Overview of Firewalls
Consider a server configured as a web server listening on port 443 for HTTPS requests. When a client sends a request to this port, the server responds accordingly. A firewall inspects traffic based on a set of predetermined rules, ensuring that only permitted data is allowed in or out. These rules are categorized as follows:- Inbound Rules: Govern incoming traffic.
- Outbound Rules: Regulate outgoing traffic.
-
Stateless Firewalls:
These firewalls do not remember established connections; hence, every packet (both inbound and outbound) must be explicitly allowed. -
Stateful Firewalls:
These track active connections, meaning that once an inbound request is permitted, the corresponding outbound response is automatically allowed.
Stateless Firewalls
When configuring a stateless firewall for a web server, you must set up explicit rules for both incoming and outgoing traffic. Consider the following configuration:-
Inbound Traffic:
- Permit incoming traffic on port 443.
-
Outbound Traffic:
- Allow responses to client requests. In a typical TCP connection, a client uses an ephemeral source port (usually in the range 1024-65535) to send a request to port 443.
- If the server initiates communication with another server (e.g., fetching updates on port 80), you should:
- Allow outbound traffic on port 80.
- Permit the return traffic on the ephemeral port range.
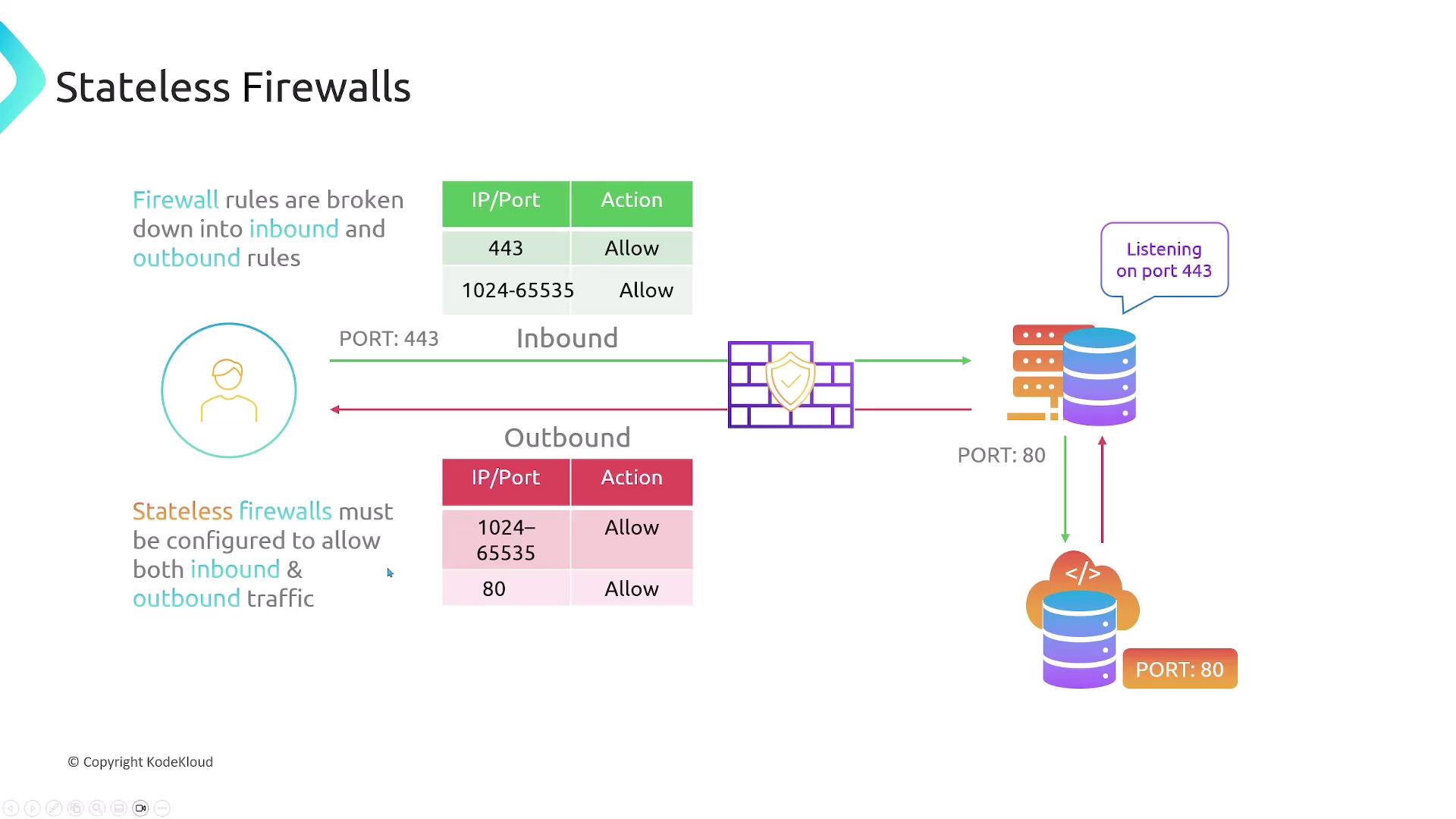
Ensure that every allowed request has a corresponding outbound rule, as failure to do so can result in blocked responses.
