speed and efficiency. The key characteristics of UDP include:-
Connectionless Communication:
No handshake is performed; data is sent immediately, significantly reducing latency. -
Unreliable Data Transfer:
There is no confirmation of data receipt, no guarantee of order, and no built-in error checking or retransmission. -
Low Overhead:
The simplified mechanism makes UDP faster, making it ideal for time-sensitive applications.
How UDP Operates
-
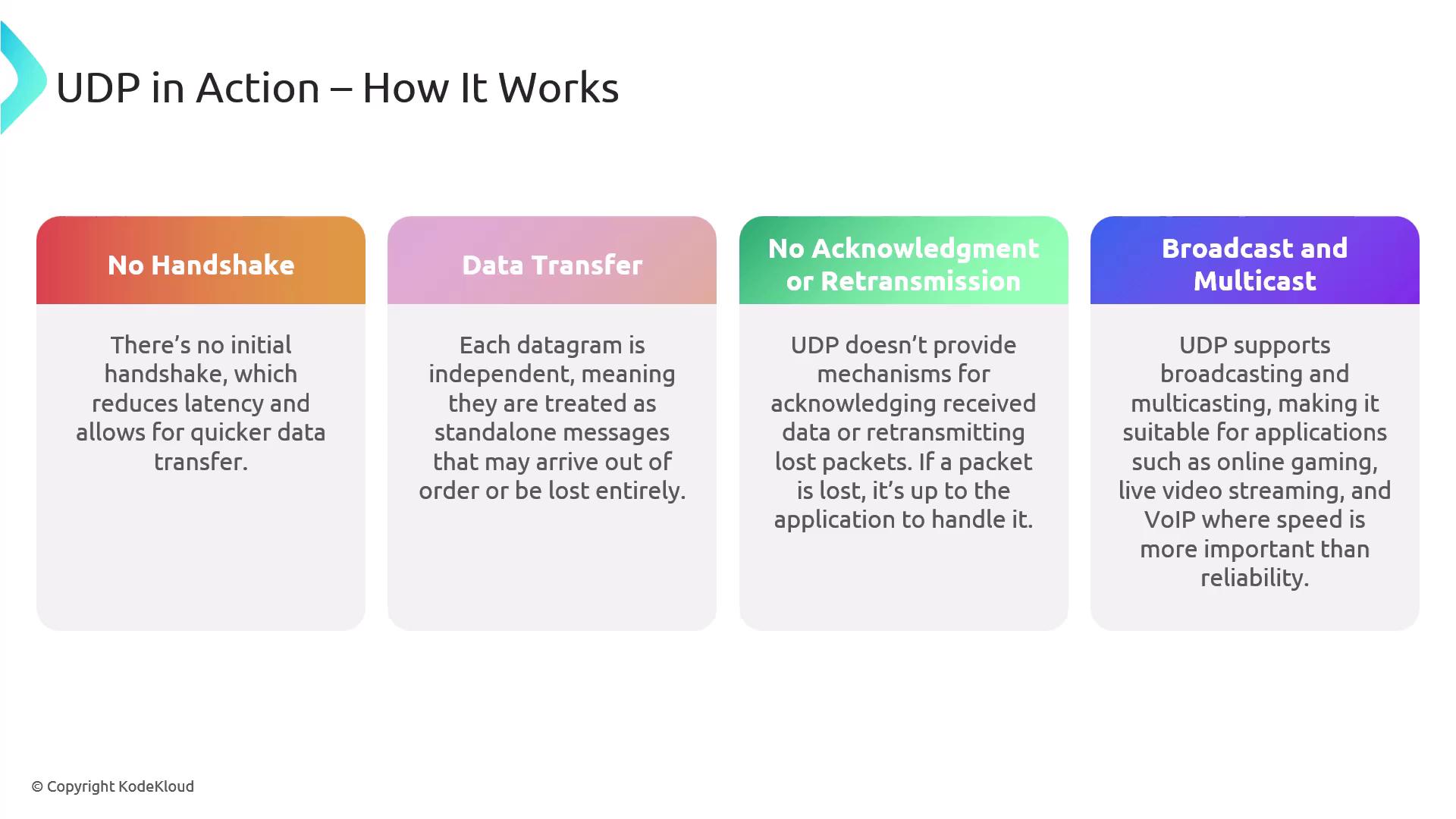
No Handshake:
Data is transmitted without any initial setup, optimizing for speed. -
Independent Datagrams:
Each packet is independent, meaning they might arrive out of order or not at all. -
No Acknowledgment or Retransmission:
Handling of lost packets is left to the application level. -
Broadcast and Multicast Support:
UDP facilitates sending data to multiple recipients simultaneously; ideal for online gaming, live streaming, and VoIP.
