Rollback Triggers
CloudFormation uses rollback triggers powered by CloudWatch alarms to monitor stack stability. If a resource fails to provision correctly—say, a web server does not start—the service automatically rolls back changes to maintain a stable environment. This design helps prevent unexpected resource usage costs resulting from partially deployed configurations. Additionally, when using change sets, you can disable this automatic rollback to freeze the state for troubleshooting, or if you plan to rebuild the entire stack later.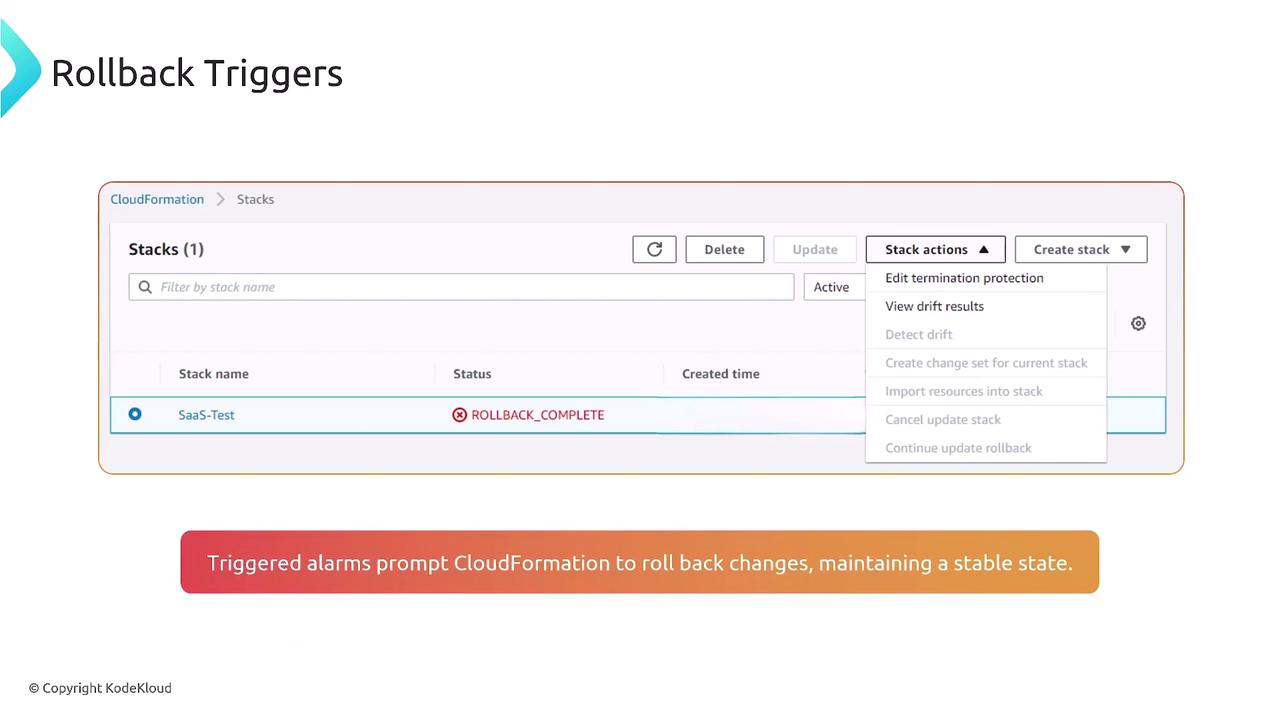
Drift Detection
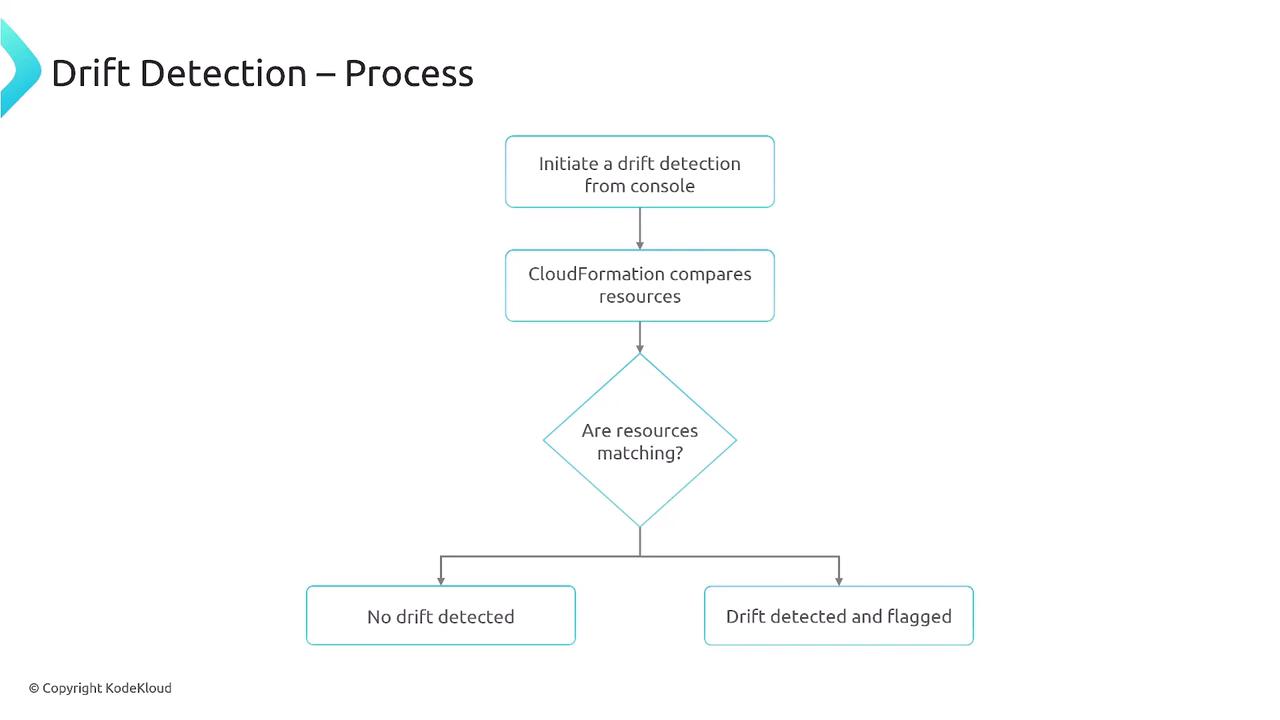
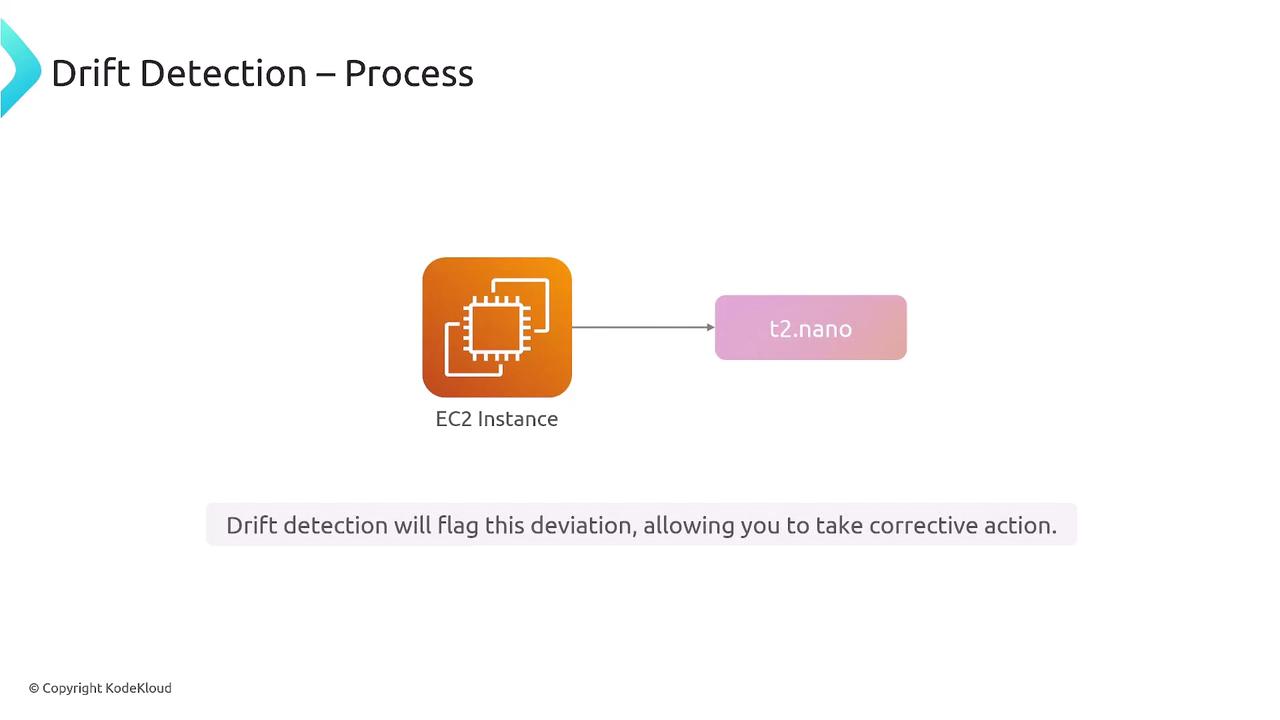
Drift detection compares your CloudFormation template with the current state of your AWS resources. This feature is particularly useful for identifying modifications made manually or outside of CloudFormation management. Consider an EC2 instance