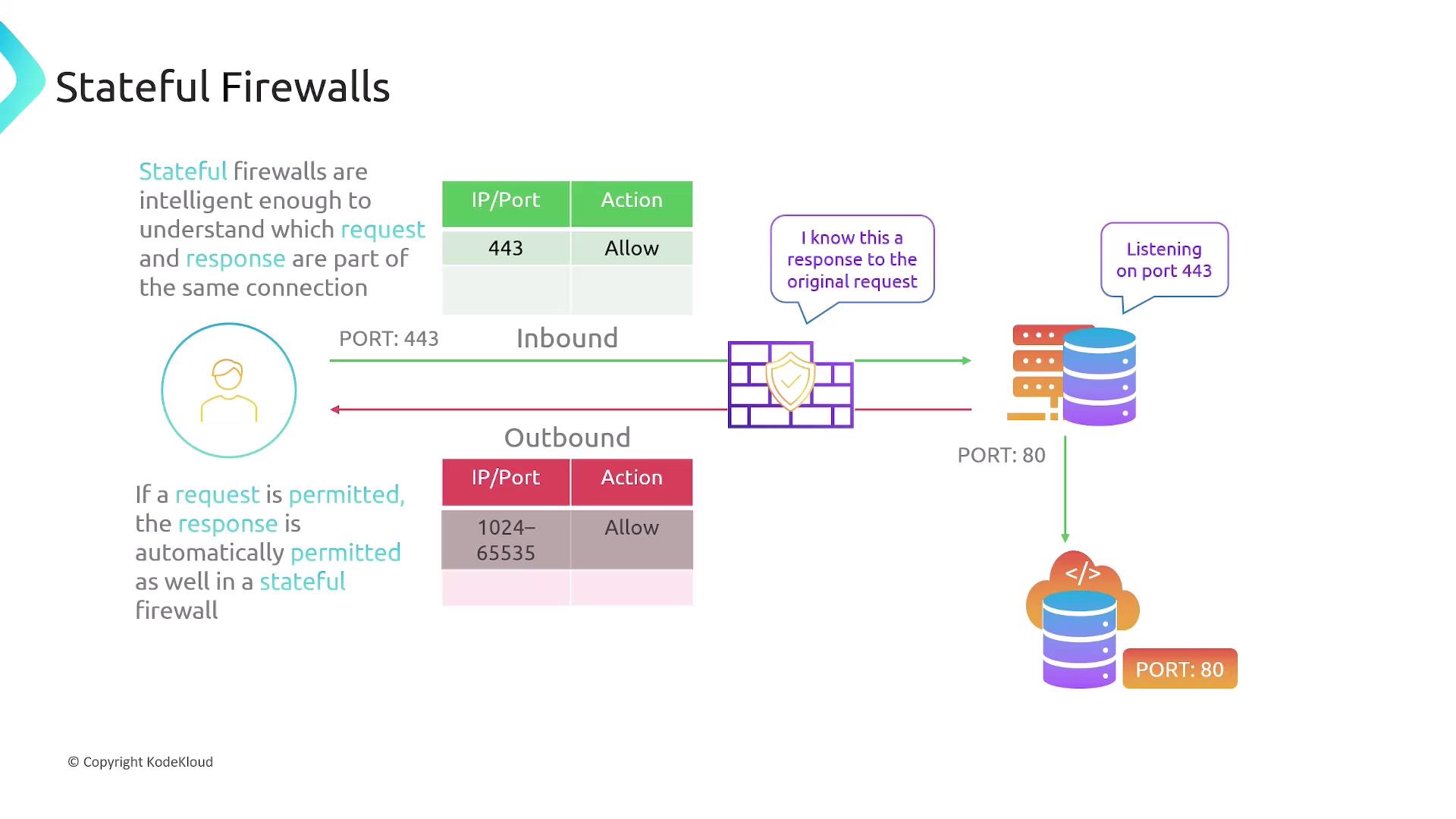
Stateful Firewalls
Stateful firewalls ease network management by tracking TCP sessions. The configuration for inbound traffic remains similar—such as allowing traffic on port 443—but outbound traffic is managed differently:- Once an inbound request on a permitted port (e.g., port 443) is allowed, the firewall automatically permits the outgoing response without requiring an explicit outbound rule.
