AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Implementing IAM Features MFA Password Policies and Roles
Welcome to this comprehensive guide on IAM features in AWS. In this lesson, we explore multi-factor authentication (MFA), password policies, and roles by drawing parallels with a castle’s defense system. Imagine a castle where the main gate is the first line of defense: you need the right key to enter. For added security, a moat (requiring a special tool like a boat or bridge) must be crossed, and security guards verify your identity as an extra layer of protection.
Multi-Factor Authentication (MFA)
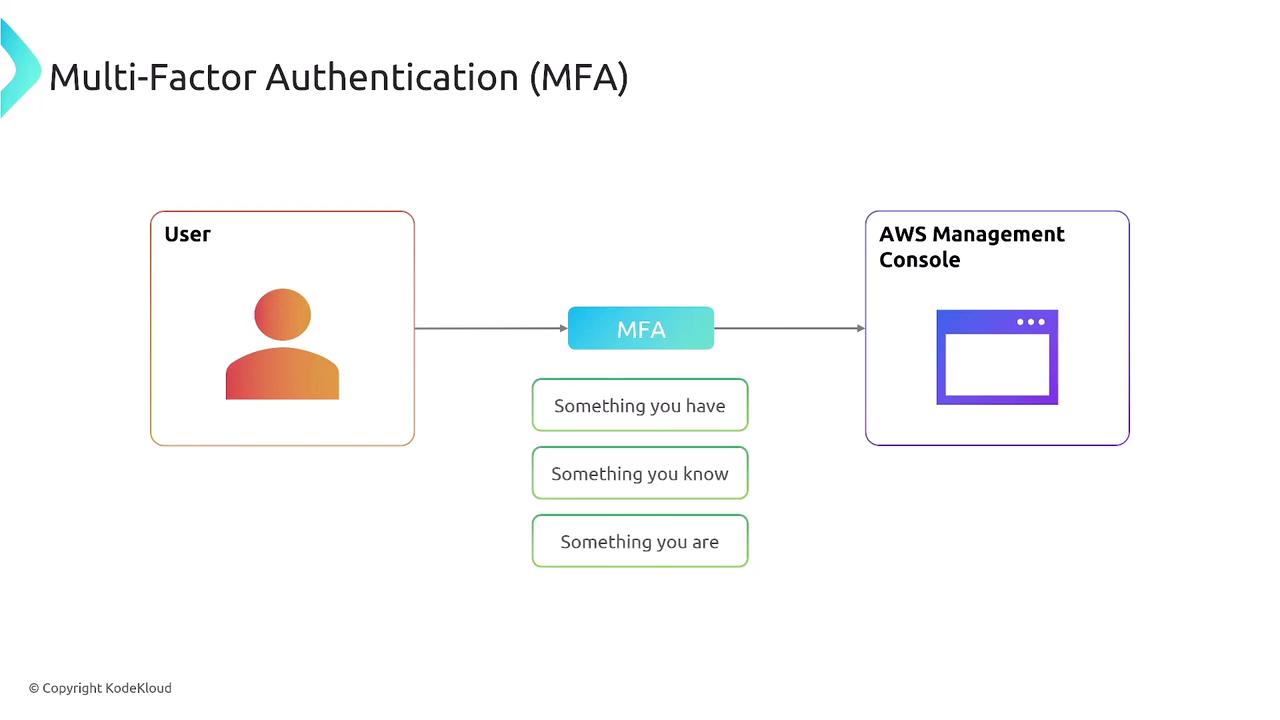
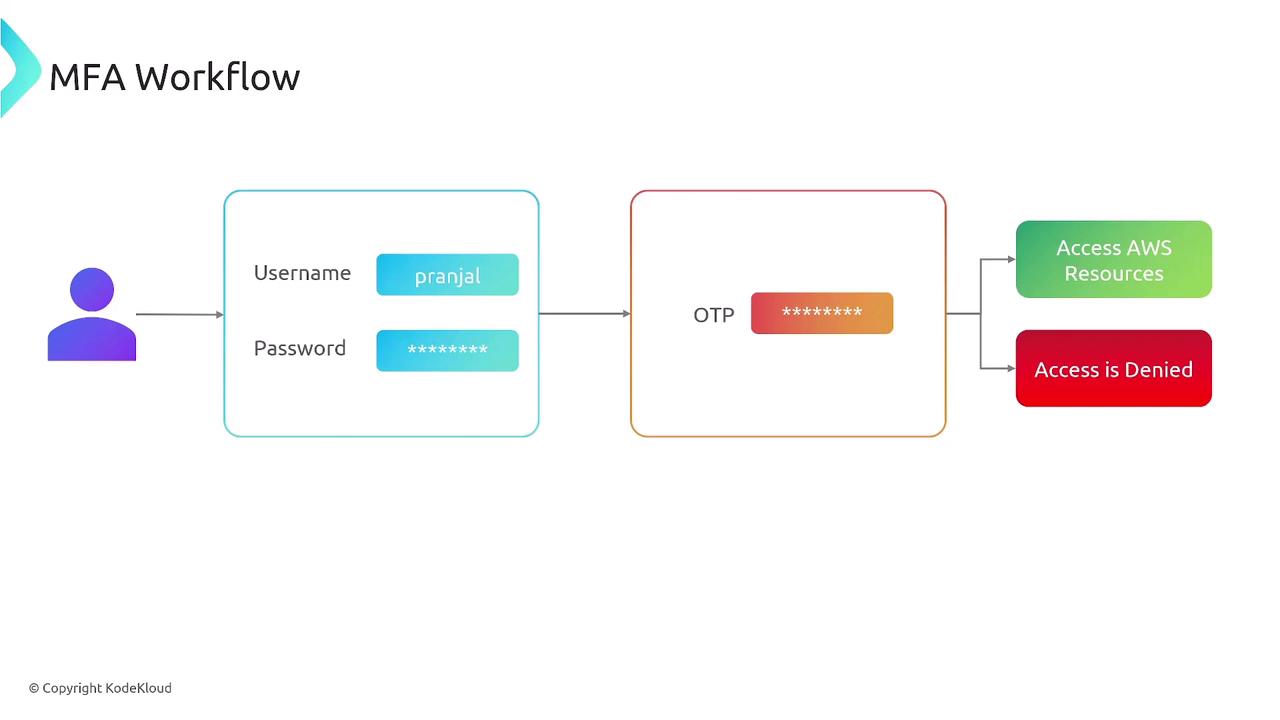
Multi-factor authentication goes beyond using just a username and password. Even if an unauthorized user discovers a password, MFA requires an additional factor—something the user has, knows, or is—to gain access. This extra security layer ensures that only authorized users access the AWS Management Console or resources programmatically.
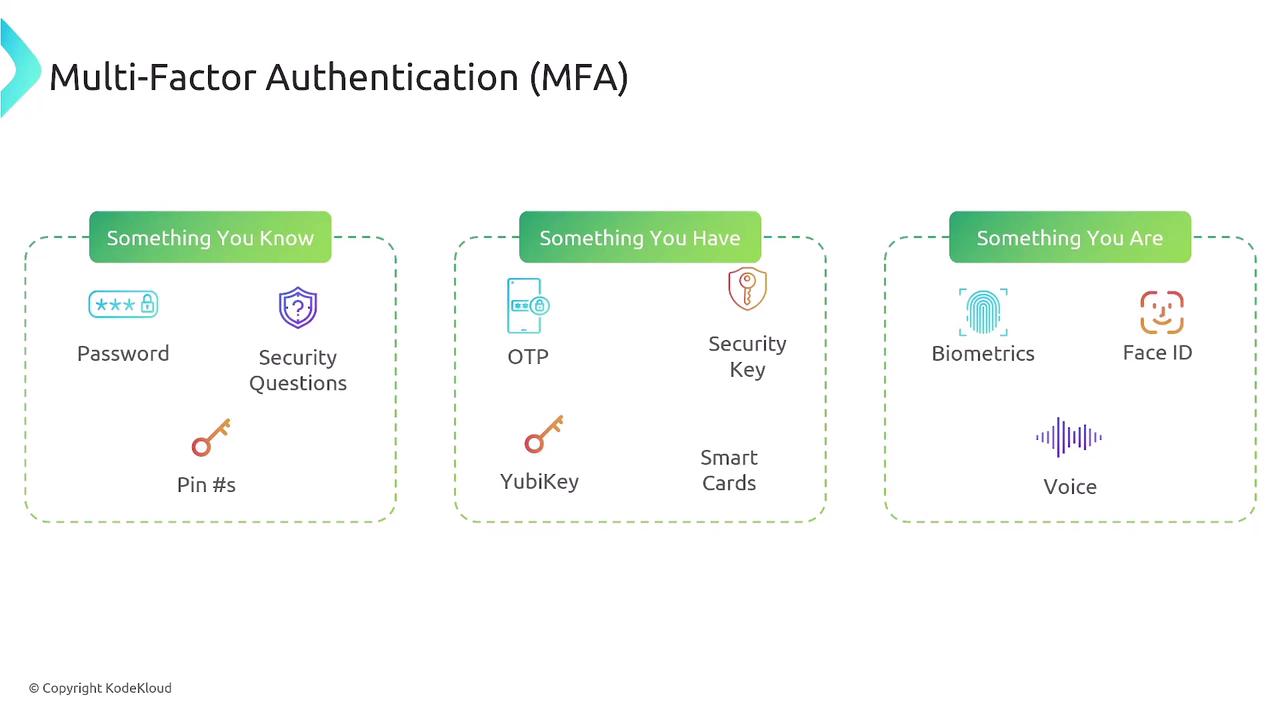
Some common MFA factors include:
- Something you have: An encryption key, one-time password (OTP) sent to your phone, or a physical security key.