that was initially set to a T2 micro but later altered to a T2 nano. Drift detection will flag this discrepancy. The JSON examples below display the expected configuration versus the actual configuration: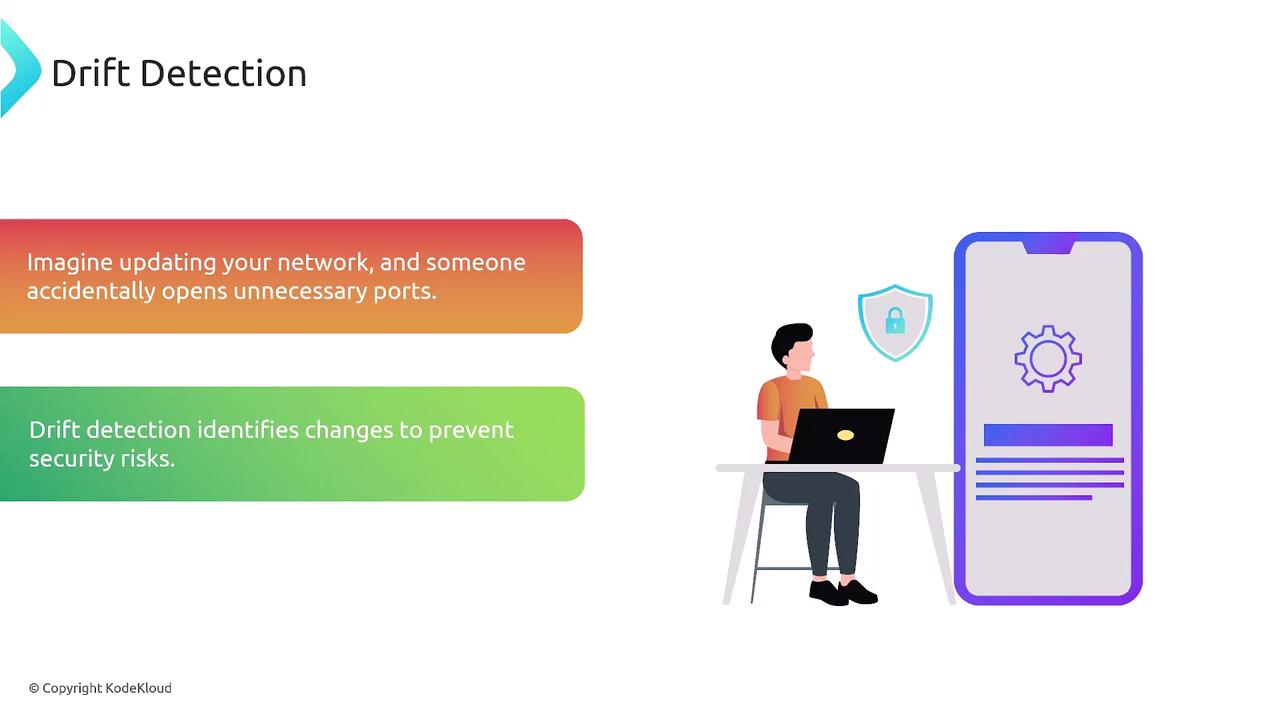
Dependency Handling
CloudFormation enables you to control the sequence in which resources are created by specifying dependencies within your template. For instance, you can ensure that a database is provisioned before