- For outbound requests (like connecting to an update server on port 80), only the initial request needs to be permitted. The response is accommodated automatically because the firewall recognizes it as part of an established session.
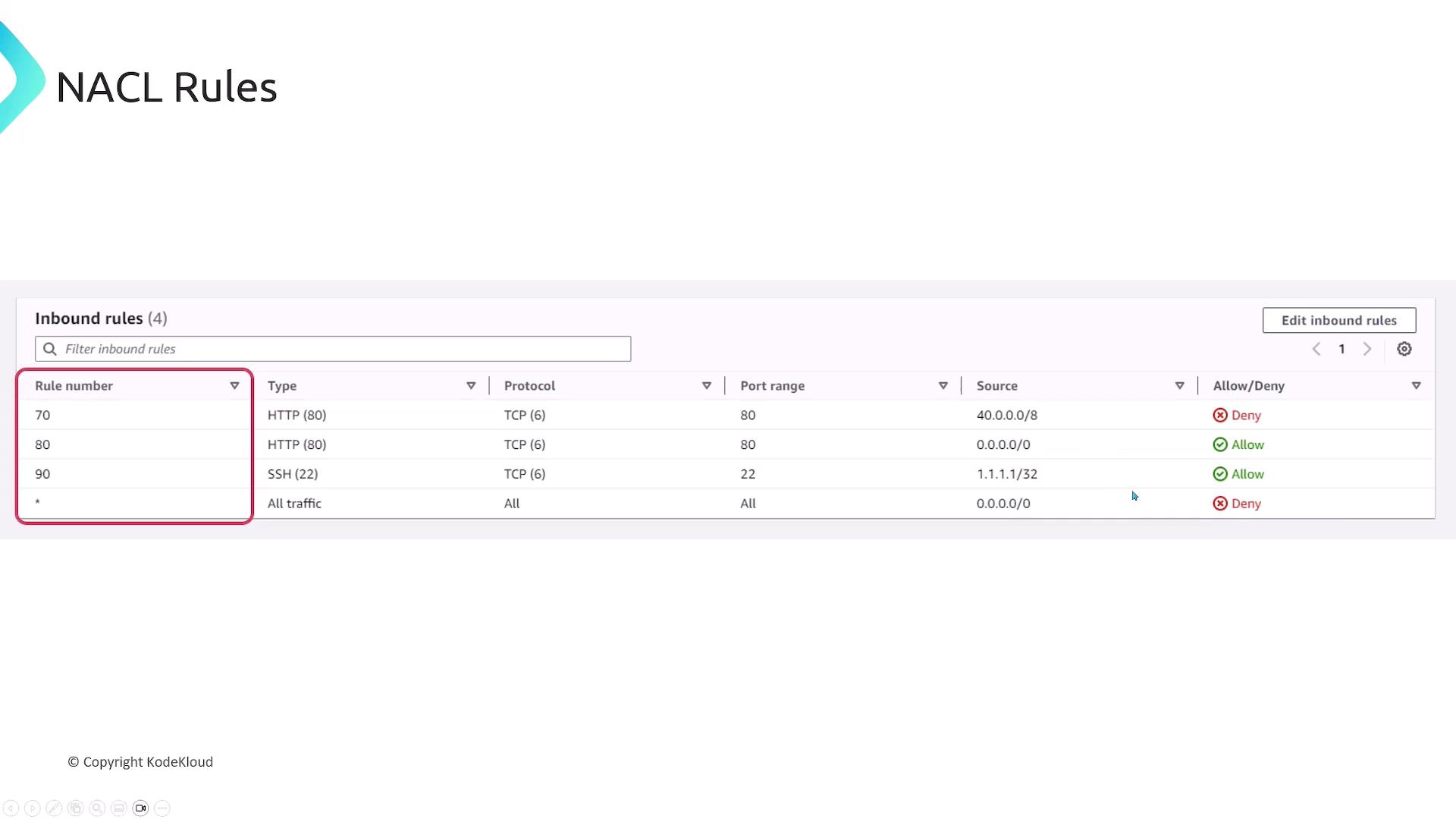
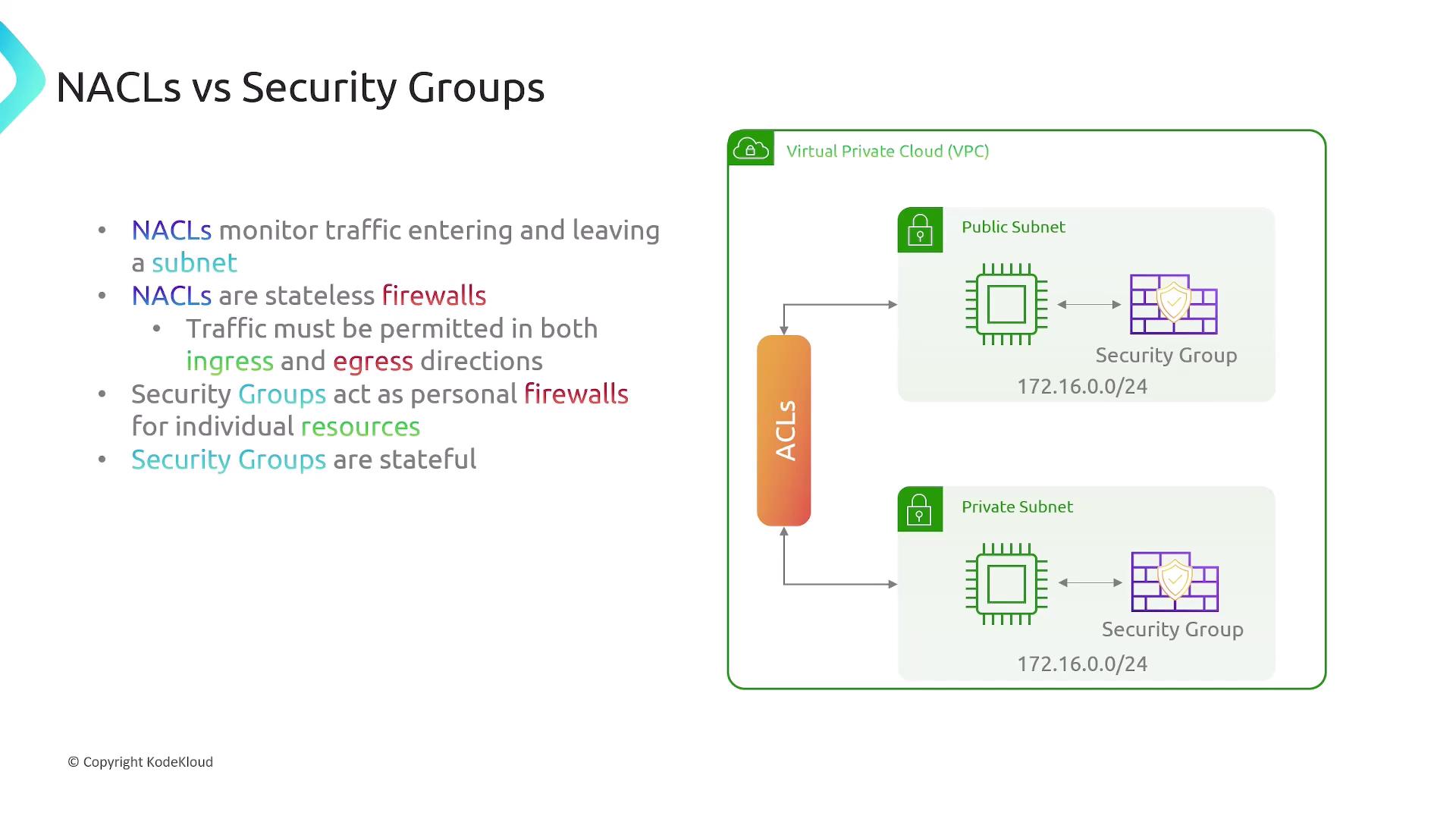
Network Access Control Lists (NACLs)
NACLs function at the subnet level within an AWS Virtual Private Cloud (VPC) and have the following characteristics:-
Traffic Filtering:
NACLs monitor and filter traffic entering and leaving a subnet. However, they do not inspect traffic within the same subnet. -
Stateless Operation:
Similar to stateless firewalls, rules in NACLs must be defined for both inbound and outbound traffic directions. -
Allow or Deny:
Unlike security groups, NACLs can be configured to either allow or deny traffic.
Security Groups
Security groups act as stateful firewalls at the resource level, protecting individual instances such as EC2, load balancers, or RDS instances. Key aspects include:-
Stateful Nature:
Traffic allowed for a request automatically permits its corresponding response. For instance, permitting HTTP traffic on port 80 automatically allows its reply. -
Default Behavior:
By default, security groups are designed to block all traffic. Adding a rule explicitly opens access for that specific traffic type. Importantly, security groups only support allow rules—they do not offer an option to explicitly deny traffic.
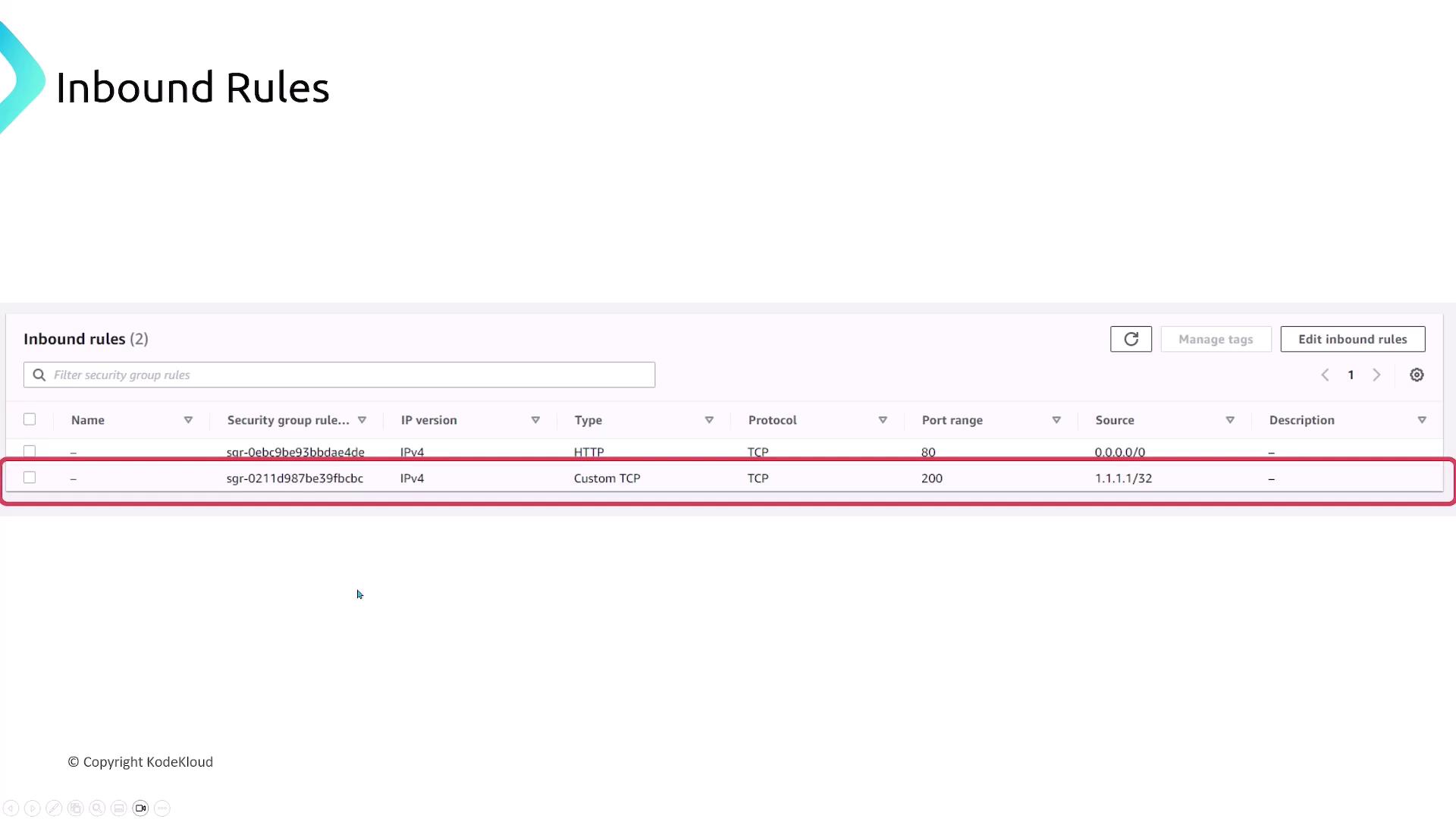
Configuring Inbound Rules
