[Updated] AZ-104: Microsoft Azure Administrator
Administer Azure Storage
Storage Service Encryption SSE and Azure Disk Encryption ADE
This article explains two essential encryption solutions available in Azure that help secure your data at rest while ensuring compliance and performance: Storage Service Encryption (SSE) and Azure Disk Encryption (ADE).
Both encryption methods provide robust security measures, using industry-standard 256-bit AES encryption, with automatic encryption and decryption processes managed by Azure services. They also support customer control over encryption keys to meet specific regulatory and security requirements.
Storage Service Encryption (SSE)
Storage Service Encryption (SSE), also known as Server Side Encryption, automatically encrypts data as it is stored in Azure. This built-in service applies to Azure Disk, Blob, File, Queue, and Table services, ensuring that data is encrypted at rest and transparently decrypted when accessed.
Key Benefits of SSE
- Protection: All data stored in Azure is encrypted by default, ensuring that data at rest remains secure.
- Compliance: Organizations can meet strict security and regulatory requirements without developing custom encryption solutions.
- Robust Security: SSE employs 256-bit AES encryption along with automatic key and data management by the Storage Service.
Default Settings
By default, SSE is enabled on all storage accounts, and this setting cannot be disabled, ensuring consistent data protection.
Bring Your Own Keys (BYOK)
If you require full control over your encryption keys and their rotation, Azure supports the Bring Your Own Keys (BYOK) model. Simply create an Azure Key Vault to securely store your keys, and then configure your Storage Service to use these Customer Managed Keys for both encryption and decryption.
Azure Disk Encryption (ADE)
Azure Disk Encryption (ADE) secures the disks of your virtual machines (VMs) by encrypting both operating system (OS) and data disks. Without ADE, a snapshot VHD could be attached to another VM, potentially exposing sensitive information. ADE mitigates this risk by ensuring the disk is encrypted.
Key Features of ADE
- Comprehensive Coverage: ADE encrypts both OS and data disks for Windows and Linux VMs.
- Encryption Mechanisms: Utilizes BitLocker for Windows and dm-crypt for Linux.
- Key Management: Encryption keys are securely stored in Azure Key Vault.
- Access Control: Only the VM owner can access the encrypted data. If a VHD is downloaded and attached elsewhere without the corresponding keys, the data remains inaccessible.
- Backup Security: When using Azure Backup, encryption keys are backed up in the Recovery Services Vault, ensuring that all backups are also encrypted.
- Encryption Standard: Implements robust 256-bit encryption.
![]()
Performance Considerations
Encrypting both OS and data disks may cause a slight performance impact due to the encryption and decryption overhead. In CPU-intensive scenarios, consider encrypting only the data disk to optimize performance. Also, note that if "Encryption at Host" is enabled, ADE cannot be used because host-level encryption relies solely on platform-managed keys.
Additionally, Azure offers an "Encryption at Host" option. For further information on this feature, refer to Microsoft Azure Security Technologies (AZ-500).
Configuring Encryption in the Azure Portal
Azure provides a straightforward interface for configuring both SSE and ADE. Follow the steps below to set up encryption:
Configuring SSE for Storage Accounts
- Navigate to your Storage Account in the Azure Portal.
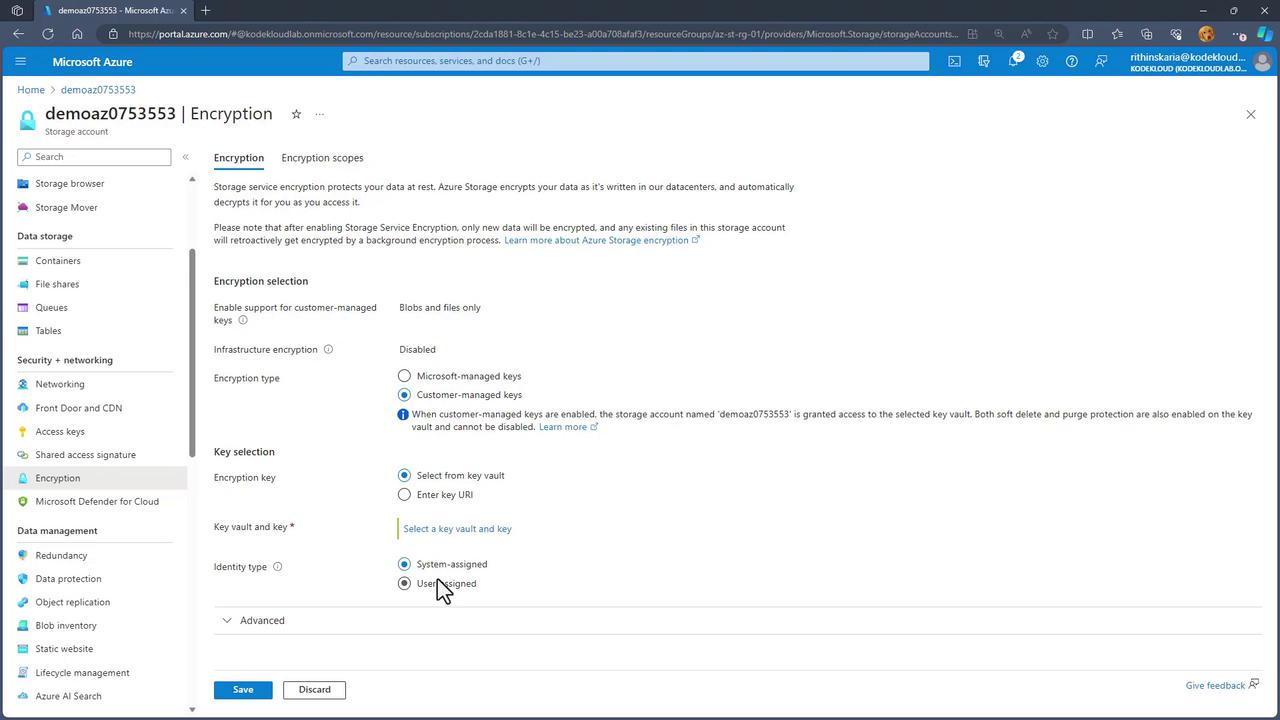
- Select the "Encryption" option to view the current encryption model.