an EC2 instance by using the “DependsOn” attribute. Explicitly declaring dependencies avoids potential conflicts or errors that might arise when CloudFormation guesses the creation order. This is critical, especially in enterprise environments where resource creation order must follow strict policies.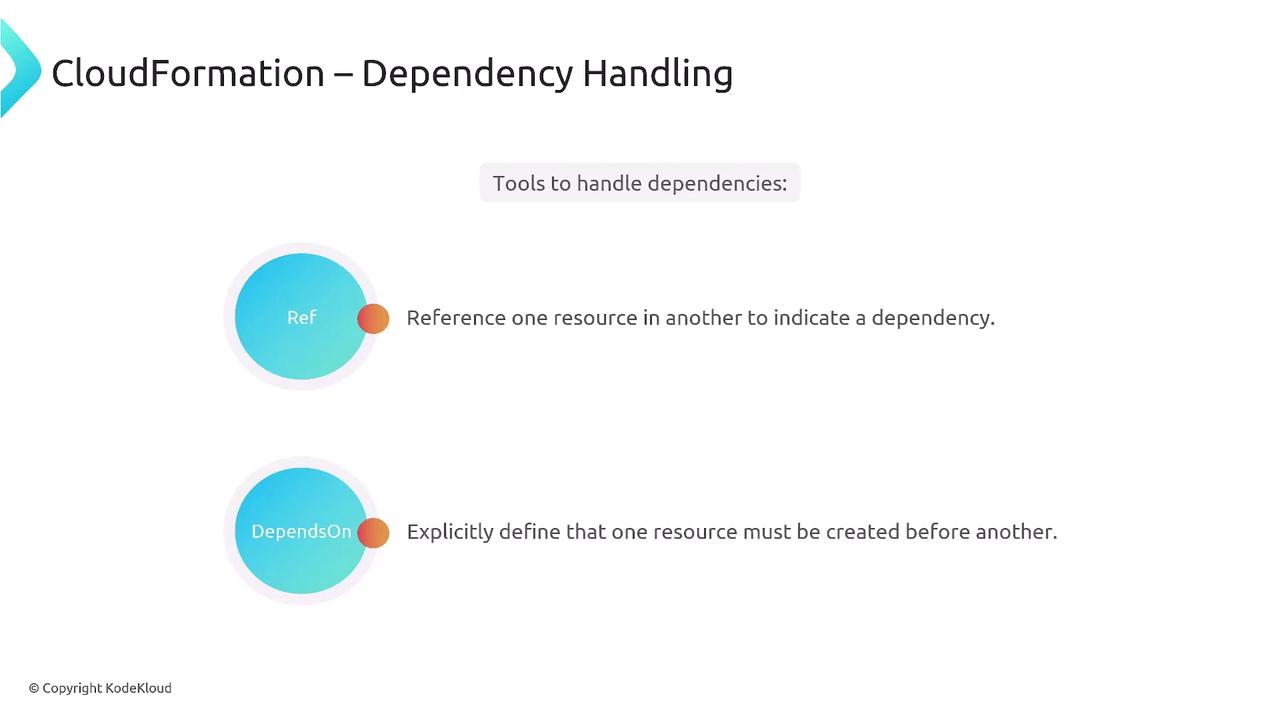
Resource Import
CloudFormation makes it possible to import existing resources into a new or existing stack. Rather than