When setting up inbound rules in the AWS Console, you will typically interact with a configuration that includes:- Name: Descriptive label for the rule (optional).
- Rule ID: Unique identifier for the rule.
- IP Version: Indicates whether the rule applies to IPv4 or IPv6.
- Type, Protocol, and Port Range:
For example, selecting HTTP automatically sets the protocol to TCP and the port to 80. Custom configurations, such as “Custom TCP”, allow you to specify one or a range of ports (e.g., 200 or 200–300). - Source: Specifies the allowed IP range (e.g., 0.0.0.0/0 for public access or 1.1.1.1/32 for a specific IP).
- Description: An optional note explaining the rule’s purpose.
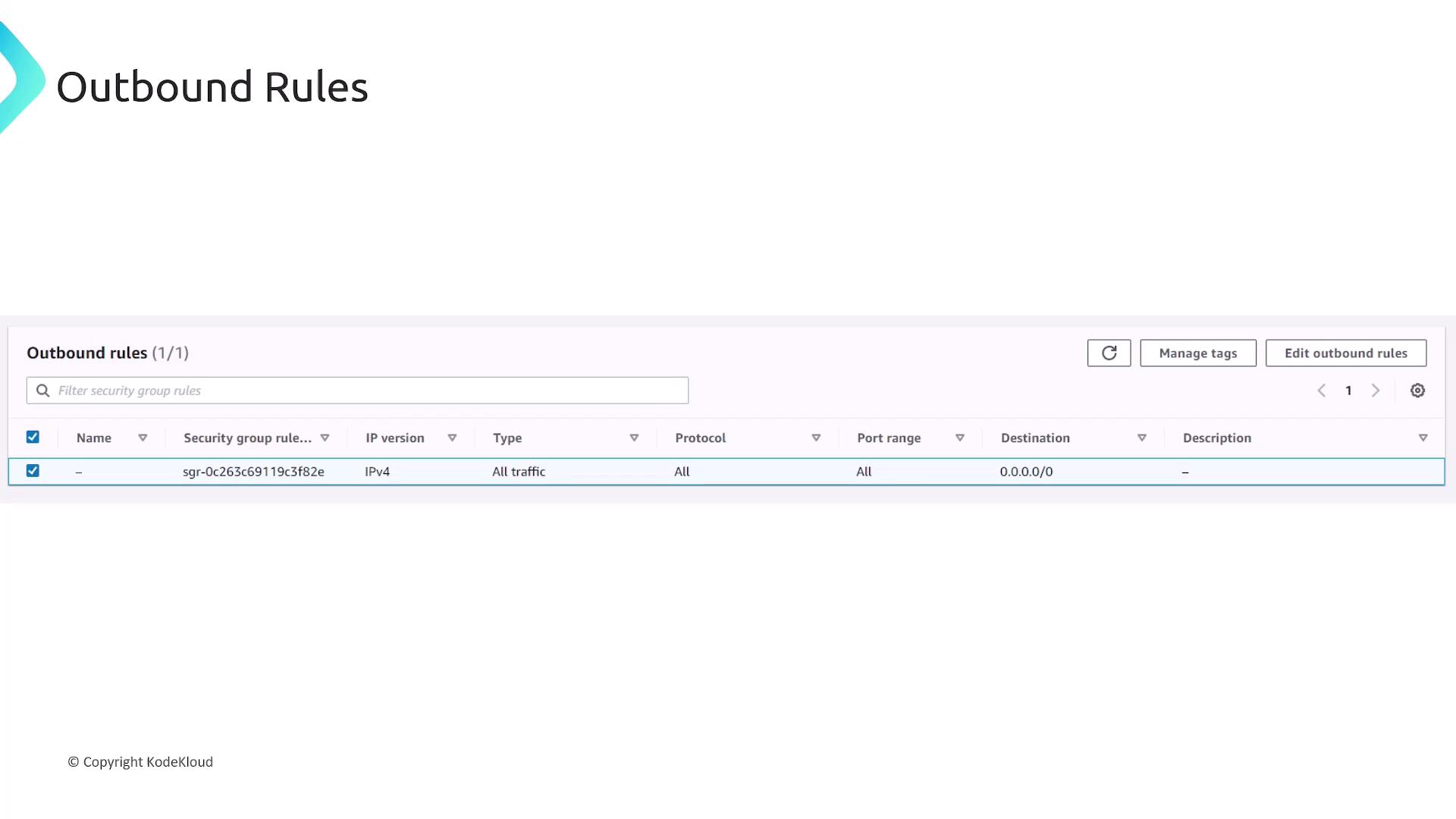
Configuring Outbound Rules
Similarly, outbound rules can be configured in the AWS Console. For instance, the default outbound setting for a security group permits all traffic:- Type: All traffic