Comparing TCP and UDP
| Protocol | Connection Mode | Data Reliability | Overhead | Use Cases |
|---|---|---|---|---|
| TCP | Connection-oriented | Reliable, guarantees order | Higher due to handshaking | Web browsing, email, file transfer |
| UDP | Connectionless | Unreliable, unordered | Lower, faster | Online gaming, live streaming, VoIP |

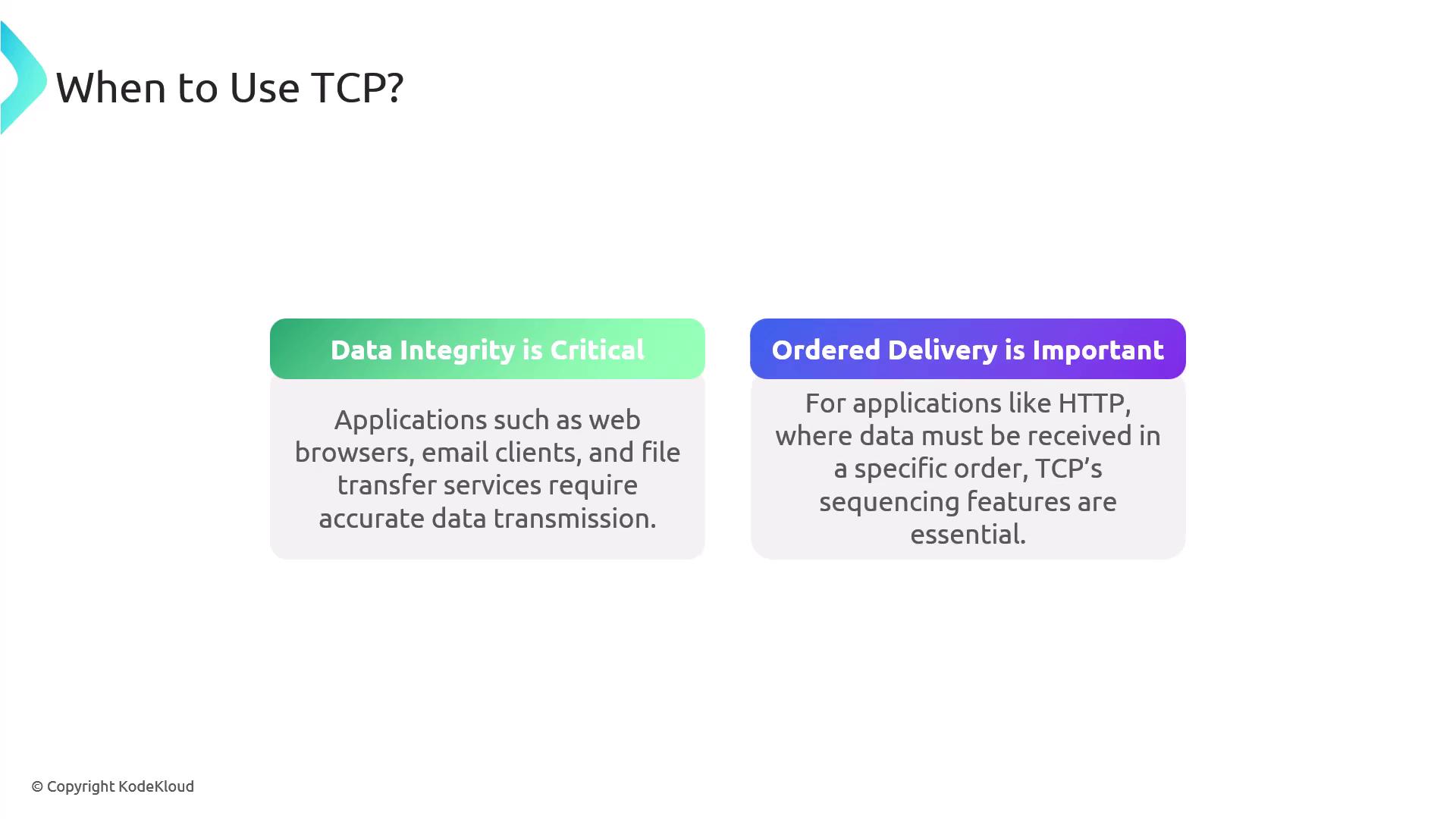
In summary, choose TCP when data integrity and sequential delivery are crucial, and opt for UDP when low latency and speed are prioritized, even if it means handling occasional data loss.