recreating resources from scratch, you can integrate them into a managed stack directly from the AWS console. This simplification streamlines tracking, drift detection, and overall infrastructure management. For example, if you have manually created RDS instances, you can import them into CloudFormation. This process reads their configurations and integrates them into a template for easier management.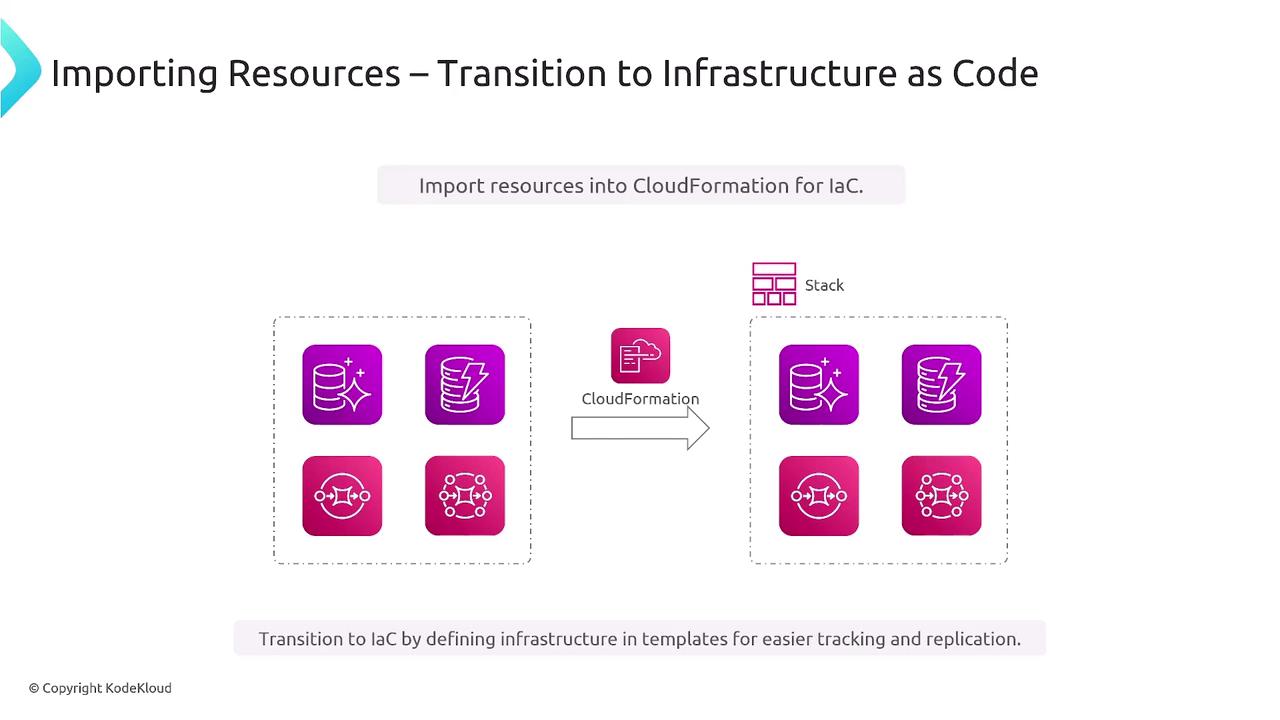

Nested Stacks