- Protocol: All (TCP, UDP, ICMP, etc.)
- Port Range: All ports
- Destination: 0.0.0.0/0 (allowing traffic to any destination)
If no rules are defined for a security group, the default behavior is to block all traffic. Always ensure that the necessary rules are in place to meet your access requirements.
Comparing NACLs and Security Groups
Below is a summary comparison between NACLs and security groups:| Feature | Network ACLs (NACLs) | Security Groups |
|---|---|---|
| Operation Level | Subnet-level | Resource-level (EC2, load balancers, RDS, etc.) |
| Statefulness | Stateless – explicit rules required for inbound and outbound traffic | Stateful – response traffic is automatically allowed |
| Traffic Management | Can allow or deny traffic | Only allows traffic; implicit deny for everything else |
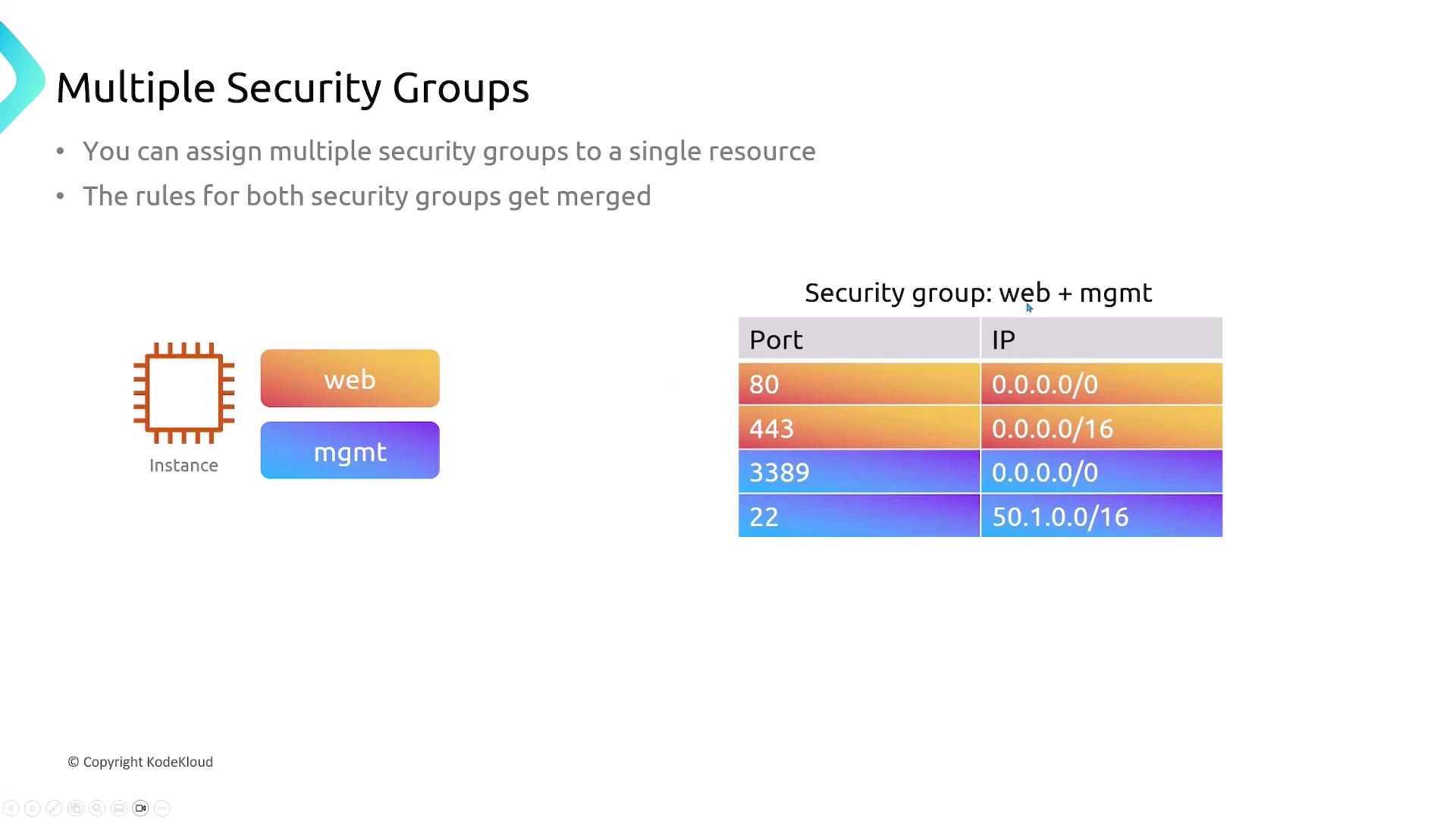
| Rule Combination | Rules are applied per subnet; each subnet associates with one NACL, though a single NACL can be attached to multiple subnets | Multiple security groups can be attached to a single resource; rules from all groups are merged |
| Default Behavior | No default rules; all rules must be explicitly defined | By default, blocks all traffic until rules are added |
Additional Considerations
-
VPC and Subnet Association:
Every subnet within a VPC must be associated with a network ACL, and although a single NACL can cover multiple subnets, each subnet can only be linked with one NACL at any given time. -
Unfiltered AWS-Specific Traffic:
NACLs do not filter certain AWS-specific communications, including:- Amazon DNS and DHCP traffic
- EC2 instance metadata and metadata endpoints
- License activation for Windows instances
- Amazon Time Sync Services
- Reserved IP addresses used by the default VPC router

Summary
-
Stateless Firewalls:
Require explicit permissions for both inbound and outbound traffic. -
Stateful Firewalls:
Track sessions so that when an inbound request is allowed, the corresponding outbound response is automatically permitted. -
Network ACLs:
- Operate at the subnet level.
- Are stateless; require rules for both directions.
- Can explicitly allow or deny traffic.
-
Security Groups:
- Protect individual resources.
- Are stateful; automatically allow responses.
- Only support allow rules, and rules from different groups merge when applied to a single resource.