AWS Certified SysOps Administrator - Associate
Domain 4 Security and Compliance
Security and Compliance Policies in AWS Overview
Welcome to our comprehensive lesson on security compliance policies in AWS. In today’s digital landscape, robust security measures are essential to protect both physical and digital assets. Just as you would secure a building with key cards, locks, and guards, AWS employs advanced tools and best practices to safeguard its infrastructure and your data.
Before diving into AWS specifics, it is important to understand the fundamental role of security. Without proper protection measures, assets become vulnerable to theft, tampering, and misuse. Consider these examples:
This diagram is analogous to a secured building where locks and security personnel ensure that only authorized individuals can gain access. Similarly, AWS integrates robust security features to protect your resources in the cloud.
AWS and Cloud Security
AWS is committed to cloud security, prioritizing the protection of consumer data and infrastructure. If security ever failed, it would risk the entire cloud industry; hence, AWS builds advanced security measures directly into its services. As your business scales and innovates, AWS ensures your data remains secure through a variety of native security features.
AWS offers integrated security services such as distributed denial of service (DDoS) protection and web application filtering through AWS WAF. Many of these features are included in the pricing model, making robust security a seamless part of your cloud experience.
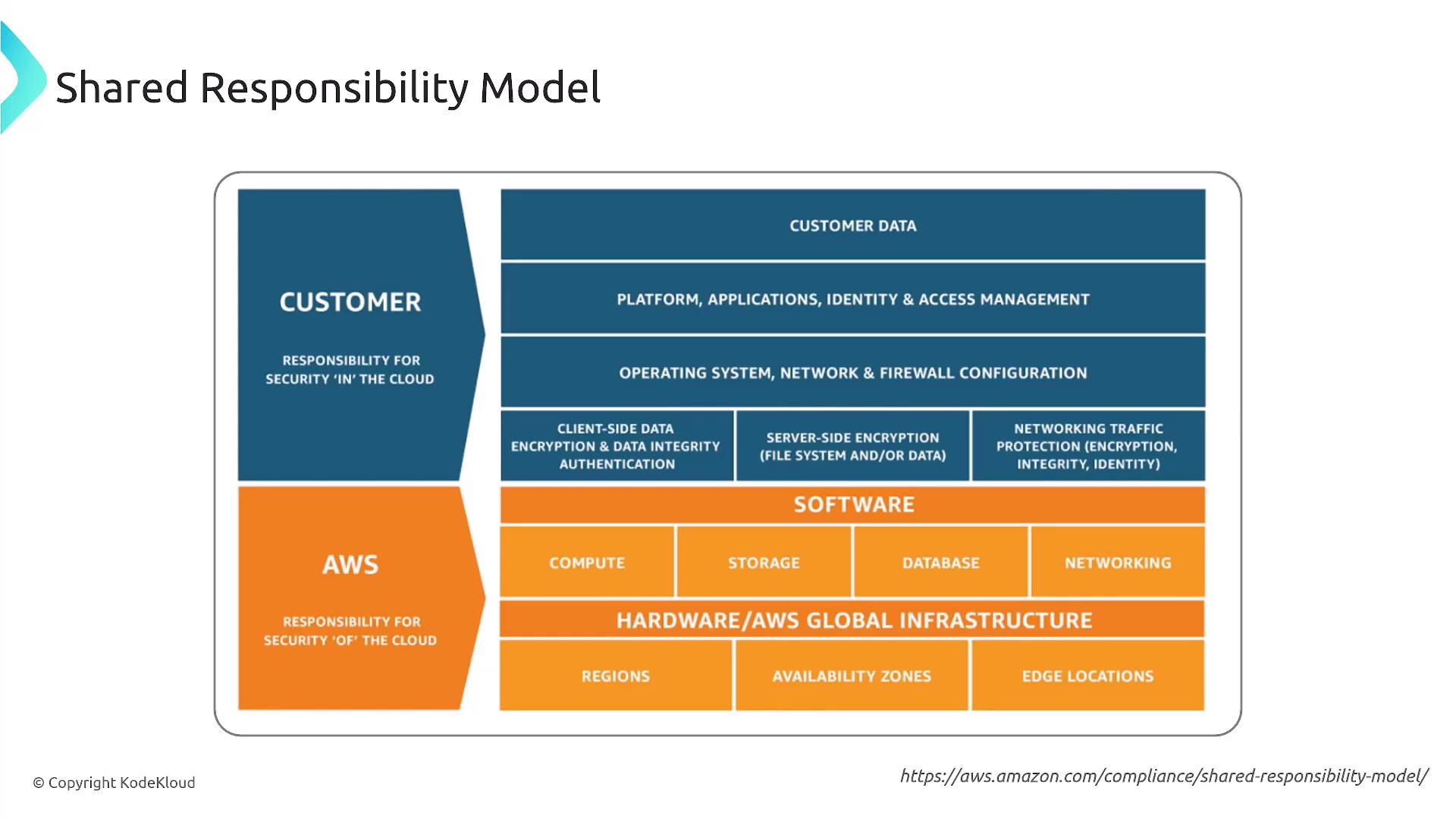
Shared Responsibility Model
AWS operates under a shared responsibility model. In this model, AWS is responsible for security "of" the cloud—including physical infrastructure, networking, and facilities—while you manage security "in" the cloud by controlling your data, configurations, and applications.
Note
Remember, your responsibility extends to managing user permissions and data configurations, ensuring that only authorized users have access to sensitive information.
Certifications, Attestations, and Compliance
By choosing AWS, you benefit from a platform that holds multiple global security certifications and attestations, such as ISO/IEC 27001, 27017, 27018, SOC 1-3, PCI DSS, HIPAA, and GDPR. Detailed compliance documentation is available through AWS Artifact, allowing you to access security and compliance reports tailored to various regions.

AWS Security Tools
AWS provides a wide range of security tools designed to manage identity and access, data protection, and network security. Below is an overview of some key services:
Identity and Access Management (IAM):
IAM allows you to manage users, groups, and roles with precise permissions. Multi-factor authentication (MFA) adds an extra layer of security to user access.
Data Protection and Encryption:
AWS Key Management Service (KMS) offers secure key management for encrypting data at rest. AWS Certificate Manager (ACM) simplifies the management of encryption for data in transit.
Network Security:
Amazon VPC provides stateful and stateless firewall capabilities to control network access. Additional services like AWS Shield, AWS WAF, and advanced network firewalls further enhance your network security.
Automation and Governance:
Automation services are critical for enforcing security policies and maintaining compliance on a large scale. AWS Security Hub centralizes security findings, while CloudWatch Logs, AWS CloudTrail, and EventBridge facilitate auditing and automated monitoring. In addition, AWS Inspector enables penetration testing, and GuardDuty uses machine learning to detect potential security threats.
Below is a summary table highlighting key AWS security services:
| Service Category | Key Services | Use Case |
|---|---|---|
| Identity and Access Management | IAM, MFA | Managing user permissions and secure logins |
| Data Protection | KMS, ACM | Encrypting data both at rest and in transit |
| Network Security | Amazon VPC, AWS Shield, AWS WAF | Controlling network access and mitigating attacks |
| Automation and Governance | Security Hub, CloudTrail, GuardDuty | Centralized monitoring and automated compliance |
AWS offers over a dozen dedicated security services, ensuring that nearly every aspect of your cloud architecture is protected. The key is to understand which services and configurations best align with your security requirements.
Thank you for reading this lesson on AWS security and compliance policies. We hope this guide provides you with the foundational understanding needed to secure your cloud environment effectively.
For further reading, check out the following references:
Watch Video
Watch video content