Nested stacks allow for the modularization of CloudFormation templates by splitting them into smaller, independent stacks for different layers of your infrastructure. This approach enables teams to work autonomously while maintaining a cohesive overall architecture. However, note that nested stacks must be stored in S3 and require broad permissions during creation. Also, an error in a parent stack could affect all nested stacks.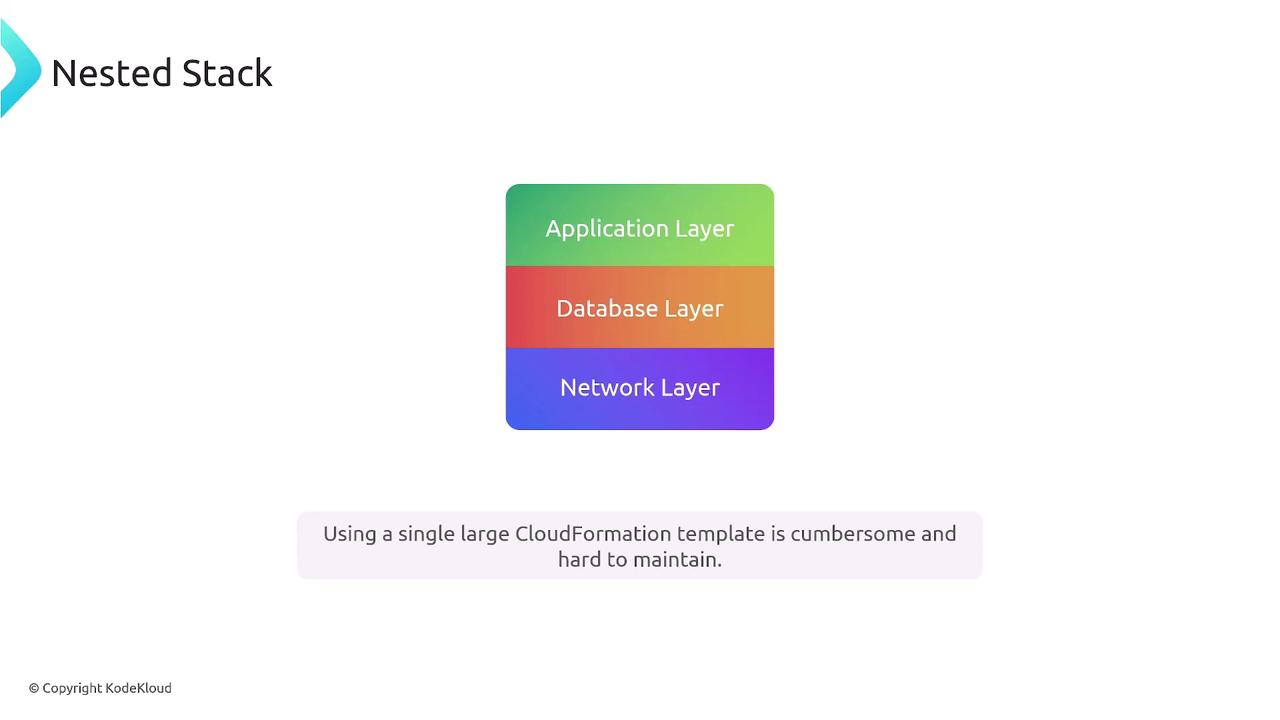