- Something you know: Your password, answers to security questions, or a PIN.
- Something you are: Biometrics such as facial recognition, voice ID, or retinal scans.
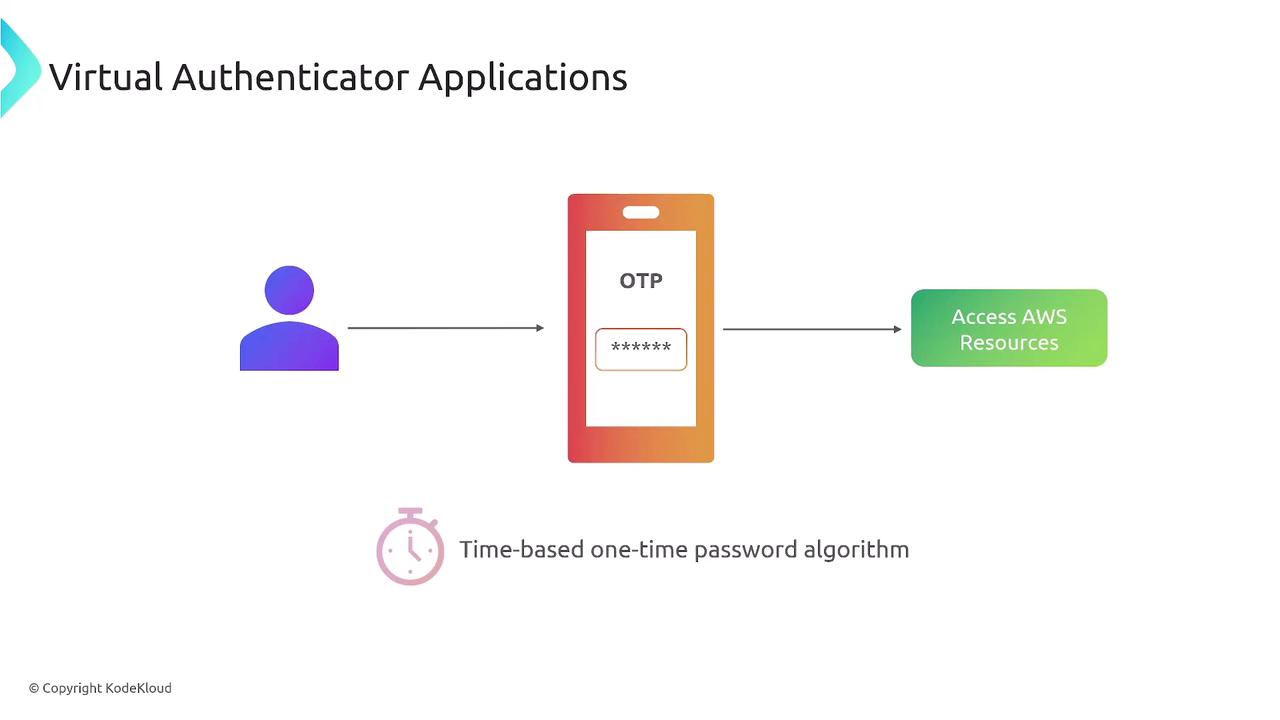
MFA enhances security by reducing the risks associated with phishing and social engineering attacks. It also helps meet regulatory standards such as GDPR, HIPAA, and PCI DSS for safeguarding sensitive data. Typically, after entering a username and password, users receive an OTP via their smartphone or generate one using a virtual authenticator app (such as Google Authenticator, Microsoft Authenticator, or other TOTP solutions).