- By default, Microsoft Managed Keys are used. If you prefer to use Customer Managed Keys for Blobs and Files, select your Azure Key Vault and assign the keys accordingly.
Enabling ADE on Virtual Machines
- Open your Virtual Machine settings in the Azure Portal.
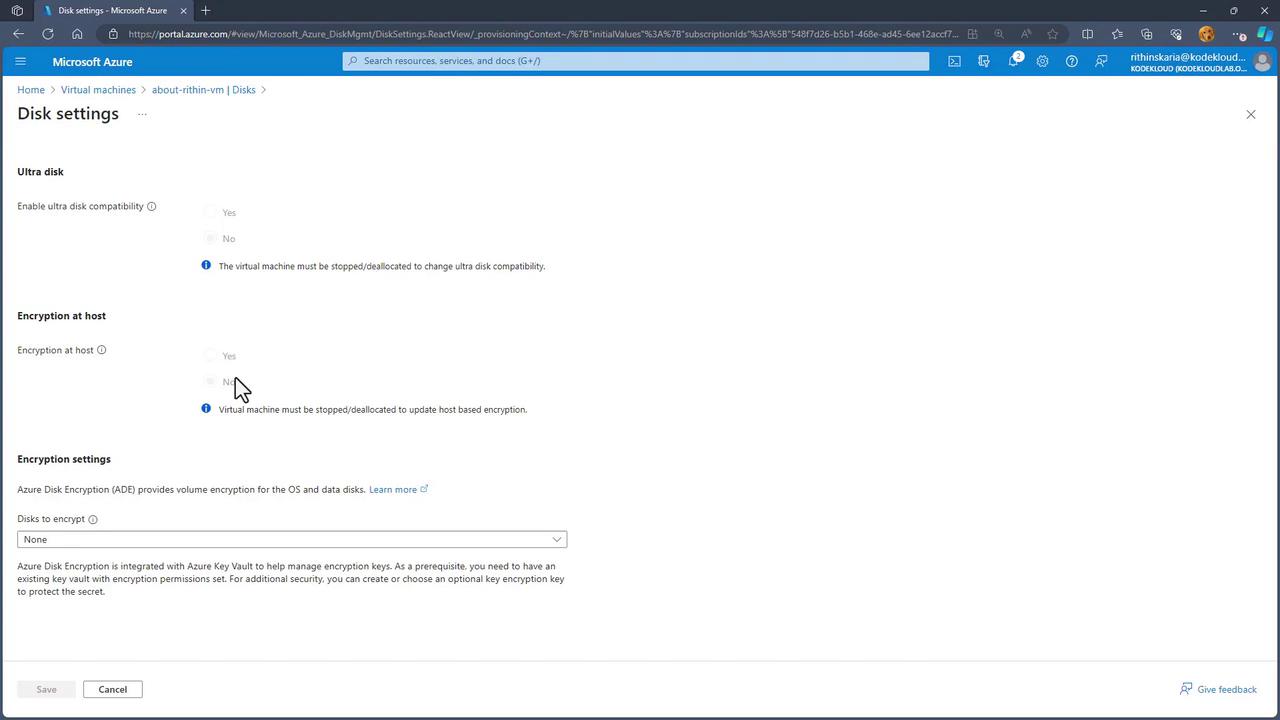
- Navigate to Disk > Additional Settings.
- Enable Azure Disk Encryption (ADE) and choose whether to encrypt the OS disk, data disk, or both.
- Note that updating the Azure Active Directory (AAD) configuration for your VM requires a reboot.
- If you wish to enable "Encryption at Host," ensure the VM is properly shut down during configuration.
Next Topic: Storage Security and Authorization
This concludes our detailed overview of Storage Service Encryption (SSE) and Azure Disk Encryption (ADE). In the next section, we will explore Storage Security and Authorization. For more Azure security best practices, check out the Azure Security Documentation.
Enhance your data protection strategy by implementing these encryption services to meet your organization's compliance and security goals.
Watch Video
Watch video content