Cross-Stack References Example
Consider the following YAML snippet where one stack exports a subnet ID for public web servers: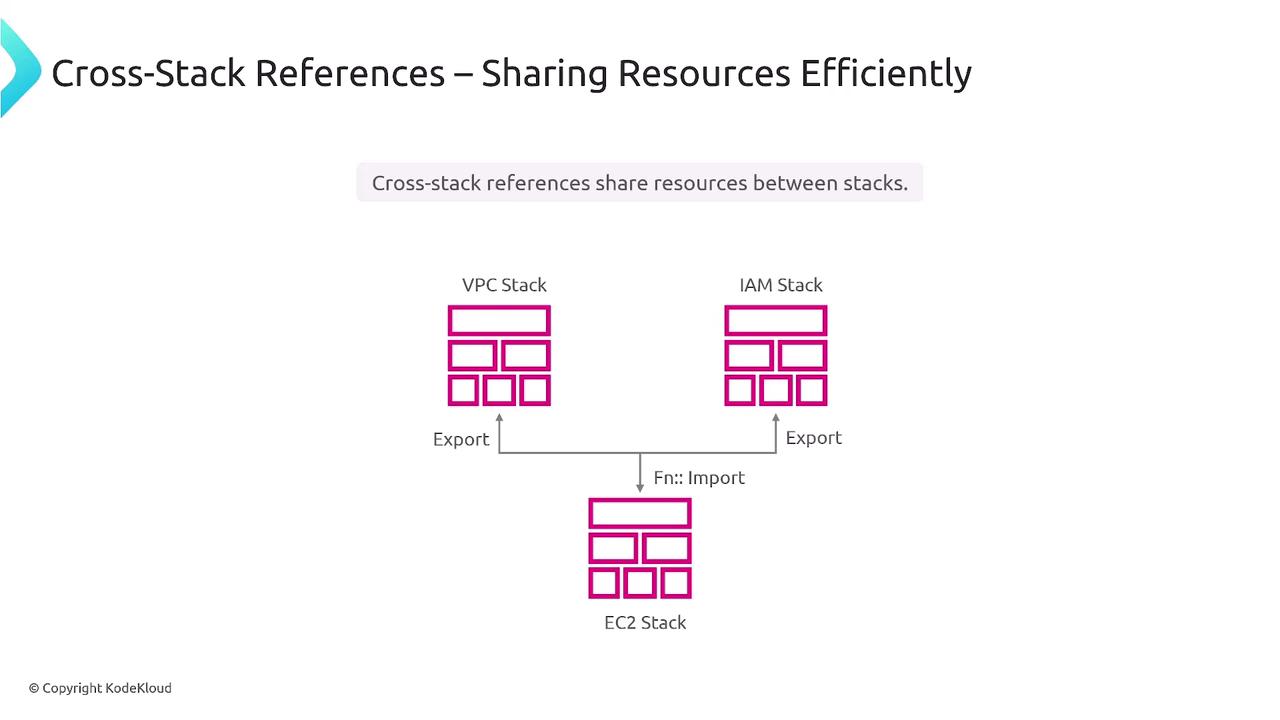
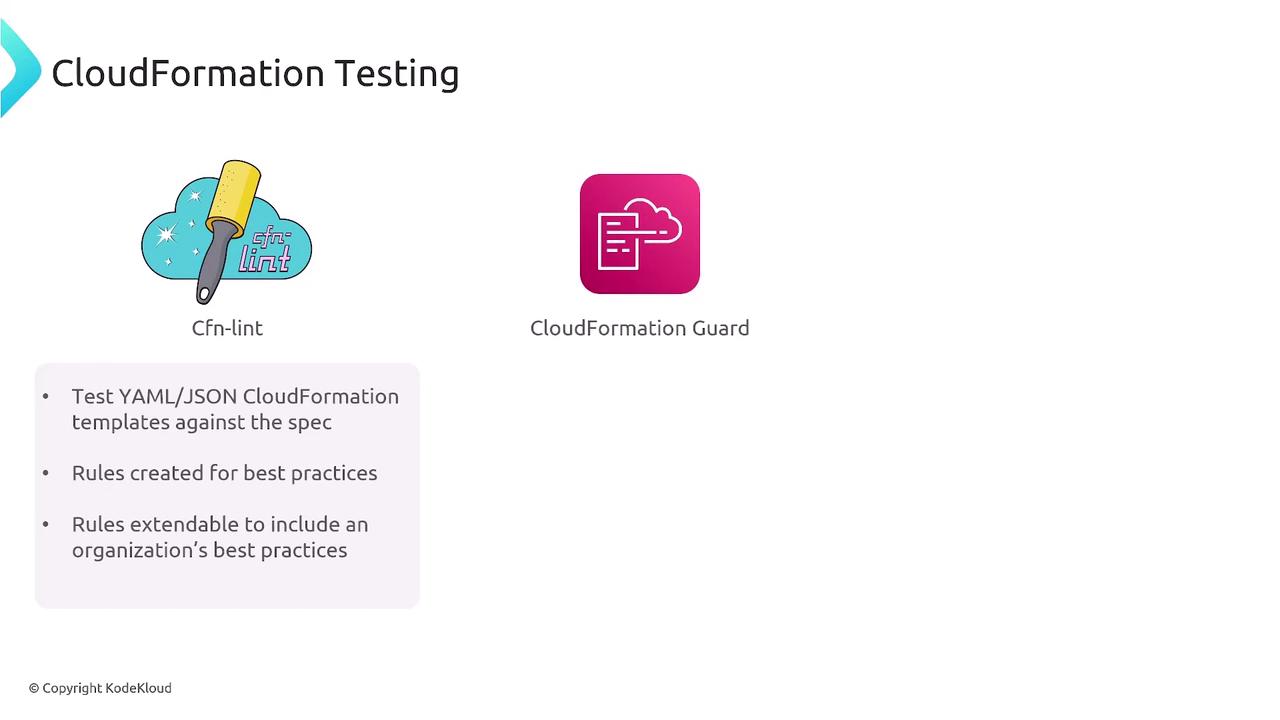
CloudFormation Testing
There are several tools available to test your CloudFormation templates and ensure they adhere to best practices:- CFN Lint: A linter that checks YAML/JSON templates for syntax errors and compliance with common best practices.