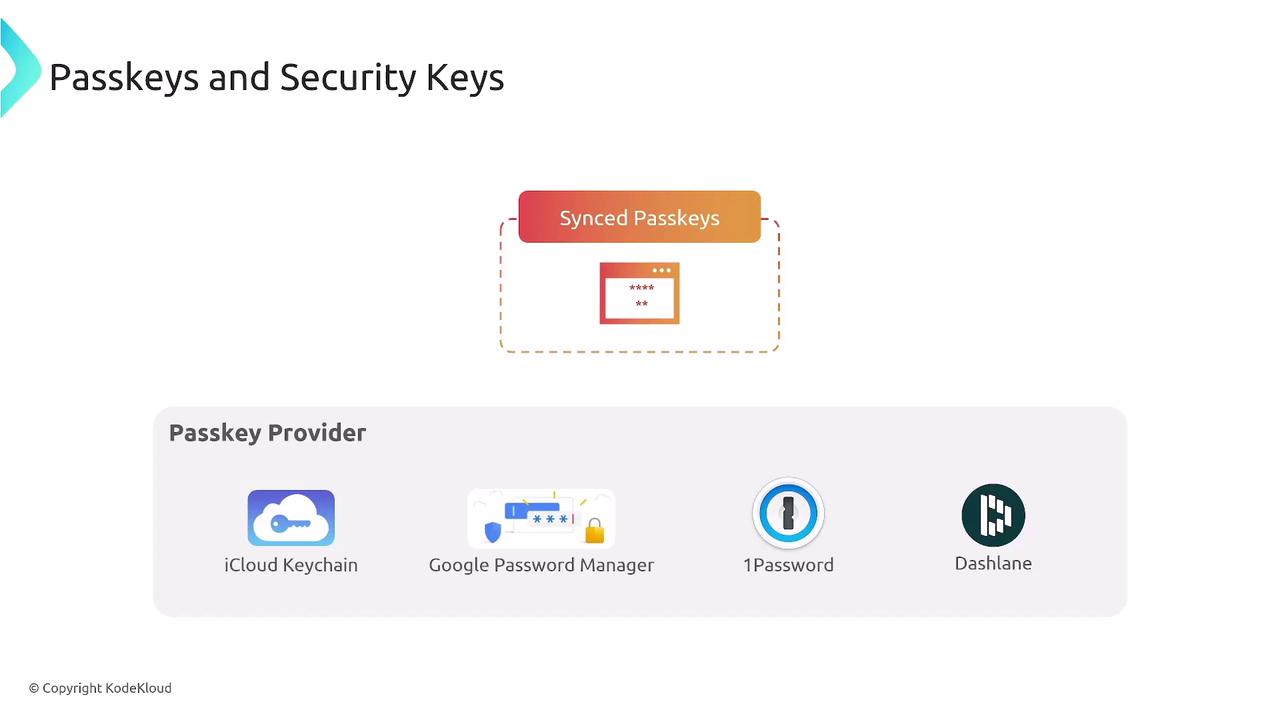
Various devices and methods can implement MFA. These include passkeys, physical security keys, and virtual authenticator apps:
- Passkeys: A new technology where encryption keys are stored in a personal keychain (managed by services like iCloud Keychain, Google Password Manager, 1Password, or Dashlane).
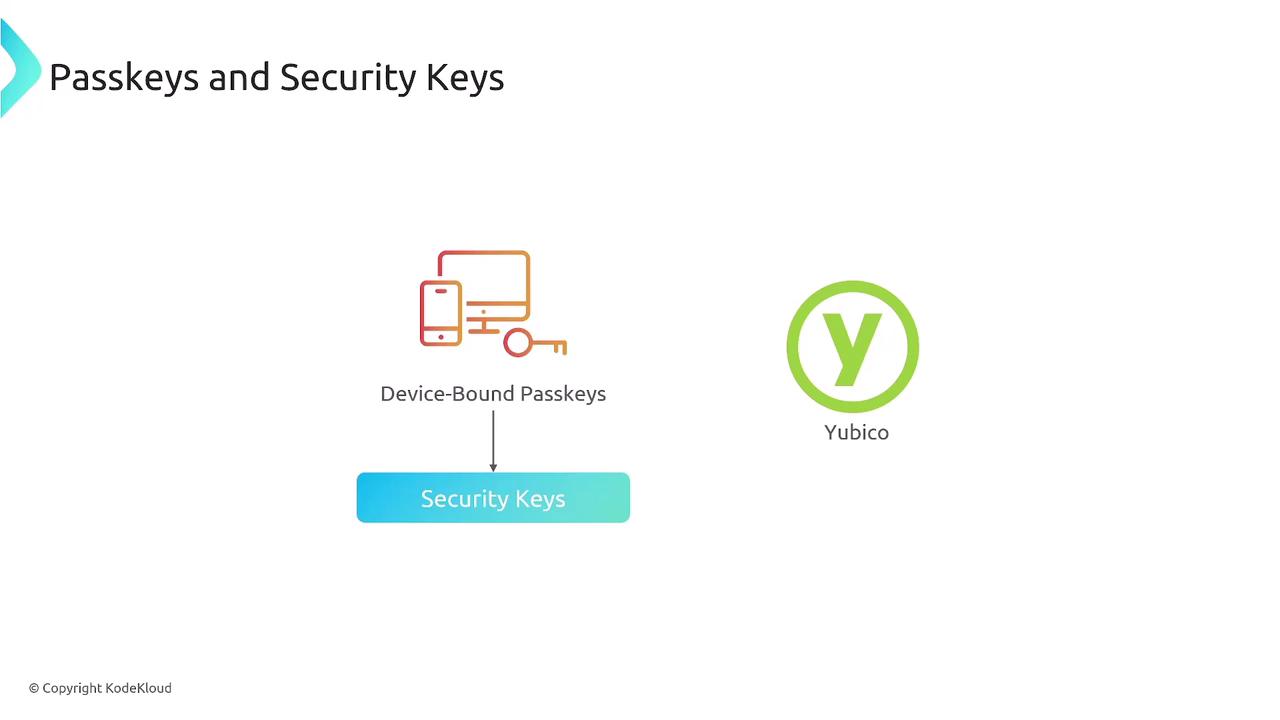
- Security Keys: Devices employing biometrics (fingerprints, facial recognition), device-bound credentials, or physical hardware tokens (e.g., YubiKey).
- Virtual Authenticators: Applications that generate time-based one-time passwords (TOTP) for secure access.

Passkeys and Security Keys
Passkeys are stored securely in managed keychains, while security keys such as YubiKey provide hardware-level authentication by requiring physical interaction.
Device-bound passkeys and hardware tokens (like YubiKey) add an extra layer by ensuring the user’s device or key is present during authentication.
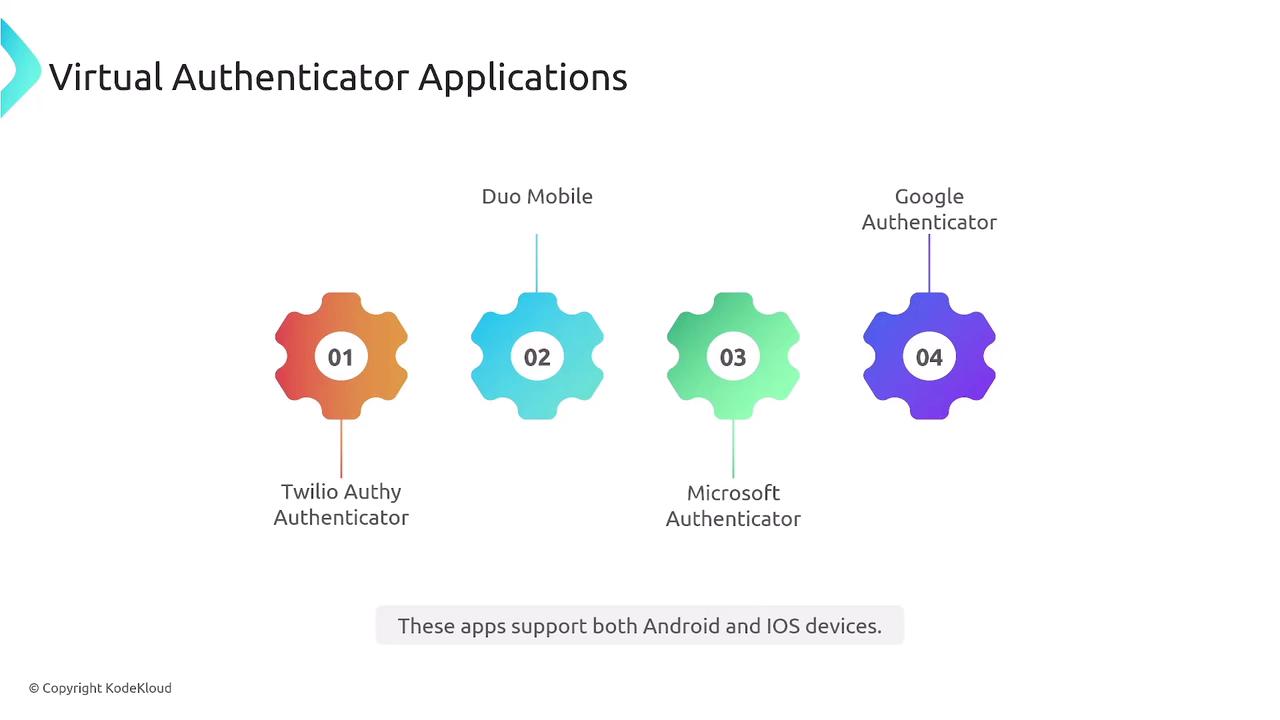