- CloudFormation Guard: A tool that validates templates against custom rules defined in a domain-specific language, allowing you to enforce organizational policies.
- TaskCat: An end-to-end testing tool that deploys CloudFormation templates across multiple regions.
TaskCat is not part of exam materials; however, CFN Lint and CloudFormation Guard are widely recognized for their effectiveness.
CI/CD with CloudFormation
Integrating CloudFormation with CI/CD pipelines can enhance your deployment processes significantly. Whether using GitHub, Bamboo, or other version control systems, you can leverage AWS CodePipeline (or similar tools) to trigger CodeBuild actions that validate and deploy CloudFormation stacks automatically. This practice ensures version control, automated deployments, and consistency across environments while facilitating rapid iteration during development.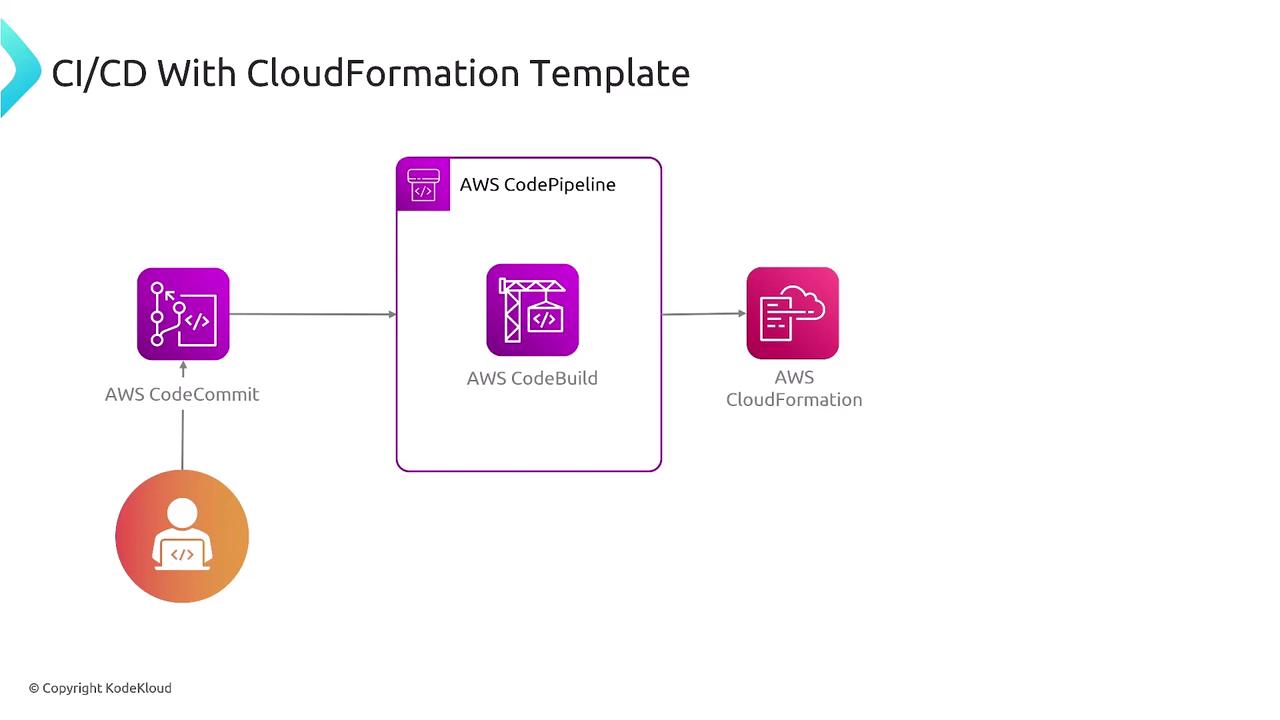
In summary, leveraging features such as rollback triggers, drift detection, dependency handling, resource import, nested stacks, cross-stack references, dedicated testing tools, and CI/CD integrations with CloudFormation can dramatically improve operational efficiency and infrastructure reliability. These practices not only aid in exam preparation but are also vital for real-world deployments. Thanks for reading.