For TOTP-based authentication, virtual authenticator applications generate a time-based one-time password verified by AWS. Popular authenticator apps include Twilio Authy, Duo Mobile, Microsoft Authenticator, and Google Authenticator. For users preferring a hardware solution, RSA tokens and similarly sized security devices are available. These generate a synchronized code that, when entered correctly, grants access to AWS resources.
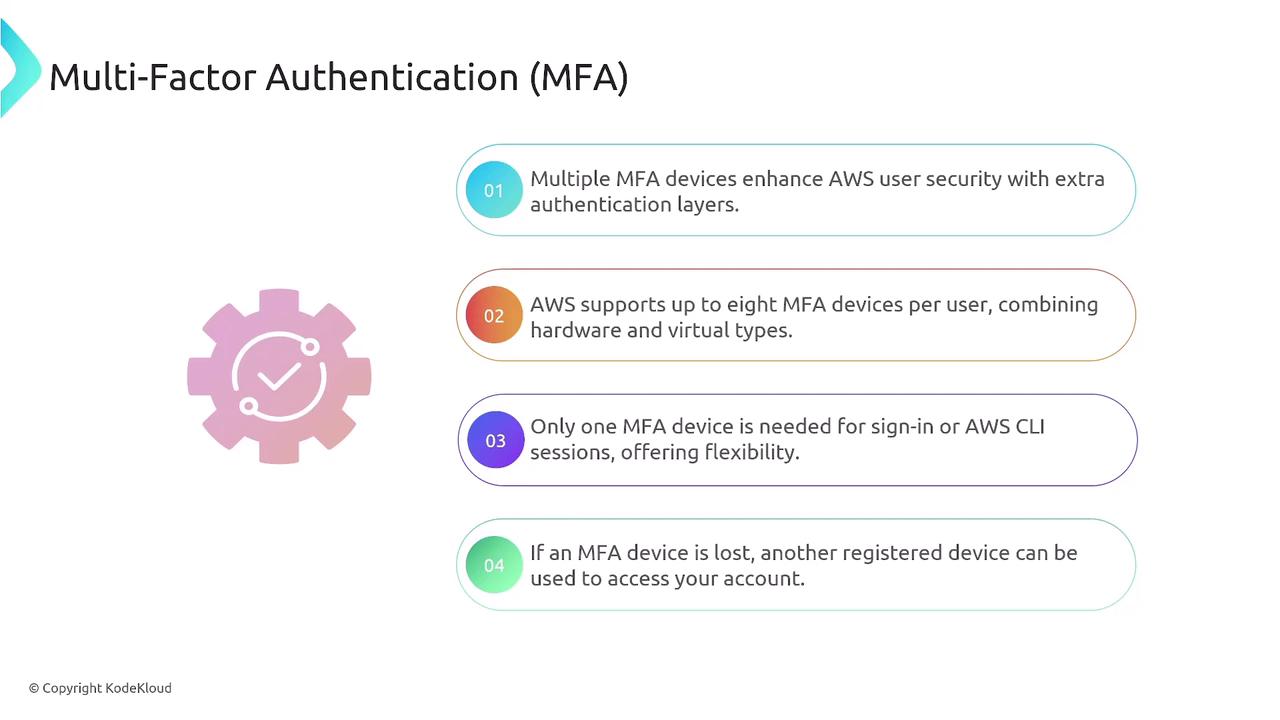
AWS allows up to eight MFA devices per user. It is advisable to designate a primary device for sign-in and secure a backup device for cases when the primary is unavailable. Many MFA solutions also offer backup codes for additional recovery options.
Password Policies
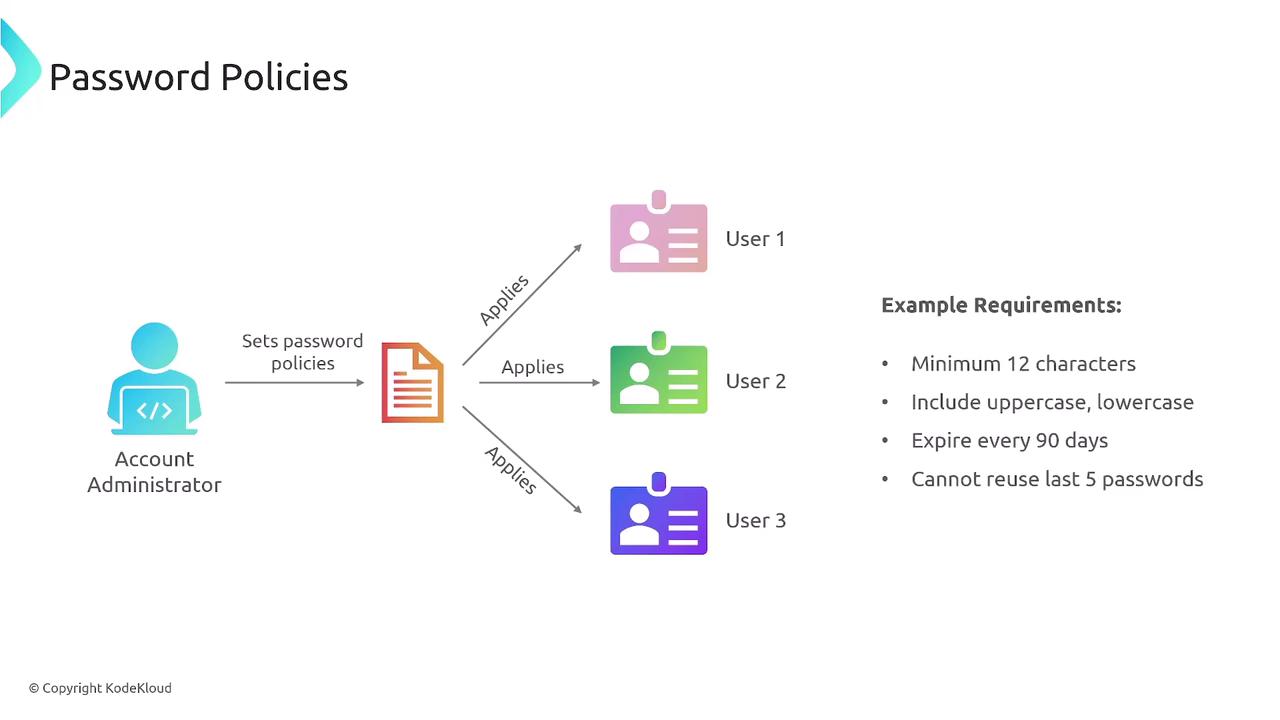
Another important IAM feature is the implementation of password policies. These policies enforce specific requirements for passwords used to access the AWS Management Console. Note that these policies do not apply to programmatic access via access keys, certificates, or CLI/SDK usage.
Administrators can set global requirements, such as:
- A minimum password length.
- A mix of uppercase and lowercase characters.
- Inclusion of special characters.
- Regular password expiration intervals.
- Restrictions on reusing previous passwords.
For example, a robust password policy might require that passwords:
- Contain at least 12 characters.
- Include both uppercase and lowercase letters.
- Expire every 90 days.
- Do not reuse the last five passwords.
Important Note
Password policies do not apply to the AWS root user or to users authenticating via access keys. Ensure that administrators plan additional protective measures for these access methods.
Keep in mind:
- If an IAM user's password expires, they lose access to the AWS Management Console, but they can still utilize their access keys.
- Password policy requirements (e.g., complexity or length) are enforced only when a password is changed. Existing passwords remain in effect until manually updated, though administrators may force expirations to apply new policies immediately.
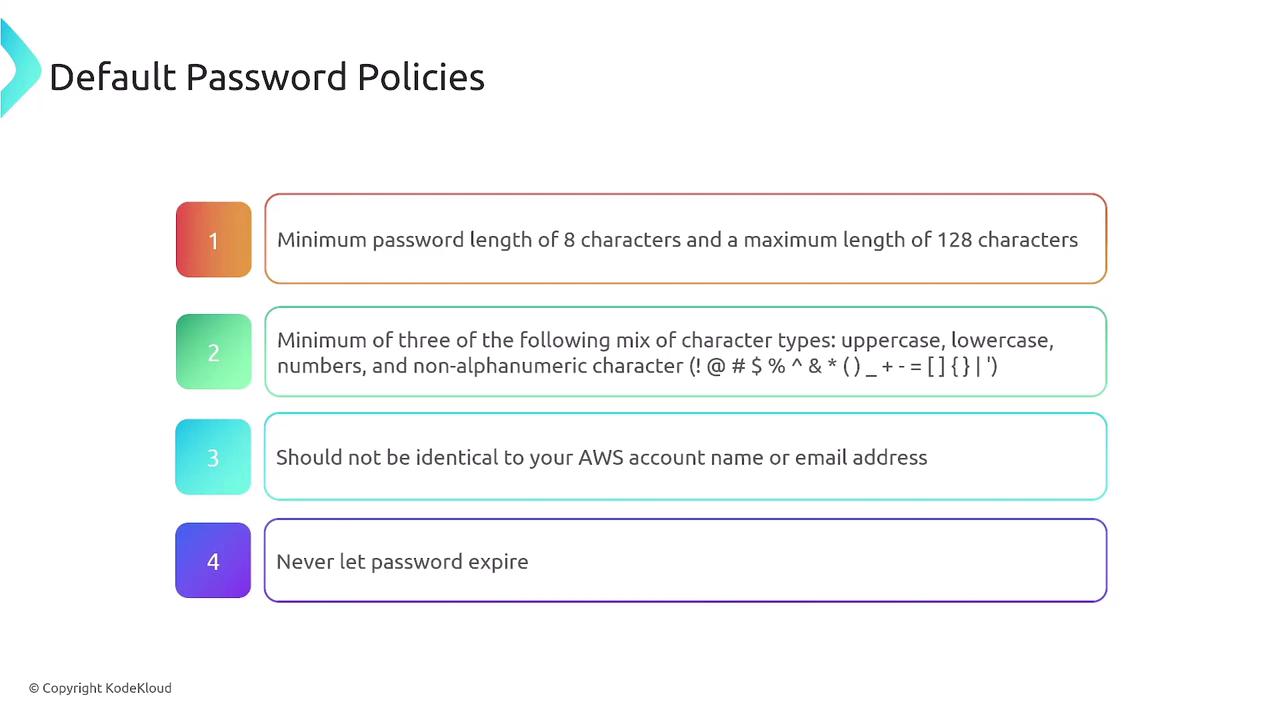
By default, AWS enforces a minimum password length of eight characters and a maximum of 128 characters. The default policy requires a mix of uppercase, lowercase, alphanumeric, and non-alphanumeric characters, and prohibits the inclusion of the AWS account name or email in the password. Passwords do not expire by default, so it is advisable to update them regularly.
Conclusion
This guide provided an in-depth look at MFA, password policies, and roles within IAM. By understanding and implementing these security features, you can significantly enhance the protection of your AWS environment.
In the next lesson, we will delve deeper into advanced IAM features and best practices to secure your AWS resources further.
For additional reading on similar topics, consider reviewing Kubernetes Basics and the AWS Documentation.
Watch Video
Watch video content